Tutorial: Microsoft Entra single sign-on (SSO) integration with GitHub Enterprise Managed User
In this tutorial, you'll learn how to integrate GitHub Enterprise Managed User (EMU) with Microsoft Entra ID. When you integrate GitHub Enterprise Managed User with Microsoft Entra ID, you can:
- Control in Microsoft Entra ID who has access to GitHub Enterprise Managed User.
- Enable your users to be automatically signed-in to GitHub Enterprise Managed User with their Microsoft Entra accounts.
- Manage your accounts in one central location.
Note
GitHub Enterprise Managed Users is a feature of GitHub Enterprise Cloud which is different from GitHub Enterprise's standard SAML SSO implementation. If you haven't specifically requested EMU instance, you have standard GitHub Enterprise Cloud plan. In that case, please refer to relevant documentation to configure your non-EMU organisation or enterprise account to authenticate with Microsoft Entra ID.
Prerequisites
To get started, you need the following items:
- A Microsoft Entra subscription. If you don't have a subscription, you can get a free account.
- GitHub Enterprise Managed User single sign-on (SSO) enabled subscription.
Scenario description
In this tutorial, you configure and test Microsoft Entra SSO in a test environment.
- GitHub Enterprise Managed User supports both SP and IDP initiated SSO.
- GitHub Enterprise Managed User requires Automated user provisioning.
Adding GitHub Enterprise Managed User from the gallery
To configure the integration of GitHub Enterprise Managed User into Microsoft Entra ID, you need to add GitHub Enterprise Managed User from the gallery to your list of managed SaaS apps.
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Identity > Applications > Enterprise applications > New application.
- Type GitHub Enterprise Managed User in the search box.
- Select GitHub Enterprise Managed User from results panel and then click on the Create button. Wait a few seconds while the app is added to your tenant.
Alternatively, you can also use the Enterprise App Configuration Wizard. In this wizard, you can add an application to your tenant, add users/groups to the app, assign roles, as well as walk through the SSO configuration as well. Learn more about Microsoft 365 wizards.
Configure and test Microsoft Entra SSO for GitHub Enterprise Managed User
To configure and test Microsoft Entra SSO with GitHub Enterprise Managed User, perform the following steps:
- Configure Microsoft Entra SSO - to enable SAML Single Sign On in your Microsoft Entra tenant.
- Configure GitHub Enterprise Managed User SSO - to configure the single sign-on settings in your GitHub Enterprise.
Configure Microsoft Entra SSO
Follow these steps to enable Microsoft Entra SSO.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > GitHub Enterprise Managed User > Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, click the pencil icon for Basic SAML Configuration to edit the settings.
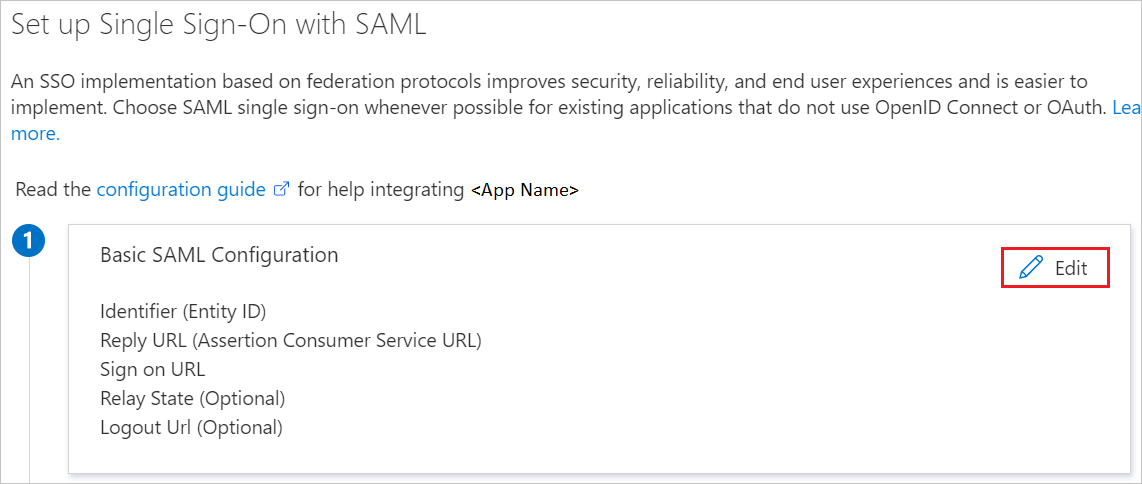
Ensure that you have your Enterprise URL before you begin. The ENTITY field mentioned below is the Enterprise name of your EMU-enabled Enterprise URL. For example, https://github.com/enterprises/contoso - contoso is the ENTITY. On the Basic SAML Configuration section, if you wish to configure the application in IDP initiated mode, enter the values for the following fields:
a. In the Identifier text box, type a URL using the following pattern:
https://github.com/enterprises/<ENTITY>Note
Note the identifier format is different from the application's suggested format - please follow the format above. In addition, please ensure the **Identifier does not contain a trailing slash.
b. In the Reply URL text box, type a URL using the following pattern:
https://github.com/enterprises/<ENTITY>/saml/consumeClick Set additional URLs and perform the following step if you wish to configure the application in SP initiated mode:
In the Sign-on URL text box, type a URL using the following pattern:
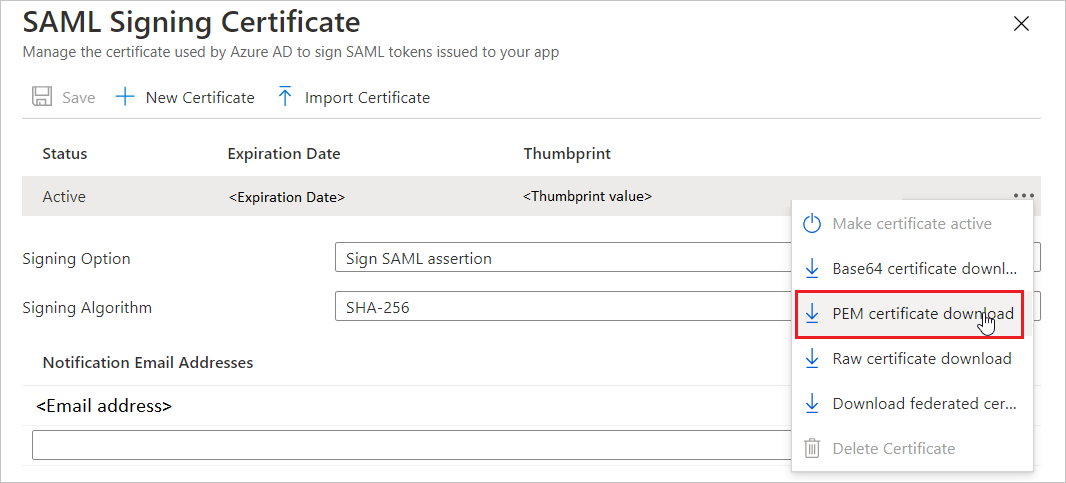
https://github.com/enterprises/<ENTITY>/ssoOn the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (PEM) and select PEM certificate download to download the certificate and save it on your computer.
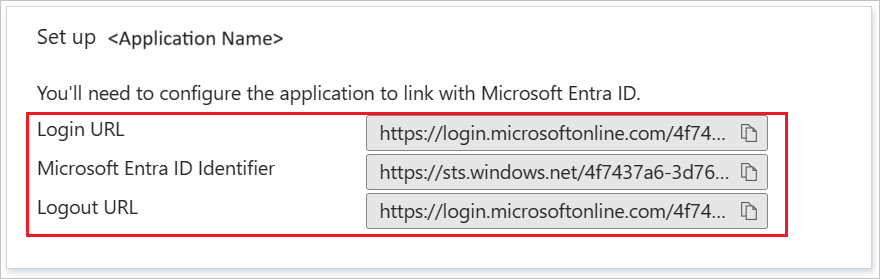
On the Set up GitHub Enterprise Managed User section, copy the URLs below and save it for configuring GitHub below.
Assign the Microsoft Entra test user
In this section, you'll assign your account to GitHub Enterprise Managed User in order to complete SSO setup.
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Identity > Applications > Enterprise applications > GitHub Enterprise Managed User.
- In the app's overview page, find the Manage section and select Users and groups.
- Select Add user, then select Users and groups in the Add Assignment dialog.
- In the Users and groups dialog, select your account from the Users list, then click the Select button at the bottom of the screen.
- In the Select a role dialog, select the Enterprise Owner role, then click the Select button at the bottom of the screen. Your account is assigned as an Enterprise Owner for your GitHub instance when you provision your account in the next tutorial.
- In the Add Assignment dialog, click the Assign button.
Configure GitHub Enterprise Managed User SSO
To configure single sign-on on GitHub Enterprise Managed User side, you will require the following items:
- The URLs from your Microsoft Entra Enterprise Managed User Application above: Login URL; Microsoft Entra Identifier; and Logout URL
- The account name and password for the first administrator user of your GitHub Enterprise. The credentials are provided by a password reset email from your GitHub Solutions Engineering contact.
Enable GitHub Enterprise Managed User SAML SSO
In this section, you'll take the information provided from Microsoft Entra ID above and enter them into your Enterprise settings to enable SSO support.
- Go to https://github.com
- Click on Sign In at the top-right corner
- Enter the credentials for the first administrator user account. The login handle should be in the format:
<your enterprise short code>_admin - Navigate to
https://github.com/enterprises/<your enterprise name>. This information should be provided by your Solutions Engineering contact. - On the navigation menu on the left, select Settings, then Authentication security.
- Click on the checkbox Require SAML authentication
- Enter the Sign-on URL. This URL is the Login URL that you copied from Microsoft Entra ID above.
- Enter the Issuer. This URL is the Microsoft Entra Identifier that you copied from Microsoft Entra ID above.
- Enter the Public Certificate. Please open the base64 certificate that you downloaded above and paste the text contents of that file into this dialog.
- Click on Test SAML configuration. This will open up a dialog for you to log in with your Microsoft Entra credentials to validate that SAML SSO is configured correctly. Log in with your Microsoft Entra credentials. you will receive a message Passed: Successfully authenticated your SAML SSO identity upon successful validation.
- Click Save to persist these settings.
- Please save (download, print, or copy) the recovery codes in a secure place.
- Click on Enable SAML authentication.
- At this point, only accounts with SSO are able to log into your Enterprise. Follow the instructions in the document below on provisioning in order to provision accounts backed by SSO.
Next steps
GitHub Enterprise Managed User requires all accounts to be created through automatic user provisioning, you can find more details here on how to configure automatic user provisioning.