หมายเหตุ
การเข้าถึงหน้านี้ต้องได้รับการอนุญาต คุณสามารถลอง ลงชื่อเข้าใช้หรือเปลี่ยนไดเรกทอรีได้
การเข้าถึงหน้านี้ต้องได้รับการอนุญาต คุณสามารถลองเปลี่ยนไดเรกทอรีได้
Important
Azure Cache for Redis announced its retirement timeline for all SKUs. We recommend moving your existing Azure Cache for Redis instances to Azure Managed Redis as soon as you can.
For more details about the retirement:
A managed identity helps Azure services connect to each other by making authentication more streamlined and secure. Instead of managing authorization between the services, a managed identity uses Microsoft Entra ID to provide authentication. This article describes how to use managed identity to connect Azure Cache for Redis caches to Azure Storage accounts.
A managed identity lets you simplify the process of securely connecting to an Azure Storage account for the following Azure Redis scenarios:
- Data persistence to back up the data in your cache.
- Import or export to save snapshots of cache data or import data from a saved file.
Note
Only the Azure Redis data persistence and import-export features use managed identity. These features are available only in Azure Redis Premium tier, so managed identity is available only in Azure Redis Premium tier.
Azure Cache for Redis supports both system-assigned and user-assigned managed identities. Each type of managed identity has advantages, but the functionality is the same in Azure Cache for Redis.
- System-assigned identity is specific to the cache resource. If the cache is deleted, the identity is deleted.
- User-assigned identity is specific to a user. You can assign this identity to any resource, such as a storage account, that supports managed identity. This assignment remains even if you delete the specific cache resource.
Configuring managed identity for Azure Redis Premium data persistence or import-export features consists of several parts:
- Enable the managed identity in the Azure Redis cache.
- Configure the Azure Storage account to use the managed identity.
- Configure the data persistence or import-export features to use the managed identity.
All the parts must be completed correctly before Azure Redis data persistence or import-export can access the storage account. Otherwise, you see errors or no data written.
Scope of availability
| Tier | Basic, Standard | Premium | Enterprise, Enterprise Flash |
|---|---|---|---|
| Available | Yes | Yes | No |
Prerequisites
- Ability to create and configure a Premium-tier Azure Redis cache and an Azure Storage account in an Azure subscription.
- To assign a user-assigned managed identity: A managed identity created in the same Azure subscription as the Azure Redis cache and Storage account.
Enable managed identity
You can enable managed identity for your Azure Redis cache by using the Azure portal, Azure CLI, or Azure PowerShell. You can enable managed identity when you create a cache instance, or afterwards.
Enable managed identity in the Azure portal
During cache creation, you can assign only system-assigned managed identity. You can add either system-assigned or a user-assigned identity to an existing cache.
Create a new cache with managed identity
In the Azure portal, choose to create an Azure Cache for Redis cache. On the Basics tab, select Premium for the Cache SKU, and complete the rest of the required information.
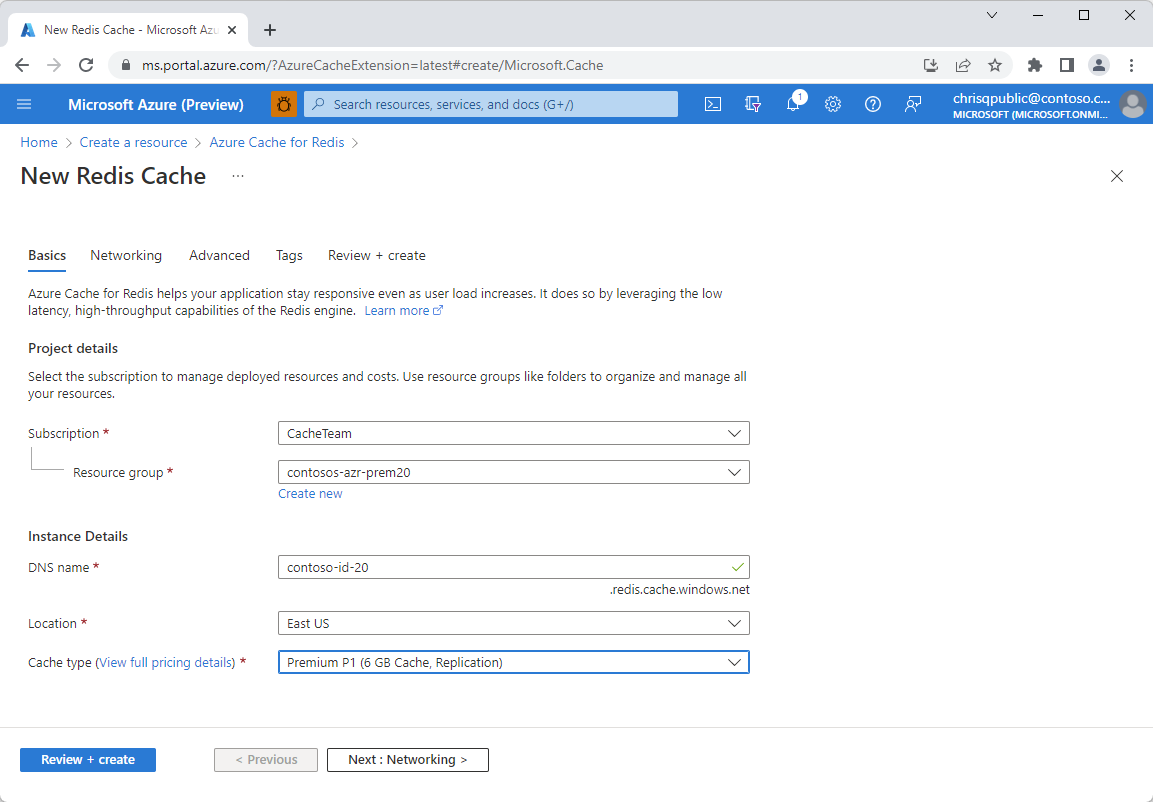
Select the Advanced tab, and under System assigned managed identity, set Status to On.
Complete the cache creation process.
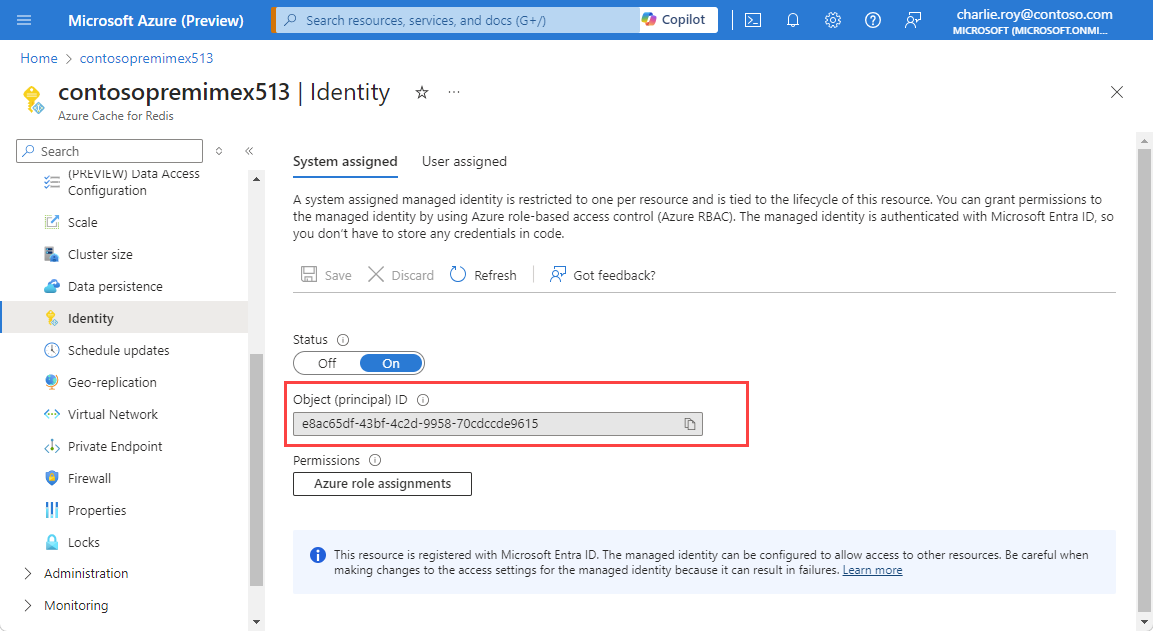
Once the cache is deployed, go to the cache page and select Identity under Settings in the left navigation menu. Verify that an Object (principal) ID appears on the System assigned tab of the Identity page.
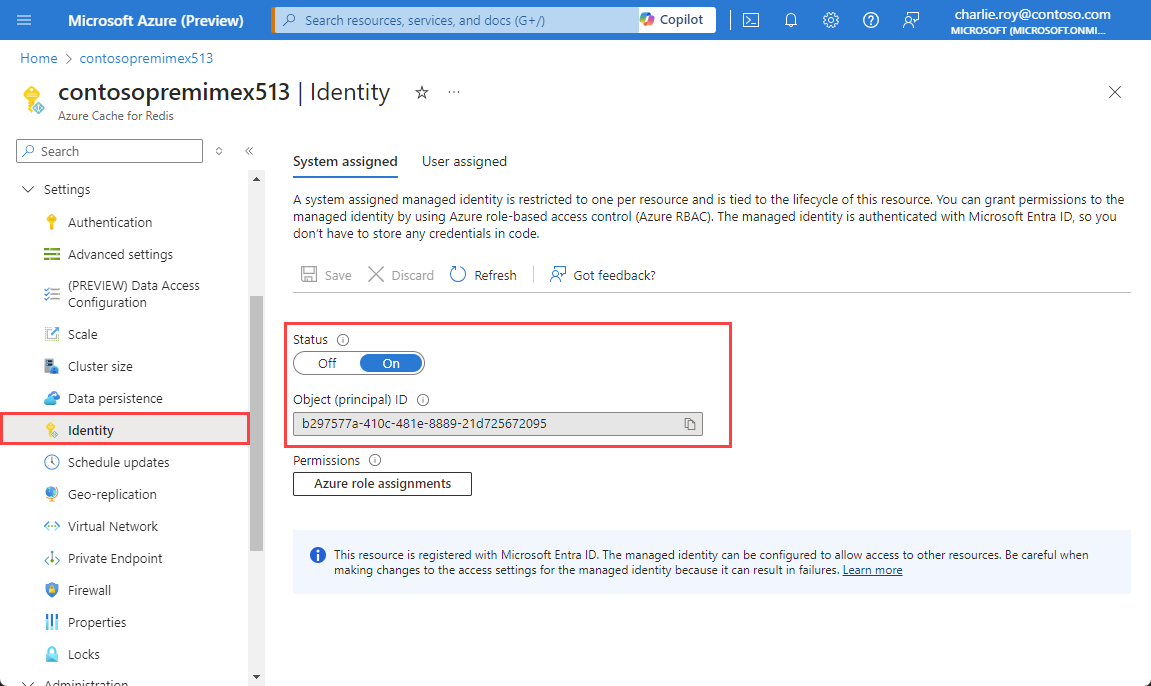
Add system-assigned identity to an existing cache
On the Azure portal page for your Azure Redis Premium cache, select Identity under Settings in the left navigation menu.
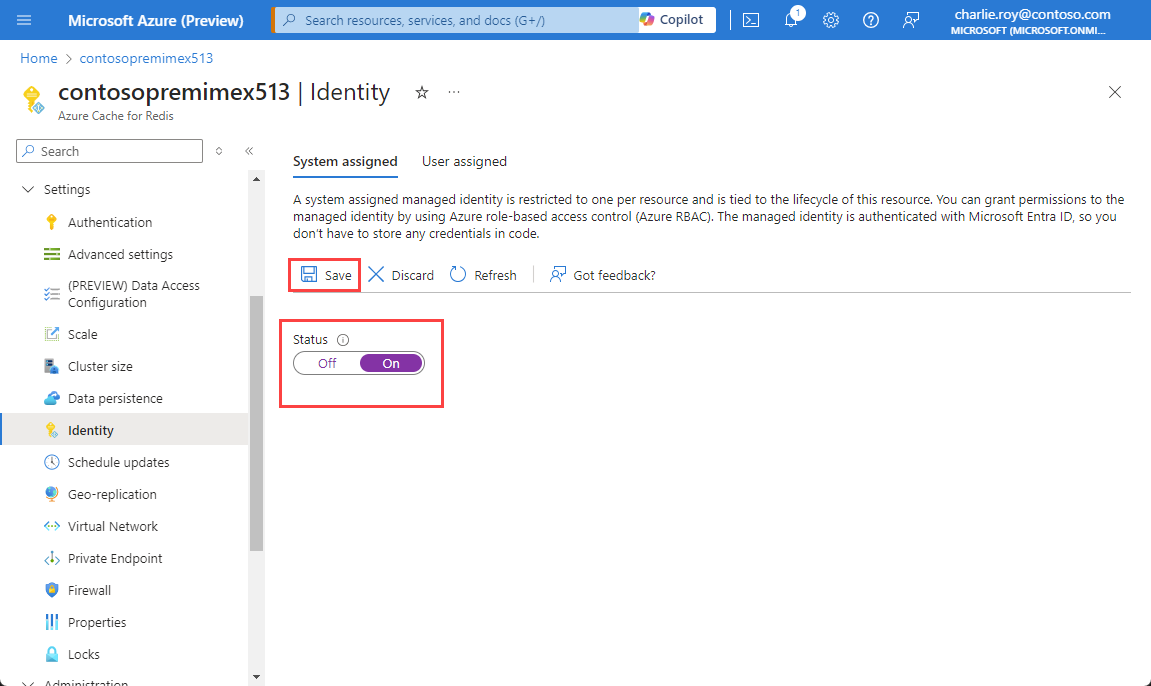
On the System assigned tab, set Status to On, and then select Save.
Respond Yes to the Enable system assigned managed identity prompt.
Once the identity is assigned, verify that an Object (principal) ID appears on the System assigned tab of the Identity page.

Add a user-assigned identity to an existing cache
On the Azure portal page for your Azure Redis Premium cache, select Identity under Settings in the left navigation menu.
Select the User assigned tab, and then select Add.
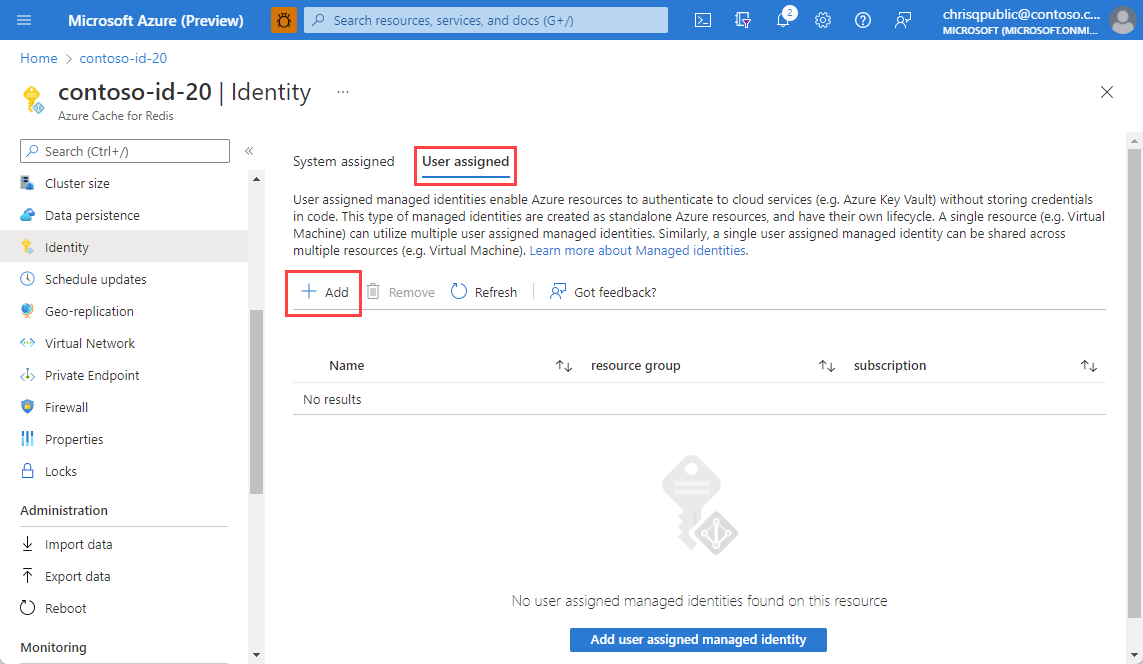
On the Add user assigned managed identity screen, select a managed identity from your subscription, and select Add. For more information on user assigned managed identities, see manage user-assigned identity.
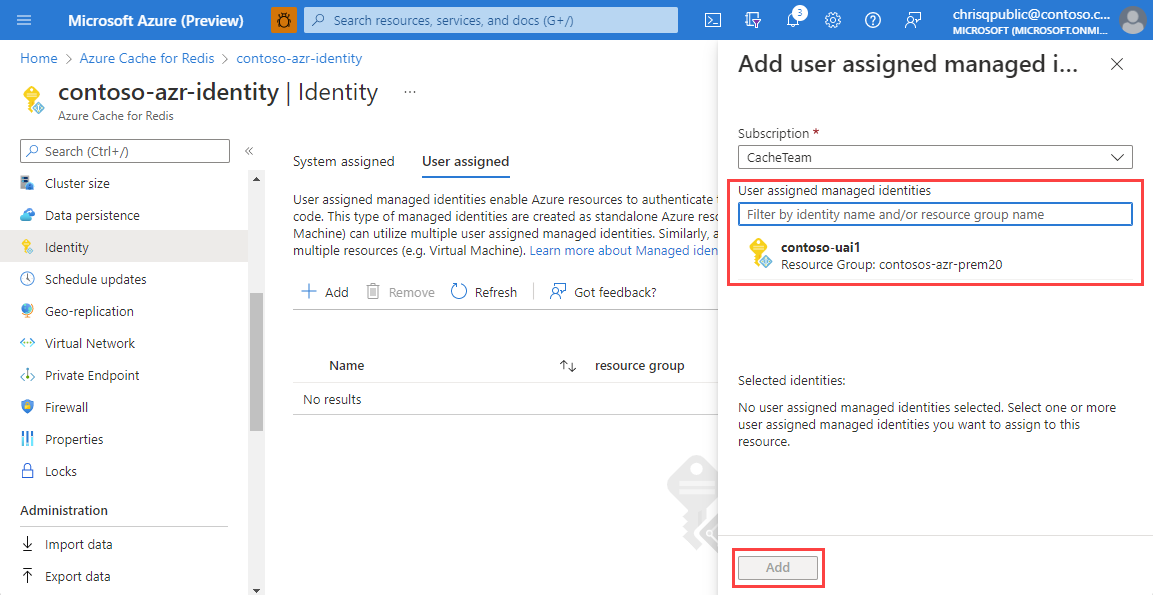
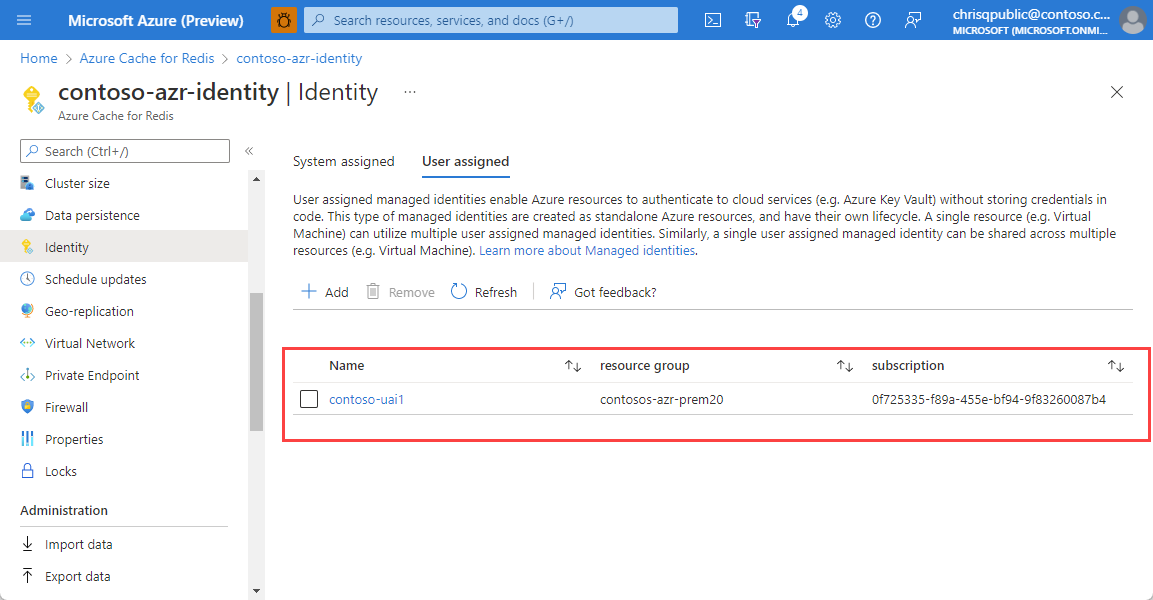
Once the user-assigned identity is added, verify that it appears on the User assigned tab of the Identity page.
Enable managed identity using Azure CLI
You can use the Azure CLI for creating a new cache with managed identity by using az redis create. You can update an existing cache to use managed identity by using az redis identity.
For example, to update a cache to use system-managed identity, use the following Azure CLI command:
az redis identity assign \--mi-system-assigned \--name MyCacheName \--resource-group MyResource Group
Enable managed identity using Azure PowerShell
You can use Azure PowerShell for creating a new cache with managed identity by using New-AzRedisCache. You can update an existing cache to use managed identity by using Set-AzRedisCache.
For example, to update a cache to use system-managed identity, use the following Azure PowerShell command:
Set-AzRedisCache -ResourceGroupName \"MyGroup\" -Name \"MyCache\" -IdentityType "SystemAssigned"
Configure the storage account to use managed identity
In the Azure portal, create a new storage account or open an existing storage account that you want to connect to your cache instance.
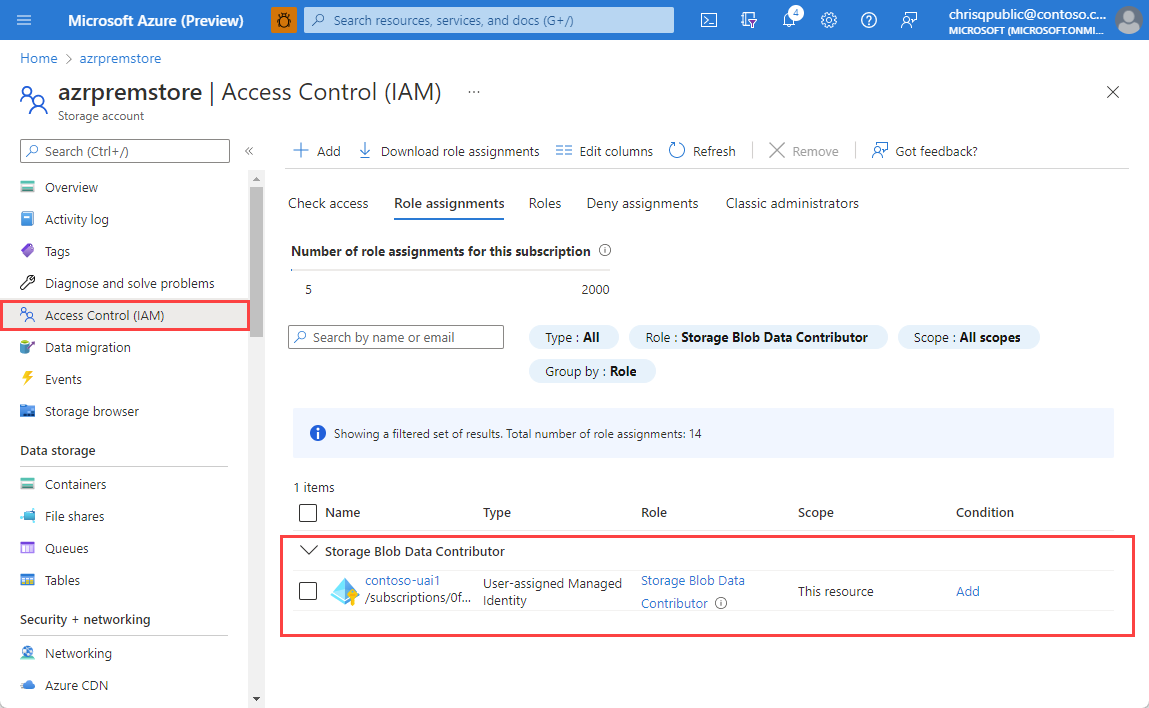
Select Access control (IAM) from the left navigation menu.
On the Access control (IAM) page, select Add > Add role assignment.
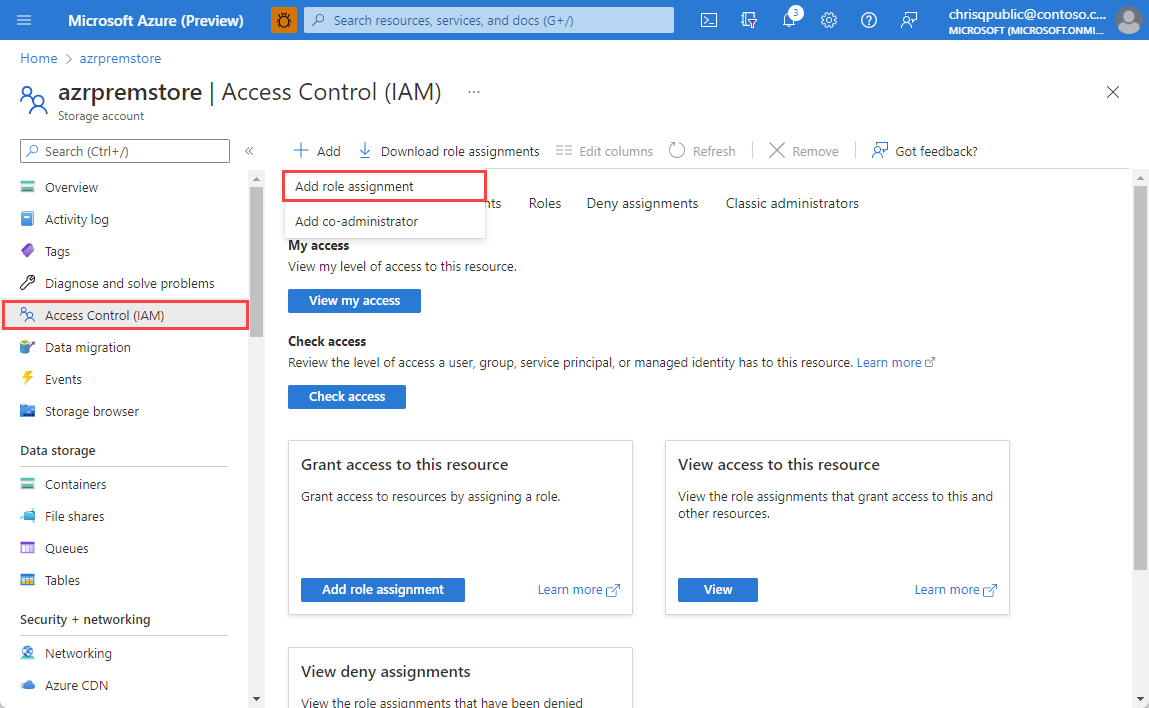
On the Role tab of the Add Role Assignment page, search for and select Storage Blob Data Contributor, and then select Next.
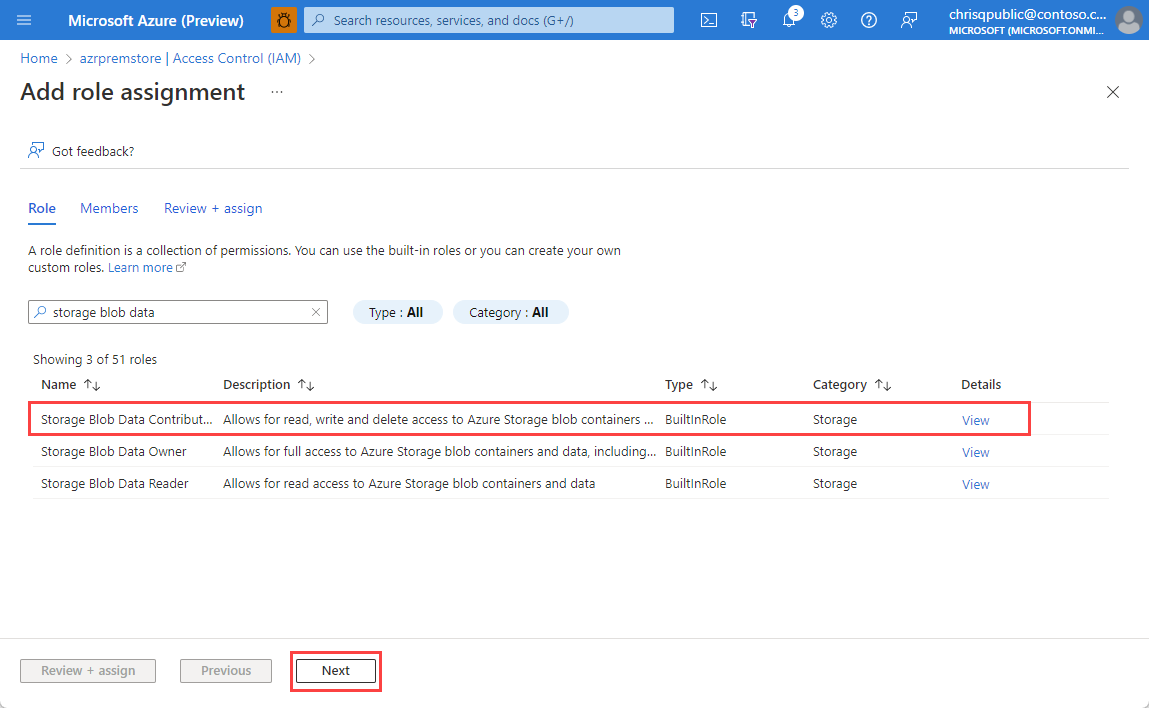
On the Members tab, for Assign access to, select Managed Identity, and then select Select members.
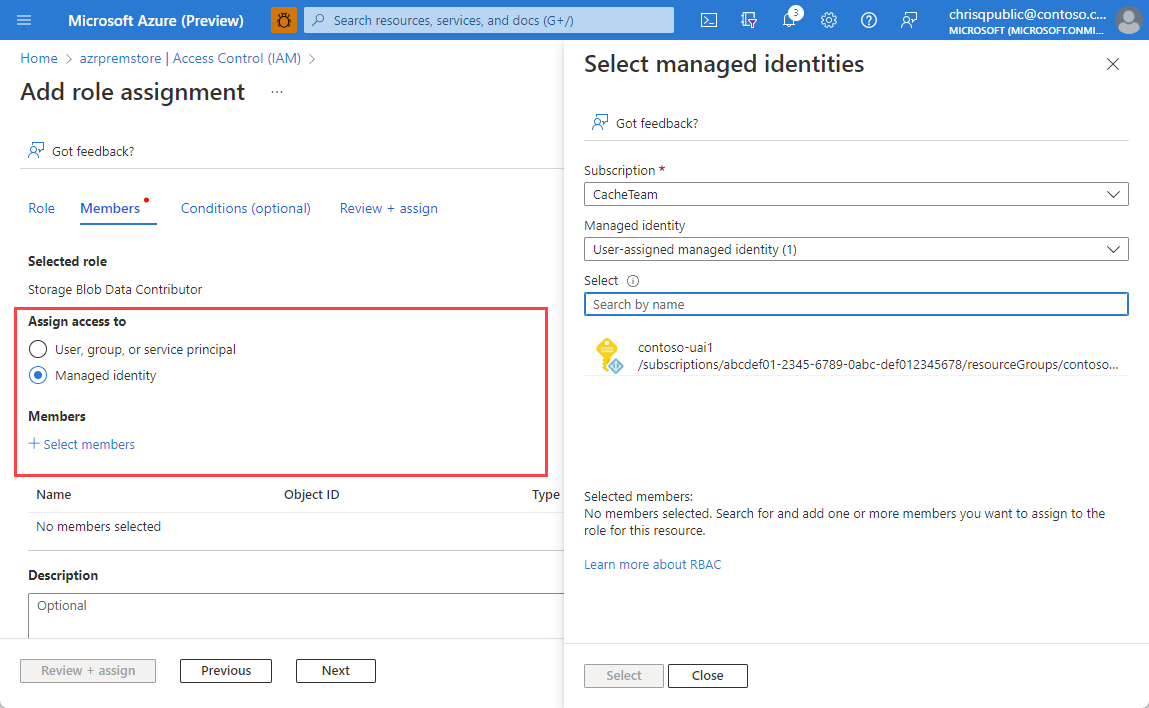
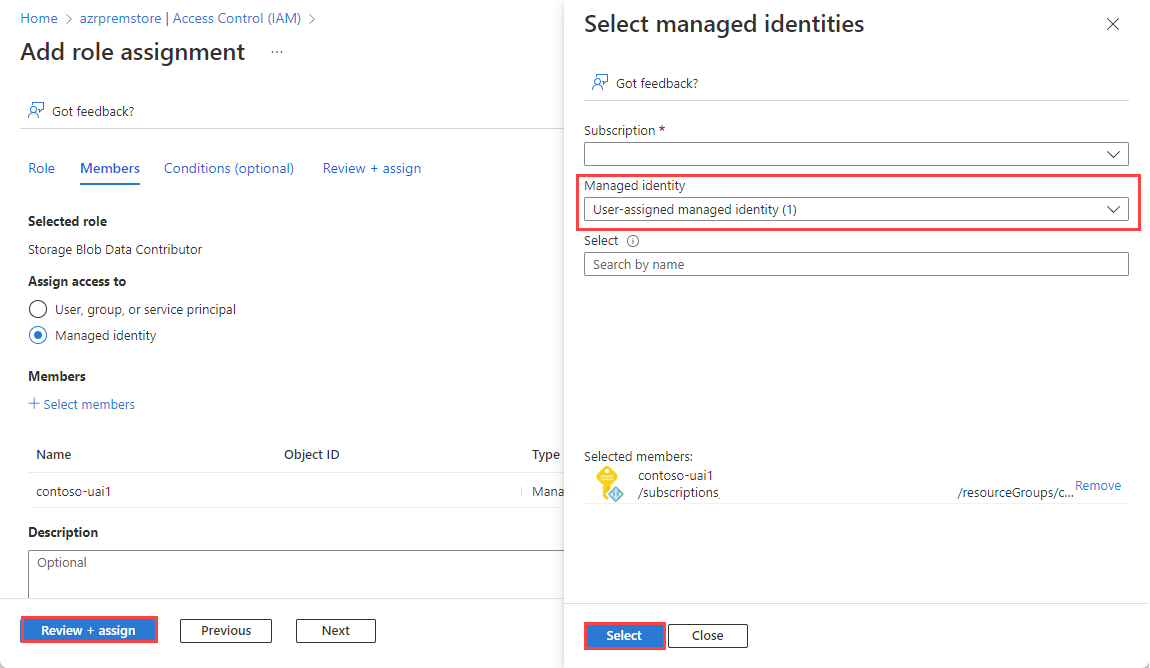
In the Select managed identities pane, select the dropdown arrow under Managed identity to see all your available user-assigned and system-assigned managed identities. If you have many managed identities, you can search for the one you want. Choose the managed identities you want, and then select Select.
On the Add role assignment page, select Review + assign, and then select Review + assign again to confirm.
On the storage account's Access control (IAM) page, select View under View access to this resource, and then search for Storage Blob Data Contributor on the Role Assignments tab to verify that the managed identities are added.
Important
For export to work with a storage account with firewall exceptions, you must:
- Add the Azure Redis cache as a Storage Blob Data Contributor through system-assigned identity, and
- On the storage account Networking page, select Allow Azure services on the trusted services list to access this storage account.
If you don't use managed identity and instead authorize a storage account with a key, having firewall exceptions on the storage account breaks the persistence process and the import-export processes.
Use managed identity with data persistence
On the Azure portal page for your Azure Redis Premium cache that has the Storage Blob Data Contributor role, select Data persistence under Settings in the left navigation menu.
Ensure that Authentication Method is set to Managed Identity.
Important
The selection defaults to the system-assigned identity if enabled. Otherwise, it uses the first listed user-assigned identity.
Under Storage Account, select the storage account you configured to use managed identity, if not already selected, and select Save if necessary.
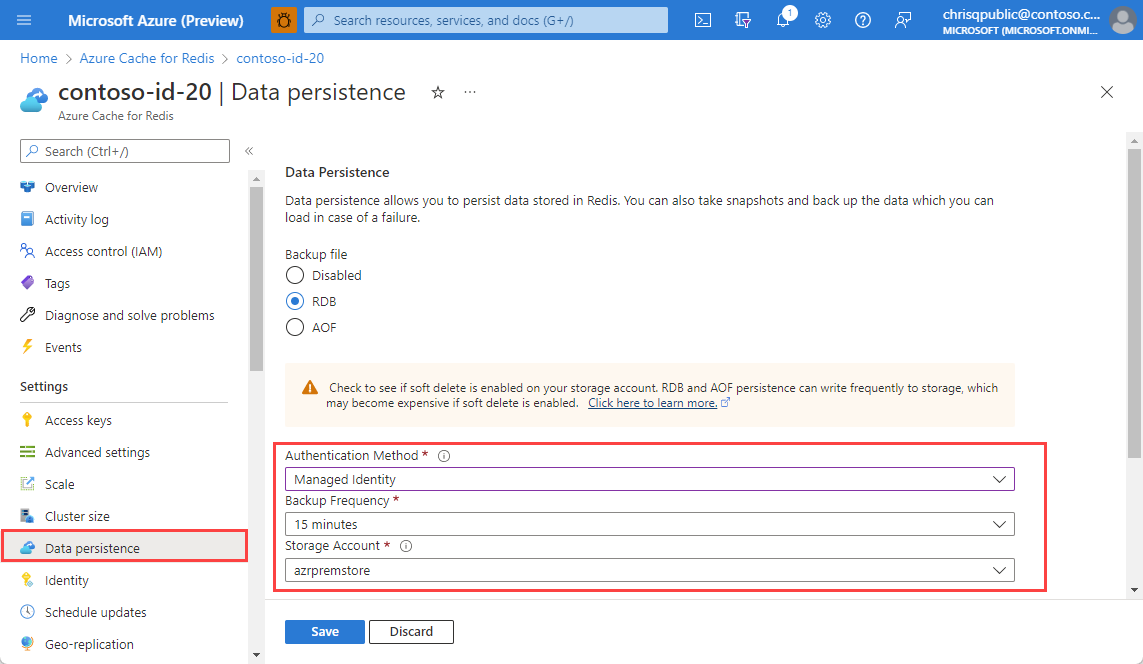
You can now save data persistence backups to the storage account using managed identity authentication.
Use managed identity to import and export cache data
On the Azure portal page for your Azure Redis Premium cache that has the Storage Blob Data Contributor role, select Import data or Export data under Administration in the left navigation menu.
On the Import data or Export data screen, select Managed Identity for Authentication Method.
To import data, on the Import data screen, select Choose Blob(s) next to RDB File(s). Select your Redis Database (RDB) file or files from the blob storage location, and select Select.
To export data, on the Export data screen, enter a Blob name prefix, and then select Choose Storage Container next to Export output. Select or create a container to hold the exported data, and select Select.
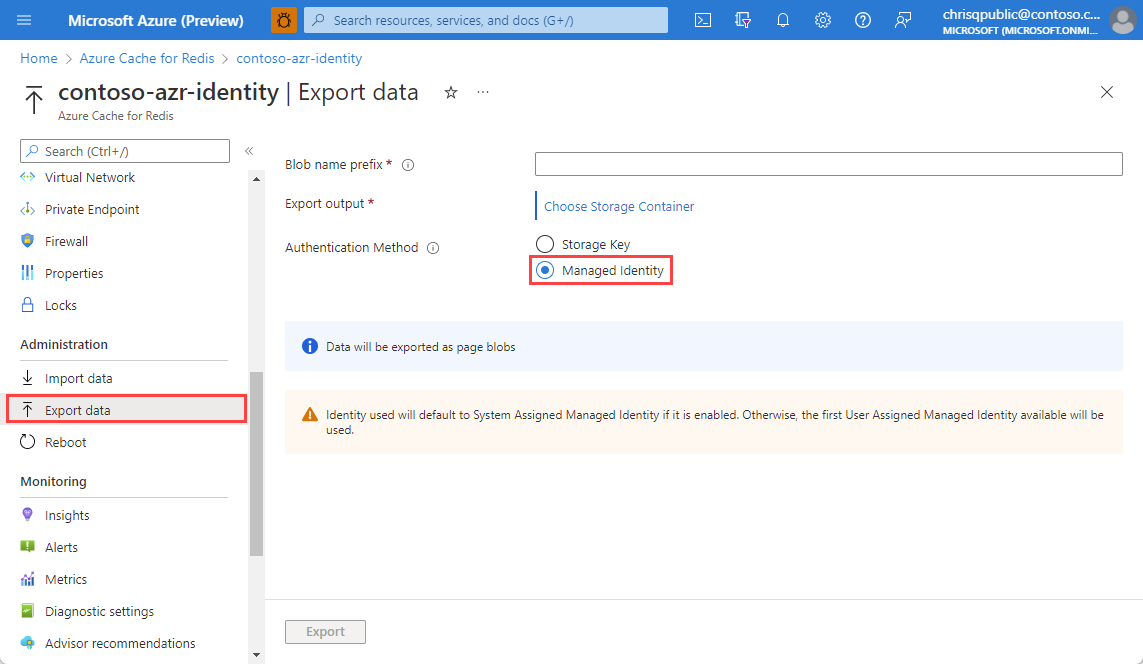
On the Import data or Export data screen, select Import or Export respectively.
Note
It takes a few minutes to import or export the data.
Important
If you see an export or import failure, double check that your storage account has been configured with your cache's system-assigned or user-assigned identity. The identity used defaults to system-assigned identity if enabled. Otherwise, it uses the first listed user-assigned identity.
Related content
- Learn more about Azure Cache for Redis features.
- What are managed identities?