Restrict retention changes by using Preservation Lock
Organizations in various industries must abide by rules defined by regulatory bodies, such as the Securities and Exchange Commission (SEC). One such rule, SEC Rule 17a-4, affects how organizations deal with data retention. It requires that after an organization turns on a policy for retention, it can't turn off the policy or make it less restrictive.
To meet this regulatory requirement, Microsoft 365 provides a feature known as Preservation Lock. It locks a retention policy or retention label policy so that no one—not even an administrator—can turn off the policy, delete the policy, or make it less restrictive.
You apply Preservation Lock after creating a retention policy or retention label policy. Preservation Lock locks a retention policy or retention label policy so that no one, including Global Administrators, can turn off the policy, delete the policy, or make it less restrictive. This configuration enables organizations to meet regulatory requirements. It also helps them safeguard against rogue administrators.
When you lock a retention policy:
- No one can disable the policy or delete it.
- You can add locations to the policy but not remove them.
- You can extend the retention period but not decrease it.
When you lock a retention label policy:
- No one can disable the policy or delete it.
- You can add locations to the policy but not remove them.
- You can add labels to the policy but not remove them.
In summary, you can increase or extend a locked policy, but you can't reduce or turn it off.
Warning
Before you lock a retention policy or retention label policy, it's critical that you understand the effect that it has on your organization. You should also confirm whether your organization requires it to meet regulatory requirements. Administrators can't disable or delete locked policies after applying the preservation lock.
Configure Preservation Lock after you create a retention policy, or a retention label policy that you publish or autoapply.
Note
Locking a label policy doesn't prevent an administrator from reducing the retention period in a label the administrator included in the locked policy. You can meet that requirement, with other restrictions, when you configure a label to mark items as a regulatory record.
How to implement Preservation Lock
You must use Security and Compliance PowerShell to implement the Preservation Lock feature in Microsoft 365. You can't enable this feature through the Microsoft 365 user interface (UI).
Important
Microsoft purposely built this limitation into Microsoft 365. Because administrators can't disable or delete a policy for retention after applying a preservation lock, Microsoft wanted to safeguard against accidental configuration of this feature. To do so, it didn't include the Preservation Lock feature in the Microsoft 365 UI. Instead, Microsoft 365 requires an administrator to enter a specific PowerShell command to enable Preservation Lock.
All policies for retention and with any configuration support Preservation Lock.
Connect to Security & Compliance PowerShell.
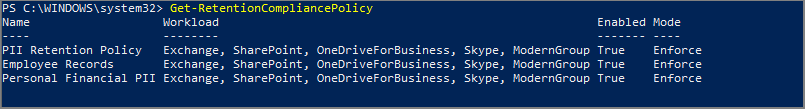
Find the name of the policy that you want to lock by running Get-RetentionCompliancePolicy. For example:
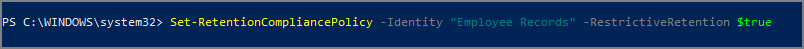
To place a Preservation Lock on your policy, run the Set-RetentionCompliancePolicy cmdlet with the name of the policy, and the RestrictiveRetention parameter set to true:
Set-RetentionCompliancePolicy -Identity "<Name of Policy>" -RestrictiveRetention $trueFor example:
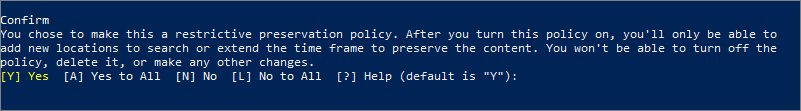
When prompted, read and acknowledge the restrictions that come with this configuration by entering Y:
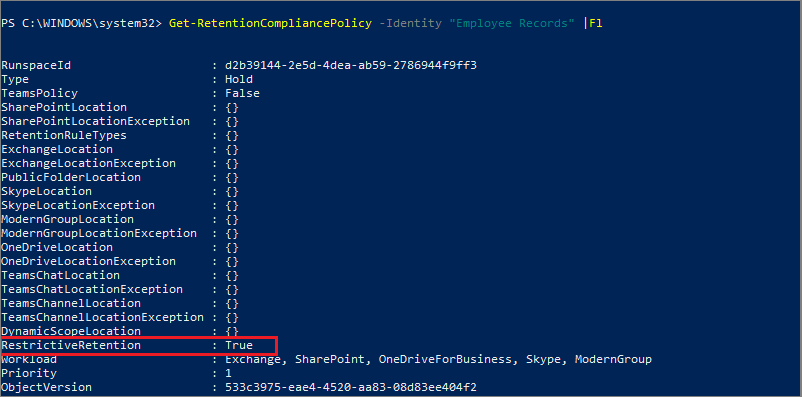
You now placed a Preservation Lock on the policy. If you want to confirm this setting, run Get-RetentionCompliancePolicy again. However, you must specify the policy name and include the |F1 parameter to display the policy settings:
Get-RetentionCompliancePolicy -Identity "<Name of Policy>" |FlIn the list of parameters displayed for this policy, verify the RestrictiveRetention setting equals True. For example:
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”