Use shared queries in advanced hunting
Advanced hunting queries can be shared among users in the same organization. You can also save queries that are only accessible to you. You can also find community queries that are shared publicly on GitHub. These saved queries let you quickly pursue specific threat hunting scenarios without having to write queries from scratch.
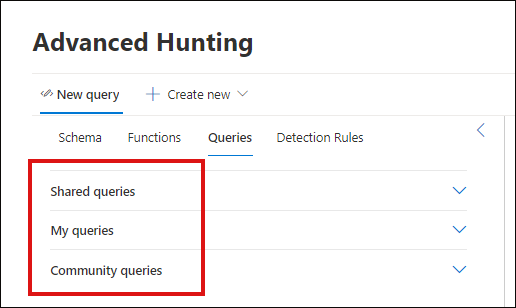
Under the Queries tab in advanced hunting, you can find the drop-down menus for Shared queries, My queries, and Community queries. You can select a downward-facing arrow to expand a menu.
Save, modify, and share a query
You can save a new or existing query so that it is only accessible to you or shared with other users in your organization.
Create or modify a query.
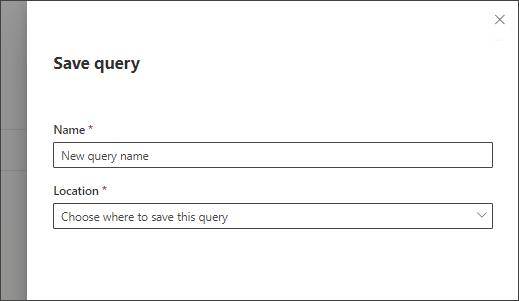
Click the Save query drop-down button and select Save as.
Enter a name for the query.
Select the folder where you'd like to save the query.
- Shared queries — shared to all users your organization
- My queries — accessible only to you
Select Save.
Delete or rename a query
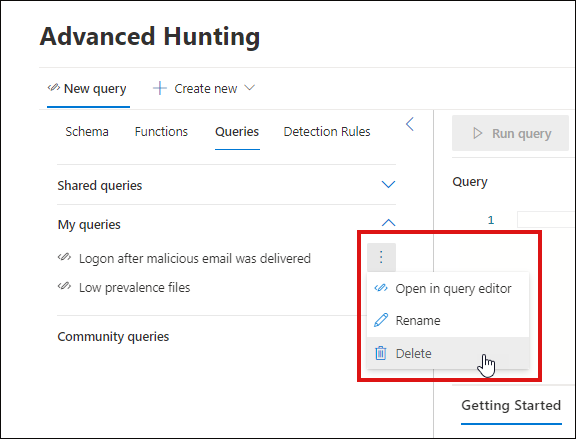
Select the three dots to the right of a query you want to rename or delete.
Select Delete and confirm deletion. Or select Rename and provide a new name for the query.
Create a direct link to a query
To generate a link that opens your query directly in the advanced hunting query editor, finalize your query and select Share link.
Access community queries in the GitHub repo
Microsoft security researchers regularly share advanced hunting queries in a designated public repository on GitHub. Contributions to this repository are reviewed before getting published. To contribute, join GitHub for free.
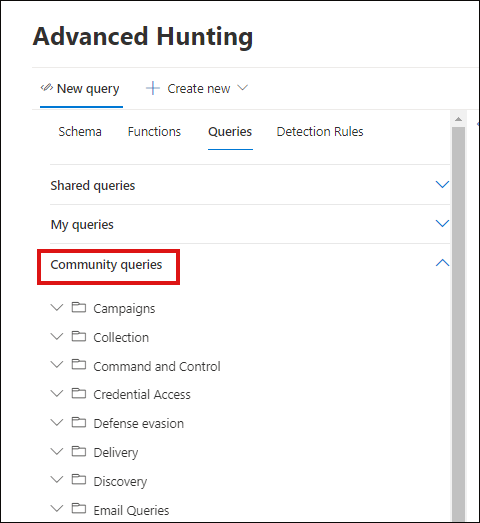
You can easily find these queries in the Community queries drop-down menu as well.
Community queries are grouped into folders like Campaigns, Collection, Defense evasion, and the like. Further information about the query is provided as in-line comments in the query itself.
Tip
Microsoft security researchers also provide advanced hunting queries that you can use to locate activities and indicators associated with emerging threats. These queries are provided as part of the threat analytics reports in Microsoft Defender XDR.
Related topics
- Advanced hunting overview
- Learn the query language
- Work with query results
- Hunt across devices, emails, apps, and identities
- Understand the schema
- Apply query best practices
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.