With inbound settings, you select which external users and groups are able to access the internal applications you choose. Whether you're configuring default settings or organization-specific settings, the steps for changing inbound cross-tenant access settings are the same. As described in this section, you navigate to either the Default tab or an organization on the Organizational settings tab, and then make your changes.
Sign in to the Microsoft Entra admin center as at least a Security Administrator.
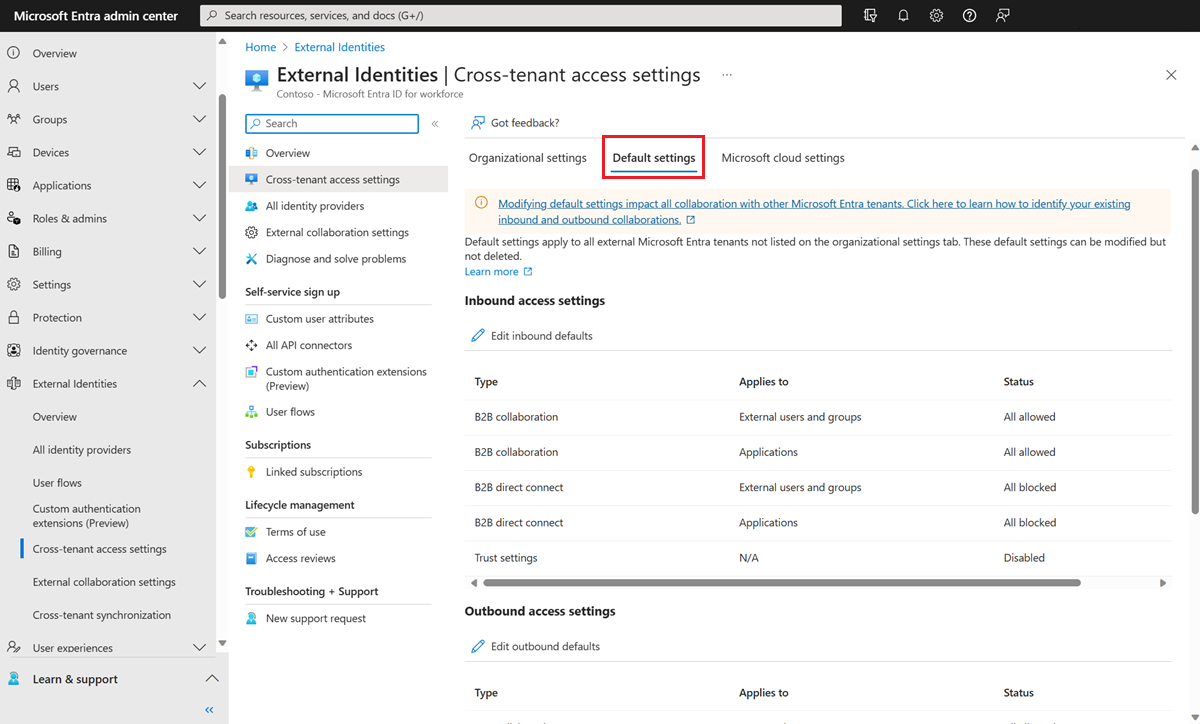
Browse to Identity > External Identities > Cross-tenant access settings.
Navigate to the settings you want to modify:
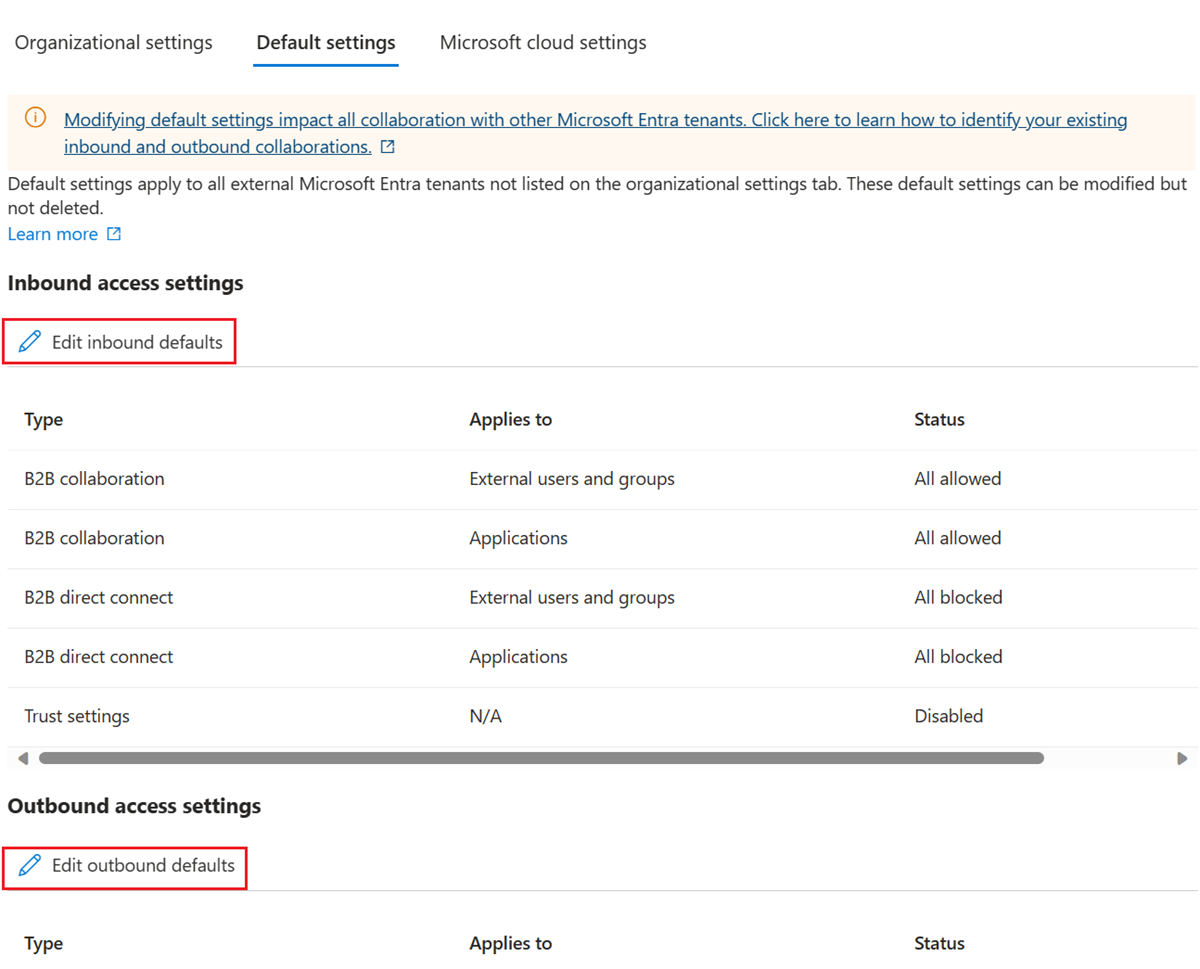
- Default settings: To modify default inbound settings, select the Default settings tab, and then under Inbound access settings, select Edit inbound defaults.
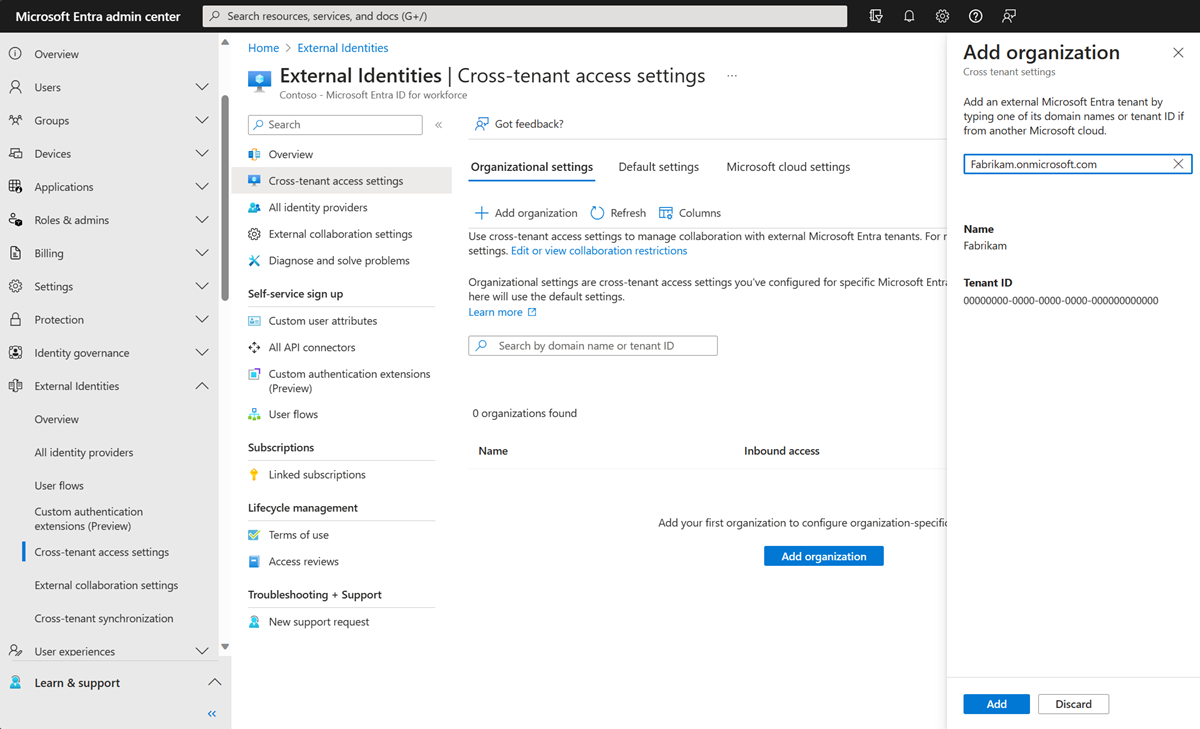
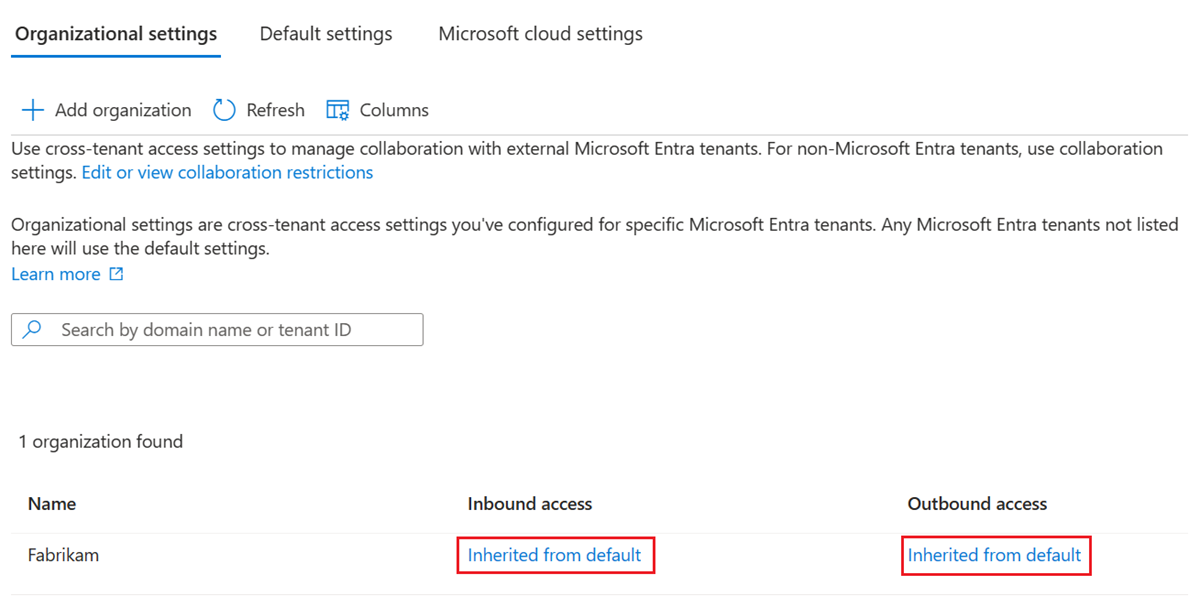
- Organizational settings: To modify settings for a specific organization, select the Organizational settings tab, find the organization in the list (or add one), and then select the link in the Inbound access column.
Follow the detailed steps for the inbound settings you want to change:
To change inbound B2B collaboration settings
Sign in to the Microsoft Entra admin center as at least a Security Administrator.
Browse to Identity > External Identities > Cross-tenant access settings, then select Organizational settings
Select the link in the Inbound access column and the B2B collaboration tab.
If you're configuring inbound access settings for a specific organization, select an option:
Default settings: Select this option if you want the organization to use the default inbound settings (as configured on the Default settings tab). If customized settings were already configured for this organization, you need to select Yes to confirm that you want all settings to be replaced by the default settings. Then select Save, and skip the rest of the steps in this procedure.
Customize settings: Select this option if you want to customize the settings to enforce for this organization instead of the default settings. Continue with the rest of the steps in this procedure.
Select External users and groups.
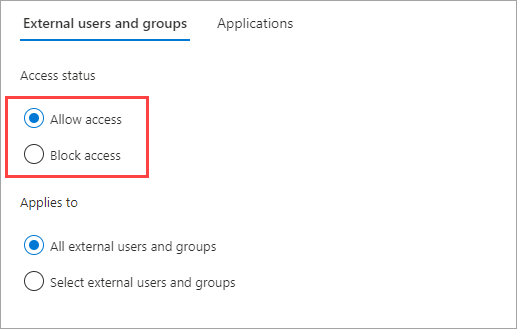
Under Access status, select one of the following:
- Allow access: Allows the users and groups specified under Applies to to be invited for B2B collaboration.
- Block access: Blocks the users and groups specified under Applies to from being invited to B2B collaboration.
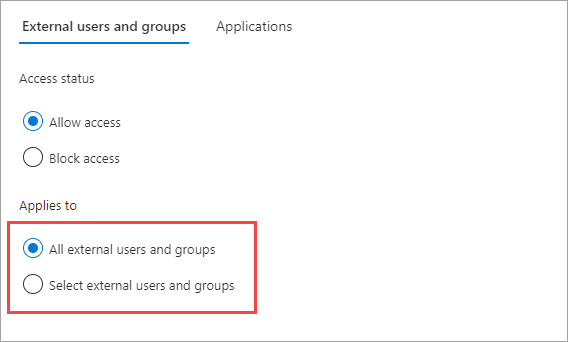
Under Applies to, select one of the following:
- All external users and groups: Applies the action you chose under Access status to all users and groups from external Microsoft Entra organizations.
- Select external users and groups (requires a Microsoft Entra ID P1 or P2 subscription): Lets you apply the action you chose under Access status to specific users and groups within the external organization.
Note
If you block access for all external users and groups, you also need to block access to all your internal applications (on the Applications tab).
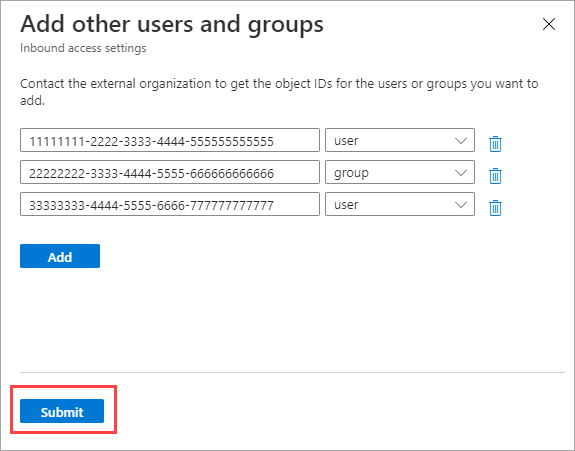
If you chose Select external users and groups, do the following for each user or group you want to add:
- Select Add external users and groups.
- In the Add other users and groups pane, in the search box, type the user object ID or group object ID you obtained from your partner organization.
- In the menu next to the search box, choose either user or group.
- Select Add.
Note
You can't target users or groups in inbound default settings.
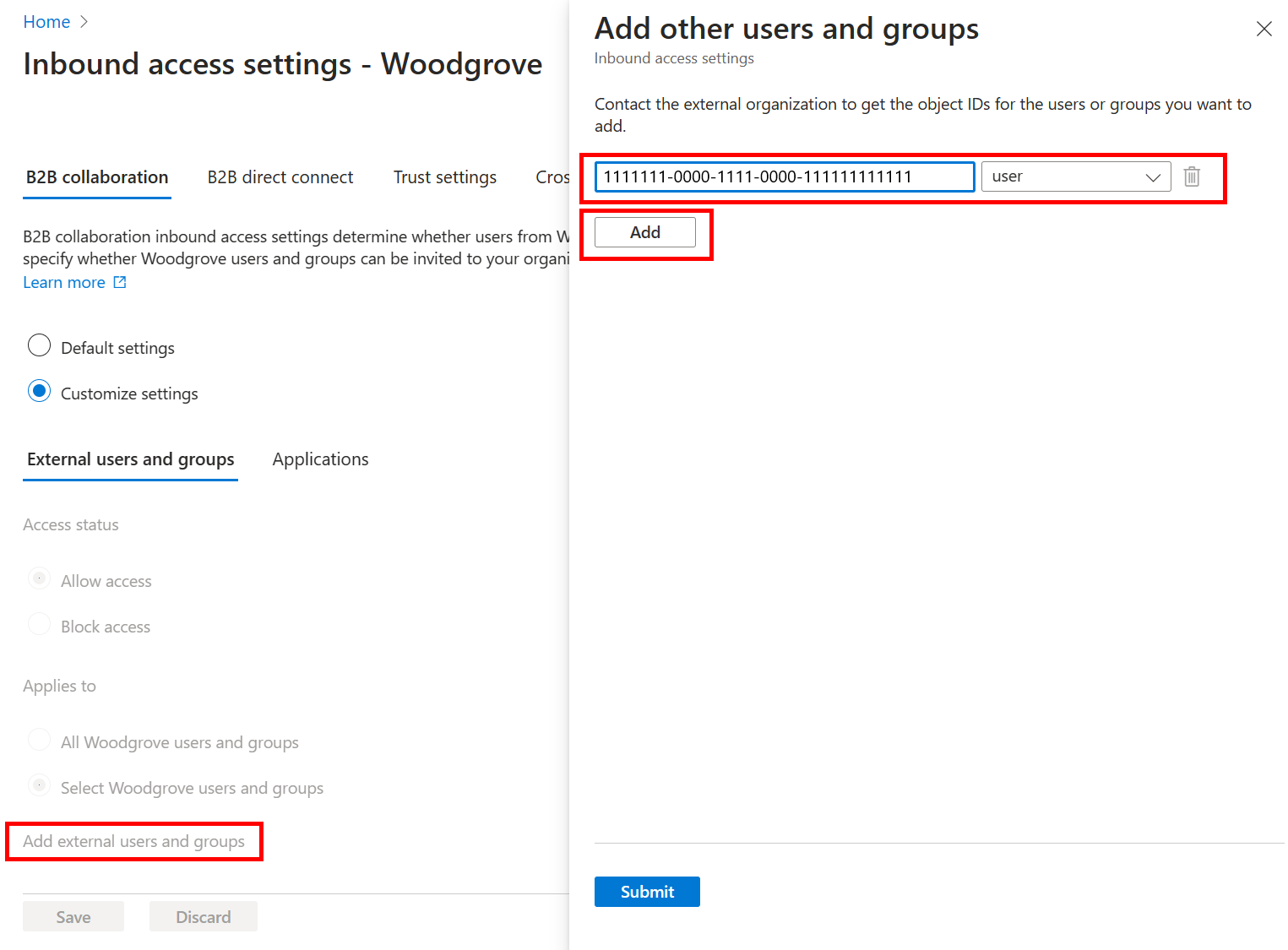
When you're done adding users and groups, select Submit.
Select the Applications tab.
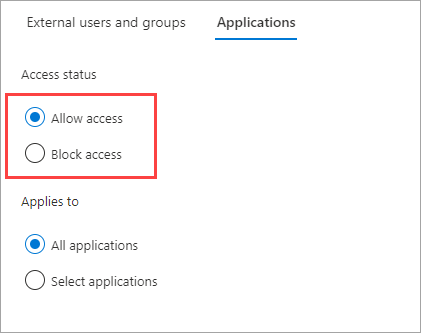
Under Access status, select one of the following:
- Allow access: Allows the applications specified under Applies to to be accessed by B2B collaboration users.
- Block access: Blocks the applications specified under Applies to from being accessed by B2B collaboration users.
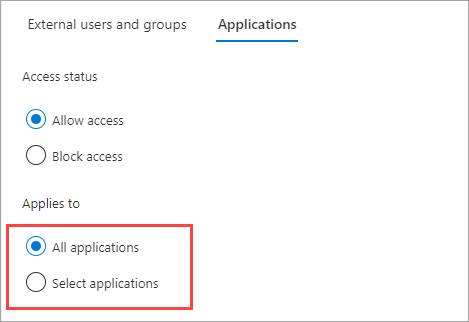
Under Applies to, select one of the following:
- All applications: Applies the action you chose under Access status to all of your applications.
- Select applications (requires a Microsoft Entra ID P1 or P2 subscription): Lets you apply the action you chose under Access status to specific applications in your organization.
Note
If you block access to all applications, you also need to block access for all external users and groups (on the External users and groups tab).
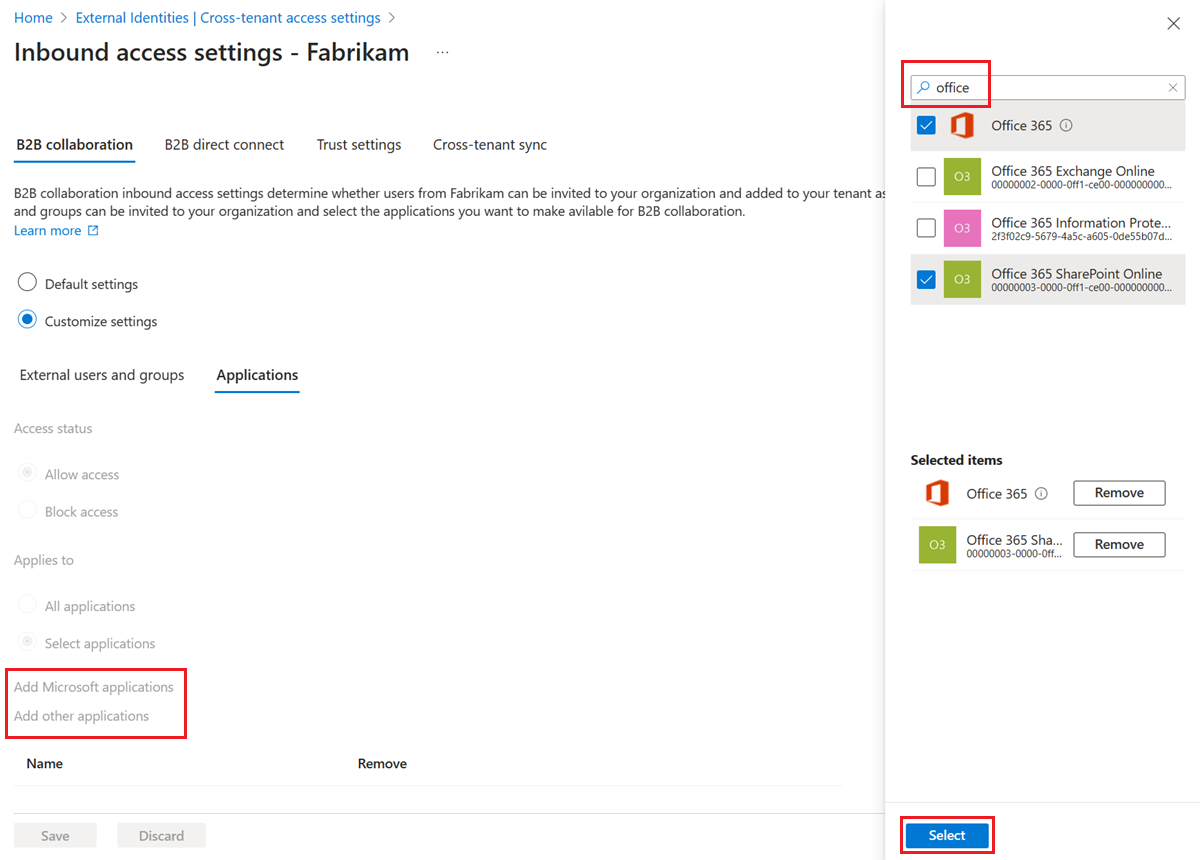
If you chose Select applications, do the following for each application you want to add:
- Select Add Microsoft applications or Add other applications.
- In the Select pane, type the application name or the application ID (either the client app ID or the resource app ID) in the search box. Then select the application in the search results. Repeat for each application you want to add.
- When you're done selecting applications, choose Select.
Select Save.
Considerations for allowing Microsoft applications
If you want to configure Cross-tenant access settings to allow only a designated set of applications, consider adding the Microsoft applications shown in the following table. For example, if you configure an allow list and only allow SharePoint Online, the user can't access My Apps or register for MFA in the resource tenant. To ensure a smooth end user experience, include the following applications in your inbound and outbound collaboration settings.
| Application |
Resource ID |
Available in portal |
Details |
| My Apps |
2793995e-0a7d-40d7-bd35-6968ba142197 |
Yes |
Default landing page after redeemed invitation. Defines access to myapplications.microsoft.com. |
| Microsoft App Access Panel |
0000000c-0000-0000-c000-000000000000 |
No |
Used in some late-bound calls when loading certain pages within My Sign ins. For example, the Security Info blade or the Organizations switcher. |
| My Profile |
8c59ead7-d703-4a27-9e55-c96a0054c8d2 |
Yes |
Defines access to myaccount.microsoft.com including My Groups and My Access portals. Some tabs within My Profile require the other apps listed here in order to work. |
| My Sign ins |
19db86c3-b2b9-44cc-b339-36da233a3be2 |
No |
Defines access to mysignins.microsoft.com including access to Security Info. Allow this app if you require users to register for and use MFA in the resource tenant (for example, MFA isn't trusted from the home tenant). |
Some of the applications in the previous table don't allow selection from the Microsoft Entra admin center. To allow them, add them with Microsoft Graph API as shown in the following example:
PATCH https://graph.microsoft.com/v1.0/policies/crossTenantAccessPolicy/partners/<insert partner’s tenant id>
{
"b2bCollaborationInbound": {
"applications": {
"accessType": "allowed",
"targets": [
{
"target": "2793995e-0a7d-40d7-bd35-6968ba142197",
"targetType": "application"
},
{
"target": "0000000c-0000-0000-c000-000000000000",
"targetType": "application"
},
{
"target": "8c59ead7-d703-4a27-9e55-c96a0054c8d2",
"targetType": "application"
},
{
"target": "19db86c3-b2b9-44cc-b339-36da233a3be2",
"targetType": "application"
}
]
}
}
}
Note
Be sure to include any additional applications you want to allow in the PATCH request as this will overwrite any previously configured applications. Applications that are already configured can be retrieved manually from the portal or by running a GET request on the partner policy. For example, GET https://graph.microsoft.com/v1.0/policies/crossTenantAccessPolicy/partners/<insert partner's tenant id>
Note
Applications added via Microsoft Graph API that do not map to an application available in the Microsoft Entra admin center will be displayed as the app ID.
You can't add the Microsoft Admin Portals app to the inbound and outbound cross-tenant access settings in the Microsoft Entra admin center. To allow external access to Microsoft admin portals, use the Microsoft Graph API to individually add the following apps that are part of the Microsoft Admin Portals app group:
- Azure portal (c44b4083-3bb0-49c1-b47d-974e53cbdf3c)
- Microsoft Entra admin center (c44b4083-3bb0-49c1-b47d-974e53cbdf3c)
- Microsoft 365 Defender Portal (80ccca67-54bd-44ab-8625-4b79c4dc7775)
- Microsoft Intune Admin Center (80ccca67-54bd-44ab-8625-4b79c4dc7775)
- Microsoft Purview Compliance Portal (80ccca67-54bd-44ab-8625-4b79c4dc7775)
To customize the order of identity providers that your guest users can use to sign in when they accept your invitation, follow these steps.
Sign in to the Microsoft Entra admin center as at least a Security Administrator. Then open the Identity service on the left hand side.
Select External Identities > Cross-tenant access settings.
On the Default settings tab, under Inbound access settings, select Edit inbound defaults.
On the B2B collaboration tab, select the Redemption order tab.
Move the identity providers up or down to change the order in which your guest users can sign in when they accept your invitation. You can also reset the redemption order to the default settings here.
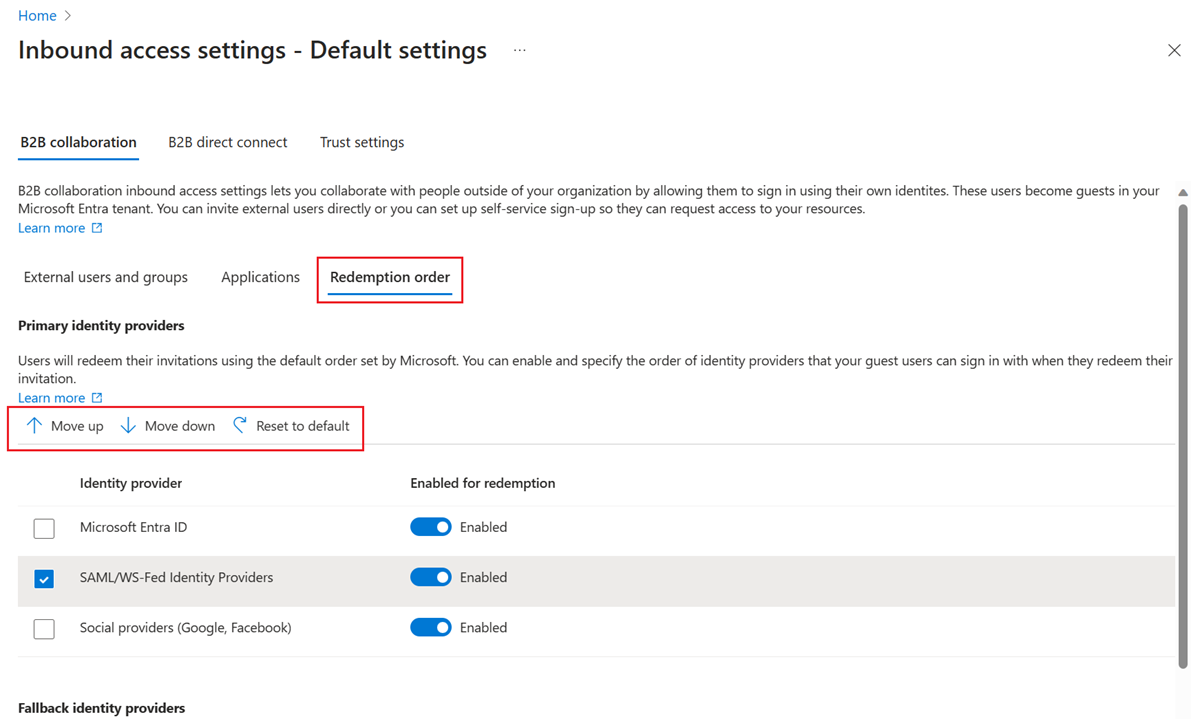
Select Save.
You can also customize the redemption order via the Microsoft Graph API.
Open the Microsoft Graph Explorer.
Sign in as at least a Security Administrator to your resource tenant.
Run the following query to get the current redemption order:
GET https://graph.microsoft.com/beta/policies/crossTenantAccessPolicy/default
- In this example, we'll move the SAML/WS-Fed IdP federation to the top of the redemption order above Microsoft Entra identity provider. Patch the same URI with this request body:
{
"invitationRedemptionIdentityProviderConfiguration":
{
"primaryIdentityProviderPrecedenceOrder": ["ExternalFederation ","AzureActiveDirectory"],
"fallbackIdentityProvider": "defaultConfiguredIdp "
}
}
To verify the changes run the GET query again.
To reset the redemption order to the default settings, run the following query:
{
"invitationRedemptionIdentityProviderConfiguration": {
"primaryIdentityProviderPrecedenceOrder": [
"azureActiveDirectory",
"externalFederation",
"socialIdentityProviders"
],
"fallbackIdentityProvider": "defaultConfiguredIdp"
}
}
SAML/WS-Fed federation (Direct federation) for Microsoft Entra ID verified domains
You can now add your enlisted Microsoft Entra ID verified domain to set up the direct federation relationship. First you need to set up the Direct federation configuration in the admin center or via the API. Make sure that the domain isn't verified in the same tenant.
Once the configuration is set up, you can customize the redemption order. The SAML/WS-Fed IdP is added to the redemption order as the last entry. You can move it up in the redemption order to set it above Microsoft Entra identity provider.
Prevent your B2B users from redeeming an invite using Microsoft accounts
To prevent your B2B guest users from redeeming their invite using their existing Microsoft accounts or creating a new one to accept the invitation, follow the steps below.
Sign in to the Microsoft Entra admin center as at least a Security Administrator. Then open the Identity service on the left hand side.
Select External Identities > Cross-tenant access settings.
On the Default settings tab, under Inbound access settings, select Edit inbound defaults.
On the B2B collaboration tab, select the Redemption order tab.
Under Fallback identity providers disable Microsoft service account (MSA).
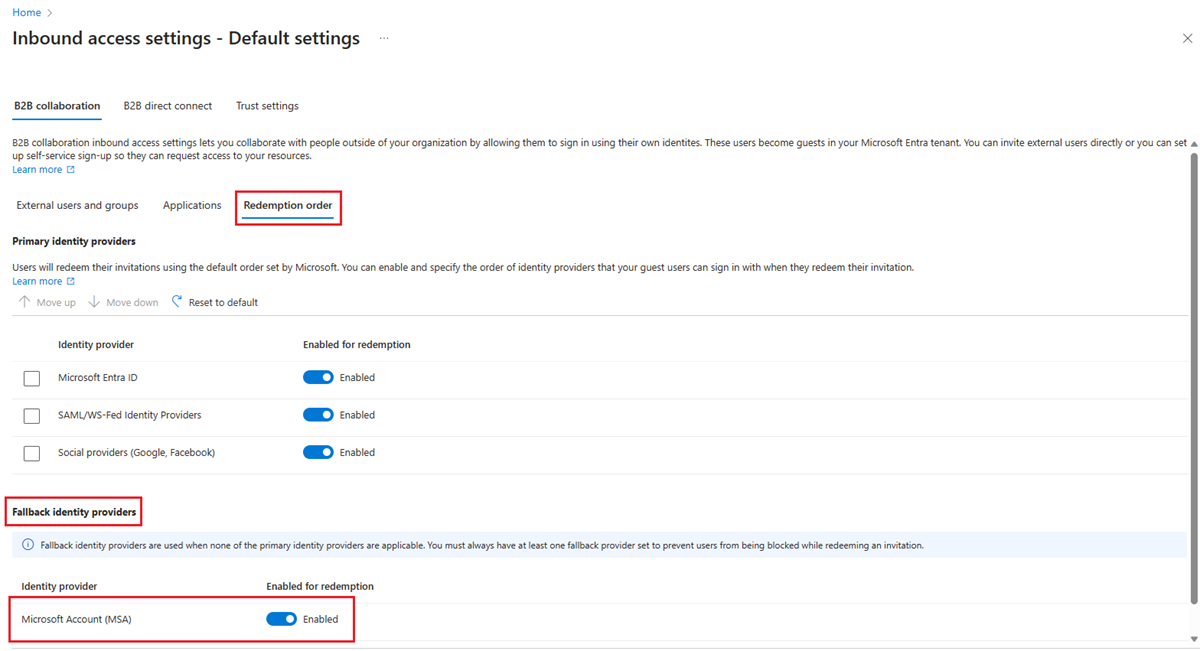
Select Save.
You need to have at least one fallback identity provider enabled at any given time. If you want to disable Microsoft accounts, you have to enable email one-time passcode. You can't disable both fallback identity providers. Any existing guest users signed in with Microsoft accounts continue using it during subsequent sign-ins. You need to reset their redemption status for this setting to apply.
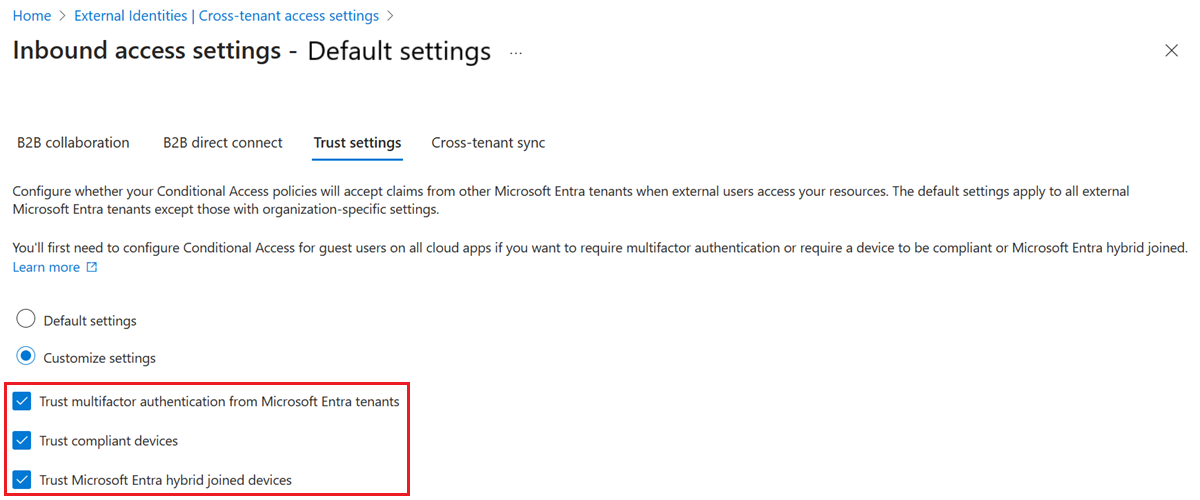
To change inbound trust settings for MFA and device claims
Select the Trust settings tab.
(This step applies to Organizational settings only.) If you're configuring settings for an organization, select one of the following:
Default settings: The organization uses the settings configured on the Default settings tab. If customized settings were already configured for this organization, select Yes to confirm that you want all settings to be replaced by the default settings. Then select Save, and skip the rest of the steps in this procedure.
Customize settings: You can customize the settings to enforce for this organization instead of the default settings. Continue with the rest of the steps in this procedure.
Select one or more of the following options:
Trust multifactor authentication from Microsoft Entra tenants: Select this checkbox to allow your Conditional Access policies to trust MFA claims from external organizations. During authentication, Microsoft Entra ID checks a user's credentials for a claim that the user completed MFA. If not, an MFA challenge is initiated in the user's home tenant. This setting isn't applied if an external user signs in using granular delegated admin privileges (GDAP), such as used by a technician at a Cloud Service Provider that administers services in your tenant. When an external user signs in using GDAP, MFA is always required in the user's home tenant, and always trusted in the resource tenant. MFA registration of a GDAP user isn't supported outside of the user's home tenant. If your organization has a requirement to disallow access to service provider technicians based on MFA in the user's home tenant, you can remove the GDAP relationship in Microsoft 365 admin center.
Trust compliant devices: Allows your Conditional Access policies to trust compliant device claims from an external organization when their users access your resources.
Trust Microsoft Entra hybrid joined devices: Allows your Conditional Access policies to trust Microsoft Entra hybrid joined device claims from an external organization when their users access your resources.
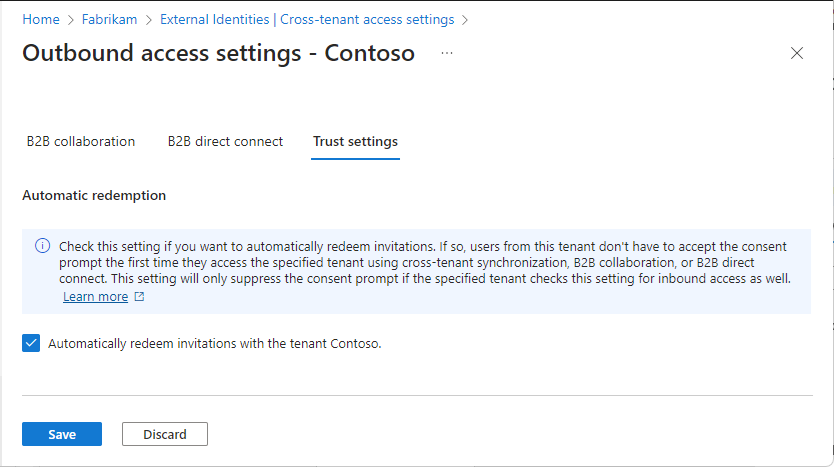
(This step applies to Organizational settings only.) Review the Automatic redemption option:
- Automatically redeem invitations with the tenant <tenant>: Check this setting if you want to automatically redeem invitations. If so, users from the specified tenant won't have to accept the consent prompt the first time they access this tenant using cross-tenant synchronization, B2B collaboration, or B2B direct connect. This setting only suppresses the consent prompt if the specified tenant also checks this setting for outbound access.
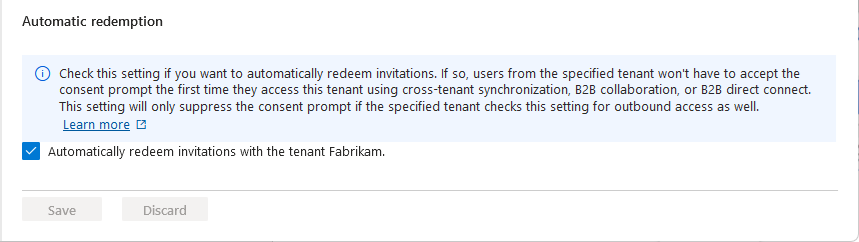
Select Save.
Allow users to sync into this tenant
If you select Inbound access of the added organization, you see the Cross-tenant sync tab and the Allow users sync into this tenant check box. Cross-tenant synchronization is a one-way synchronization service in Microsoft Entra ID that automates creating, updating, and deleting B2B collaboration users across tenants in an organization. For more information, see Configure cross-tenant synchronization and the Multitenant organizations documentation.

Modify outbound access settings
With outbound settings, you select which of your users and groups are able to access the external applications you choose. Whether you're configuring default settings or organization-specific settings, the steps for changing outbound cross-tenant access settings are the same. As described in this section, you navigate to either the Default tab or an organization on the Organizational settings tab, and then make your changes.
Sign in to the Microsoft Entra admin center as at least a Security Administrator.
Browse to Identity > External Identities > Cross-tenant access settings.
Navigate to the settings you want to modify:
To modify default outbound settings, select the Default settings tab, and then under Outbound access settings, select Edit outbound defaults.
To modify settings for a specific organization, select the Organizational settings tab, find the organization in the list (or add one) and then select the link in the Outbound access column.
Select the B2B collaboration tab.
(This step applies to Organizational settings only.) If you're configuring settings for an organization, select an option:
Default settings: The organization uses the settings configured on the Default settings tab. If customized settings were already configured for this organization, you need to select Yes to confirm that you want all settings to be replaced by the default settings. Then select Save, and skip the rest of the steps in this procedure.
Customize settings: You can customize the settings to enforce for this organization instead of the default settings. Continue with the rest of the steps in this procedure.
Select Users and groups.
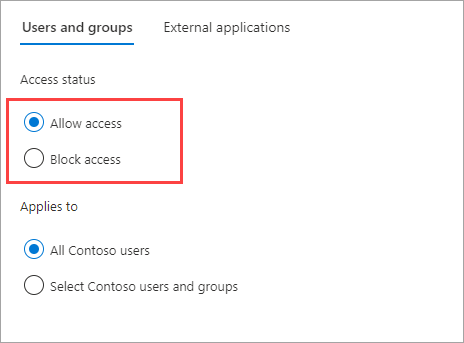
Under Access status, select one of the following:
- Allow access: Allows your users and groups specified under Applies to to be invited to external organizations for B2B collaboration.
- Block access: Blocks your users and groups specified under Applies to from being invited to B2B collaboration. If you block access for all users and groups, this also blocks all external applications from being accessed via B2B collaboration.
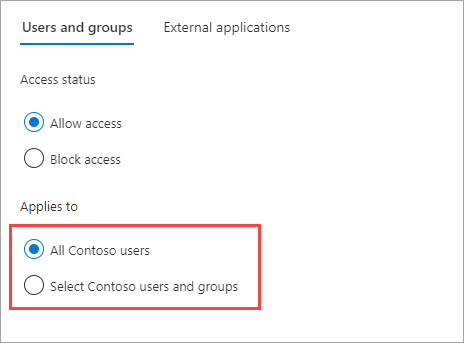
Under Applies to, select one of the following:
- All <your organization> users: Applies the action you chose under Access status to all your users and groups.
- Select <your organization> users and groups (requires a Microsoft Entra ID P1 or P2 subscription): Lets you apply the action you chose under Access status to specific users and groups.
Note
If you block access for all of your users and groups, you also need to block access to all external applications (on the External applications tab).
If you chose Select <your organization> users and groups, do the following for each user or group you want to add:
- Select Add <your organization> users and groups.
- In the Select pane, type the user name or group name in the search box.
- Select the user or group in the search results.
- When you're done selecting the users and groups you want to add, choose Select.
Note
When targeting your users and groups, you won't be able to select users who have configured SMS-based authentication. This is because users who have a "federated credential" on their user object are blocked to prevent external users from being added to outbound access settings. As a workaround, you can use the Microsoft Graph API to add the user's object ID directly or target a group the user belongs to.
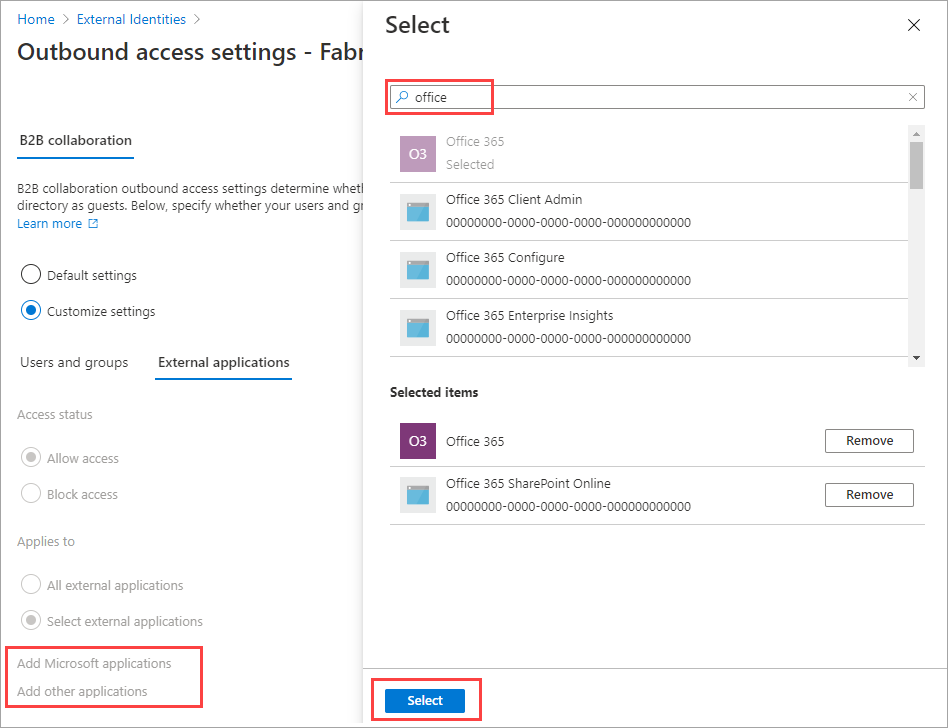
Select the External applications tab.
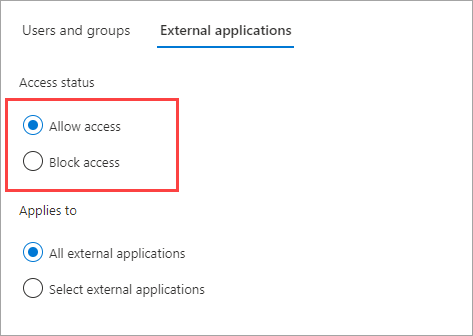
Under Access status, select one of the following:
- Allow access: Allows the external applications specified under Applies to to be accessed by your users via B2B collaboration.
- Block access: Blocks the external applications specified under Applies to from being accessed by your users via B2B collaboration.
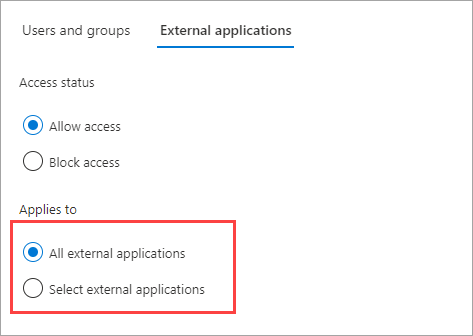
Under Applies to, select one of the following:
- All external applications: Applies the action you chose under Access status to all external applications.
- Select external applications: Applies the action you chose under Access status to all external applications.
Note
If you block access to all external applications, you also need to block access for all of your users and groups (on the Users and groups tab).
If you chose Select external applications, do the following for each application you want to add:
- Select Add Microsoft applications or Add other applications.
- In the search box, type the application name or the application ID (either the client app ID or the resource app ID). Then select the application in the search results. Repeat for each application you want to add.
- When you're done selecting applications, choose Select.
Select Save.
To change outbound trust settings
(This section applies to Organizational settings only.)
 Workforce tenants
Workforce tenants  External tenants (learn more)
External tenants (learn more)