Deploy your identity infrastructure for Microsoft 365
Check out all of our small business content on Small business help & learning.
In Microsoft 365 for enterprise, a well-planned and executed identity infrastructure paves the way for stronger security, including restricting access to your productivity workloads and their data to only authenticated users and devices. Security for identities is a key element of a Zero Trust deployment, in which all attempts to access resources both on-premises and in the cloud are authenticated and authorized.
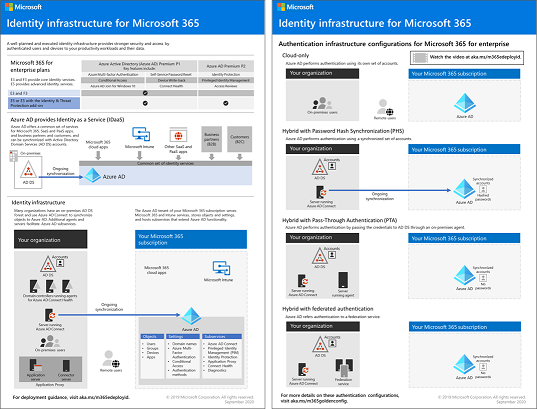
For information about the identity features of each Microsoft 365 for enterprise, the role of Microsoft Entra ID, on-premises and cloud-based components, and the most common authentication configurations, see the Identity Infrastructure poster.
Review this two-page poster to quickly ramp up on identity concepts and configurations for Microsoft 365 for enterprise.
You can download this poster and can print it in letter, legal, or tabloid (11 x 17) format.
This solution is the first step to build out the Microsoft 365 Zero Trust deployment stack.
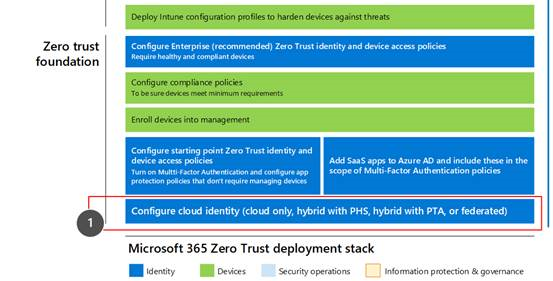
For more information, see the Microsoft 365 Zero Trust deployment plan.
What’s in this solution
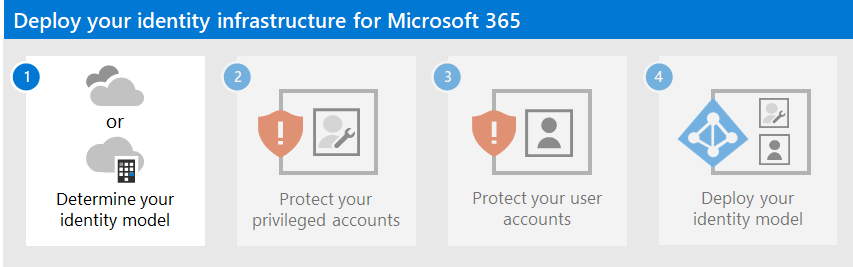
This solution steps you through the deployment of an identity infrastructure for your Microsoft 365 tenant to provide access for your employees and protection against identity-based attacks.
The steps in this solution are:
- Determine your identity model.
- Protect your Microsoft 365 privileged accounts.
- Protect your Microsoft 365 user accounts.
- Deploy your identity model.
This solution supports the key principles of Zero Trust:
- Verify explicitly: Always authenticate and authorize based on all available data points.
- Use least privilege access: Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection.
- Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Unlike conventional intranet access, which trusts everything behind an organization's firewall, Zero Trust treats each sign-in and access as though it originated from an uncontrolled network, whether it's behind the organization firewall or on the Internet. Zero Trust requires protection for the network, infrastructure, identities, endpoints, apps, and data.
Microsoft 365 capabilities and features
Microsoft Entra ID provides a full suite of identity management and security capabilities for your Microsoft 365 tenant.
| Capability or feature | Description | Licensing |
|---|---|---|
| Multifactor authentication (MFA) | MFA requires users to provide two forms of verification, such as a user password plus a notification from the Microsoft Authenticator app or a phone call. MFA greatly reduces the risk that stolen credentials can be used to access your environment. Microsoft 365 uses the Microsoft Entra multifactor authentication service for MFA-based sign-ins. | Microsoft 365 E3 or E5 |
| Conditional Access | Microsoft Entra ID evaluates the conditions of the user sign-in and uses Conditional Access policies to determine the allowed access. For example, in this guidance we show you how to create a Conditional Access policy to require device compliance for access to sensitive data. This greatly reduces the risk that a hacker with their own device and stolen credentials can access your sensitive data. It also protects sensitive data on the devices, because the devices must meet specific requirements for health and security. | Microsoft 365 E3 or E5 |
| Microsoft Entra groups | Conditional Access policies, device management with Intune, and even permissions to files and sites in your organization rely on the assignment to user accounts or Microsoft Entra groups. We recommend you create Microsoft Entra groups that correspond to the levels of protection you're implementing. For example, members of your executive staff are likely higher value targets for hackers. Therefore, it makes sense to add the user accounts of these employees to a Microsoft Entra group and assign this group to Conditional Access policies and other policies that enforce a higher level of protection for access. | Microsoft 365 E3 or E5 |
| Microsoft Entra ID Protection | Enables you to detect potential vulnerabilities affecting your organization's identities and configure automated remediation policy to low, medium, and high sign-in risk and user risk. This guidance relies on this risk evaluation to apply Conditional Access policies for multifactor authentication. This guidance also includes a Conditional Access policy that requires users to change their password if high-risk activity is detected for their account. | Microsoft 365 E5, Microsoft 365 E3 with the E5 Security add-on, EMS E5, or Microsoft Entra ID P2 licenses |
| Self-service password reset (SSPR) | Allow your users to reset their passwords securely and without help-desk intervention, by providing verification of multiple authentication methods that the administrator can control. | Microsoft 365 E3 or E5 |
| Microsoft Entra password protection | Detect and block known weak passwords and their variants and additional weak terms that are specific to your organization. Default global banned password lists are automatically applied to all users in a Microsoft Entra tenant. You can define additional entries in a custom banned password list. When users change or reset their passwords, these banned password lists are checked to enforce the use of strong passwords. | Microsoft 365 E3 or E5 |
Next steps
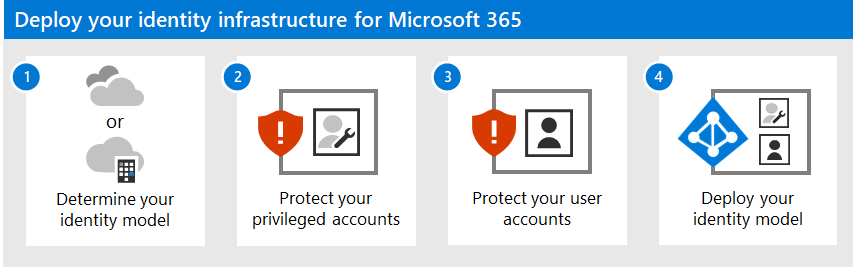
Use these steps to deploy an identity model and authentication infrastructure for your Microsoft 365 tenant:
- Determine your cloud identity model.
- Protect your Microsoft 365 privileged accounts.
- Protect your Microsoft 365 user accounts.
- Deploy your cloud identity model: cloud-only or hybrid.
Additional Microsoft cloud identity resources
Manage
To manage your Microsoft cloud identity deployment, see:
How Microsoft does identity for Microsoft 365
Learn how IT experts at Microsoft manage identities and secure access.
Note
This IT Showcase resource is available only in English.
How Contoso did identity for Microsoft 365
For an example of how a fictional but representative multinational organization has deployed a hybrid identity infrastructure for Microsoft 365 cloud services, see Identity for the Contoso Corporation.
คำติชม
เร็วๆ นี้: ตลอดปี 2024 เราจะขจัดปัญหา GitHub เพื่อเป็นกลไกคำติชมสำหรับเนื้อหา และแทนที่ด้วยระบบคำติชมใหม่ สำหรับข้อมูลเพิ่มเติม ให้ดู: https://aka.ms/ContentUserFeedback
ส่งและดูข้อคิดเห็นสำหรับ