 Visual Studio 2019 version 16.4 Release Notes
Visual Studio 2019 version 16.4 Release Notes
Developer Community | System Requirements | Compatibility | Distributable Code | Release History | License Terms | Blogs | Whats New in Visual Studio Docs
Note
This is not the latest version of Visual Studio. To download the latest release, please visit the Visual Studio site.
Support Timeframe
Visual Studio 2019 version 16.4 is now out of support.
Enterprise and Professional users of Visual Studio 2019 version 16.4 were supported and did receive fixes to security vulnerabilities through October 2021. This timeframe was determined by the fact that in August 2020, Visual Studio 2019 version 16.7 was designated as the next servicing baseline to the Visual Studio 2019 product. For more information about Visual Studio supported baselines, please review the support policy for Visual Studio 2019.
Refer to the latest version of the release notes or visit the Visual Studio site to download the latest supported version of Visual Studio 2019.
Visual Studio 2019 version 16.4 Releases
- October 12, 2021 — Visual Studio 2019 version 16.4.27
- September 14, 2021 — Visual Studio 2019 version 16.4.26
- August 10, 2021 — Visual Studio 2019 version 16.4.25
- July 13, 2021 — Visual Studio 2019 version 16.4.24
- June 08, 2021 — Visual Studio 2019 version 16.4.23
- May 11, 2021 — Visual Studio 2019 version 16.4.22
- April 13, 2021 — Visual Studio 2019 version 16.4.21
- March 09, 2021 — Visual Studio 2019 version 16.4.20
- February 10, 2021 — Visual Studio 2019 version 16.4.19
- February 09, 2021 — Visual Studio 2019 version 16.4.18
- January 12, 2021 — Visual Studio 2019 version 16.4.17
- December 08, 2020 — Visual Studio 2019 version 16.4.16
- November 10, 2020 — Visual Studio 2019 version 16.4.15
- October 13, 2020 — Visual Studio 2019 version 16.4.14
- September 8, 2020 — Visual Studio 2019 version 16.4.13
- August 11, 2020 — Visual Studio 2019 version 16.4.12
- July 14, 2020 — Visual Studio 2019 version 16.4.11
- June 09,2020 — Visual Studio 2019 version 16.4.10
- May 27, 2020 — Visual Studio 2019 version 16.4.9
- May 12, 2020 — Visual Studio 2019 version 16.4.8
- April 14, 2020 — Visual Studio 2019 version 16.4.7
- March 10, 2020 — Visual Studio 2019 version 16.4.6
- February 11, 2020 — Visual Studio 2019 version 16.4.5
- January 30, 2020 — Visual Studio 2019 version 16.4.4
- January 14, 2020 — Visual Studio 2019 version 16.4.3
- December 17, 2019 — Visual Studio 2019 version 16.4.2
- December 10, 2019 — Visual Studio 2019 version 16.4.1
- December 3, 2019 — Visual Studio 2019 version 16.4.0
Archived Release Notes
- Visual Studio 2019 version 16.3 Release Notes
- Visual Studio 2019 version 16.2 Release Notes
- Visual Studio 2019 version 16.1 Release Notes
- Visual Studio 2019 version 16.0 Release Notes
Visual Studio 2019 Blog
The Visual Studio 2019 Blog is the official source of product insight from the Visual Studio Engineering Team. You can find in-depth information about the Visual Studio 2019 releases in the following posts:
- 'Tis the Season for Visual Studio 2019 v16.4 Release
- Visual Studio 2019 v16.4 Preview 2, Fall Sports, and Pumpkin Spice
- .NET Core Support and More in Visual Studio 2019 version 16.3 - Update Now!
- Visual Studio 2019 version 16.3 Preview 2 and Visual Studio 2019 for Mac version 8.3 Preview 2 Released!
- Visual Studio 2019 version 16.2 and 16.3 Preview 1 now available
- Visual Studio 2019 version 16.2 Preview 2
- Visual Studio 2019 version 16.1 and Preview 16.2 Preview
- Visual Studio 2019: Code faster. Work smarter. Create the future.
See this full list of all Developer Community items taken in Visual Studio 2019 version 16.4
 Visual Studio 2019 version 16.4.27
Visual Studio 2019 version 16.4.27
released October 12, 2021
Top Issues Addressed in Visual Studio 2019 version 16.4.27
Security Advisory Notice
CVE-2021-1971 OpenSSL Denial of Service Vulnerability
A potential denial of service vulnerability exists in OpenSSL library, which is consumed by Git.
CVE-2021-3449 OpenSSL Denial of Service Vulnerability
A potential denial of service vulnerability exists in OpenSSL library, which is consumed by Git.
CVE-2021-3450 OpenSSL Denial of Service Vulnerability
A potential flag bypass exists in OpenSSL library, which is consumed by Git.
 Visual Studio 2019 version 16.4.26
Visual Studio 2019 version 16.4.26
released September 14, 2021
Top Issues Addressed in Visual Studio 2019 version 16.4.26
Security Advisory Notice
CVE-2021-26434 Visual Studio Incorrect Permission Assignment Privilege Escalation Vulnerability
A permission assignment vulnerability exists in Visual Studio after installing the Game development with C++ and selecting the Unreal Engine Installer workload. The system is vulnerable to LPE during the installation it creates a directory with write access to all users.
CVE-2021-36952 Visual Studio Remote Code Execution Vulnerability
A remote code execution vulnerability exists in Visual Studio when it improperly handles objects in memory. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the current user.
 Visual Studio 2019 version 16.4.25
Visual Studio 2019 version 16.4.25
released August 10, 2021
Top Issues Addressed in Visual Studio 2019 version 16.4.25
- Fixed an issue that affected command line execution of the update command. If the update fails the first time, a subsequent issuing of the update command now causes the update to resume the prior operation where it left off.
Security Advisory Notice
CVE-2021-26423 .NET Core Denial of Service Vulnerability
A denial of service vulnerability exists where .NET (Core) server applications providing WebSocket endpoints could be tricked into endlessly looping while trying to read a single WebSocket frame.
CVE-2021-34485 .NET Core Information Disclosure Vulnerability
An information disclosure vulnerability exists when dumps created by the tool to collect crash dumps and dumps on demand are created with global read permissions on Linux and macOS.
CVE-2021-34532 ASP.NET Core Information Disclosure Vulnerability
An information disclosure vulnerability exists in where a JWT token is logged if it cannot be parsed.
 Visual Studio 2019 version 16.4.24
Visual Studio 2019 version 16.4.24
released July 13, 2021
Top Issues Addressed in Visual Studio 2019 version 16.4.24
- .NET 3.1.117 SDK inserted into Visual Studio 2019.
 Visual Studio 2019 version 16.4.23
Visual Studio 2019 version 16.4.23
released June 08, 2021
Top Issues Fixed in Visual Studio 2019 version 16.4.23
Security Advisory Notice
CVE-2021-31957 ASP.NET Denial of Service Vulnerability
A denial of service vulnerability exists when ASP.NET Core improperly handles client disconnect.
 Visual Studio 2019 version 16.4.22
Visual Studio 2019 version 16.4.22
released May 11, 2021
Top Issues Fixed in Visual Studio 2019 version 16.4.22
- Fixed an issue causing updates to fail when an administrator creates a new layout of Visual Studio for deploying updates. The client machine update will fail since the layout has moved locations.
Security Advisory Notice
CVE-2021-27068 RCE possible when planting python.exe in nested folder
A remote code execution vulnerability exists when opening a workspace with python code and that workspace contains a python.exe in a scripts subfolder.
CVE-2021-31204 .NET Core Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists in .NET 5.0 and .NET Core 3.1 when a user runs a single file application on Operating Systems based on Linux or macOS.
 Visual Studio 2019 version 16.4.21
Visual Studio 2019 version 16.4.21
released April 13, 2021
Top Issues Fixed in Visual Studio 2019 version 16.4.21
Security Advisory Notice
CVE-2021-27064 Visual Studio Installer Elevation of Privilege Vulnerability
A remote code execution vulnerability exists when the Visual Studio installer executes the feedback client in an elevated state.
CVE-2021-28313 / CVE-2021-28321 / CVE-2021-28322 Diagnostics Hub Standard Collector Service Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Diagnostics Hub Standard Collector incorrectly handles data operations.
 Visual Studio 2019 version 16.4.20
Visual Studio 2019 version 16.4.20
released March 09, 2021
Top Issues Fixed in Visual Studio 2019 version 16.4.20
Security Advisory Notice
CVE-2021-21300 Git for Visual Studio Remote Code Execution Vulnerability
A remote code execution vulnerability exists when Visual Studio clones a malicious repository.
CVE-2021-26701 .NET Core Remote Code Execution Vulnerability
A remote code execution vulnerability exists in .NET 5 and .NET Core due to how text encoding is performed.
 Visual Studio 2019 version 16.4.19
Visual Studio 2019 version 16.4.19
released February 10, 2021
Top Issues Fixed in Visual Studio 2019 version 16.4.19
 Visual Studio 2019 version 16.4.18
Visual Studio 2019 version 16.4.18
released February 09, 2021
Top Issues Fixed in Visual Studio 2019 version 16.4.18
Security Advisory Notice
CVE-2021-1639 TypeScript Language Service Remote Code Execution Vulnerability
A remote code execution vulnerability exists when Visual Studio loads a malicious repository containing JavaScript or TypeScript code files.
CVE-2021-1721 .NET Core Denial of Service Vulnerability
A denial-of-service vulnerability exists when creating HTTPS web request during X509 certificate chain building.
CVE-2021-24112 .NET 5 and .NET Core Remote Code Execution Vulnerability
A remote code execution vulnerability exists when disposing metafiles when a graphics interface still has a reference to it. This vulnerability only exists on systems running on MacOS or Linux.
 Visual Studio 2019 version 16.4.17
Visual Studio 2019 version 16.4.17
released January 12, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.17
Security Advisory Notice
CVE-2021-1651 / CVE-2021-1680 Diagnostics Hub Standard Collector Service Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Diagnostics Hub Standard Collector incorrectly handles data operations.
CVE-2020-26870 Visual Studio Installer Remote Code Execution Vulnerability
A remote code execution vulnerability exists when the Visual Studio Installer attempts to show malicious markdown.
CVE-2021-1723 .NET Core and Visual Studio Denial of Service Vulnerability
A denial of service vulnerability exists in the implementation of Kestrel.
 Visual Studio 2019 version 16.4.16
Visual Studio 2019 version 16.4.16
released December 08, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.16
Security Advisory Notice
CVE-2020-17156 Visual Studio Remote Code Execution Vulnerability
A remote code execution vulnerability exists when Visual Studio clones a malicious repository.
 Visual Studio 2019 version 16.4.15
Visual Studio 2019 version 16.4.15
released November 10, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.15
Security Advisory Notice
CVE-2020-17100 Visual Studio Tampering Vulnerability
A tampering vulnerability exists when the Python Tools for Visual Studio creates the python27 folder. An attacker who successfully exploited this vulnerability could run processes in an elevated context.
 Visual Studio 2019 version 16.4.14
Visual Studio 2019 version 16.4.14
released October 13, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.14
- Added an opt-in flag to mitigate performance impact of JCC erratum on certain Intel processors.
- The PGO MEMMAX switch should now behave in such a way that user input is more likely to be respected.
- The amount of memory reserved for PGO profiling has been reduced.
- .NET Core 2.1.13 Runtime and 3.1.109 SDK (3.1.9) added to Visual Studio 2019.
 Visual Studio 2019 version 16.4.13
Visual Studio 2019 version 16.4.13
released September 8, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.13
Security Advisory Notice
CVE-2020-1130 Diagnostics Hub Standard Collector Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Diagnostics Hub Standard Collector improperly handles data operations. An attacker who successfully exploited this vulnerability could run processes in an elevated context.
CVE-2020-1133 Diagnostics Hub Standard Collector Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Diagnostics Hub Standard Collector improperly handles file operations. An attacker who successfully exploited this vulnerability could run processes in an elevated context.
CVE-2020-16856 Visual Studio Remote Code Execution Vulnerability
A remote code execution vulnerability exists in Visual Studio when it improperly handles objects in memory. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the current user.
CVE-2020-16874 Visual Studio Remote Code Execution Vulnerability
A remote code execution vulnerability exists in Visual Studio when it improperly handles objects in memory. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the current user.
CVE-2020-1045 Microsoft ASP.NET Core Security Feature Bypass Vulnerability
A security feature bypass vulnerability exists in the way Microsoft ASP.NET Core parses encoded cookie names. The ASP.NET Core cookie parser decodes entire cookie strings which could allow a malicious attacker to set a second cookie with the name being percent encoded.
Additional Fixes in 16.4.13
- Fixed an issue that would sometimes cause Visual Studio or MSBuild to stop responding after cancelling a C++ build.
- Out of support versions of .NET Core will no longer be reinstalled during a repair or upgrade if they were removed outside of Visual Studio setup.
 Visual Studio 2019 version 16.4.12
Visual Studio 2019 version 16.4.12
released August 11, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.12
Security Advisory Notice
CVE-2020-1597
A denial of service vulnerability exists when ASP.NET Core improperly handles web requests. An attacker who successfully exploited this vulnerability could cause a denial of service against an ASP.NET Core web application. The vulnerability can be exploited remotely, without authentication.
 Visual Studio 2019 version 16.4.11
Visual Studio 2019 version 16.4.11
released July 14, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.11
- Fixed an occasional bug where code analysis of C/C++ stops responding.
- Fixed a bug where there wrong values could be restored after setjmp.
- 1.0 and 2.0 .NET Core runtimes have been marked as "out of support" in the setup UI and made optional for all scenarios.
Security Advisory Notice
CVE-2020-1393 Diagnostics Hub Standard Collector Service Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Windows Diagnostics Hub Standard Collector Service fails to properly sanitize input, leading to an unsecure library-loading behavior.
CVE-2020-1416 Visual Studio Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists in Visual Studio when it loads software dependencies.
CVE-2020-1147 .NET Core Denial of Service Vulnerability
A remote unauthenticated attacker could exploit this vulnerability by issuing specially crafted requests to an ASP.NET Core application, or other application that parses certain types of XML. The security update addresses the vulnerability by restricting the types that are allowed to be present in the XML payload.
 Visual Studio 2019 version 16.4.10
Visual Studio 2019 version 16.4.10
released June 09, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.10
- Fixed a bug where there wrong values could be restored after setjmp.
Security Advisory Notice
CVE-2020-1108 / CVE-2020-1108.NET Core Denial of Service Vulnerability
To comprehensively address CVE-2020-1108, Microsoft has released updates for .NET Core 2.1 and .NET Core 3.1. Customers who use any of these versions of .NET Core should install the latest version of .NET Core. See the Release Notes for the latest version numbers and instructions for updating .NET Core.
CVE-2020-1202 / CVE-2020-1203 Diagnostics Hub Standard Collector Service Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Diagnostics Hub Standard Collector or the Visual Studio Standard Collector fails to properly handle objects in memory.
CVE-2020-1293 / CVE-2020-1278 / CVE-2020-1257 Diagnostics Hub Standard Collector Service Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Diagnostics Hub Standard Collector Service improperly handles file operations.
 Visual Studio 2019 version 16.4.9
Visual Studio 2019 version 16.4.9
released May 27, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.9
- This fixes a caching bug in an analysis used by an optimization, the effect being we remove instructions erroneously marked as unneeded. The fix is to detect cases where we would have otherwise stored stale data to the cache. It is difficult to entirely characterize when this manifests, but in the report it was a modulo operator on an index in a loop. For the future, we've added the (unsupported) /d2ssa-bit-estimator- flag to turn off the particular optimization entirely. This flag was added with the fix, and is not present in prior versions.
- Added support to mitigate the performance impact caused by the Intel Jump Conditional Code (JCC) erratum microcode update in certain Intel processors.
- False C6244 warnings and crash in cl.exe during code analysis caused by lambda local variables has been fixed.
- ICE in PREfast 16.5 running against Office code
 Visual Studio 2019 version 16.4.8
Visual Studio 2019 version 16.4.8
released May 12, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.8
- Add a change that enables Enterprise IT administrators and deployment engineers to configure tools like Microsoft Update client & SCCM to determine applicability of VS2019 16.4 updates hosted on Microsoft Update Catalog & WSUS.
Security Advisory Notice
CVE-2020-1108 .NET Core Denial of Service Vulnerability
A remote unauthenticated attacker could exploit this vulnerability by issuing specially crafted requests to the .NET Core application. The security update addresses the vulnerability by correcting how the .NET Core web application handles web requests.
CVE-2020-1161 .NET Core Denial of Service Vulnerability
A remote unauthenticated attacker could exploit this vulnerability by issuing specially crafted requests to the ASP.NET Core application. The security update addresses the vulnerability by correcting how the ASP.NET Core web application handles web requests.
 Visual Studio 2019 version 16.4.7
Visual Studio 2019 version 16.4.7
released April 14, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.7
Security Advisory Notice
CVE-2020-0899 Microsoft Visual Studio Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when Microsoft Visual Studio updater service improperly handles file permissions. An attacker who successfully exploited this vulnerability could overwrite arbitrary file content in the security context of the local system.
CVE-2020-0900 Visual Studio Extension Installer Service Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Visual Studio Extension Installer Service improperly handles file operations. An attacker who successfully exploited the vulnerability could delete files in arbitrary locations with elevated permissions.
CVE-2020-5260 Git for Visual Studio Credential Leak Vulnerability due to insufficient validation on URLs
A credential leak vulnerability exists when specially crafted URLs are parsed and sent to credential helpers. This can lead to credentials being sent to the wrong host.
 Visual Studio 2019 version 16.4.6
Visual Studio 2019 version 16.4.6
released March 10, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.6
- Miscompile, boolean condition deduced to be always true.
- Issue with loop unroll in Visual Studio 2019 compiler
- CL (VC v19.24) crashes when building in a docker volume folder
- CL (VC v19.22) crashes when it starts with the /ZI parameter in the docker container
- Compiling SSE intrinsics with MSVC compiler 19.20: compiled code yields incorrect results in one specific case
- C++ AMP code will not compile in Visual Studio 2019 16.3.1
- Sometimes coroutine_handle<>::destroy() resumes coroutine instead of destroying it.
- New Spectre mitigation options in C++ compiler: /Qspectre-load & /Qspectre-load-cf for speculative load hardening.
Security Advisory Notice
CVE-2020-0793 & CVE-2020-0810 Diagnostics Hub Standard Collector Service Elevation of Privilege Vulnerability
An elevation of privilege vulnerability exists when the Diagnostics Hub Standard Collector improperly handles file operations, or the Windows Diagnostics Hub Standard Collector Service fails to properly sanitize input.
CVE-2020-0884 Spoofing vulnerability when creating Outlook Web -Add-in
A spoofing vulnerability exists when creating an Outlook Web-Addin if multi-factor authentication is enabled, as it includes a reply URL that is not secured by SSL. An attacker who successfully exploited this vulnerability could compromise the access tokens, exposing security and privacy risks.
CVE-2020-0789 Visual Studio Extension Installer Service Denial of Service Vulnerability
 Visual Studio 2019 version 16.4.5
Visual Studio 2019 version 16.4.5
released February 11, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.5
- Merge Conflict: "Take Source"/"Keep Target" is missing
- Crashes when trying to debug uwp application
- Unable to select target platform azure v12 for database project
- Fixed crashes or errors that can occur when running Visual Studio after an install action that requires a reboot.
- Fixed an issue deploying Xamarin.Android apps. This peviously required a manual uninstall of the app from the device or emulator.
- This change fixes a bug where the compiler may sometimes incorrectly remove an instruction in a C++ coroutine.
 Visual Studio 2019 version 16.4.4
Visual Studio 2019 version 16.4.4
released January 30, 2020
Top Issues Fixed in Visual Studio 2019 version 16.4.4
- Custom Project Template Not Found
- msvsmon.exe crashes when hitting breakpoint in native C++ code
- Search for a folder in solution explorer, then click home or the X in the search box. The view is reset.
- External Tools argument current line is always zero.
- Can't create v3 Function project.
- Access violation reading location 0xFFFFFFFFFFFFFFFF. after updating to VS 2019 Update 16.4.3
- Cannot create function app under 16.4
- MSVC2019 generates AVX-512 instruction in AVX/AVX2 mode
- Bad code generation with rsqrtss (register clobber)
- Visual Studio 2019 Debugger crashes when viewing FastLink callstack.
- C#: Fixed a crash when an attribute constructor is decorated with itself and Nullable Reference Types is enabled.
- Fixed an optimization-analysis bug where we lose track of alias information for arrays of indeterminate length (declared as extern int a[]) when we unroll loops, leading to possible incorrect dead-store removal.
 Visual Studio 2019 version 16.4.3
Visual Studio 2019 version 16.4.3
released January 14, 2020
Security Advisory Notice
CVE-2020-0602 ASP.NET Core Denial of Service Vulnerability
A remote unauthenticated attacker could exploit this vulnerability by issuing specially crafted requests to the ASP.NET Core application. The security update addresses the vulnerability by correcting how the ASP.NET Core web application handles web requests.
CVE-2020-0603 ASP.NET Core Remote Code Execution Vulnerability
A remote unauthenticated attacker could exploit this vulnerability by issuing specially crafted requests to the ASP.NET Core application. The security update addresses the vulnerability by correcting how the ASP.NET Core web application handles in memory.
CVE-2020-0605 .NET Core Remote Code Execution Vulnerability
Exploitation of the vulnerability requires that a user open a specially crafted file with an affected version of .NET Core. In an email attack scenario, an attacker could exploit the vulnerability by sending the specially crafted file to the user and convincing the user to open the file.The security update addresses the vulnerability by correcting how .NET Core checks the source markup of a file.
CVE-2020-0606 .NET Core Remote Code Execution Vulnerability
Exploitation of the vulnerability requires that a user open a specially crafted file with an affected version of .NET Core. In an email attack scenario, an attacker could exploit the vulnerability by sending the specially crafted file to the user and convincing the user to open the file.The security update addresses the vulnerability by correcting how .NET Core checks the source markup of a file.
Top Issues Fixed in Visual Studio 2019 version 16.4.3
- DateTime.Now = Cannot provide the value: host value not found
- MSVC codegen error vector reverse_iterator x64 C++17 debug build
- C2440 error building atlenc.h with /permissive- in VS 16.4 Preview 1
- Last Visual Studio update broke NTLM authentication on Android (seems like new version of Momo would be a reason)
- Visual Studio 16.3.1 fails at compiling template code (e.g. from Basler Pylon SDK)
- Using TypeScript 3.7 for IntelliSense
- XCode 11.3 is too new all of a sudden after update to 8.4
- You uploaded an APK or Android App Bundle with invalid or missing signing information for some of its files. You need to create a valid signed APK or Android App Bundle.
- Unable to Run UWP project
- JavaScript IntelliSense not working after update 16.4.1
- Xib : Xcode is to new(rendering problem when using custom components)
- Storyboard error: 'Xcode is too new'
- Stability improvements for debugging watchOS applications.
- Adds Xcode 11.3 SDK support.
- Fixed crash when fstack-protector-strong flag is enabled.
- Fixed some inconsistent behavior with Debugger.
 Visual Studio 2019 version 16.4.2
Visual Studio 2019 version 16.4.2
released December 17, 2019
Top Issues Fixed in Visual Studio 2019 version 16.4.2
- VS2019 Preview 4 broke conditional compilation symbols in C#
- API has been deprecated
- Android debugging not working in latest release 16.4 "Debuggee returned error code INVALID_ARGUMENT"
- Fixed a frequent UI delay that can occur while using the editor.
- Fixed a crash when an attribute constructor is decorated with itself and Nullable Reference Types is enabled while using C#.
- Fixed an issue that resulted in Visual Studio failing to start or crashing on C# solution load on certain Virtual Machine setups.
- Fixed a bug where user defined conditional compliation symbols are lost when the build properties page is reopened.
 Visual Studio 2019 version 16.4.1
Visual Studio 2019 version 16.4.1
released December 10, 2019
Top Issues Fixed in Visual Studio 2019 version 16.4.1
- Fixed "the write operation failed. you must first acquire write access from dataschemamodelcontroller" error trying to publish a database
- Fix ExecutionEngineException exceptions when using SignalR on iOS devices in some configurations
- Runtime Fix "CEE_RET: value type stack" crash when interpreter was enabled with some libraries
- TypeScript 3.7.3 is now included by default, which contains several fixes for issues that affect the JavaScript and TypeScript editing experience.
- May allow mitigation of a Per-Monitor awareness related crash in Visual Studio
Security Advisory Notice
CVE-2019-1349 Git for Visual Studio Remote Excecution Vulnerability due to too lax restrictions on submodule names
A remote code execution vulnerability exists when Git runs into collisions of submodule names for directories of sibling submodules. An attacker who successfully exploited this vulnerability could remote execute code on the target machine. The security update addresses the vulnerability by taking a new version of Git for Windows which requires the directory for the submodules’ clone to be empty.
CVE-2019-1350 Git for Visual Studio Remote Excecution Vulnerability due to incorrect quoting of command-line arguments
A remote code execution vulnerability exists when Git interprets command-line arguments with certain quoting during a recursive clone in conjunction with SSH URLs. An attacker who successfully exploited this vulnerability could remote execute code on the target machine. The security update addresses the vulnerability by taking a new version of Git for Windows which fixes the issue.
CVE-2019-1351 Git for Visual Studio Arbitrary File Overwrite Vulnerability due to usage of non-letter drive names during clone
An arbitrary file overwrite vulnerability exists in Git when non-letter drive names bypass safety checks in git clone. An attacker who successfully exploited this vulnerability could write to arbitrary files on the target machine. The security update addresses the vulnerability by taking a new version of Git for Windows which fixes the issue.
CVE-2019-1352 Git for Visual Studio Remote Excecution Vulnerability due to unawareness of NTFS Alternate Data Streams
A remote code execution vulnerability exists in Git when cloning and writing to .git/ directory via NTFS alternate data streams. An attacker who successfully exploited this vulnerability could remote execute code on the target machine. The security update addresses the vulnerability by taking a new version of Git for Windows which has been made aware of NTFS alternate data streams.
CVE-2019-1354 Git for Visual Studio Arbitrary File Overwrite Vulnerability due to not refusing to write out tracked files containing backslashes
An arbitrary file overwrite vulnerability exists in Git when tree entries with backslashes and malicious symlinks could break out of the work tree. An attacker who successfully exploited this vulnerability could write to arbitrary files on the target machine. The security update addresses the vulnerability by taking a new version of Git for Windows which does not allow this usage of backslashes.
CVE-2019-1387 Git for Visual Studio Remote Execution Vulnerability due to too lax validation of submodule names in recursive clones
A remote code execution vulnerability exists in Git when cloning recursively with submodules. An attacker who successfully exploited this vulnerability could remote execute code on the target machine. The security update addresses the vulnerability by taking a new version of Git for Windows which tightens validation of submodule names.
CVE-2019-1486 Live Share extension URL redirection vulnerability
A spoofing vulnerability was detected in the Visual Studio Live Share extension, when a guest connected to a Live Share session was redirected to an arbitrary URL specified by the session host. An attacker would have been able to successfully exploit this vulnerability and cause the guest's computer to open a browser and navigate to a malicious URL without explicit consent. This was part of the "Shared Server" feature of Live Share that allowed auto-port forwarding during an active Live Share session. The latest update addresses this vulnerability by prompting the Live Share guest for consent prior to browsing the host-specified URL.
 Visual Studio 2019 version 16.4
Visual Studio 2019 version 16.4
released December 3, 2019
Summary of What's New in Visual Studio 2019 version 16.4
- Visual Studio now supports “FIPS compliance mode”
- XAML Designer zoom/position now defaults to Fit All.
- Create Data Binding Dialog has been added.
- Improvements to regions IntelliSense
- Snippets in XAML IntelliSense
- Pop-up XAML editor as a separate window from designer
- Displaying resources for referenced assemblies
- Just My XAML in Live Visual Tree
- Merge Resource Dictionary
- XAML Islands support
- Edit Template now works with controsl from 3rd party controls.
- Clang-Tidy support in C++ MSBuild and CMake projects, for both Clang and MSVC.
- AddressSanitizer support for projects compiled with MSVC on Windows.
- Support for publishing local Git repositories to GitHub.
- Change your document tabs to a vertical layout with Vertical Document Tabs.
- .NET Productivity additions in this release include the ability to configure the severity level of a code style rule directly in the error list, Find All References now has the option to group by type and member, and a refactoring to make a local function static and pass in variables defined outside of the function to the function's declaration and calls.
- Quickly customize how objects are displayed in debugger windows using the new Pinnable Properties feature.
- Containers tool window adds the ability to inspect, stop, start, and remove Docker containers and images
- Option to improve startup peformance by auto hiding tool windows
- Automatic detection of SQL Server and Azure Storage connections strings when managing publish dependencies or using Connected Services
- Added support for developing Azure Functions using the 64bit runtime.
- Added support for .NET Core 3.0 app publishing options: Ready to Run (Crossgen), Linking, and SingleExe
- .NET Productivity additions in this release include the ability to configure the severity level of a code style rule directly through the editor, navigate easily up the inheritance chain with the new Go To Base command, adding null checks for all parameters, and XML documentation for overriding methods.
- XAML Hot Reload for Xamarin.Forms
- Android App Bundle Publishing
- AndroidX Migration Wizard
- Android Layout Linting
Details of What's new in Visual Studio 2019 version 16.4
Visual Studio now supports “FIPS compliance mode”
Starting with version 16.4, Visual Studio 2019 now supports “FIPS 140-2 compliance mode” when developing apps and solutions for Windows, Azure, and .NET. When you’re developing apps or solutions for non-Microsoft platforms like Linux, iOS, or Android, these platforms may not use FIPS 140-2 approved algorithms. Third-party software included with Visual Studio or extensions that you install also may not use FIPS 140-2 approved algorithms. In addition, development for SharePoint solutions does not support FIPS 140-2 compliance mode.
To configure FIPS 140-2 compliance mode for Visual Studio, install .NET Framework 4.8 and enable the Windows group policy setting: “System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing.”
WPF/UWP Tooling
Customers building WPF/UWP applications will see the following improvements in Visual Studio XAML tooling:
Designer
- XAML Designer zoom/position now defaults to Fit All: Based on customer feedback we’ve reevaluated the default XAML Designer zoom behavior that occurs when you open a XAML window/page/control/etc. The previous experienced stored the zoom level and position for each file across Visual Studio sessions which caused confusion when customers were coming back to a file after some time had passed. Starting with this release we will only store the zoom level and position for the duration of the active session and go back to a “fit all” default once Visual Studio is restarted.
- Create Data Binding Dialog: Visual Studio has had a data binding dialog available to WPF .NET Framework developers from the right-click of the XAML Designer and Property Explorer, and this dialog was also previously available to UWP developers. In this release we’re bringing back this experience to UWP developers and adding support for WPF .NET Core applications. This feature is still in development and will continue to improve in the future to bring back feature parity with .NET Framework dialog capabilities.
XAML Editor
- Improvements to #regions IntelliSense: Starting with Visual Studio 2015 #region support has been available for WPF and UWP XAML developers and more recently for Xamarin.Forms. In this release we’ve fixed an IntelliSense bug, with this fix #regions will now show properly as you begin to type <!.
- Snippets in XAML IntelliSense: IntelliSense has been enhanced to support showing XAML snippets, this will work for both built-in snippets and any custom snippets that you add manually. Starting with this release we’re also including some out-of-the-box XAML snippets: #region, Column definition, Row definition, Setter and Tag.
- Pop up XAML editor as a separate window from designer: It is now possible to easily split the XAML Designer and its underlying XAML editor into separate windows using the new Pop up XAML button next to the XAML tab. When clicked the XAML designer will minimize its attached XAML tab and pop open a new window for just the XAML editor view. You can move this new window to any display or tab group in Visual Studio. Note that it is still possible to expand the original XAML view but regardless all XAML views of the same file will stay synchronized in real-time.
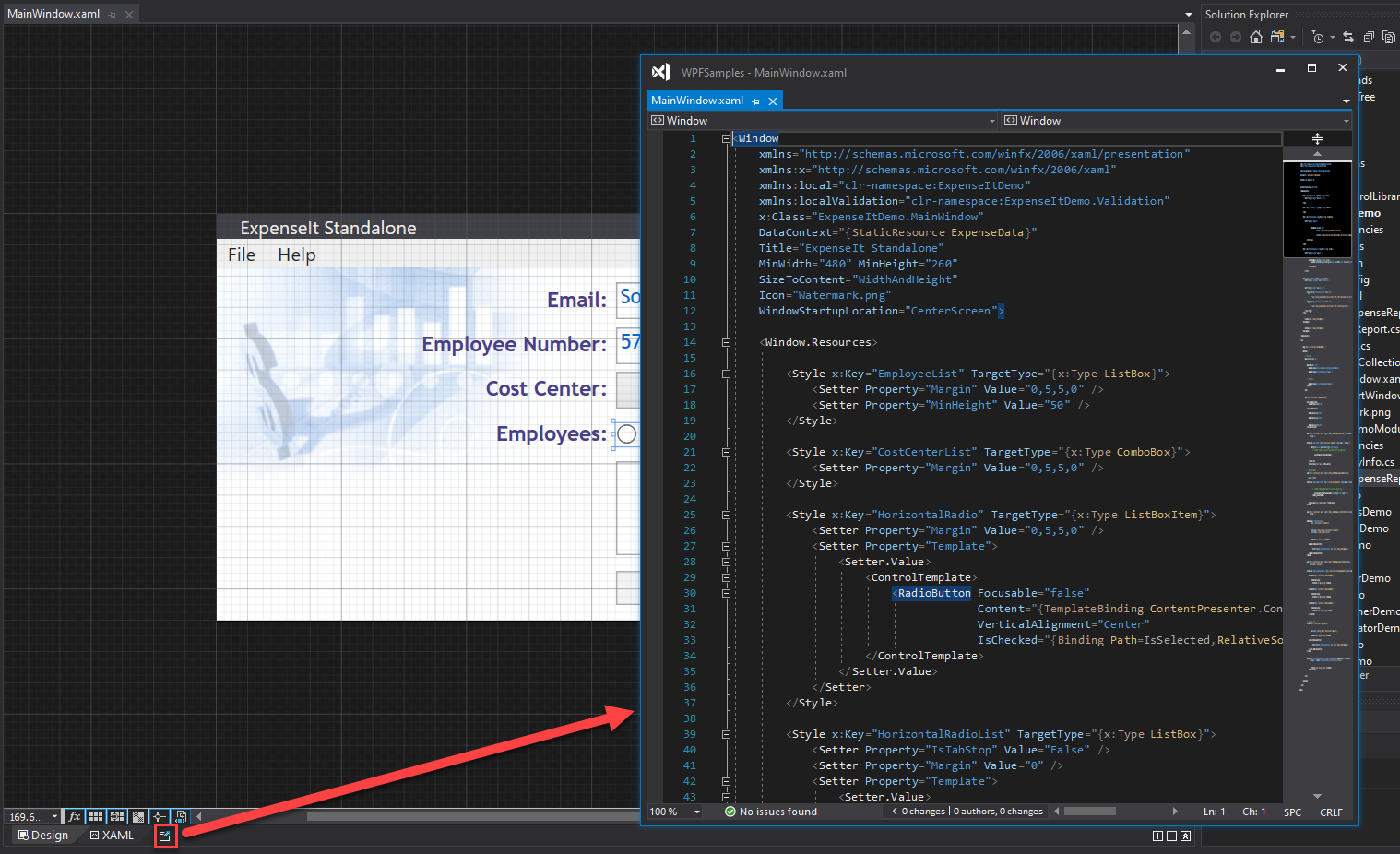
- Displaying resources for referenced assemblies: XAML IntelliSense has been updated to support displaying XAML resources from a referenced assembly (when source is not available) for WPF Framework and WPF .NET Core projects.
XAML Debugging Tools
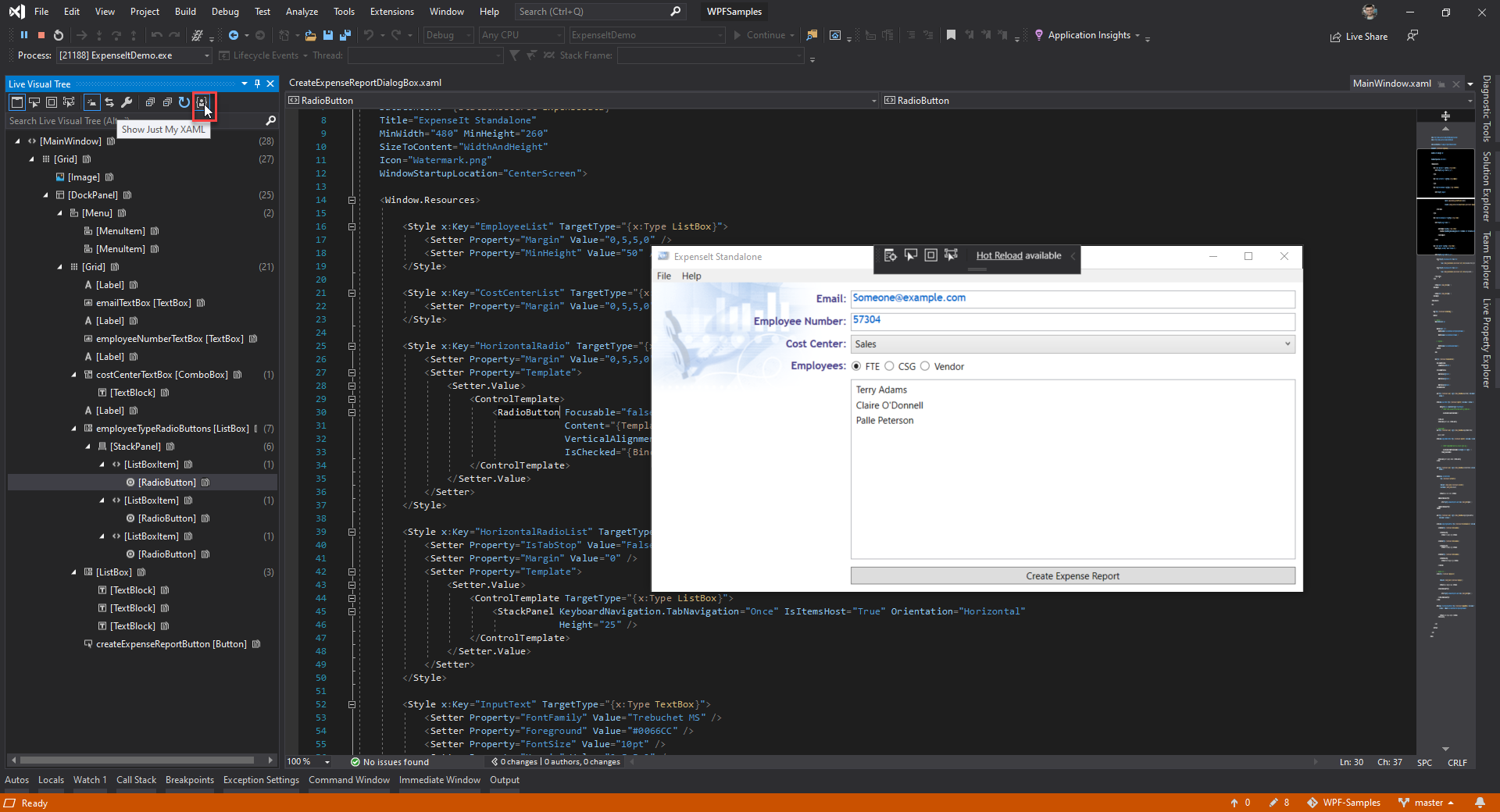
- Just My XAML in Live Visual Tree: The Live Visual Tree is a feature that is available to both UWP and WPF developers when they run their application in debug mode and is part of the live editing tooling related to XAML Hot Reload. Previously the feature would display the full live visual tree of the attached running application with no filter possible to see just the XAML you’ve written in your app. This made for a very noisy experience and based on customer feedback we’ve added a new default called “Just My XAML” which will limit the tree to just controls you wrote in your application. While this is the new default it is still possible to go back to the previous behavior through either the button within tine Live Visual Tree itself or through a new setting (found under: Options > Debugging > General > Enable Just My XAML)
Resources & Templates
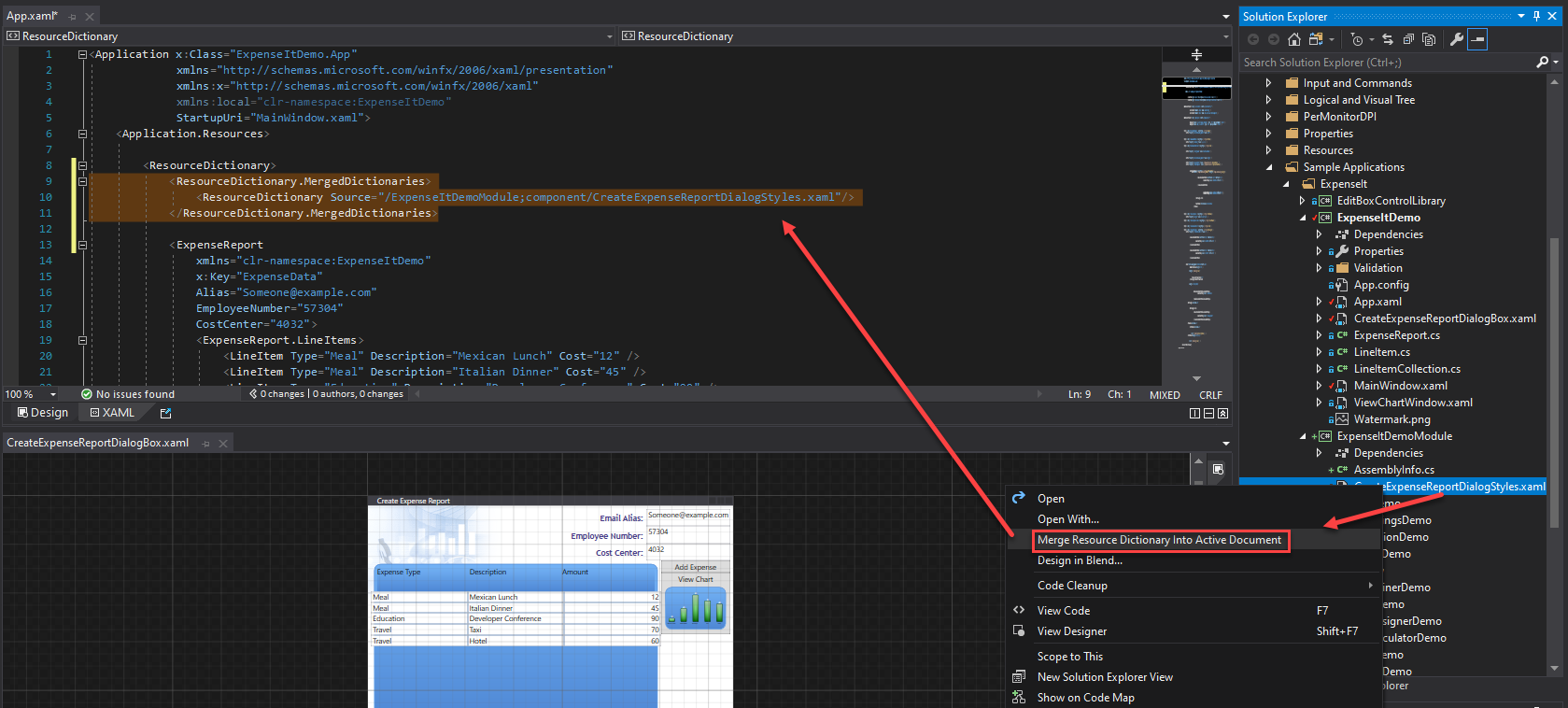
- Merge Resource Dictionary: It is now possible to easily merge an existing resource dictionary within your UWP/WPF project with any valid XAML file using the new feature available through the solution explorer. Simply open the XAML file in which you want to add the merge statement, then find the file you wish to merge in and right-click on it in solution explorer. In the context menu select the option “Merge Resource Dictionary Into Active Window”, which will add the right merge XAML with path.
- Edit Template now works with controls from 3rd party controls: It is now possible to create a copy of a controls template even when it’s not part of your solution as source code. With this change the “Edit Template” feature will now be available and work as it does for 1st party elements where the source is available today. Note that this feature is applicable to both 3rd party control libraries and 1st party where source isn’t available.
XAML Islands:
- Improved XAML Island support: We’ve added support for XAML Islands scenario for Windows Forms and WPF .NET Core 3 apps making it easier to add UWP XAML control into these applications. With these improvements a .NET Core 3 project can a reference to UWP project that contains custom UWP XAML controls. Those custom controls can be used by the WindowsXamlHost controls shipped within the Windows Community Toolkit v6 (Microsoft.Toolkit.Wpf.UI.XamlHost v6.0). You can also use the Windows Application Packaging project to generates MSIX for you .NET Core 3 with Islands. To learn how to get started visit our documentation.
C++
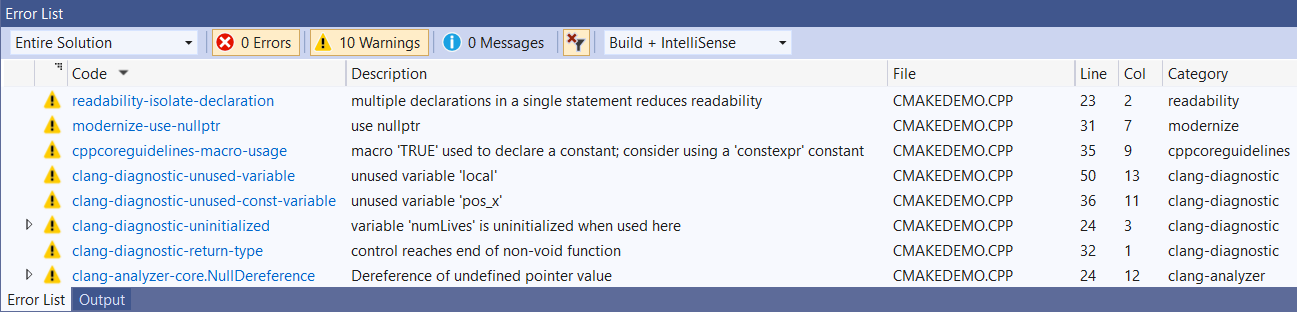
- Code Analysis now natively supports Clang-Tidy for both MSBuild and CMake projects, whether you're using a Clang or MSVC toolset. clang-tidy checks can run as part of background code analysis, appear as in-editor warnings (squiggles), and display in the Error List.
- Visual Studio CMake projects now have Overview Pages to help you get started with cross-platform development. These pages are dynamic and help you connect to a Linux system and add a Linux or WSL configuration to your CMake project.
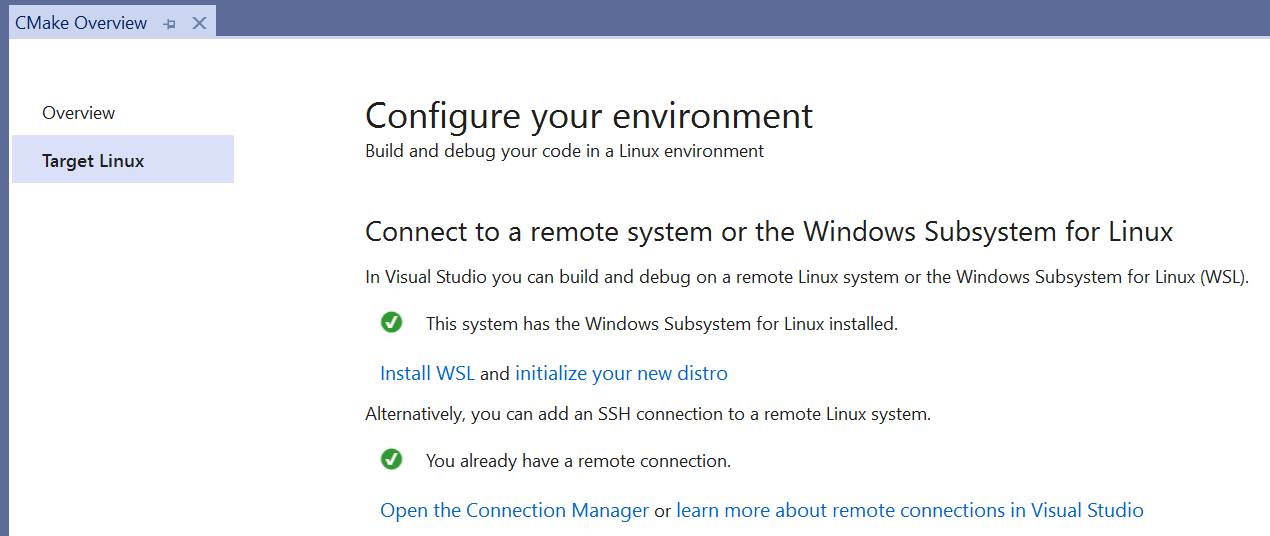
- The launch drop-down menu for CMake projects now displays your most recently used targets and can be filtered.
- C++/CLI now supports interop with .NET Core 3.1 and higher on Windows.
- You can now enable ASan for projects compiled with MSVC on Windows for runtime instrumentation of C++ code that helps with detection of memory errors.
- Updates to MSVC's C++ Standard Library:
- C++17: Implemented
to_chars()general precision, completing P0067R5 Elementary String Conversions (charconv). This completes implementation of all library features in the C++17 Standard. - C++20: Implemented P1754R1 Rename concepts to standard_case. To include preview features from the Latest C++ Working Draft, use the compiler flag
/std:c++latest; the flag can also be set in the C/C++ > Language project property page via the C++ Language Standard property.
- C++17: Implemented
- A new collection of tools named C++ Build Insights is now available. See the C++ Team Blog for more information.
Publish to GitHub Support
- The publish to GitHub feature that was a part of the GitHub Extension for Visual Studio is now included in Visual Studio’s GitHub Essentials.
- You can now publish local Git repositories to GitHub using the Publish to GitHub button on Team Explorer Synchronization page.
Vertical Document Tabs in Visual Studio
Manage your document tabs in a vertical list on either the left or right side of your editor.
Pinnable Properties Debugging Tool
You can now quickly identify and inspect objects at debug-time by pinning properties to the top of DataTips or the Watch, Autos, and Locals windows using the Pinnable Properties feature.
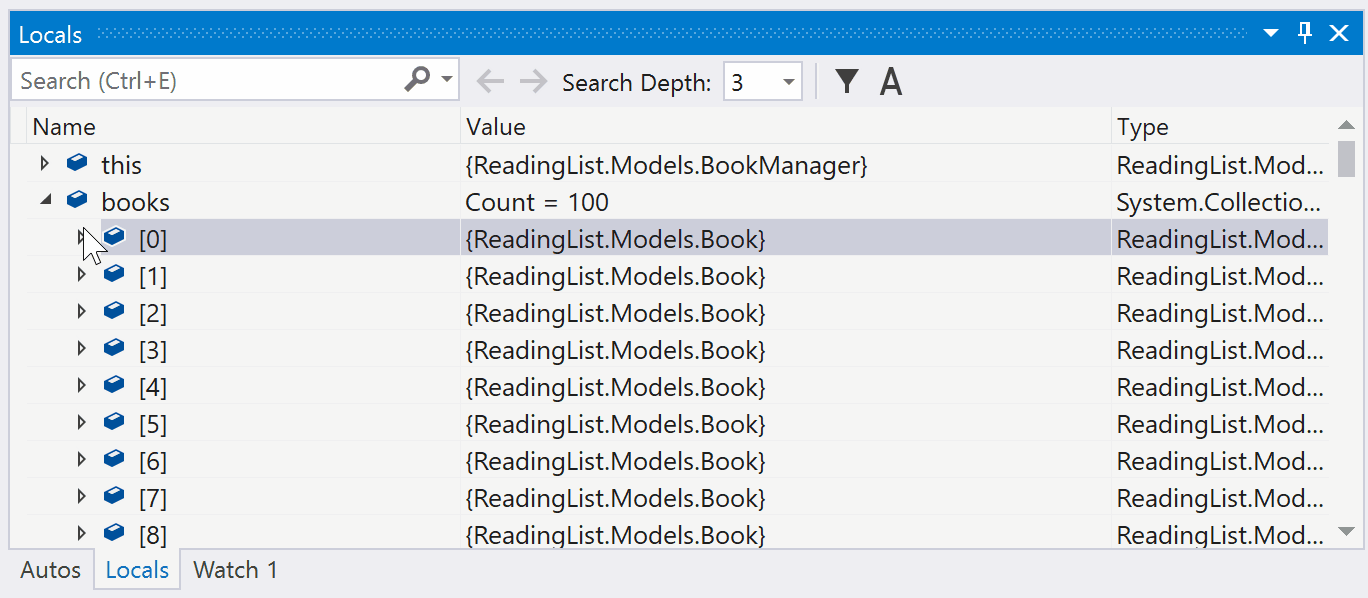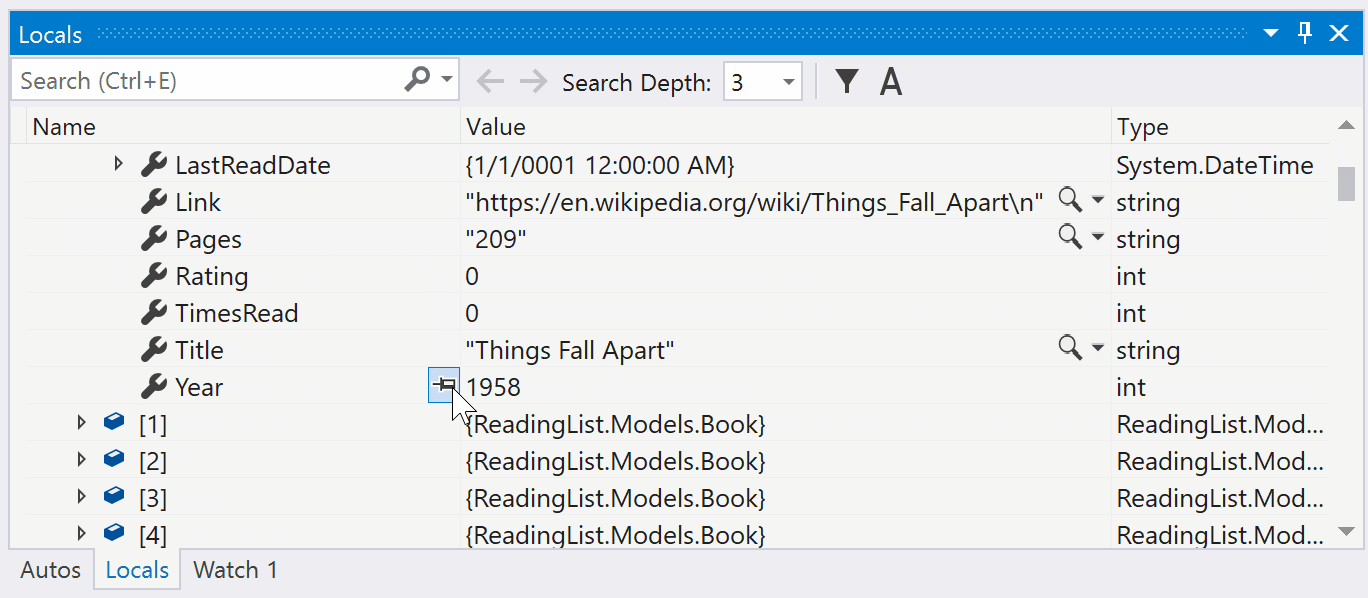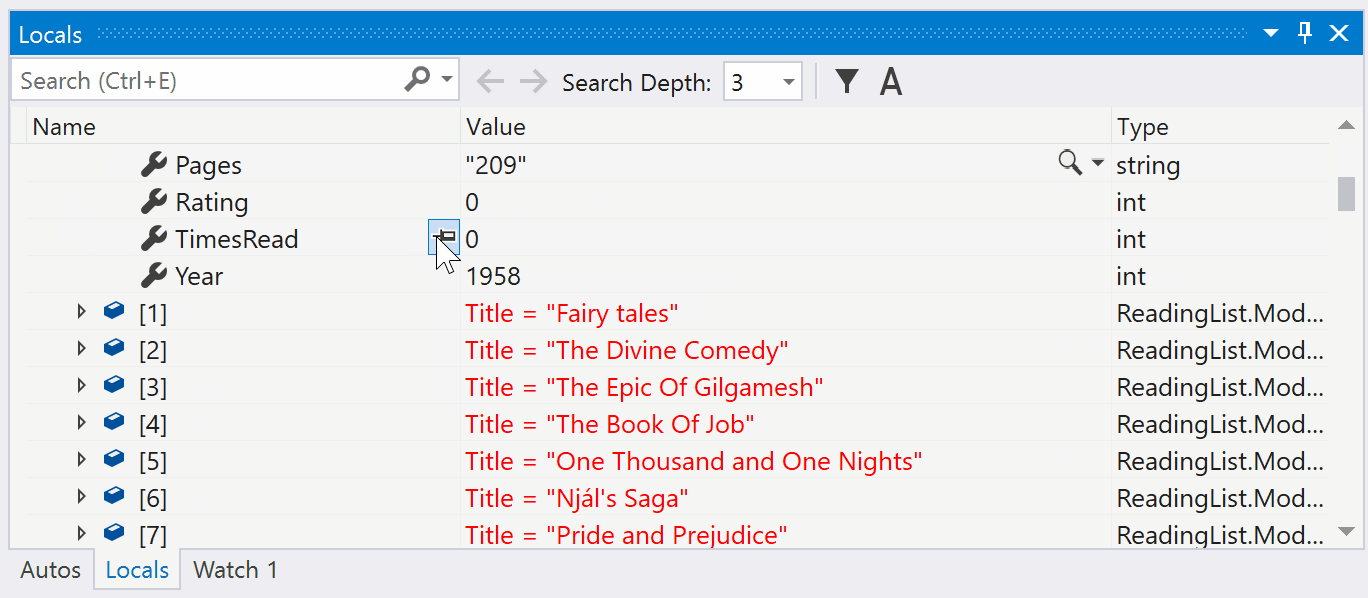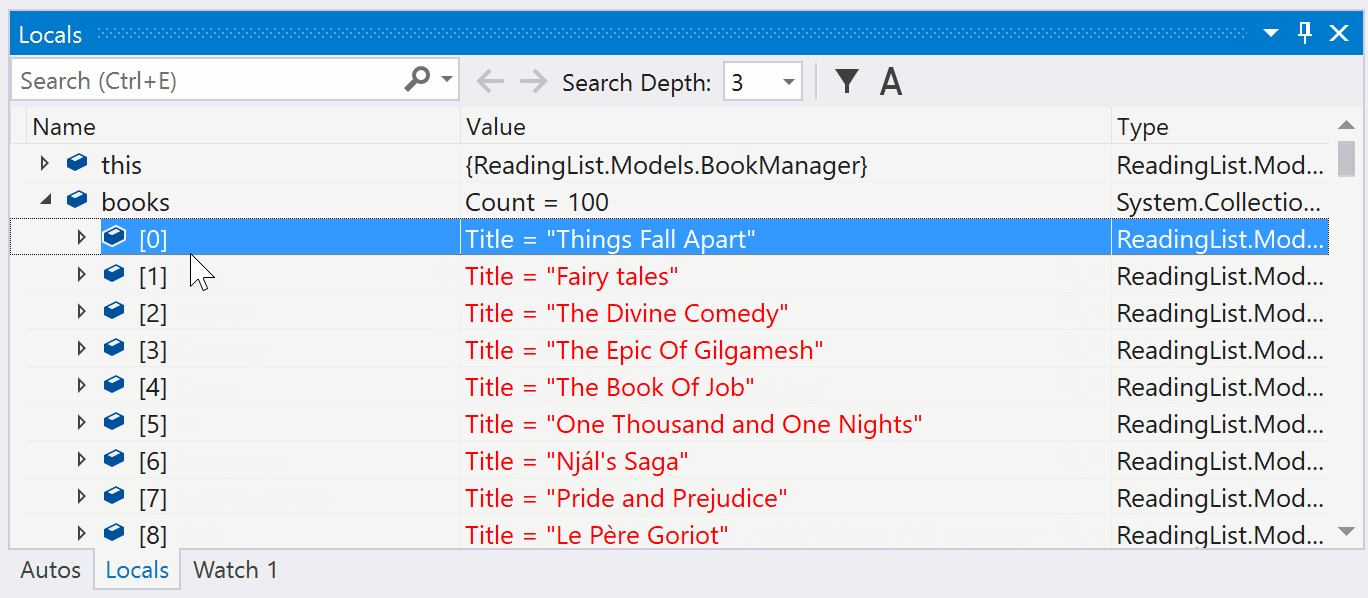
Containers tool window
- You can list, inspect, stop, start, and remove containers
- You can view logs and file contents for running containers, as well as open a terminal window into the containers
- You can view, inspect, and remove images
Autohide tool windows
Enabling this preview feature option allows you to skip startup delays introduced by launching Visual Studio with multiple tool windows opened.
.NET Productivity
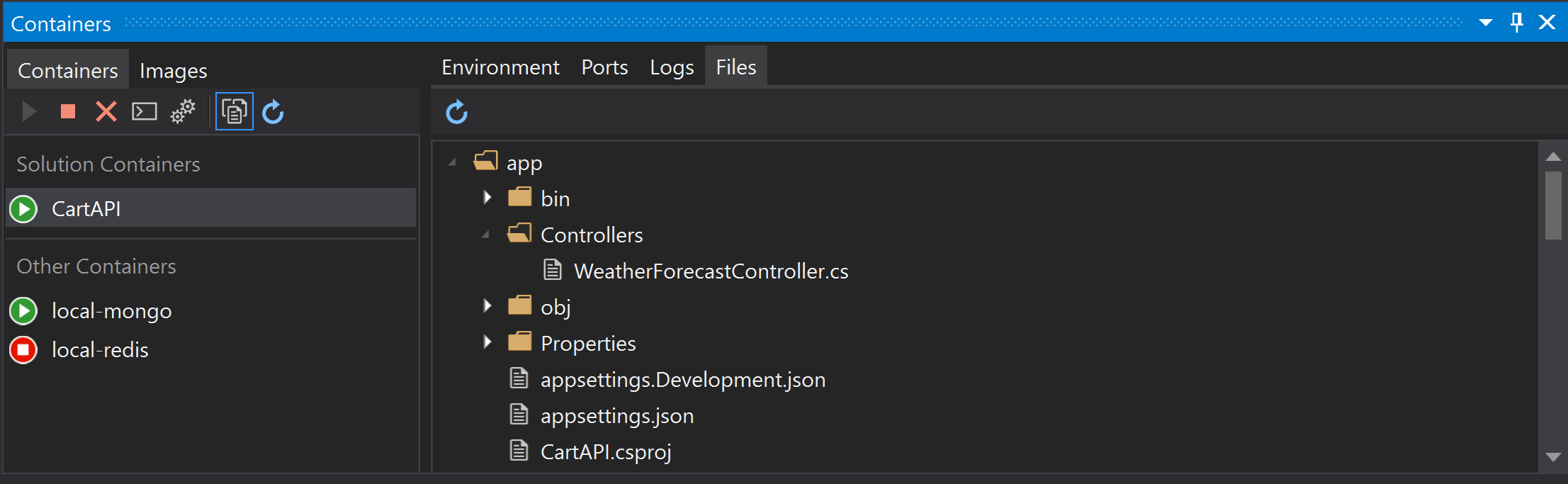
- You can now configure the severity level of a code style rule directly through the error list. Place your cursor on the error, warning, or suggestion. Right click and select Set severity. Then select the severity level you would like to configure for that rule. This will update your existing EditorConfig with the rule’s new severity. This also works for third party analyzers.
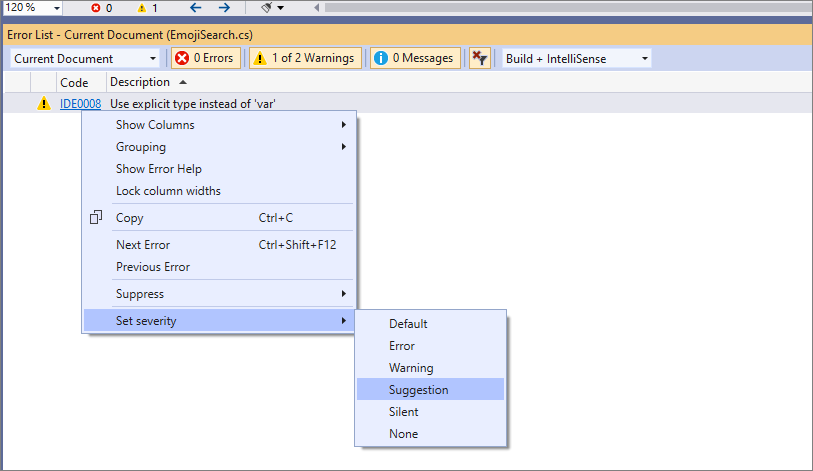
- Find All References now allows you to group by type and member.
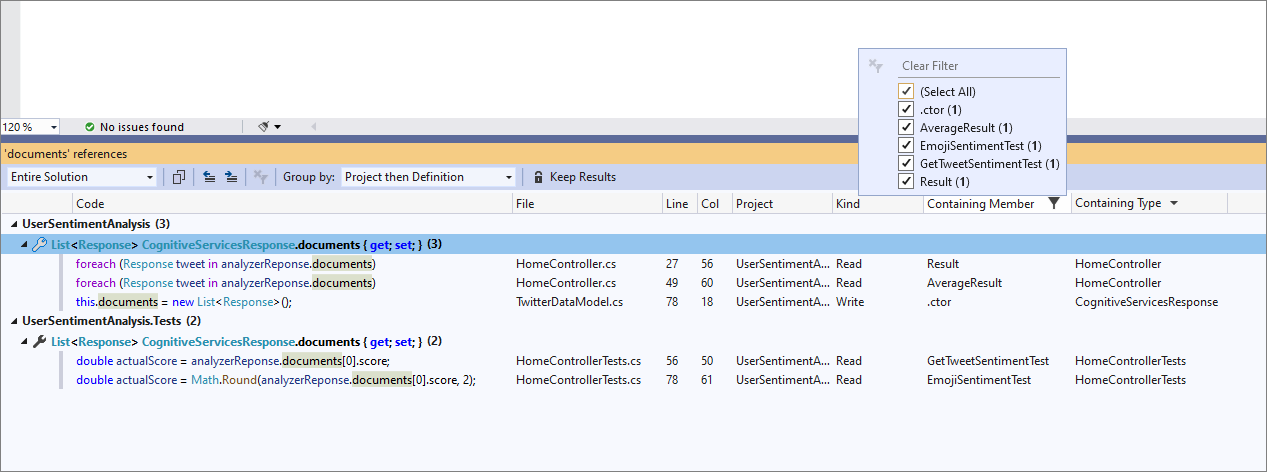
- You can now make a local function static and pass in variables defined outside the function to the function’s declaration and calls. Place your cursor on the local function name. Press (Ctrl+.) to trigger the Quick Actions and Refactorings menu. Select Make local function
static.
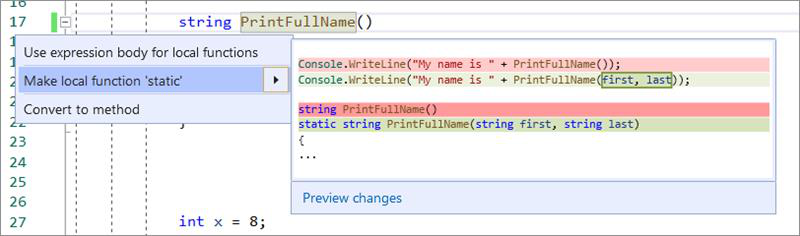
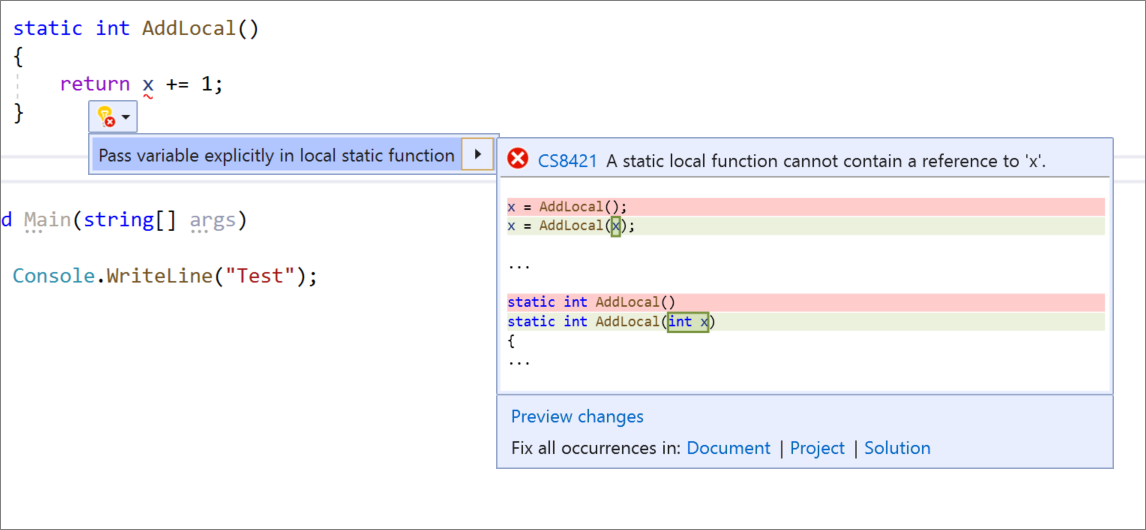
- You can now pass a variable explicitly into a local static function. Place your cursor on the variable in the static local function. Press (Ctrl+.) to trigger the Quick Actions and Refactorings menu. Select Pass variable explicitly in local static function.
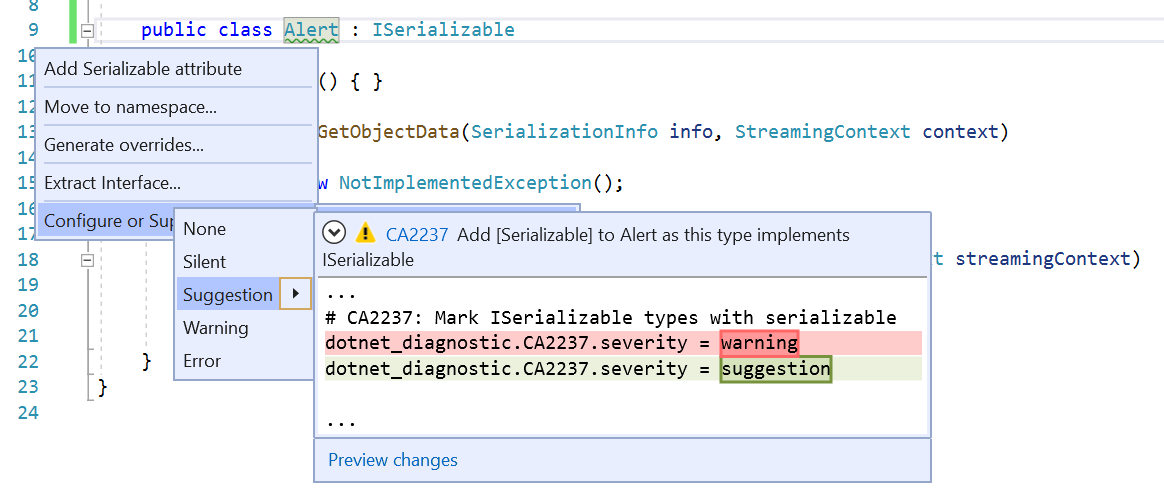
.NET Productivity
- You can now configure the severity level of a code style rule directly through the editor. If a user does not currently have an .editorconfig file, one will be generated for them. Place your cursor on the error, warning, or suggestion and type (Ctrl+.) to open the Quick Actions and Refactorings menu. Select ‘Configure or Suppress issues’. Then select the rule and choose the severity level you would like to configure for that rule. This will update your existing EditorConfig with the rule’s new severity. This also works for third party analyzers.
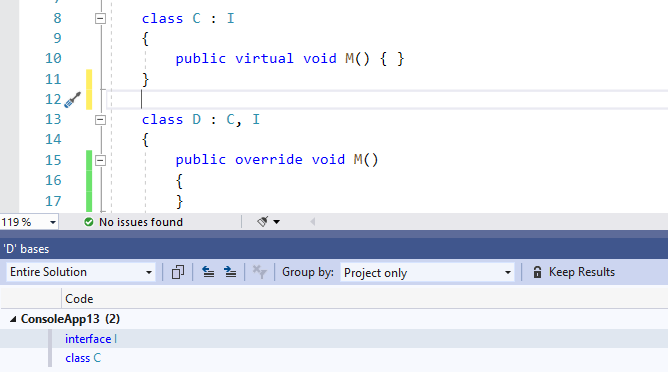
- You can now use the Go To Base command to navigate up the inheritance chain. Go To Base command is available on the context (right-click) menu of the element you want to navigate the inheritance hierarchy. Or you can type (Alt+Home). If there is more than one result a tool window will open with all of the results that you can choose to navigate to.
- You can now add null checks for all parameters. This will add if statements that check nullity of all the nullable, non-checked parameters. Place your cursor on any parameter within the method. Press (Ctrl+.) to trigger the Quick Actions and Refactorings menu. Select the option to ‘Add null checks for all parameters’.
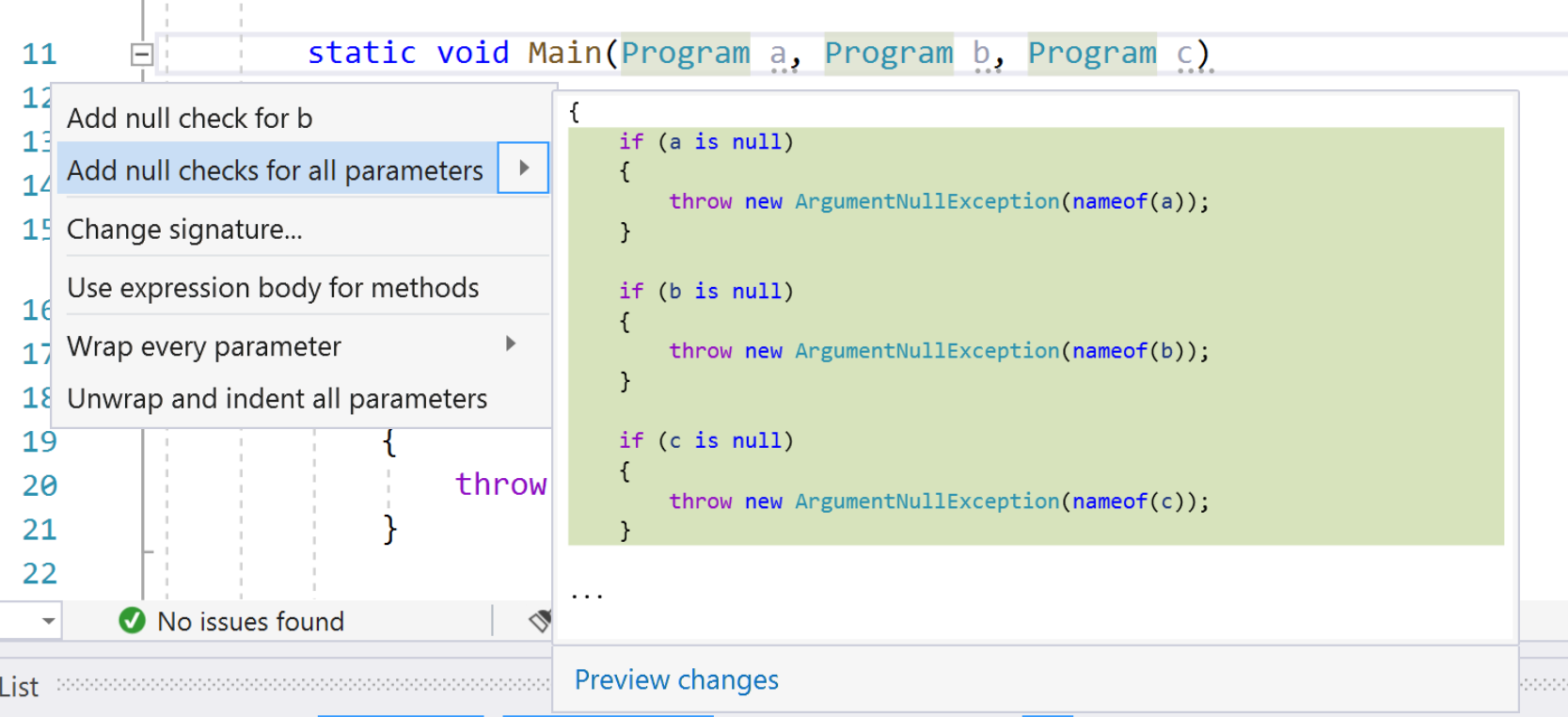
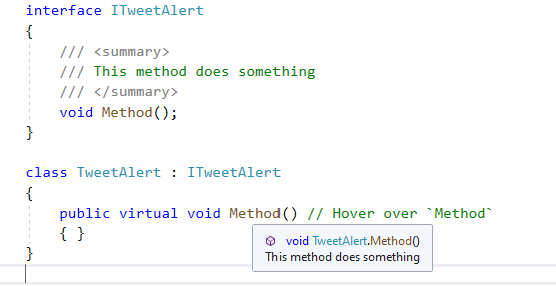
- Methods that have no XML documentation can now automatically inherit XML documentation from the method it is overriding. Place your cursor over the undocumented method that implements a documented interface method. Quick Info will then display the XML documentation from the interface method. You can also inherit xml comments from base classes and interfaces with the
<inheritdoc>tag. Docs example.
Xamarin
XAML Hot Reload for Xamarin.Forms
XAML Hot Reload for Xamarin.Forms speeds up your development and makes it easier to build, experiment, and iterate on your user interface. You no longer have to rebuild your app each time you tweak your UI – it instantly shows you your changes in your running app.
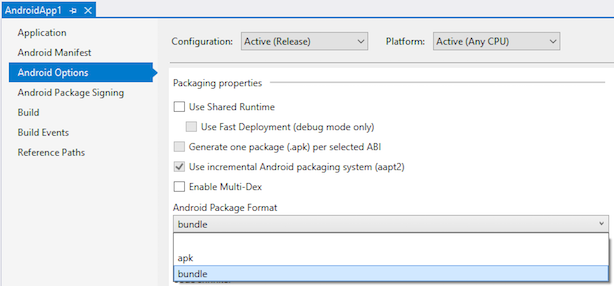
Android App Bundle Publishing
You can now create Android App Bundles when publishing your Android applications in Visual Studio. App Bundles provide users with with optimized APKs per their device specifications when downloading an app from the Google Play Store or various Android App Stores.
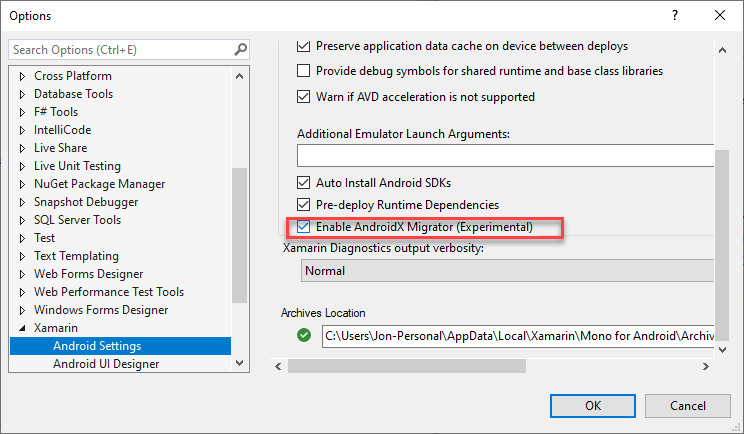
AndroidX Migration Wizard
You can now use an AndroidX migration wizard to convert your existing Android application to AndroidX from the Android Support Library.
Android Layout Linting
You are now provided a set of common issues when editing your layouts inside the Android designer.
Top Issues Fixed in Visual Studio 2019 version 16.4
- Incorrect code generation with Visual Studio 2019 16.3.0
- Could not connect to Mac-Server using Address XXX and User ... Buildprocess cannot continue without connection.
- MSVC 14.23.28019 compilation bug
- System.MethodAccessException: Attempt by method
- Go to definition goes to wrong definition in CRTP scenarios
- VS2019 ComboBox的闪退问题-VS2019 ComboBox's exits problem
- Visual Studio Feedback sign in fails for "Failed to acquire file lock on ... AadConfiguration.lock"
- cmake project file could not be loaded
- ftp publish does not upload all folders
- Mandatory collection of VS System Logs
- Starting Visual Studio 2019 from command line to load CMake project doesn't work.
- VS feedback Tool CRASHED while trying to crop a non-existent screenshot
- Searching and submitting feedback doesn't work for me behind a proxy
- navigate to definition Find symbol results does not list correct symbol
- Visual Studio 2019 crashing consistently when clicking on number of references
- there was an error running the selected code generator "sequence contains no matching element"
- Printing a class diagram
- ADD SENSITIVITY CLASSIFICATION statement support for SSDT
- Feedback Tool does not apply Black High Contrast theme
- test explorer window fails to open
- Retain unit test status after repository update
- Explicit interface bug introduced in Mono 6.4
- Design-Build Error for Debug/Arm when "Setting up your project for Linux Development.
- In VSTO add-in, the VS not letting me create a new WPF class
- Last Visual Studio update broke NTLM authentication on Android (seems like new version of Momo would be a reason)
- Without any changes to source files, "Edits were made which cannot be compile.."
- Show Output window when build starts" not working correctly
- Ability to set runsettings in project file
- C++ highlighter partially stops working after "An exception of type NullReferenceException"
- Pressing semi-colon closes intellisense instead of actually typing it.
- Automatic ANSI .rc file conversion to UTF8 !!! (not wanted !!!)
- Azure Functions projects never hit breakpoints when the "Automatically close the console when debugging stops" option is enabled
- Add area from a Razor Pages project throws "There are no scaffolders supported for this item."
- vs2017rc edit and continue not working
- Non-WPF auto-hidden tool windows can sometimes throw an initialization error
- Null Reference exception thrown by debugger
- Problem using clang-tidy on project using precompiled headers
- Cannot create iOS Archive - Process cannot be executed on XMA server (the path or filename are too long)
- Visual Studio freezes when using git blame
- "Analyse Code Coverage" missing from the test menu
- C++ Intellisense on VS2019 reports incorect errors that Intellisense on VS2017 does not
- explicit operator bool can be invoked implicitly by comparison operators
- CodeLens isn't working
- Very fragile ICE
- Fatal error C1001: when using constexpr template function in the MFC macro ON_COMMAND_RANGE() with a DEBUG build
- Sync with active document while solution explorer is closed selects all files
- Alignas of Structured Bindings (C++17) not working
- VS2019 C++ failed to specialize SFINAE (regression)
- C++ CLI Intellisense incorrectly warns that property has no 'set' accessor
- Xamarin fastlane: "There was an error while syncing the developer information: 'Limit of requests to iTunes Connect is reached.'"
- Intellisense tooltip cut off
- C++ control keywords not showing up in IntelliSense Member List suggestions
- XAML UI debugging tools - incorrect work the Button "Enable selection"
- Function paremeters list is not fully displayed in a popup when calling the function with many parameters.
- Wrong code formatting with ampersand operator v2
- Incorrect detection of support for nodiscard with reason
- Intellisense does not see vcpkg include directories for WSL configuration for CMake project
- error LNK2005: "__cdecl Windows::Foundation::operator co_await(struct Windows::Foundation::IAsyncAction ^)" (?? __LFoundation@Windows@@YA@PE$AAUIAsyncAction@01@@Z) already defined in pch.obj
- VS2019 #pragme message 显示异常-VS2019 #pragme message shows an exception
- Identifier Tag
- VCManagedPackage package did not load correctly when joining LiveShare session
- VS2019 16.2.1 #pragme message shows an exception
- VS2019 Win10 1703 Modeling SDK DiagramClientView blank on reload
- C++/CLR + .Net Core crashes Visual Studio
- C++: wrong code generation for structure copy operation
- Disabling Diagnostic tools resource limits is not persistent
- Test Explorer/CMake is searching for tests before running tests
- VS2019 Preview xaml snippets row and col work badly with IntelliSense
- VS2019 16.3 seems to incorrectly detect AVX512 on Windows 7 64 bit when it is not present
Known Issues
See all issues and available workarounds in Visual Studio 2019 version 16.4 by following the below link.
Feedback and suggestions
We would love to hear from you! For issues, let us know through the Report a Problem option in the upper right-hand
corner of either the installer or the Visual Studio IDE itself. The ![]() icon is located in the upper right-hand corner.
You can make a product suggestion or track your issues in the Visual Studio Developer Community, where you can ask questions, find answers, and propose new features.
You can also get free installation help through our Live Chat support.
icon is located in the upper right-hand corner.
You can make a product suggestion or track your issues in the Visual Studio Developer Community, where you can ask questions, find answers, and propose new features.
You can also get free installation help through our Live Chat support.
Blogs
Take advantage of the insights and recommendations available in the Developer Tools Blogs site to keep you up-to-date on all new releases and include deep dive posts on a broad range of features.
Visual Studio 2019 Release Notes History
For more information relating to past versions of Visual Studio 2019, see the Visual Studio 2019 Release Notes History page.