Minimize internal risks with Microsoft Purview Insider Risk Management
Microsoft Purview Insider Risk Management is a compliance solution that helps minimize internal risks. It does so by enabling organizations to detect, investigate, and act on malicious and inadvertent activities. Insider risk policies enable an organization to define the types of risks it wants to identify and detect. They also enable organizations to act on cases and escalate cases to Microsoft eDiscovery (Premium) if needed. An organization's risk analysts can quickly take appropriate actions to ensure users are compliant with the organization's compliance standards.
Additional viewing. Watch the following short videos to learn how insider risk management can help your organization prevent, detect, and contain risks while prioritizing your organization values, culture, and user experience:
- Insider risk management solution and development (2 minutes)
- Insider risk management workflow (4 minutes)
Important
Insider risk management is currently available in tenants hosted in geographical regions and countries supported by Azure service dependencies. To verify that your organization supports insider risk management, see Azure dependency availability by country/region.
Modern risk pain points
Managing and minimizing risk in your organization starts with understanding the types of risks found in the modern workplace. External events and factors outside of an organization's direct control drive some risks. Conversely, internal events and user activities that organizations can minimize and avoid drive other risks. Some examples are risks from illegal, inappropriate, unauthorized, or unethical behavior and actions by users in your organization. These behaviors include a broad range of internal risks from users:
- Leaks of sensitive data and data spillage
- Confidentiality violations
- Intellectual property (IP) theft
- Fraud
- Insider trading
- Regulatory compliance violations
Users in the modern workplace have access to create, manage, and share data across a broad spectrum of platforms and services. In most cases, organizations have limited resources and tools to identify and mitigate organization-wide risks while also meeting user privacy standards.
Insider risk management uses the full breadth of service and third-party indicators to help organizations quickly identify, triage, and act on risk activity. By using logs from Microsoft 365 and Microsoft Graph, insider risk management enables organizations to define specific policies to identify risk indicators. These policies enable them to identify risky activities and to act to mitigate these risks.
The following principles form the foundation of Insider risk management:
- Transparency. Balance user privacy versus organization risk with privacy-by-design architecture.
- Configurable. Configurable policies based on industry, geographical, and business groups.
- Integrated. Integrated workflow across Microsoft Purview solutions.
- Actionable. Provides insights to enable reviewer notifications, data investigations, and user investigations.
Identify potential risks with analytics
Insider risk analytics enables organizations to conduct an evaluation of potential insider risks without configuring any insider risk policies. This evaluation can help an organization identify potential areas of higher user risk. It can also help determine the type and scope of insider risk management policies it may consider configuring. This evaluation may also help an organization determine needs for extra licensing or future optimization of existing insider risk policies.
Additional reading. For more information about insider risk analytics, see Insider risk management settings: Analytics.
Get started with recommended actions
Whether an organization is setting up insider risk management for the first time or getting started with creating new policies, the recommended actions experience can help it get the most out of insider risk management capabilities. Recommended actions include setting up permissions, choosing policy indicators, creating a policy, and more.
Workflow
The insider risk management workflow helps organizations identify, investigate, and take action to address internal risks. An organization can use actionable insights to quickly identify and act on risky behavior. Organizations can base the insider risk management workflow on:
- Focused policy templates.
- Comprehensive activity signaling across the Microsoft 365 service.
- Alert and case management tools.
The following diagram shows how an organization can use insider risk management workflows to identify and resolve internal risk activities and compliance issues.
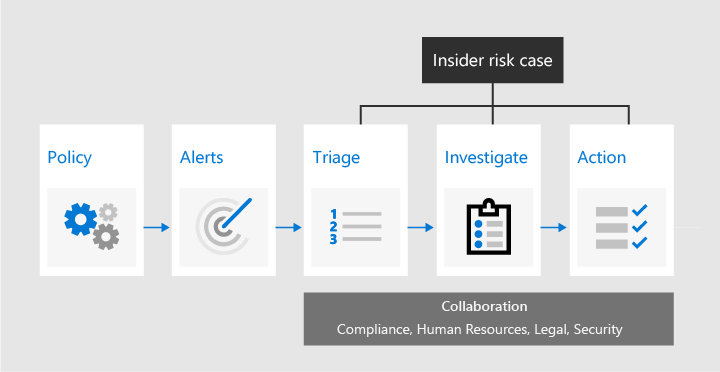
Policies and Policy templates
Insider risk management templates are predefined policy conditions that define the types of risk indicators and risk scoring model used by the policy. Each policy must have a template assigned in the policy creation wizard before it creates the policy. Insider risk management supports up to five policies for each policy template.
The triggering events and policy prerequisites vary depending on the template you choose for an insider risk management policy. Triggering events are prerequisites that determine if a user is active in an insider risk management policy. If you add a user to an insider risk management policy that doesn't have a triggering event, the policy can't evaluate the user's activity. The policy can still evaluate the user if an administrator manually added the user in the Users dashboard.
Policy prerequisites are required items so that the policy receives the signals or activities necessary to evaluate risk.
The following table lists each available insider risk management policy template. For each template, it displays the triggering events and prerequisites for policies created from it.
| Policy template | Triggering events for policies | Prerequisites |
|---|---|---|
| Data theft by departing users | Resignation or termination date indicator from HR connector or Microsoft Entra ID account deletion | (optional) Configure the Microsoft 365 HR connector for termination and resignation date indicators |
| Data leaks | Data leak policy activity that creates a High severity alert or built-in exfiltration event triggers | Configure a DLP policy for High severity alerts OR Customized triggering indicators |
| Data leaks by priority users | Data leak policy activity that creates a High severity alert or built-in exfiltration event triggers | Configure a DLP policy for High severity alerts OR Customized triggering indicators Configure priority user groups in insider risk settings |
| Data leaks by risky users | Performance improvement, poor performance, or job level change indicators from HR connector. Messages containing potentially threatening, harassing, or discriminatory language |
Configure the Microsoft 365 HR connector for disgruntlement indicators AND/OR Communication Compliance integration and dedicated disgruntlement policy |
| Security policy violations | Defense evasion of security controls or unwanted software detected by Microsoft Defender for Endpoint | Active Microsoft Defender for Endpoint subscription Configure Microsoft Defender for Endpoint integration with the Microsoft Purview compliance portal |
| Patient data misuse | Defense evasion of security controls from EMR systems User and patient address matching indicators from HR systems |
Select Healthcare access indicators in a policy or insider risk settings Configure the Microsoft 365 HR connector or address matching Configure the Microsoft Healthcare or Epic connector |
| Risky browser usage | User browsing activity related to security that matches at least one selected Browsing indicator | See the complete list of prerequisites in the browser signal detection article |
| Security policy violations by departing users | Resignation or termination date indicators from HR connector or Microsoft Entra ID account deletion | (optional) Configure the Microsoft 365 HR connector for termination and resignation date indicators Active Microsoft Defender for Endpoint subscription Configure Microsoft Defender for Endpoint integration with the Microsoft Purview compliance portal |
| Security policy violations by priority users | Defense evasion of security controls or unwanted software detected by Microsoft Defender for Endpoint | Active Microsoft Defender for Endpoint subscription Configure Microsoft Defender for Endpoint integration with the Microsoft Purview compliance portal Configure Priority user groups in insider risk settings |
| Security policy violations by risky users | Performance improvement, poor performance, or job level change indicators from HR connector. Messages containing potentially threatening, harassing, or discriminatory language |
Configure the Microsoft 365 HR connector for risk indicators AND/OR Communication Compliance integration and dedicated risky user policy AND Active Microsoft Defender for Endpoint subscription Configure Microsoft Defender for Endpoint integration with the Microsoft Purview compliance portal |
Alerts
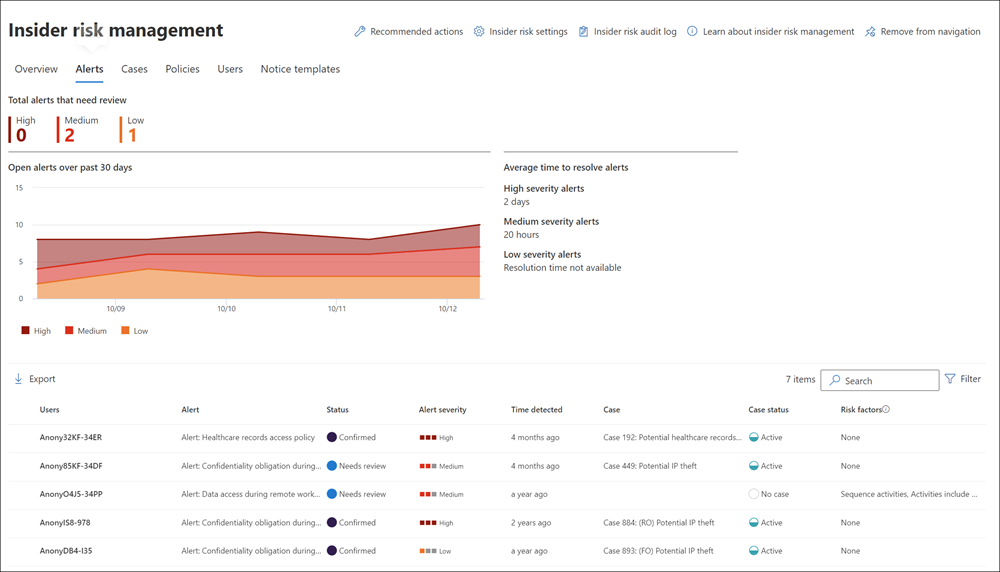
Risk indicators that match policy conditions automatically generate alerts. The Alerts dashboard, which displays alerts, enables a quick view of:
- All alerts needing review
- Open alerts over time
- Alert statistics for the organization
The dashboard displays the following information for each policy alert:
- Status
- Severity
- Time detected
- Case
- Case status
The goal of the dashboard is to help organizations quickly identify the status of existing alerts and new alerts that need action.
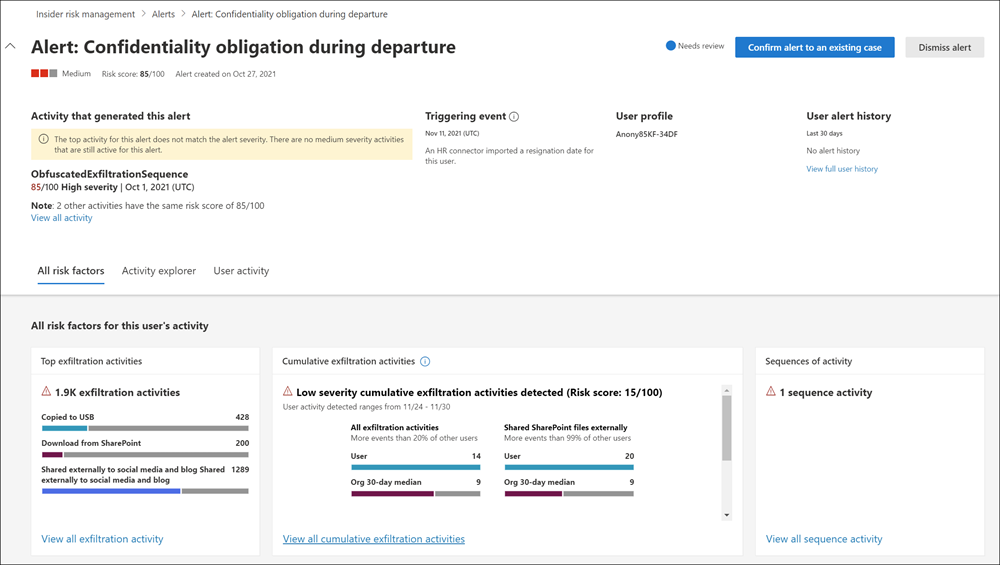
Triage
New user activities that need investigation automatically generate alerts. They assign a Needs review status to the alerts. Reviewers can quickly identify and review, evaluate, and triage these alerts.
Any of the following tasks can resolve an alert:
- Opening a new case
- Assigning an alert to an existing case
- Dismissing an alert
Using alert filters, it's easy to quickly identify alerts by status, severity, or time detected. As part of the triage process, reviewers can:
- View alert details for the activities identified by the policy.
- View user activity associated with the policy match.
- See the severity of the alert.
- Review user profile information.
Investigate
Organizations can quickly investigate all activities for a selected user with User activity reports. These reports enable investigators in an organization to examine activities for specific users for a defined time period. They can do so without having to temporarily or explicitly assign them to an insider risk management policy. After investigators examine activities for a user, they can:
- Dismiss individual activities as benign.
- Share or email a link to the report with other investigators.
- Choose to temporarily or explicitly assign the user to an insider risk management policy.
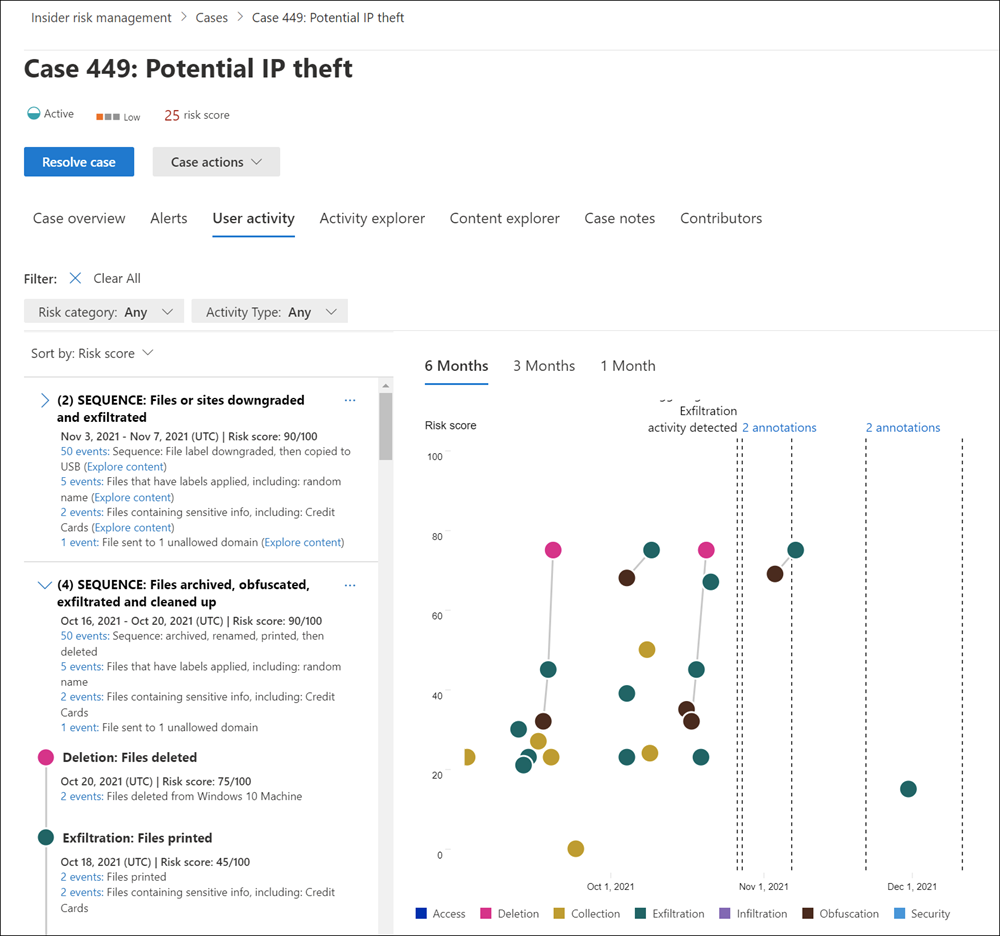
Investigators can create cases for alerts that require deeper review of the activity details and circumstances around the policy match. The Case dashboard provides an all-up view of all active cases, open cases over time, and case statistics for your organization. Reviewers can quickly filter cases by status, the date the investigator opened the case, and the date an investigator last updated the case.
Selecting a case on the Case dashboard opens the case for investigation and review. This step is the heart of the insider risk management workflow. The dashboard synthesizes the following information into an integrated view for reviewers:
- Risk activities
- Policy conditions
- Alert details
- User details
The primary investigation tools in this area are:
- User activity. User activity is automatically displayed in an interactive chart. This chart plots activities over time and by risk level for current or past risk activities. Reviewers can quickly filter and view the entire risk history for the user. They can then drill into specific activities for more details.
- Content explorer. Automatically captures and displays all data files and email messages associated with alert activities. Reviewers can filter and view files and messages by data source, file type, tags, conversation, and many more attributes.
- Case notes. Reviewers can provide notes for a case in the Case Notes section. This list consolidates all notes in a central view and include reviewer and date submitted information.
Additionally, the Insider Risk Management audit log enables you to stay informed of the actions taken on insider risk management features. The audit log allows for an independent review of user actions. The users included in the review must belong to one or more insider risk management role groups.
Action
Once investigators finish investigating a case, reviewers can quickly act to resolve the case or collaborate with other risk stakeholders in their organization. If users accidentally or inadvertently violate policy conditions, the system can automatically send a reminder notice to the user. The system generates reminder notice from reminder notice templates. Organizations can customize the reminder notices to meet their business requirements. These notices may serve as simple reminders or may direct the user to refresher training or guidance to help prevent future risky behavior. For more information, see Insider risk management notice templates.
In more serious situations, a reviewer may need to share the insider risk management case information with other reviewers or services in their organization. Microsoft 365 tightly integrates Insider risk management and other Microsoft Purview solutions to help organizations with end-to-end risk resolution.
- eDiscovery (Premium). Escalating a case for investigation allows you to transfer data and management of the case to Microsoft Purview eDiscovery (Premium). eDiscovery (Premium) provides an end-to-end workflow to preserve, collect, review, analyze, and export content that's responsive to your organization's internal and external investigations. It allows legal teams to manage the entire legal hold notification workflow. To learn more about eDiscovery (Premium) cases, see Overview of Microsoft Purview eDiscovery (Premium).
- Office 365 Management APIs integration. Insider risk management supports exporting alert information to security information and event management (SIEM) services through Office 365 Management APIs. Having access to alert information in the platform that best fits an organization's risk processes gives it more flexibility in how to act on risk activities. To learn more about exporting alert information with Office 365 Management APIs, see Export alerts.
Scenarios
Insider risk management can help organizations detect, investigate, and take action to mitigate internal risks in several common scenarios. The following sections outline these scenarios.
Data theft by departing users
When users leave an organization, either voluntarily or as the result of termination, there's often legitimate concerns that company, customer, and user data are at risk. Users may innocently assume that project data isn't proprietary. They may also take company data for personal gain and in violation of company policy and legal standards.
Insider risk management policies that use the Data theft by departing users policy template automatically detects activities typically associated with this type of theft. With this policy, you automatically receive alerts for suspicious activities associated with data theft by departing users. Tipped off by this alert, you can take appropriate investigative actions. This policy template requires that you configure a Microsoft 365 HR connector for your organization.
Intentional or unintentional leak of sensitive or confidential information
In most cases, users try their best to properly handle sensitive or confidential information. But occasionally, users make mistakes. When they do, they may accidentally share information outside their organization or in violation of its information protection policies. In other circumstances, users may intentionally leak or share sensitive and confidential information with malicious intent and for potential personal gain.
Data leaks policy templates automatically detect activities typically associated with sharing sensitive or confidential information. Organizations can create Insider risk management policies using the following data leaks templates:
- General data leaks
- Data leaks by priority users
- Data leaks by disgruntled users
Intentional or unintentional security policy violations
Users typically have a large degree of control when managing their devices in the modern workplace. This control may include permissions to install or uninstall applications needed in the performance of their duties. The permissions may also enable users to temporarily disable device security features. Whether this activity is inadvertent, accidental, or malicious, this conduct can pose risk to an organization. As such, it's critical that organizations identify this conduct and try to minimize it.
To help identify these risky security activities, the following insider risk management security policy violation templates score security risk indicators. They also use Microsoft Defender for Endpoint alerts to provide insights for security-related activities:
- General security policy violations
- Security policy violations by departing users
- Security policy violations by priority users
- Security policy violations by disgruntled users
Policies for users based on position, access level, or risk history
Users in an organization may have different levels of risk depending on their position, level of access to sensitive information, or risk history. This structure may include:
- Members of an organization's executive leadership team.
- IT administrators that have extensive data and network access privileges.
- Users with a past history of risky activities.
In these circumstances, closer inspection and more aggressive risk scoring are important to help surface alerts for investigation and quick action. To help identify risky activities for these types of users, organizations can create priority user groups and create policies from the following policy templates:
- Security policy violations by priority users
- Data leaks by priority users
Actions and behaviors by disgruntled users
Stressful employment events can affect user behavior in several ways that relate to insider risks. These stressful events may be a poor performance review, a position demotion, or management placing the user on a performance review plan. Though most users don't respond maliciously to these events, the stress of these actions may result in some users taking actions they may not normally consider during normal circumstances.
To help identify these types of risky activities, the following insider risk management policy templates score risk indicators relating to behaviors that may occur near stressful employment events:
- Data leaks by disgruntled users
- Security policy violations by disgruntled users