IDA for Dummies – Part III
Access Management
Access Management aka Authorization Management enforces the policies for Access Control specified at Enterprise Level. Does this mean that you would not require authorization within the Applications????
Well, there has been lot of debates and views on this topic. Lots of people feel that the native authorization (embedded within application) can be eliminated when Access Management Solution is deployed.
Its easy said than done.
Firstly, let me clarify what I mean.
When any organization deploys Access Management Solution, they can -
- Perform the enterprise wide access control to the application from central system
- eliminate the broader authorization decisions from the application logic and let it be governed centrally
- provide enhanced user experience by facilitating SSO (Single Sign On) to the users- off course for web-based applications
How would access management work???
Deploying access management would typically mean that you would -
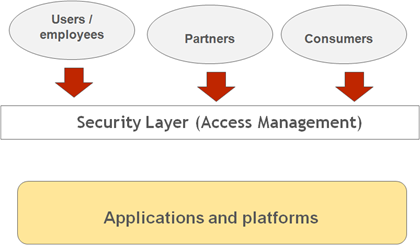
- Use Access Management as a security layer to perform access control / authorization at Enterprise Level. Which implies that -
- the user would first hit the Access Management layer when they browse for applications….
- Access Management would intercept the request and validate the user credentials
- If the user credentials are valid, then based on the role of user, the entitled applications are displayed in the portal
- User clicks on the application in portal and gets SSO to the application.
- The control is passed to the application and then the application would perform the granular access control.
- If the user is not entitled to access the application, the application is not displayed in the Access Management portal interface.
Challenges
With existing applications that has been deployed in any organization for years, it is difficult to strip off the authorization layer and pass it to something which is external. The Application logic needs to recoded and compiled to support this, which is not very well received by the Application teams/owners.
Also, no Access Management solution can provide you granular authorization control from central system which the built-in application authorization module would provide.
So, How do we use Access Management at Enterprise level?
The Access Management solution and applications needs to coexist currently…as you cannot strip off authorization module from apps. But the future apps can rely completely on Access Management Framework. But to what granular level, its a question of organizations decision :)
What are benefits of Access Management?
As I mentioned earlier -
- Centralized control of access rather than native
- Faster time to deploy as new applications may have limited authorization module and rely on Access Management framework.
- SSO to users…hence less credentials to remember
- Centralized audit trails of activities performed by users
- Hide the applications from users which they are not entitled to access…