Configure Microsoft Entra Connect Sync
You must run a setup program to install Microsoft Entra Connect Sync. Because of the ever changing nature of the cloud, it's important to download the latest version of the setup program when you're ready to run it. The setup program initiates a Microsoft Entra Connect Sync installation wizard. The wizard gives you the option of installing Microsoft Entra Connect Sync using one of two setup modes: Express or Custom. The following sections examine each of these setup options.
Microsoft Entra Connect Sync Express setup
Express Settings is the default setup option when installing Microsoft Entra Connect Sync because it supports the most common installation scenario. When an organization runs Express setup, Microsoft Entra Connect Sync deploys synchronization with the password hash synchronization (PHS) option. This option is for a single forest only. By using PHS, organizations can synchronize password hashes to Microsoft Entra ID while retaining full control over password policies and resets on the on-premises infrastructure.
Express setup mode offers several advantages that make it a convenient option for organizations:
- Simplicity and ease of use. The Express setup mode simplifies the installation and configuration process, making it easy for organizations to quickly get started. It provides a streamlined installation experience with default settings that are suitable for most common scenarios.
- Recommended best practices. The Express setup mode automatically applies recommended best practices based on Microsoft's guidelines and industry standards. Doing so helps ensure the Microsoft Entra Connect deployment follows the recommended configurations for optimal functionality, security, and performance.
- Automatic configuration. With the Express setup mode, Microsoft Entra Connect Sync automatically configures key components, such as password hash synchronization (PHS) and device writeback, based on the information provided during the installation process. This process eliminates the need for manual configuration and reduces the chances of errors or misconfigurations.
- Seamless directory synchronization. Microsoft Entra Connect Sync in Express setup mode enables seamless synchronization of user accounts, passwords, and other attributes from the on-premises Active Directory to Microsoft Entra ID. This feature ensures that user identities and attributes remain up to date in the cloud, enabling consistent access and management across on-premises and cloud resources.
- Integration with Microsoft Entra ID features. The Express setup mode enables integration with various Microsoft Entra ID features and services, such as self-service password reset, group-based licensing, and dynamic group membership. These features enhance the overall functionality and user experience within the Microsoft Entra ID environment.
- Future updates and maintenance. When organizations use Express setup mode, they benefit from automated future updates and maintenance. Microsoft Entra Connect Sync regularly receives updates and improvements. The Express setup mode ensures that organizations can easily stay up to date with the latest features and enhancements without extra manual intervention.
Overall, the Express setup mode is ideal for organizations seeking a straightforward and recommended approach to quickly deploy and configure Microsoft Entra Connect Sync with minimal effort and expertise required.
During installation of Microsoft Entra Connect Sync with Express Settings, the installer will:
- Install the synchronization engine.
- Configure Microsoft Entra Connect Sync.
- Configure the on-premises Active Directory connector.
- Enable password hash synchronization.
- Configure synchronization services.
- Configure sync services for Exchange hybrid deployment (optional).
- Enable automatic upgrade of Microsoft Entra Connect Sync.
When installing Microsoft Entra Connect Sync using the Express Settings option, you can optionally choose to start the synchronization process once the installation is complete.
The Microsoft Entra Connect Sync server installation process configures Active Directory, Microsoft Entra ID, and the local machine for identity synchronization.
Microsoft Entra Connect Sync Custom setup
While the Express setup mode offers simplicity and convenience, it might not cover all advanced configuration options or an organization's specific customization needs. In such cases, you can choose the Custom setup mode. This option provides more flexibility and granular control over the installation and configuration process.
Organizations can select the Customized Settings option when they require optional features not covered in Express setup. Organizations use the Customized Settings option for various reasons, including:
- They have multiple forests.
- They want to use single sign-on (passwords hash synchronization plus pass-through authentication), or just password hash synchronization, or AD FS (federation) for their sign-in option.
- They use a non-Microsoft identity provider.
- They have customized synchronization features, such as filtering or writeback.
A Custom setup installs two types of components: the same required components installed in an Express setup, plus the following optional components selected during Custom setup installation:
- Specify a custom installation location. Enables you to specify a different installation path to install Microsoft Entra Connect.
- Use an existing server running SQL Server. Enables you to select an existing SQL database server.
- Use an existing service account. Enables you to specify an existing service account. By default, Microsoft Entra Connect Sync creates a local service account for the synchronization services to use. Microsoft Entra Connect Sync automatically generates the password, which remains unknown to the person running the installation. If you specify a remote server running SQL Server, then you need a service account for which you know the password.
- Specify custom sync groups. Enables you to specify existing management groups for Microsoft Entra Connect Sync. By default, Microsoft Entra Connect Sync creates the following groups on the server when the synchronization services install: Administrators group, Operators group, Browse group, and Password Reset group. Use this option if you prefer to specify your own groups. The groups must be local on the server and can't be in the domain.
You can enable the following features when you run Microsoft Entra Connect Custom setup:
| Feature | Description | When to use it? |
|---|---|---|
| Select the single sign-on (SSO) method. | This feature allows you to specify the SSO method for users. The SSO methods include password hash synchronization, pass-through authentication, federation with AD FS, and Don't configure SSO. You can also select the option to enable single sign-on. | The organization wants to enable its users for SSO. |
| Connect multiple on-premises directories or forests. | This feature allows you to connect to one or more Active Directory domains or forests. | The organization has multiple forests to connect to one Microsoft Entra tenant. |
| Matching across forests. | This feature allows you to define how Microsoft Entra ID represents users from your Active Directory forests. You can either represent a user only once across all forests, or you can have a combination of enabled and disabled accounts. | The organization has multiple forests to connect to one Microsoft Entra tenant. |
| Sync filtering based on organizational units. | This feature allows you to run a small pilot where you create only a small subset of objects in Microsoft Entra ID and Microsoft 365. To use this feature, create an organizational unit in your on-premises Active Directory and add the users and groups that should synchronize from the OU to Microsoft Entra ID. You can later add and remove users to this group to maintain the list of objects that should be present in Microsoft Entra ID. | The organization only wants to sync specific OUs or items to Microsoft Entra ID. |
| Select the source anchor. | This feature allows you to choose the primary key (that is, the ImmutableID) that links the on-premises user with the user in Microsoft Entra ID. | The organization must change the source anchor, such as when it has multi-forests. |
| Select the sign-in attribute. | This feature allows you to choose the attribute users use when they sign in to Microsoft Entra ID and Microsoft 365. Typically, this attribute is the userPrincipalName attribute. But if this attribute is nonroutable and the system can't verify it, then it's possible to select another attribute. For example, email, as the attribute holding the sign-in ID, known as Alternate ID. | The organization wants to use UPNs for user sign-in. |
| Exchange hybrid deployment. | This optional feature enables coexistence of Exchange mailboxes, both on-premises and in Microsoft 365. It does so by synchronizing a specific set of attributes from Microsoft Entra ID back to your on-premises Active Directory. | The organization currently has Exchange on-premises installed and it plans to move mailboxes to Exchange Online. |
| Exchange mail public folders. | This feature allows you to synchronize mail-enabled public folders from your on-premises Active Directory to Microsoft Entra ID to support EOP’s directory-based edge blocking (DBEB). | The organization currently uses mail-enabled public folders on-premises. |
| Microsoft Entra app and attribute filtering. | This optional feature enables you to tailor the set of synchronized attributes to a specific set, based on Microsoft Entra apps. | The organization currently uses Microsoft Entra apps. |
| Password writeback. | This feature enables the system to write password changes that originate in Microsoft Entra ID back to your on-premises Active Directory. You typically deploy this feature when you want to enable users for self-service password reset of their Microsoft Entra passwords. | The organization wants to allow users to change their password in the Microsoft 365 portal or other areas. |
| Group writeback. | With this feature, if you use the Microsoft 365 Groups feature, then you can have these groups in your on-premises Active Directory as a distribution group. This option is only available if you deploy Exchange Server on-premises. | The organization has an Exchange hybrid deployment and uses Microsoft 365 groups. |
| Device writeback. | With this feature, the system writes device objects in Microsoft Entra ID back to your on-premises Active Directory for conditional access scenarios. | The organization plans to implement conditional access for its mobile devices. |
| Directory extension attribute sync. | This feature enables you to extend the schema in Microsoft Entra ID with custom attributes added by your organization or other attributes in your on-premises Active Directory. | The organization extended its on-premises Active Directory schema with custom attributes. |
One of the key reasons an organization might run the Microsoft Entra Connect Sync installation program in Custom setup mode is the single sign-on (SSO) option. If you select the option to enable SSO, the installation program configures both password hash synchronization (PHS) and Microsoft Entra pass-through authentication (PTA). If you don't select the option to enable SSO, the installation program only enables PHS, which is the default option when running the installation program in Express setup mode.
Enabling SSO with both password hash synchronization (PHS) and pass-through authentication (PTA) provides a more comprehensive authentication solution. However, there can be reasons why an organization chooses not to enable SSO and opts for PHS only, such as:
- Simplicity and minimal infrastructure. Implementing and managing PHS alone requires fewer components and infrastructure changes compared to setting up PTA or SSO. If an organization prefers a simpler deployment that doesn't require the advanced capabilities of PTA or SSO, they can use PHS as the primary authentication method.
- On-premises password management. Some organizations might have specific requirements or policies that dictate managing user passwords solely within the on-premises Active Directory environment. By using PHS, organizations can synchronize password hashes to Microsoft Entra ID while retaining full control over password policies and resets on the on-premises infrastructure.
- Compliance and regulatory considerations. In certain industries or regulatory environments, organizations might have strict compliance requirements that restrict the use of certain authentication methods or dictate specific password handling procedures. By using PHS alone, organizations can align with these requirements while still benefiting from password synchronization to Microsoft Entra ID.
- Existing identity and access management infrastructure. Organizations with well-established identity and access management (IAM) systems and processes might already have robust authentication mechanisms in place, such as smart cards, certificates, or third-party federation services. In such cases, they might prefer to rely on their existing infrastructure for authentication and use PHS for synchronizing passwords to Microsoft Entra ID. Doing so would save them from introducing more components like PTA or SSO.
- Limited on-premises infrastructure availability. If an organization's on-premises infrastructure has limited availability due to connectivity or resource constraints, implementing PTA or SSO might not be feasible. In such cases, PHS provides a viable option for password synchronization to Microsoft Entra ID without the need for real-time validation against the on-premises Active Directory.
It's important to note that PHS still offers benefits such as password synchronization, reduced password fatigue for users, and the ability to apply on-premises password policies. While PTA and SSO provide more capabilities for enhanced user experience and real-time authentication, organizations might choose PHS alone based on their specific requirements, infrastructure limitations, or compliance considerations.
Enabling SSO in Microsoft Entra Connect Sync, which configures both Password Hash Synchronization (PHS) and Pass-through Authentication (PTA), offers several advantages over using only PHS without SSO, including:
- Seamless user experience. With SSO enabled, users can sign in to Microsoft Entra ID and Microsoft 365 services using their on-premises Active Directory credentials. They don't need to enter their credentials multiple times, reducing the need for password re-entry and enhancing the user experience.
- Reduced password management. With SSO and PHS/PTA, users can use their on-premises passwords to authenticate to Microsoft Entra ID and Microsoft 365 services. Doing so eliminates the need for users to remember and manage separate passwords for cloud services, reducing password-related issues and simplifying password management.
- Authentication options. SSO with PHS/PTA provides flexibility in authentication methods. Users can authenticate using password hash synchronization (PHS) when on-premises Active Directory is reachable. Or, they can fall back to pass-through authentication (PTA) when the on-premises infrastructure is unavailable. This flexibility ensures continuous access to cloud services even during on-premises infrastructure disruptions.
- On-premises password policies. By using SSO with PHS/PTA, organizations can enforce their on-premises Active Directory password policies for cloud authentication. These policies can consistently apply password complexity requirements, expiration policies, and other password-related settings across on-premises and cloud environments.
- Security enhancements. SSO with PHS/PTA adds another layer of security compared to using only PHS. PTA verifies user credentials directly against the on-premises Active Directory. This process provides real-time authentication validation and reduces the risk of compromised or stolen passwords.
- Flexible deployment. SSO with PHS/PTA can be beneficial in hybrid environments, where organizations have a combination of on-premises and cloud resources. It provides a unified authentication experience, allowing users to seamlessly access resources both on-premises and in the cloud using their existing credentials.
The following diagram shows the authentication process using pass-through authentication.
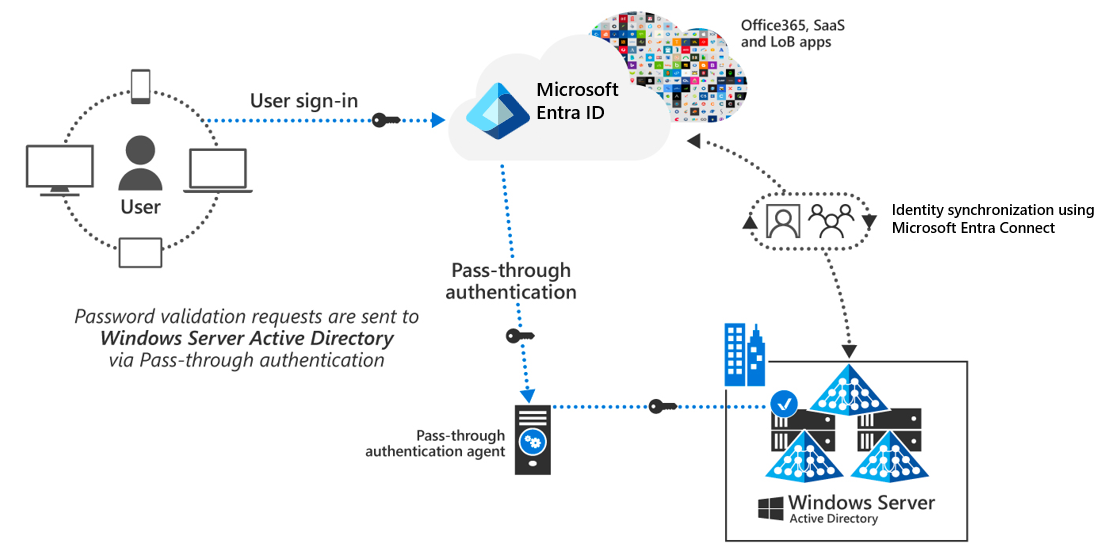
If you have an existing Active Directory Federation Services (AD FS) deployment in a federated environment, you can identify this configuration during the installation process. If you select the option to enable SSO, the installation program not only configures PHS and PTA, but it also provides an option to configure AD FS. If you select this AD FS option, the installation program prompts you to enter the required federation information. For example, the AD FS server farm name, service account, and the TLS/SSL certificate for AD FS.
When installing Microsoft Entra Connect Sync using the Custom Settings option, you can optionally choose to start the synchronization process once the installation is complete.
You can also choose to enable staging mode. This process allows you to set up a new directory synchronization server in parallel with an existing server. Microsoft 365 only supports one directory synchronization server connected to one Microsoft Entra directory in the cloud. If you want an extra backup server for your directory synchronization setup, you can enable Microsoft Entra Connect Sync in staging mode. When enabled, the sync engine imports and synchronizes data as normal. However, it doesn't export anything to Microsoft Entra ID. It also turns off password hash synchronization and password writeback.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”