Manage tamper protection for your organization using Microsoft Defender portal
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender Antivirus
- Microsoft Defender for Business
- Microsoft 365 Business Premium
Platforms
- Windows
Tamper protection helps protect certain security settings, such as virus and threat protection, from being disabled or changed. If you're part of your organization's security team, you can turn tamper protection on (or off) tenant wide by using the Microsoft Defender portal (https://security.microsoft.com).
Important
If tamper protection is deployed and managed through Intune, turning tamper protection on or off in the Microsoft Defender portal won't impact the state of tamper protection. It restricts tamper-protected settings to their secure default values. For more information, see What happens when tamper protection is turned on?
Requirements for managing tamper protection in the Microsoft Defender portal
You must have appropriate permissions assigned through roles, such as Global Administrator or Security Administrator. (See Microsoft Defender XDR role-based access control (RBAC).)
Devices must be running certain versions of Windows or macOS. (See On what devices can tamper protection be enabled?)
Devices must be onboarded to Microsoft Defender for Endpoint.
Devices must be using anti-malware platform version
4.18.2010.7(or above) and anti-malware engine version1.1.17600.5(or above). (Manage Microsoft Defender Antivirus updates and apply baselines.)Cloud-delivered protection must be turned on.
Note
When tamper protection is enabled via the Microsoft Defender portal, cloud-delivered protection is required so that the enabled state of tamper protection can be controlled. Starting with the November 2021 update (platform version 4.18.2111.5), if cloud-delivered protection is not already turned on for a device, when tamper protection is turned on, cloud-delivered protection is turned on automatically on the device.
Turn tamper protection on (or off) in the Microsoft Defender portal
Go to the Microsoft Defender portal (https://security.microsoft.com) and sign in.
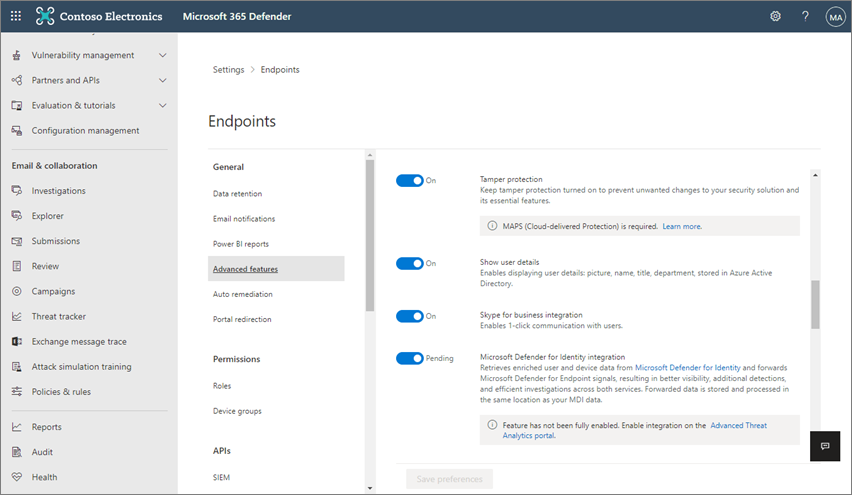
Choose Settings > Endpoints.
Go to General > Advanced features, and then turn tamper protection on.
Important points to keep in mind
Currently, the option to manage tamper protection in the Microsoft Defender portal is on by default for new deployments, as part of built-in protection, which helps guard against ransomware. For existing deployments, tamper protection is available on an opt-in basis. To opt in, in the Microsoft Defender portal, choose Settings > Endpoints > Advanced features > Tamper protection.
When you enable tamper protection in the Microsoft Defender portal, the setting is applied tenant wide and restricts tamper-protected settings to their secure defaults. Any changes made to tamper-protected settings are ignored. Depending on your particular scenario, you have several options available:
If you must make changes to a device and those changes are blocked by tamper protection, you can use troubleshooting mode to temporarily disable tamper protection on the device.
You can use Intune or Configuration Manager to exclude devices from tamper protection.
If you're managing tamper protection through Intune and certain other conditions are met, you can manage tamper-protected antivirus exclusions.
See also
- Built-in protection helps guard against ransomware
- What happens when tamper protection is turned on?
- Defender for Endpoint on non-Windows devices
- Troubleshoot problems with tamper protection
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.