Exercise - Test your Front Door and WAF policy
The final step is to test the Front Door environment and verify if routing rules are configured correctly to direct web traffic. We also want to test availability of the origin web servers and if cached contents can still be accessed when servers are down.
Test traffic distribution for vehicle registration web app
In Cloud Shell, run the following command to generate the URL for your Front Door endpoint.
echo https://$(az afd endpoint show \ --profile-name vehicleFrontDoor \ --endpoint-name $endpoint \ --resource-group $RG \ --query hostName \ --output tsv)Using a web browser, navigate to the web site at the URL returned in the previous command. This URL is the address of the endpoint you created in the Front Door profile. Verify that the home page of the vehicle registration web app appears. Notice that the name of the web server is shown on the page to let you know which instance is serving your request.
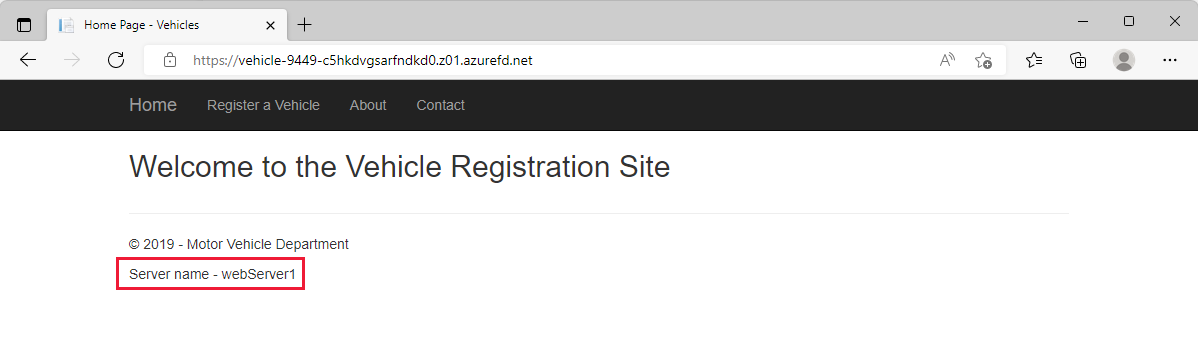
Refresh the browser by pressing F5 a few times on your keyboard. Notice the server name changing back and forth between webServer1 and webServer2. Both web servers are located in the same region and have similar latency. So, both servers have equal chances to serve your requests.
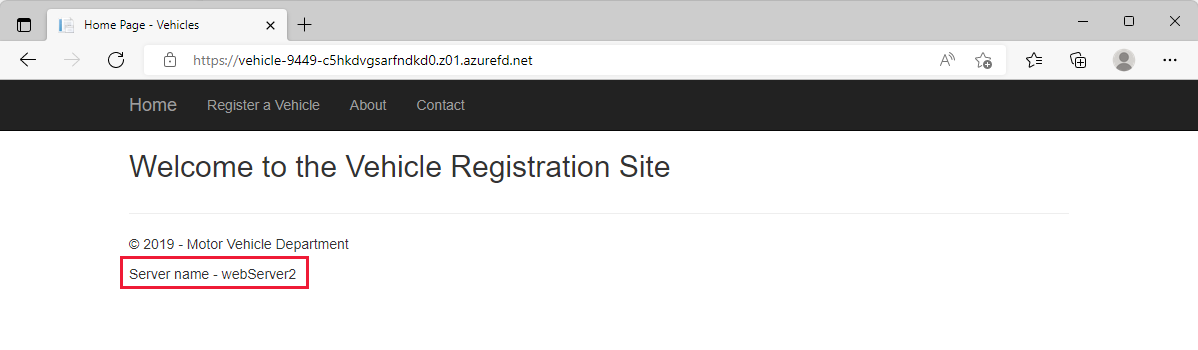
Test routing
Now let's test the routing of the route configuration to each website. You configured a route that matches /VehicleRegistration/ and /VehicleRegistration/* to go to the private endpoint for the web servers. For requests that match /LicenseRenewal/ and /LicenseRenewal/* you routed them to the App service. In this lab, communication between your Azure Front Door and the origin resources are private because you're using Private Link service to establish connectivity.
To test routing to other pages for the Vehicle registration website, select Register a Vehicle.
Notice the URL changed to contain the path
/VehicleRegistration/Create. Since we have a pattern to match of/VehicleRegistration/*, the wildcard matches anything after/and is routed to the web servers hosting the Vehicle registration web site.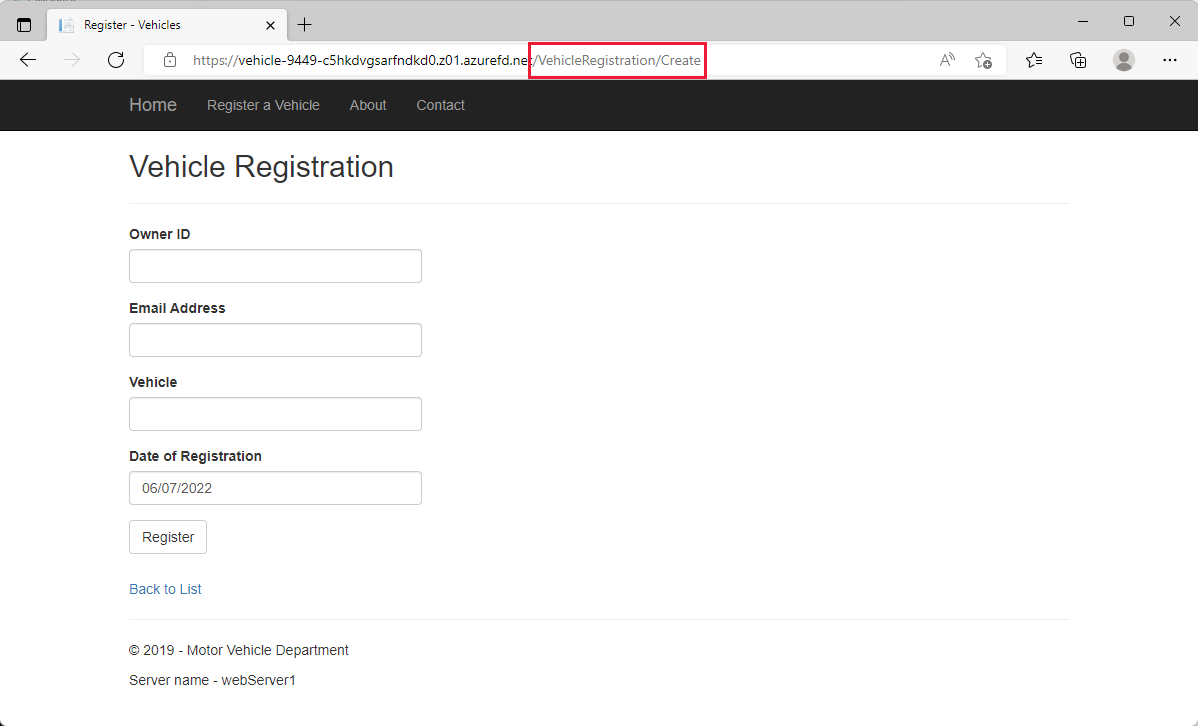
Next let's test routing to license renewal website. Change the path from
/VehicleRegistration/Createto/LicenseRenewal/. This path routes to the App service origin.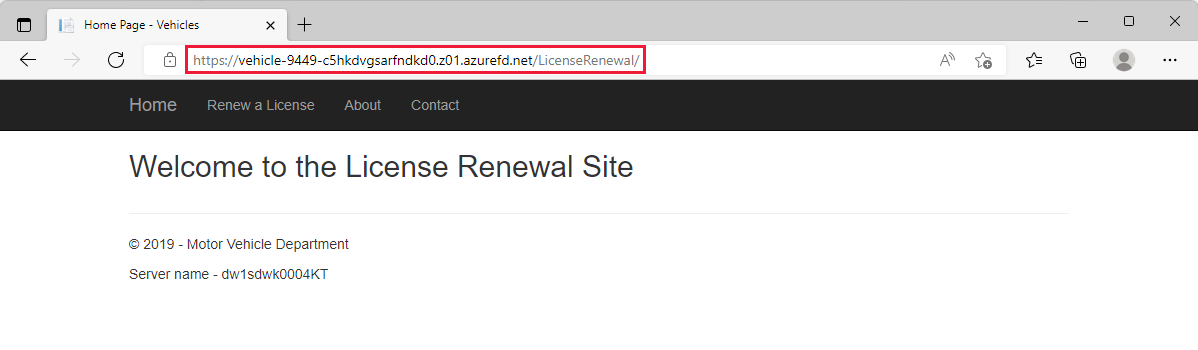
Select Renew a License to see the path change to
/LicenseRenewal/Create. Just like the route for Vehicle registration, there's a pattern to match of/LicenseRenewal/*that has a wildcard to match anything after/and direct that traffic to the App service.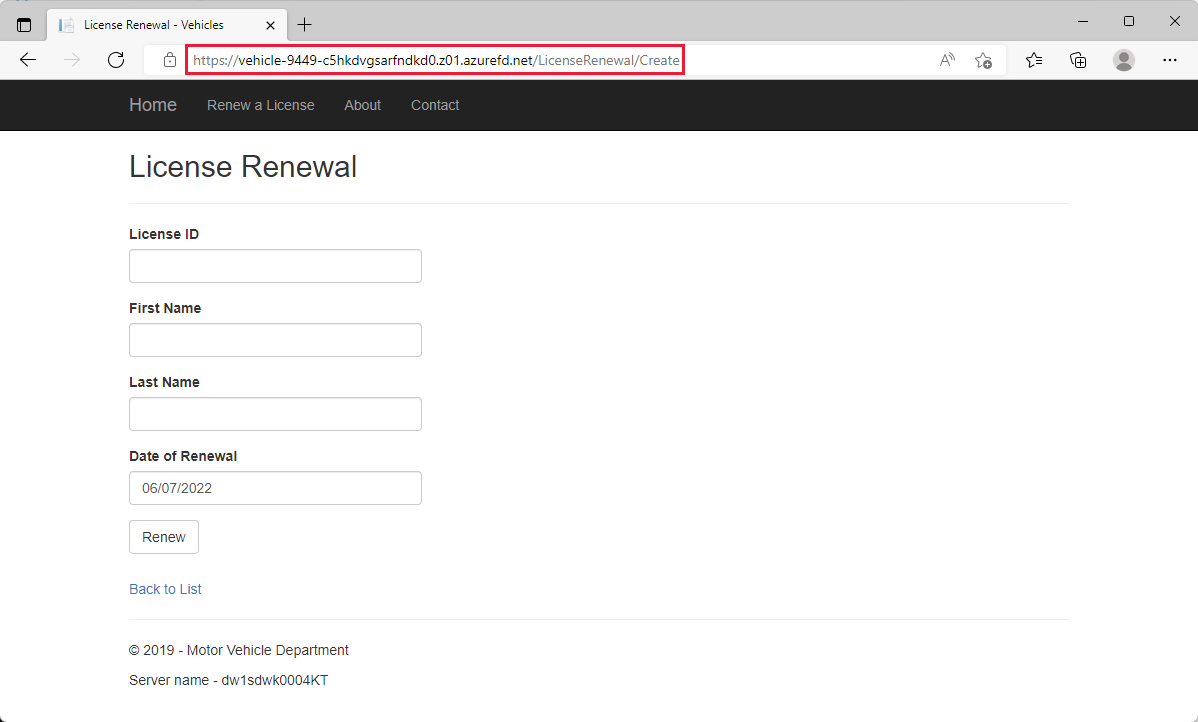
With this configuration, you can direct your users to both web sites through the Front Door. You can set up a custom domain that can easily be remembered and direct users to the correct page for their needs. With Front Door you can expand to host multiple web sites, enable caching to improve performance of static resources, and deliver a high scalable and available web application.
Test security policy
Download and install Go for Windows. Use all default settings during installation. You need Go to run the GoTestWAF application.
Download and install Git for Windows. Use all default settings during installation. You need Git to clone the gotestwaf repository to your local machine.
Once you've installed both Go and Git for Windows, open Git Bash and run
git clone https://github.com/wallarm/gotestwaf.gitto download the GoTestWAF files to your local machine.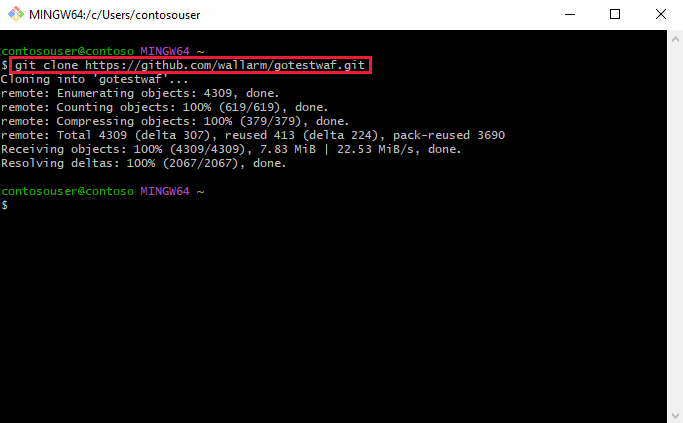
Change the directory to gotestwaf folder with
cd gotestwafcommand.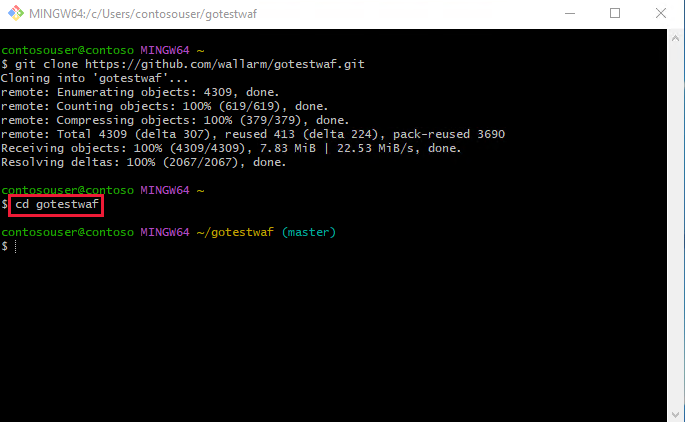
Now run the following command to test if the security policy is working. Replace `<EVALUATE_SECURITY_SOLUTION_URL> with the URL of the endpoint at the beginning of this unit.
go run ./cmd --url=<EVALUATED_SECURITY_SOLUTION_URL> --verboseIf you configured the WAF policy settings correctly, you should see a
Baseline attack status code: 999in the output. This response status code is the same one you configured if WAF blocks a request.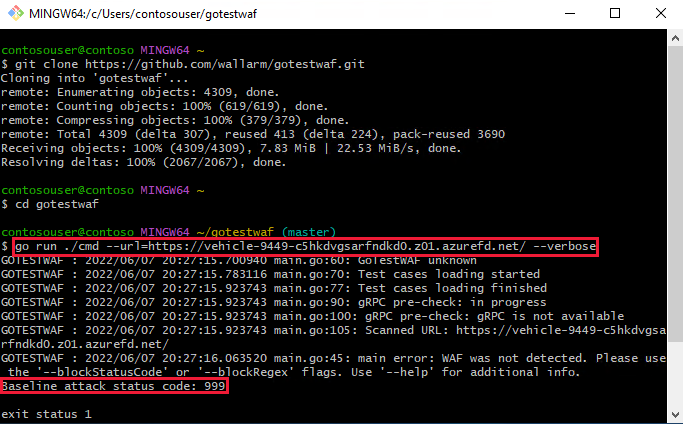
You now have a fully functional motor vehicle web application protected by a Web Application Firewall (WAF) policy.