Device control policies in Microsoft Defender for Endpoint
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender for Business
This article describes device control policies, rules, entries, groups, and advanced conditions. Essentially, device control policies define access for a set of devices. The devices that are in scope are determined by a list of included device groups and a list of excluded device groups. A policy applies if the device is in all of the included device groups and none of the excluded device groups. If no policies apply, then the default enforcement is applied.
By default device control is disabled, so access to all types of devices is allowed. To learn more about device control, see Device control in Microsoft Defender for Endpoint.
Controlling default behavior
When device control is enabled, it's enabled for all device types by default. The default enforcement can also be changed from Allow to Deny. Your security team can also configure the types of devices that device control protects. The following table below illustrates how various combinations of settings change the access control decision.
| Is device control enabled? | Default behavior | Device types |
|---|---|---|
| No | Access is allowed | - CD/DVD drives - Printers - Removable media devices - Windows portable devices |
| Yes | (Not specified) Access is allowed |
- CD/DVD drives - Printers - Removable media devices - Windows portable devices |
| Yes | Deny | - CD/DVD drives - Printers - Removable media devices - Windows portable devices |
| Yes | Deny removable media devices and printers | - Printers and removable media devices (blocked) - CD/DVD drives and Windows portable devices (allowed) |
When device types are configured, device control in Defender for Endpoint ignores requests to other device families.
For more information, see the following articles:
Policies
To further refine access to devices, device control uses policies. A policy is a set of rules and groups. How rules and groups are defined varies slightly among management experiences and operating systems, as described in the following table.
| Management tool | Operating system | How rules and groups are managed |
|---|---|---|
| Intune – Device control policy | Windows | Device and printer groups can be managed as reusable settings and included in rules. Not all features are available in the device control policy (see Deploy and manage device control with Microsoft Intune) |
| Intune – Custom | Windows | Each group/rule is stored as an XML string in custom configuration policy. The OMA-URI contains the GUID of the group/rule. The GUID must be generated. |
| Group Policy | Windows | The groups and rules are defined in separate XML settings in the Group Policy Object (see Deploy and manage device control with Group Policy). |
| Intune | Mac | The rules and policies are combined into a single JSON and included in the mobileconfig file that is deployed by using Intune |
| JAMF | Mac | The rules and policies are combined into a single JSON and configured by using JAMF as the device control policy (see Device Control for macOS) |
Rules and groups are identified by Global Unique ID (GUIDs). If device control policies are deployed using a management tool other than Intune, the GUIDs must be generated. You can generate the GUIDs by using PowerShell.
For schema details, see JSON schema for Mac.
Users
Device control policies can be applied to users and/or user groups.
Note
In the articles related to device control, groups of users are referred to as user groups. The term groups refer to groups defined in the device control policy.
Using Intune, on either Mac and Windows, device control policies can be targeted to user groups defined in Entra Id.
On Windows, a user or user group can be a condition on an entry in a policy.
Entries with user or user groups can reference objects from either Entra Id or a local Active Directory.
Best practices for using device control with users and user groups
To create a rule for an individual user on Windows, create an entry with a
Sidcondition foreach user in a ruleTo create a rule for a user group on Windows and Intune, either create an entry with a
Sidcondition for each user group in a [rule] and target the policy to a machine group in Intune or create a rule without conditions and target the policy with Intune to the user group.On Mac, use Intune and target the policy to a user group in Entra Id.
Warning
Do not use both user/user group conditions in rules and user group targeting in Intune.
Note
If network connectivity is an issue, use Intune user group targeting or a local Active Directory groups. User/user group conditions that reference Entra Id should only be used in environments that have a reliable connection to Entra Id.
Rules
A rule defines the list of included groups and a list of excluded groups. For the rule to apply, the device must be in all of the included groups and none of the excluded groups. If the device matches the rule, then the entries for that rule are evaluated. An entry defines the action and notification options applied, if the request matches the conditions. If no rules apply or no entries match the request then the default enforcement is applied.
For example, to allow write access for some USB devices, and read access for all other USB devices, use the following policies, groups, and entries with default enforcement set to deny.
| Group | Description |
|---|---|
| All Removable Storage Devices | Removable Storage Devices |
| Writeable USBs | List of USBs where write access is permitted |
| Rule | Included Device Groups | Excluded Device Groups | Entry |
|---|---|---|---|
| Read only access for USBs | All Removable storage devices | Writeable USBs | Read Only Access |
| Write access for USBs | Writeable USBs | Write Access |
The name of the rule appears in the portal for reporting and in the toast notification to users, so make sure to give the rules descriptive names.
You can configure rules by editing policies in Intune, using an XML file in Windows, or using a JSON file on Mac. Select each tab for more details.
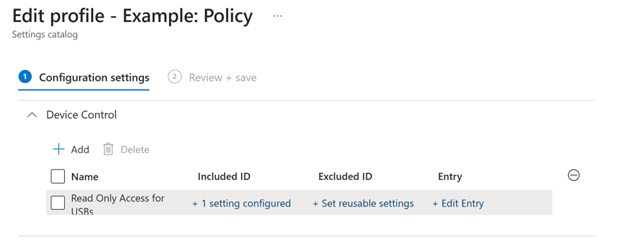
The following image depicts configuration settings for a device control policy in Intune:
In the screenshot, the Included ID and Excluded ID are the references to included and excluded reusable settings groups. A policy can have multiple rules.
Intune doesn't honor the ordering of the rules. The rules can be evaluated in any order, so make sure to explicitly exclude groups of devices that aren't in scope for the rule.
Entries
Device control policies define access (called an entry) for a set of devices. Entries define the action and notification options for devices that match the policy and the conditions defined in the entry.
| Entry setting | Options |
|---|---|
| AccessMask | Applies the action only if the access operations match the access mask - The access mask is the bit-wise OR of the access values: 1 - Device Read 2 - Device Write 4 - Device Execute 8 - File Read 16 - File Write 32 - File Execute 64 - Print For example: Device Read, Write, and Execute = 7 (1+2+4) Device Read, Disk Read = 9 (1+8) |
| Action | Allow Deny AuditAllow AuditDeny |
| Notification | None (default) An event is generated The user receives notification |
Entry evaluation
There are two types of entries: enforcement entries (Allow/Deny) and audit entries (AuditAllow/AuditDeny).
Enforcement entries for a rule are evaluated in order until all of the requested permissions have been matched. If no entries match a rule, then the next rule is evaluated. If no rules match, then the default is applied.
Audit entries
Audit events control the behavior when device control enforces a rule (allow/deny). Device control can display a notification to the end-user. The user gets a notification that contains the name of the device control policy and the name of the device. The notification appears once every hour after initial access is denied.
Device control can also create an event that is available in Advanced Hunting.
Important
There is a limit of 300 events per device per day. Audit entries are processed after the enforcement decision has been made. All corresponding audit entries are evaluated.
Conditions
An entry supports the following optional conditions:
- User/User Group Condition: Applies the action only to the user/user group identified by the SID
Note
For user groups and users that are stored in Microsoft Entra Id, use the object id in the condition. For user groups and users that are stored locally, use the Security Identifier (SID)
Note
On Windows, The SID of the user who's signed in can be retrieved by running the PowerShell command whoami /user.
- Machine Condition: Applies the action only to the device/group identified by the SID
- Parameters Condition: Applies the action only if the parameters match (See Advanced Conditions)
Entries can be further scoped to specific users and devices. For example, allow read access to these USBs for this user only on this device.
| Policy | Included Device Groups | Excluded Device Groups | Entry(ies) |
|---|---|---|---|
| Read only access for USBs | All Removable storage devices | Writeable USBs | Read Only Access |
| Write access for USBs | Writeable USBs | Write Access for User 1 Write Access for User 2 on Device Group A |
All of the conditions in the entry must be true for the action to be applied.
You can configure entries using Intune, an XML file in Windows, or a JSON file on Mac. Select each tab for more details.
In Intune, the Access mask field has options, such as:
- Read (Disk Level Read = 1)
- Write (Disk Level Write = 2)
- Execute (Disk Level Execute = 4)
- Print (Print = 64).
Not all features are shown in the Intune user interface. For more information, see Deploy and manage device control with Intune.
Groups
Groups define criteria for filtering objects by their properties. The object is assigned to the group if its properties match the properties defined for the group.
Note
Groups in this section do not refer to user groups.
For example:
- Allowed USBs are all the devices that match any of these manufacturers
- Lost USBs are all the devices that match any of these serial numbers
- Allowed printers are all the devices that match any of these VID/PID
The properties can be matched in four ways: MatchAll, MatchAny, MatchExcludeAll, and MatchExcludeAny
MatchAll: The properties are an "And" relationship; for example, if administrator putsDeviceIDandInstancePathID, for every connected USB, the system checks to see whether the USB meets both values.MatchAny: The properties are an "Or" relationship; for example, if administrator puts DeviceID andInstancePathID, for every connected USB, the system enforces as long as the USB has either an identicalDeviceIDorInstanceIDvalue.MatchExcludeAll: The properties are an "And" relationship, any items that do NOT meet are covered. For example, if administrator putsDeviceIDandInstancePathIDand usesMatchExcludeAll, for every connected USB, system enforces as long as the USB doesn't have both identicalDeviceIDandInstanceIDvalue.MatchExcludeAny: The properties are an "Or" relationship, any items that do NOT meet are covered. For example, if administrator putsDeviceIDandInstancePathIDand usesMatchExcludeAny, for every connected USB, system enforces as long as the USB doesn't have either an identicalDeviceIDorInstanceIDvalue.
Groups are used two ways: to select devices for inclusion/exclusion in rules, and to filter access for advanced conditions. This table summarizes the group types and how they're used.
| Type | Description | O/S | Include/Exclude Rules | Advanced conditions |
|---|---|---|---|---|
| Device (default) | Filter devices and printers | Windows/Mac | X | |
| Network | Filter network conditions | Windows | X | |
| VPN Connection | Filter VPN conditions | Windows | X | |
| File | Filter file properties | Windows | X | |
| Print Job | Filter properties of the file being printed | Windows | X |
The devices that are in scope for the policy determined by a list of included groups and a list of excluded groups. A rule applies if the device is in all of the included groups and none of the excluded groups. Groups can be composed from the properties of devices. The following properties can be used:
| Property | Description | Windows devices | Mac devices | Printers |
|---|---|---|---|---|
FriendlyNameId |
The friendly name in Windows Device Manager | Y | N | Y |
PrimaryId |
The type of the device | Y | Y | Y |
VID_PID |
Vendor ID is the four-digit vendor code that the USB committee assigns to the vendor. Product ID is the four-digit product code that the vendor assigns to the device. Wildcards are supported. For example, 0751_55E0 |
Y | N | Y |
PrinterConnectionId |
The type of printer connection: - USB: A printer connected through USB port of a computer. - Network: A network printer is a printer that is accessible by network connection, making it usable by other computers connected to the network.- Corporate: A corporate printer is a print queue shared through on-premise Windows Print Server.- Universal: Universal Print is a modern print solution that organizations can use to manage their print infrastructure through cloud services from Microsoft. What is Universal Print? - Universal Print | Microsoft Docs - File: 'Microsoft Print to PDF' and 'Microsoft XPS Document Writer' or other printers using a FILE: or PORTPROMPT: port- Custom: printer that is not connecting through Microsoft print port- Local: printer not any of above type, e.g. print through RDP or redirect printers |
N | N | Y |
BusId |
Information about the device (for more information, see the sections that follow this table) | Y | N | N |
DeviceId |
Information about the device (for more information, see the sections that follow this table) | Y | N | N |
HardwareId |
Information about the device (for more information, see the sections that follow this table) | Y | N | N |
InstancePathId |
Information about the device (for more information, see the sections that follow this table) | Y | N | N |
SerialNumberId |
Information about the device (for more information, see the sections that follow this table) | Y | Y | N |
PID |
Product ID is the four-digit product code that the vendor assigns to the device | Y | Y | N |
VID |
Vendor ID is the four-digit vendor code that the USB committee assigns to the vendor. | Y | Y | N |
DeviceEncryptionStateId |
(Preview) The BitLocker encryption state of a device. Valid values are BitlockerEncrypted or Plain |
Y | N | N |
APFS Encrypted |
If the device is APFS encrypted | N | Y | N |
Using Windows Device Manager to determine device properties
For Windows devices, you can use Device Manager to understand the properties of devices.
Open Device Manager, locate the device, right-click on Properties, and then select the Details tab.
In the Property list, select Device instance path.
The value shown for device instance path is the
InstancePathId, but it also contains other properties:USB\VID_090C&PID_1000\FBH1111183300721{BusId}\{DeviceId}\{SerialNumberId}
The properties in the device manager map to device control as shown in the following table:
Device Manager Device Control Hardware Ids HardwareIdFriendly name FriendlyNameIdParent VID_PIDDeviceInstancePath InstancePathId
Using reports and advanced hunting to determine properties of devices
Device properties have slightly different labels in advanced hunting. The table below maps the labels in the portal to the propertyId in a device control policy.
| Microsoft Defender Portal property | Device control property Id |
|---|---|
| Media name | FriendlyNameId |
| Vendor Id | HardwareId |
| DeviceId | InstancePathId |
| Serial Number | SerialNumberId |
Note
Make sure that the object selected has the correct Media Class for the policy. In general, for removable storage, use Class Name == USB.
Configure groups in Intune, XML in Windows, or JSON on Mac
You can configure groups in Intune, by using an XML file for Windows, or by using a JSON file on Mac. Select each tab for more details.
Note
The Group Id in XML and id in JSON is used to identify the group within device control. Its not a reference to any other such as a user group in Entra Id.
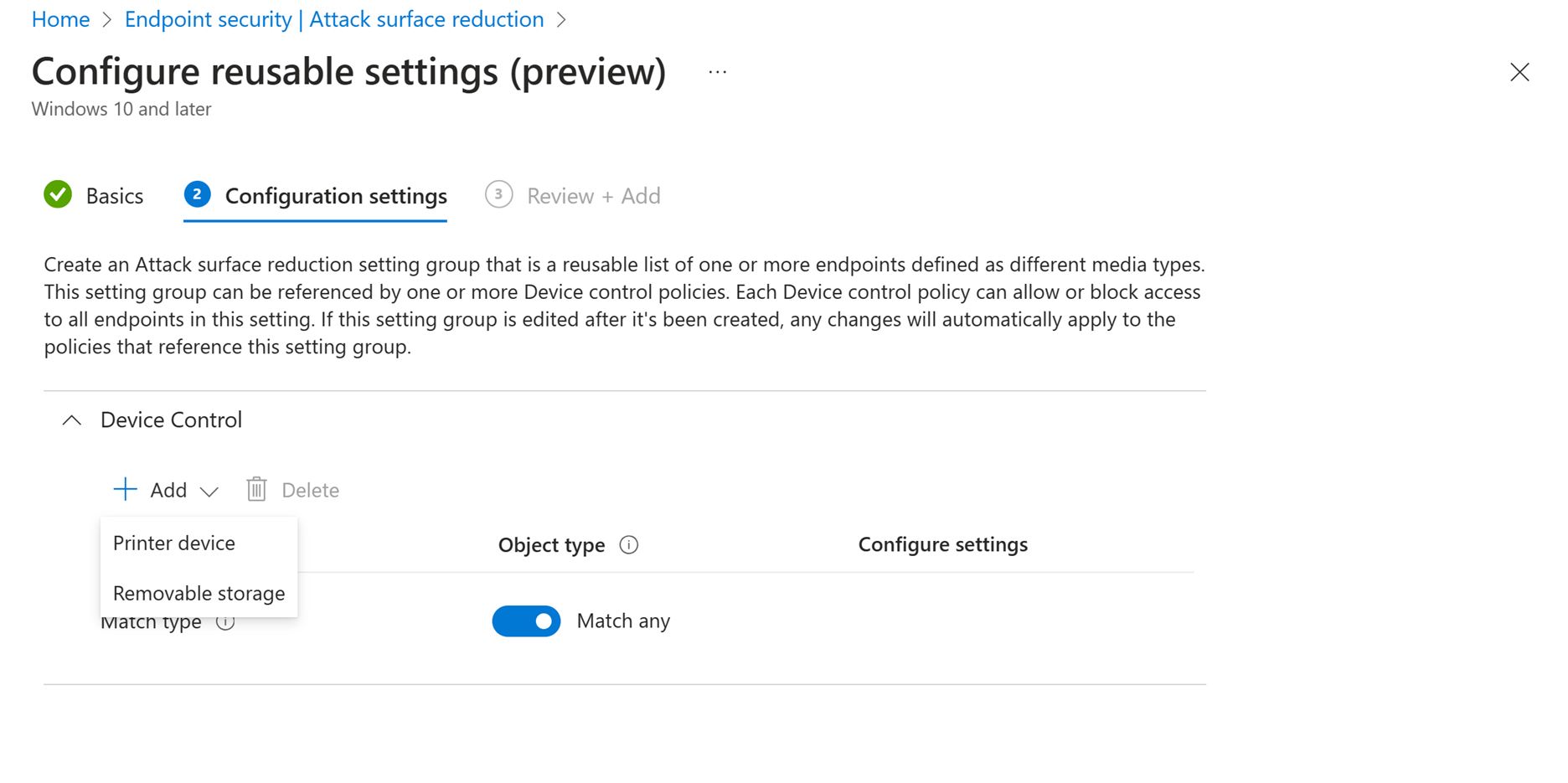
Reusable settings in Intune map to device groups. You can configure reusable settings in Intune.
There are two types of groups: Printer Device and Removable Storage. The following table lists the properties for these groups.
| Group type | Properties |
|---|---|
| Printer device | - FriendlyNameId- PrimaryId- PrinterConnectionId- VID_PID |
| Removable storage | - BusId - DeviceId- FriendlyNameId- HardwareId- InstancePathId- PID- PrimaryId- SerialNumberId- VID- VID_PID |
Advanced conditions
Entries can be further restricted based on parameters. Parameters apply advanced conditions that go beyond the device. Advanced conditions allow for fine-grained control based on Network, VPN Connection, File or Print Job being evaluated.
Note
Advanced conditions are only supported in the XML format.
Network Conditions
The following table describes network group properties:
| Property | Description |
|---|---|
NameId |
The name of the network. Wildcards are supported. |
NetworkCategoryId |
Valid options are Public, Private, or DomainAuthenticated. |
NetworkDomainId |
Valid options are NonDomain, Domain, DomainAuthenticated. |
These properties are added to the DescriptorIdList of a group of type Network. Here's an example snippet:
<Group Id="{e5f619a7-5c58-4927-90cd-75da2348a30a}" Type="Network" MatchType="MatchAll">
<DescriptorIdList>
<NetworkCategoryId>Public</PathId>
<NetworkDomainId>NonDomain</PathId>
</DescriptorIdList>
</Group>
The group is then referenced as parameters in the entry, as illustrated in the following snippet:
<Entry Id="{1ecfdafb-9b7f-4b66-b3c5-f1d872b0961d}">
<Type>Deny</Type>
<Options>0</Options>
<AccessMask>40</AccessMask>
<Parameters MatchType="MatchAll">
<Network MatchType="MatchAny">
<GroupId>{ e5f619a7-5c58-4927-90cd-75da2348a30a }</GroupId>
</Network>
</Parameters>
</Entry>
VPN Connection Conditions
The following table describes VPN connection conditions:
| Name | Description |
|---|---|
NameId |
The name of the VPN Connection. Wildcards are supported. |
VPNConnectionStatusId |
Valid values are Connected or Disconnected. |
VPNServerAddressId |
The string value of VPNServerAddress. Wildcards are supported. |
VPNDnsSuffixId |
The string value of VPNDnsSuffix. Wildcards are supported. |
These properties are added to the DescriptorIdList of a group of type VPNConnection, as shown in the following snippet:
<Group Id="{d633d17d-d1d1-4c73-aa27-c545c343b6d7}" Type="VPNConnection">
<Name>Corporate VPN</Name>
<MatchType>MatchAll</MatchType>
<DescriptorIdList>
<NameId>ContosoVPN</NameId>
<VPNServerAddressId>contosovpn.*.contoso.com</VPNServerAddressId>
<VPNDnsSuffixId>corp.contoso.com</VPNDnsSuffixId>
<VPNConnectionStatusId>Connected</VPNConnectionStatusId>
</DescriptorIdList>
</Group>
Then the group is then referenced as parameters in an entry, as illustrated in the following snippet:
<Entry Id="{27c79875-25d2-4765-aec2-cb2d1000613f}">
<Type>Allow</Type>
<Options>0</Options>
<AccessMask>64</AccessMask>
<Parameters MatchType="MatchAny">
<VPNConnection>
<GroupId>{d633d17d-d1d1-4c73-aa27-c545c343b6d7}</GroupId>
</VPNConnection>
</Parameters>
</Entry>
The group is then referenced as parameters in an entry, as illustrated in the following snippet:
<Entry Id="{1ecfdafb-9b7f-4b66-b3c5-f1d872b0961d}">
<Type>Deny</Type>
<Options>0</Options>
<AccessMask>40</AccessMask>
<Parameters MatchType="MatchAll">
<File MatchType="MatchAny">
<GroupId>{ e5f619a7-5c58-4927-90cd-75da2348a30f }</GroupId>
</File>
</Parameters>
</Entry>
Print Job Conditions
The following table describes PrintJob group properties:
| Name | Description |
|---|---|
PrintOutputFileNameId |
The output destination file path for print to file. Wildcards are supported. For example, C:\*\Test.pdf |
PrintDocumentNameId |
The source file path. Wildcards are supported. This path might not exist. For example, add text to a new file in Notepad, and then print without saving the file. |
These properties are added to the DescriptorIdList of a group of type PrintJob, as illustrated in the following snippet:
<Group Id="{e5f619a7-5c58-4927-90cd-75da2348a30b}" Type="PrintJob" MatchType="MatchAny">
<DescriptorIdList>
<PrintOutputFileNameId>C:\Documents\*.pdf</PrintOutputFileNameId >
<PrintDocumentNameId>*.xlsx</PrintDocumentNameId>
<PrintDocumentNameId>*.docx</PrintDocumentNameId>
</DescriptorIdList>
</Group>
The group is then referenced as parameters in an entry, as illustrated in the following snippet:
<Entry Id="{1ecfdafb-9b7f-4b66-b3c5-f1d872b0961d}">
<Type>Deny</Type>
<Options>0</Options>
<AccessMask>40</AccessMask>
<Parameters MatchType="MatchAll">
<PrintJob MatchType="MatchAny">
<GroupId>{e5f619a7-5c58-4927-90cd-75da2348a30b}</GroupId>
</PrintJob>
</Parameters>
</Entry>