Test resource-specific consent permissions in Teams
Resource-specific consent (RSC) is an authorization framework built by Microsoft Teams and Microsoft identity that allows for granting scoped access to an application.
Through RSC, an authorized user can give an application access to the data of a specific instance of a resource type instead of every instance in the entire tenant. For example, a person who owns both team A and team B can decide to give the data for the Contoso app to only team A and not team B. The same concept of scoped data access applies to chats and meetings. For more information, see Resource-specific consent (RSC).
Prerequisites
Ensure that you verify the following app manifest changes for resource-specific consent before testing:
RSC permissions for app manifest version 1.12 and later
Add a webApplicationInfo key to your app manifest with the following values:
| Name | Type | Description |
|---|---|---|
id |
String | Your Microsoft Entra app ID. For more information, see register your app in the Microsoft Entra admin center. |
resource |
String | This field has no operation in RSC, but must be added and have a value to avoid an error response; any string will do. |
Specify permissions needed by the app.
| Name | Type | Description |
|---|---|---|
authorization |
Object | List of permissions that the app needs to function. For more information, see authorization. |
Example for RSC in a team
"webApplicationInfo": {
"id": "XXxxXXXXX-XxXX-xXXX-XXxx-XXXXXXXxxxXX",
"resource": "https://RscBasedStoreApp"
},
"authorization": {
"permissions": {
"resourceSpecific": [
{
"name": "TeamSettings.Read.Group",
"type": "Application"
},
{
"name": "TeamSettings.ReadWrite.Group",
"type": "Application"
},
{
"name": "ChannelSettings.Read.Group",
"type": "Application"
},
{
"name": "ChannelSettings.ReadWrite.Group",
"type": "Application"
},
{
"name": "Channel.Create.Group",
"type": "Application"
},
{
"name": "Channel.Delete.Group",
"type": "Application"
},
{
"name": "ChannelMessage.Read.Group",
"type": "Application"
},
{
"name": "ChannelMeeting.ReadBasic.Group",
"type": "Application"
},
{
"name": "TeamsAppInstallation.Read.Group",
"type": "Application"
},
{
"name": "TeamsTab.Read.Group",
"type": "Application"
},
{
"name": "TeamsTab.Create.Group",
"type": "Application"
},
{
"name": "TeamsTab.ReadWrite.Group",
"type": "Application"
},
{
"name": "TeamsTab.Delete.Group",
"type": "Application"
},
{
"name": "TeamMember.Read.Group",
"type": "Application"
},
{
"name": "TeamsActivity.Send.Group",
"type": "Application"
}
]
}
}
Example for RSC in a chat
"webApplicationInfo": {
"id": "XXxxXXXXX-XxXX-xXXX-XXxx-XXXXXXXxxxXX",
"resource": "https://RscBasedStoreApp"
},
"authorization": {
"permissions": {
"resourceSpecific": [
{
"name": "ChatSettings.Read.Chat",
"type": "Application"
},
{
"name": "ChatSettings.ReadWrite.Chat",
"type": "Application"
},
{
"name": "ChatMessage.Read.Chat",
"type": "Application"
},
{
"name": "ChatMember.Read.Chat",
"type": "Application"
},
{
"name": "Chat.Manage.Chat",
"type": "Application"
},
{
"name": "TeamsTab.Read.Chat",
"type": "Application"
},
{
"name": "TeamsTab.Create.Chat",
"type": "Application"
},
{
"name": "TeamsTab.Delete.Chat",
"type": "Application"
},
{
"name": "TeamsTab.ReadWrite.Chat",
"type": "Application"
},
{
"name": "TeamsAppInstallation.Read.Chat",
"type": "Application"
},
{
"name": "OnlineMeeting.ReadBasic.Chat",
"type": "Application"
},
{
"name": "Calls.AccessMedia.Chat",
"type": "Application"
},
{
"name": "Calls.JoinGroupCalls.Chat",
"type": "Application"
},
{
"name": "TeamsActivity.Send.Chat",
"type": "Application"
}
]
}
}
Note
If the app is meant to support installation in both team and chat scopes, then both team and chat permissions can be specified in the same manifest under authorization.
RSC permissions for app manifest version 1.11 and earlier
Add a webApplicationInfo key to your app manifest with the following values:
| Name | Type | Description |
|---|---|---|
id |
String | Your Microsoft Entra app ID. For more information, see register your app in the Microsoft Entra admin center. |
resource |
String | This field has no operation in RSC, but must be added and have a value to avoid an error response; any string will do. |
applicationPermissions |
Array of strings | RSC permissions for your app. For more information, see Supported RSC permissions. |
Example for RSC in a team
"webApplicationInfo": {
"id": "XXxxXXXXX-XxXX-xXXX-XXxx-XXXXXXXxxxXX",
"resource": "https://RscBasedStoreApp",
"applicationPermissions": [
"TeamSettings.Read.Group",
"TeamSettings.ReadWrite.Group",
"ChannelSettings.Read.Group",
"ChannelSettings.ReadWrite.Group",
"Channel.Create.Group",
"Channel.Delete.Group",
"ChannelMessage.Read.Group",
"ChannelMeeting.ReadBasic.Group",
"TeamsAppInstallation.Read.Group",
"TeamsTab.Read.Group",
"TeamsTab.Create.Group",
"TeamsTab.ReadWrite.Group",
"TeamsTab.Delete.Group",
"TeamMember.Read.Group",
"TeamsActivity.Send.Group"
]
}
Example for RSC in a chat
"webApplicationInfo": {
"id": "XXxxXXXXX-XxXX-xXXX-XXxx-XXXXXXXxxxXX",
"resource": "https://RscBasedStoreApp",
"applicationPermissions": [
"ChatSettings.Read.Chat",
"ChatSettings.ReadWrite.Chat",
"ChatMessage.Read.Chat",
"ChatMember.Read.Chat",
"Chat.Manage.Chat",
"TeamsTab.Read.Chat",
"TeamsTab.Create.Chat",
"TeamsTab.Delete.Chat",
"TeamsTab.ReadWrite.Chat",
"TeamsAppInstallation.Read.Chat",
"OnlineMeeting.ReadBasic.Chat",
"Calls.AccessMedia.Chat",
"Calls.JoinGroupCalls.Chat",
"TeamsActivity.Send.Chat"
]
}
Note
If the app is meant to support installation in both team and chat scopes, then both team and chat permissions can be specified in the same manifest under applicationPermissions.
Important
In your app manifest, only include the RSC permissions that you want your app to have.
Note
If the app is meant to access calling or media APIs, then the webApplicationInfo.Id should be the Microsoft Entra app ID of an Azure Bot Service.
Test added RSC permissions to a team using the Postman app
To check whether the RSC permissions are being honored by the API request payload, you need to copy the RSC JSON test code for team into your local environment and update the following values:
azureADAppId: Your app's Microsoft Entra app ID.azureADAppSecret: Your Microsoft Entra app password.token_scope: The scope is required to get a token. Set the value tohttps://graph.microsoft.com/.default.teamGroupId: You can get the team group ID from the Teams client as follows:- In the Teams client, select Teams from the far left navigation bar.
- Select the team where the app is installed from the dropdown menu.
- Select the More options icon (⋯).
- Select Get link to team.
- Copy and save the groupId value from the string.
Test added RSC permissions to a chat using the Postman app
To check whether the RSC permissions are being honored by the API request payload, you need to copy the RSC JSON test code for chats into your local environment and update the following values:
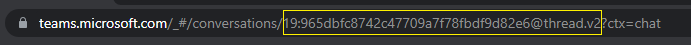
azureADAppId: Your app's Microsoft Entra app ID.azureADAppSecret: Your Microsoft Entra app password.token_scope: The scope is required to get a token. Set the value tohttps://graph.microsoft.com/.default.tenantId: The name or the Microsoft Entra Object ID of your tenant.chatId: You can get the chat thread ID from the Teams web client as follows:- In the Teams web client, select Chat from the far left navigation bar.
- Select the chat where the app is installed from the dropdown menu.
- Copy the web URL and save the chat thread ID from the string.
Use Postman
- Open the Postman app.
- Select File > Import > Import file to upload the updated JSON file from your environment.
- Select the Collections tab.
- Select the chevron > next to the Test RSC to expand the details view and see the API requests.
Execute the entire permissions collection for each API call. The permissions that you specified in your app manifest must succeed, while those not specified must fail with an HTTP 403 status code. Check all of the response status codes to confirm that the behavior of the RSC permissions in your app meets expectations.
Note
To test specific DELETE and READ API calls, add those instance scenarios to the JSON file.
Test revoked RSC permissions using Postman
- Uninstall the app from the specific resource.
- Follow the steps for either chat or team:
- Check all the response status codes to confirm that the specific API calls have failed with an HTTP 403 status code.
See also
Platform Docs
คำติชม
เร็วๆ นี้: ตลอดปี 2024 เราจะขจัดปัญหา GitHub เพื่อเป็นกลไกคำติชมสำหรับเนื้อหา และแทนที่ด้วยระบบคำติชมใหม่ สำหรับข้อมูลเพิ่มเติม ให้ดู: https://aka.ms/ContentUserFeedback
ส่งและดูข้อคิดเห็นสำหรับ