Using Microsoft Identity Manager 2016 SP1 Portal / Self Service Password Reset with Web Application Proxy
Hello folks, David Steadman Here !!
Today we want to talk about a scenario that came by the product group that we wanted to address and highlight configuration to allow users and administrators connect to the Microsoft Identity Manager Portal and SSPR Registration and reset portals from a secure VPN using a a domain joined machine or BYOD scenario. The Basis of the scenario is a company would hire a contractor to perform work and they are using a non domain connected machine and the company policy is to enforce Kerberos authentication at all endpoints.
Scenarios trying to solve:
- Access to MIM Portal from domain/non-domain joined machine and requiring Kerberos
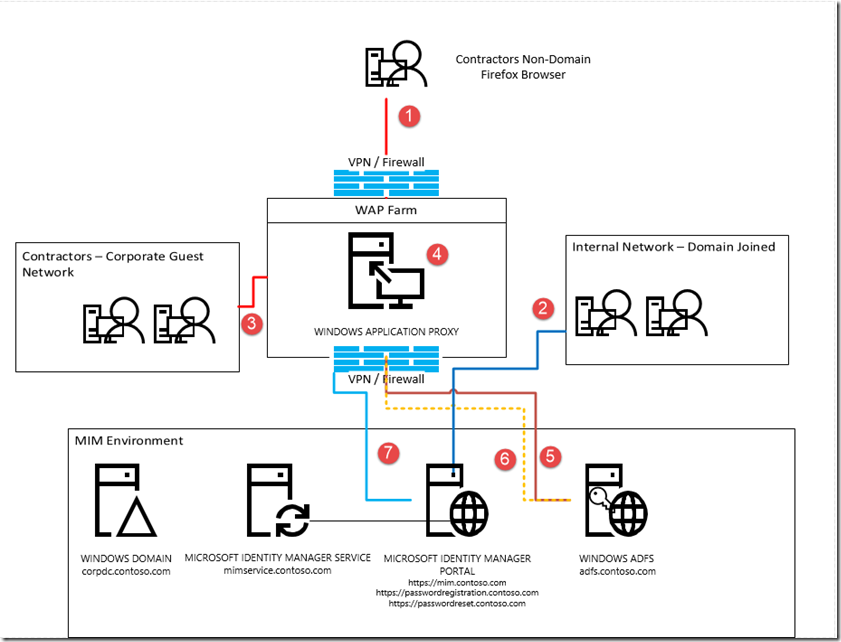
- Supported Example: VPN user coming in from VPN Service (as indicated in below image (item 1))
- Supported Example: Access from internal network from non-domain joined machines(as indicated in below image (item 3))
- Supported Example: Access from internal network from domain joined machines (as indicated in below image (item 2))
- Access to Self Service Password Reset Registration (SSPR) from domain/non-domain joined and requiring Kerberos
- Supported Example: This included VPN user coming in from VPN Service (as indicated in below image (item 1))
- Supported Example: Access from internal network from non-domain joined machines(item 2)
- Supported Example: Access from internal network from domain joined machines (as indicated in below image(item 2)) -- See Firefox doc
- Access to Password reset (SSPR) from domain/non-domain joined machine
- Supported Example: This included VPN user coming in from VPN Service (as indicated in below image (item 1))
- Supported Example: Publishing external for anonymous access (as indicated in below image (item 1))
- Supported Example: Access from internal network from non-domain / Domain joined machines(as indicated in below image(item 2 & 3))
In order to understand the high-level scenario the business wants to enforce Kerberos across the enterprise. With this comes some challenges around contractors that remote in or guest network within corporate network.
Right now the portal default for IIS is to have negotiate and then fail to NTLM. But when we use the resource management switch in the web config to requireKerberos="true" switch for the resource management client (https://technet.microsoft.com/en-us/library/jj134299(v=ws.10).aspx). The first part of this document we will identify what is needed to include enforcing Kerberos within SharePoint and Microsoft Identity Manager Portal while using alternant browsers like Firefox for example
This guidance will not cover every screen by screen only the important area of focus
Step 1: lets install our MIM Service Portal and SSPR (If already installed skip this step) : /en-us/microsoft-identity-manager/deploy-use/microsoft-identity-manager-deploy
Step 2: We need to make sure we are talking Kerberos for basic out of the box scenario , keeping it simple using IE some guides to help us that we always use:
- https://technet.microsoft.com/en-us/library/jj134299(v=ws.10).aspx
- http://setspn.blogspot.com/2011/06/fim-2010-understanding-kerberos.html
Step 3: Lets Install ADFS and WAP on the domain as we will require Kerberos constrained delegation(KDC)
At this point we have all the key players in place , We have the Web Application Proxy joined installed, we have ADFS installed and working.
Now let's look at the first scenario We have users that are on the domain and can successfully authenticate to the domain as indicated(item 2 above) for this scenario your corporate users should just be able to go to directly to the Web server and or a load balancer servicing multiple Web servers. In this case the user can go directly and then be prompted for their Kerberos ticket but we have to make sure that the browser is capable of communicating via this protocol.
Next thing we need to do is on our IIS site is to update the web.config to enforce Kerberos from the resource management client as we mentioned earlier to do the we go to the directory that MIM Portal resides in most environments it is located : C:\inetpub\wwwroot\wss\VirtualDirectories\80
Open the web config , scroll to the bottom and you will see the following :
We will then add : requireKerberos="true"
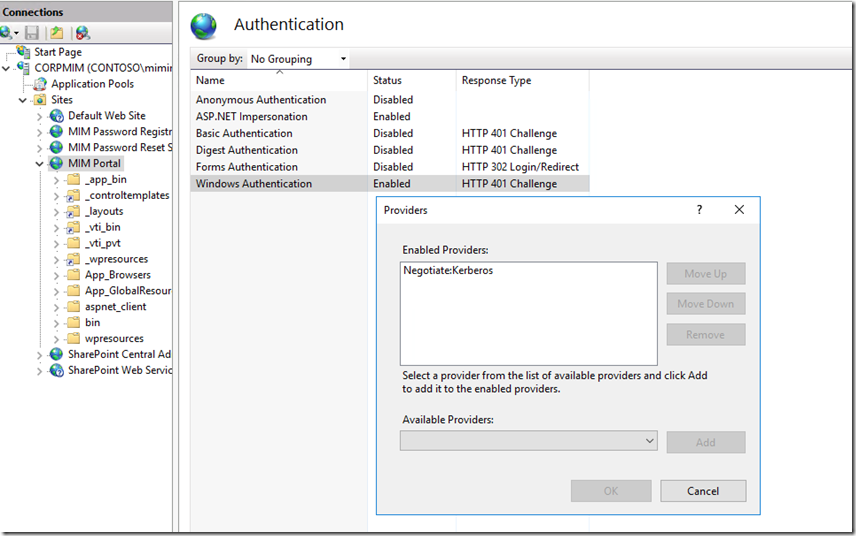
The second thing we need to do is update the IIS settings to not fall back to NTLM. As we cannot mix NTLM and Kerberos authentication. To do this we need to open IIS, then go to the MIM Portal site and then select authentication --> Windows Authentication --> Providers and remove negotiate and NTLM and add Negotiate:Kerberos. Like you see below
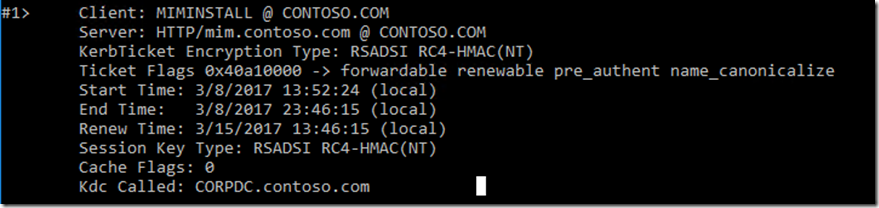
At this point we would do a IIS reset and test when using client we should get a Kerberos ticket when connecting to site , to see this we can run klist on the client computer we just opened the site on. https://technet.microsoft.com/en-us/library/hh134826(v=ws.11).aspx
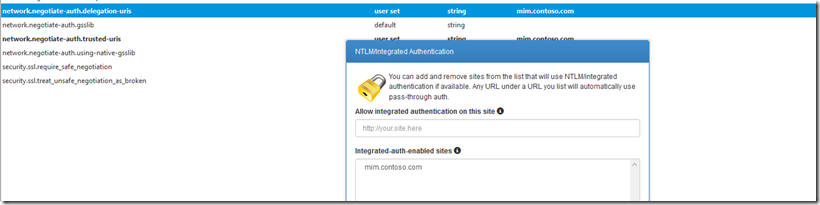
Now for Firefox as an example users that need to connect that are on the domain we have some work to do from the browser configuration as on the domain by default it simply does not do negotiate for this we have two options
Method 1 - Do it yourself!
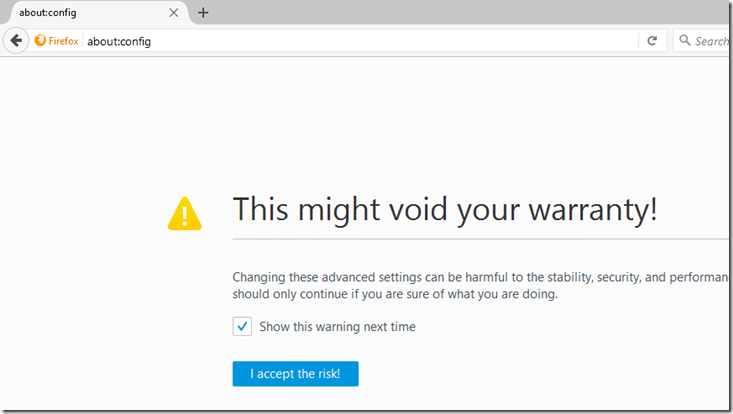
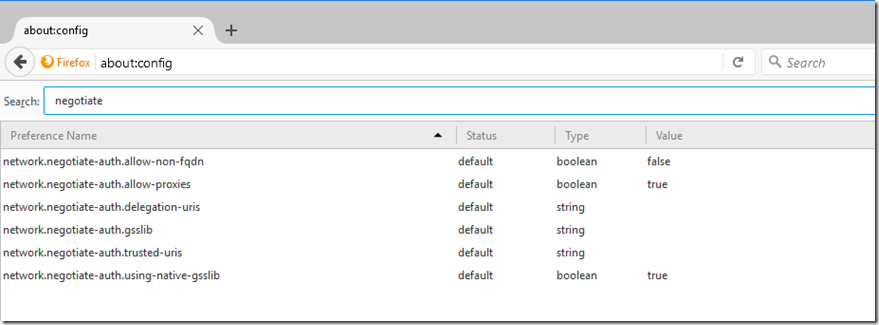
- Open Firefox and type about:config in the address bar.
- You will be prompted with a warning - click the "I Accept the risk!" button.
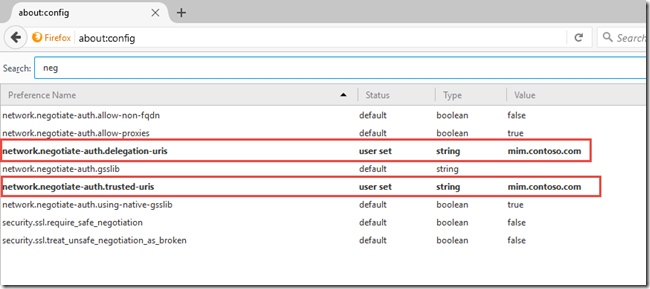
- Use the ‘Filter’ field to find the network.negotiate-auth.delegation-uris & network.negotiate-auth.trusted-uris configuration parameter
- Double-click the name of the configuration parameter
- Enter the URLs of the sites you wish to enable authentication for in the form:
- mim.contoso.com
Method 2 - Use an extension!(Warning this is a third party plugin)
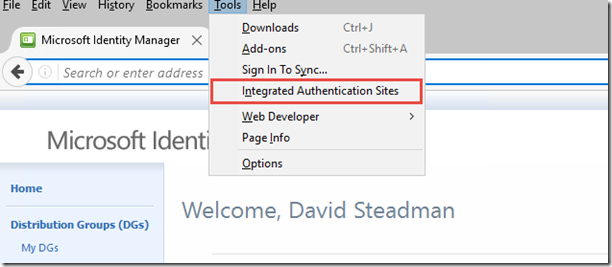
If you don't want to open up the about:config page whenever you come across a site that you'd like to add authentication, then as you would expect, someone has written a Firefox Extension called Integrated Authentication for Firefox that provides a simple interface to add and remove entries. Install the Extension, restart Firefox, and then in your Tools menu also hidden
You will find a new option called Integrated Authentication Sites
Next that will open up a simple dialog box that lets you add or remove entries. As per the manual method, note that you should only include the hostname (mim.contoso.com) there is no trailing slash nor a path to any particular page. Authentication is enabled on a per-site basis.
Now internal users on the domain are great they authenticate using whatever browsers they want. Now the challenge of users not on the domain or that VPN into the network we need to have those users on a segregated network (most enterprises have a guest network) to control what contractors have access to this also includes VPN access were VPN policies can be applied to a set of users (Contractors) to have different rules.
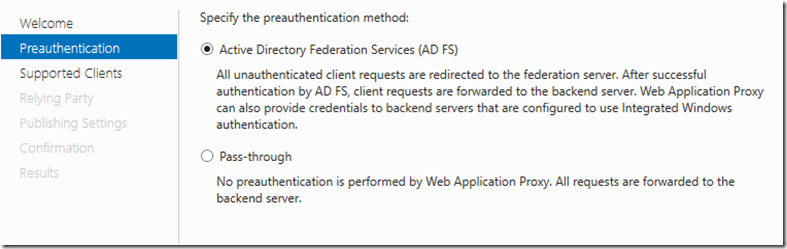
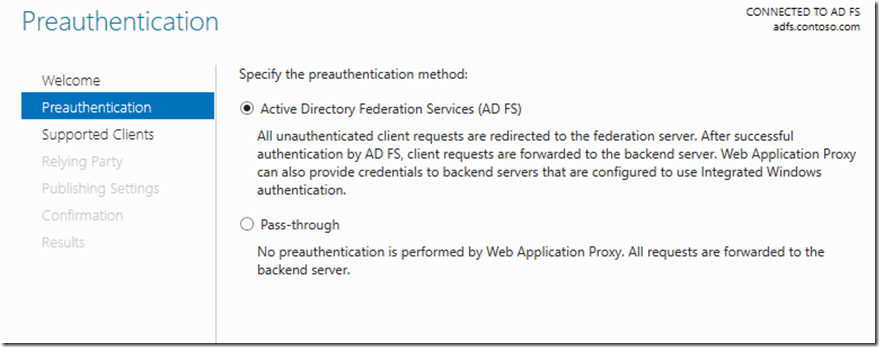
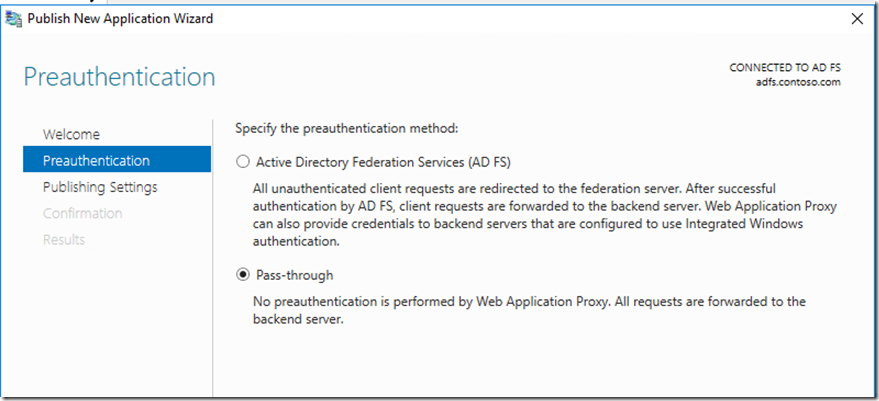
The way this will work a user will request for access going through WAP , We will configure WAP for KDC and also configure the portal and registration as pre-auth(AD FS Forms Based).
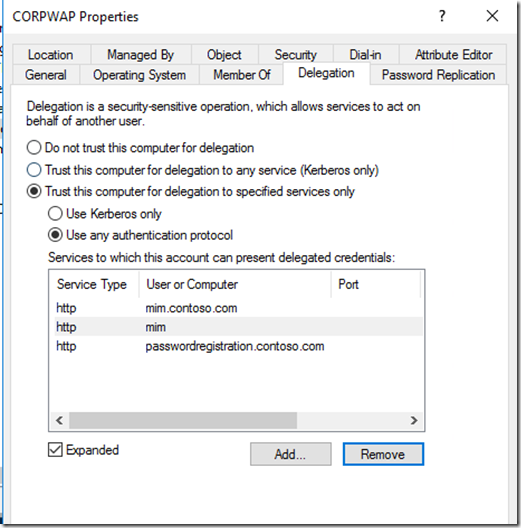
This is a simple approach as the user comes in (1)(3) they connect to WAP(4) then get redirected to ADFS(5). Once authenticated the user is redirected and a token(6) is handed back to WAP and then WAP request a Kerberos ticket on contractors behalf and WAP allow access to application(7). For this we need to enable KCD on the WAP computer account and specify the app pool account that holds the SPN that we need to delegate for in active directory like below. The reset and ADFS will be published as pass-through.
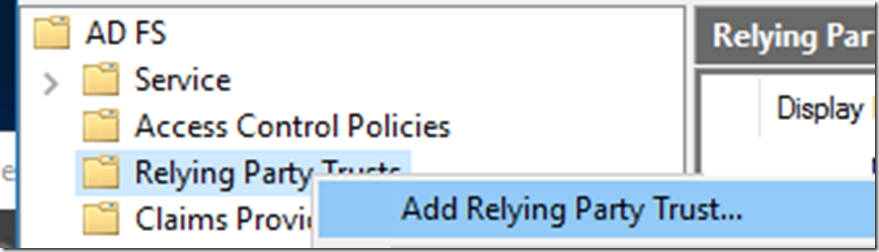
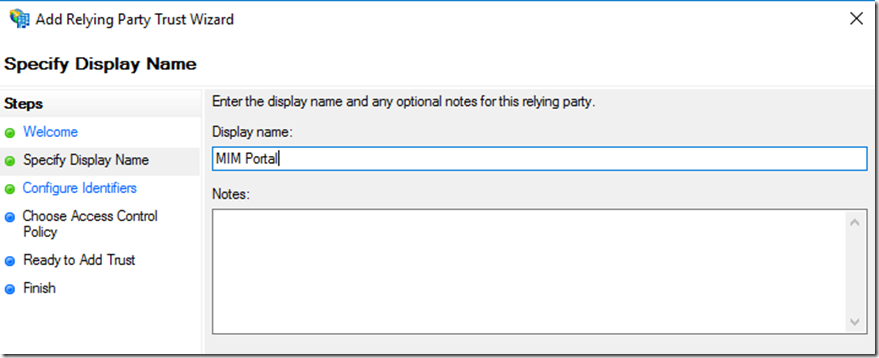
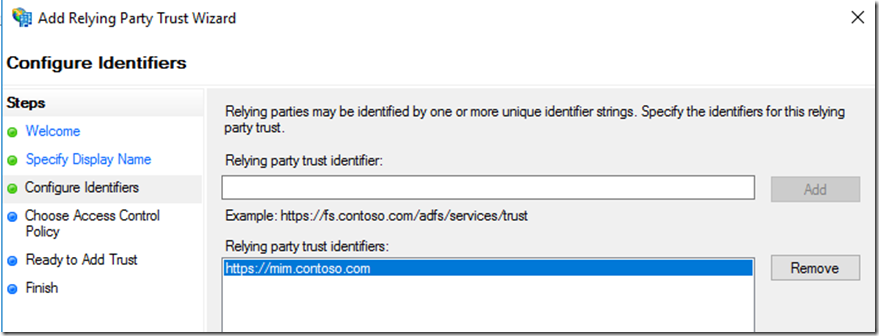
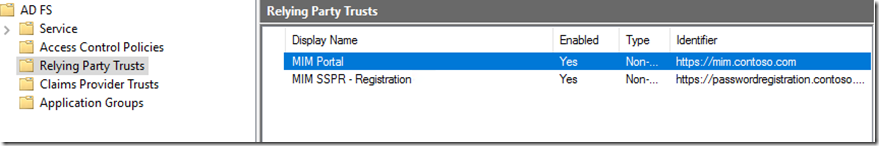
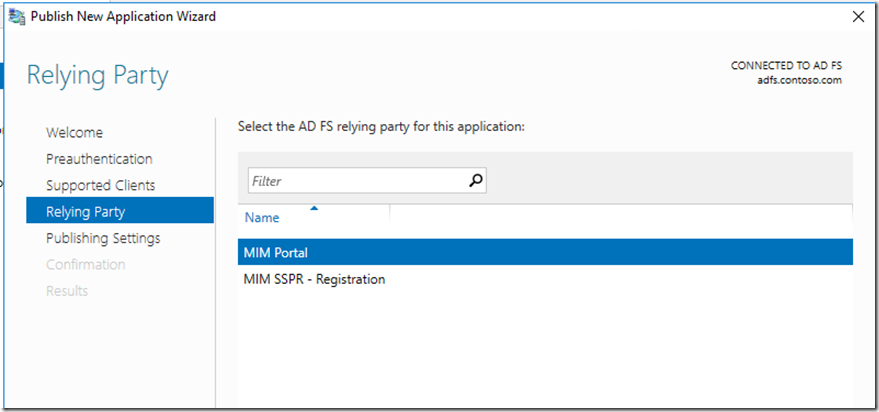
Once we have done this we need to configure ADFS Relying party for MIM Portal and SSPR Registration. For this we will add non-claims aware using the wizard.
Select the Relying Party Trust --> Right click and then Add Relying party Trust
Select Non claims aware
Add Display Name and any notes
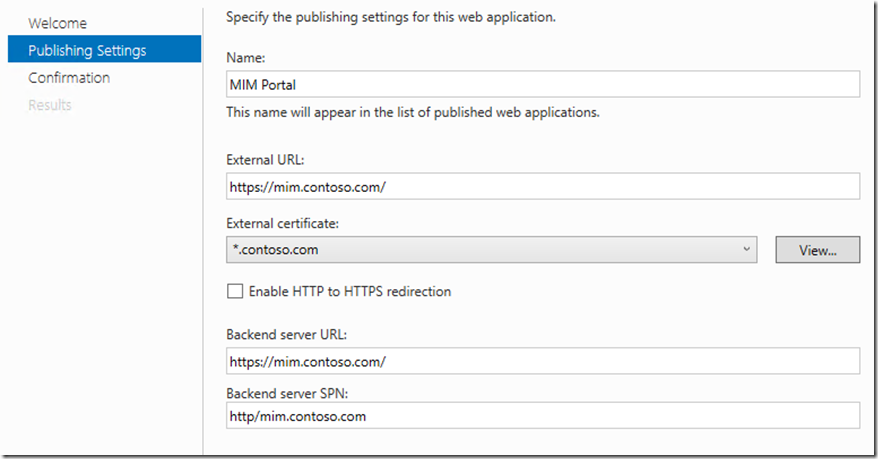
Add the full FQDN for the MIM Portal Site
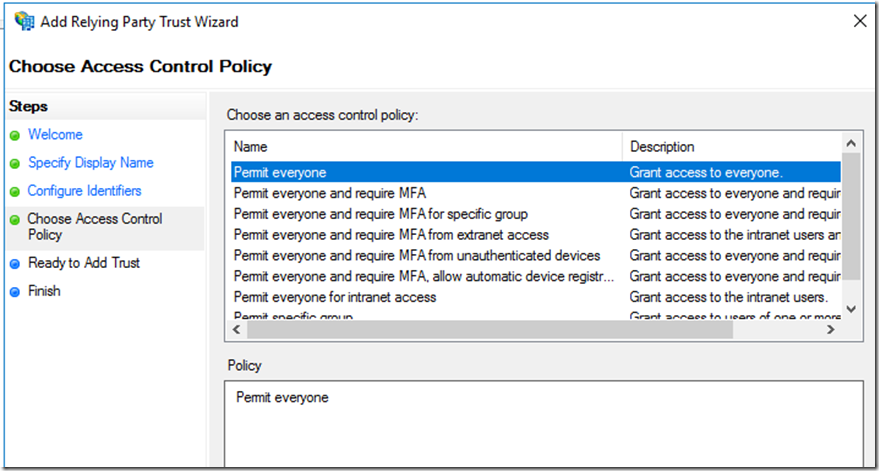
Here you have several option at this point you could have a custom access control policy just for contractors to permit but also have MFA before granting access id MFA is enable on your ADFS farm : /en-us/azure/multi-factor-authentication/multi-factor-authentication-get-started-adfs
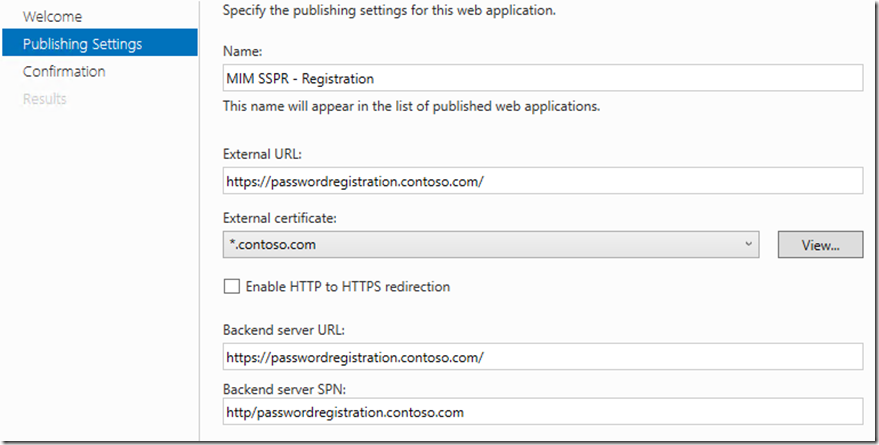
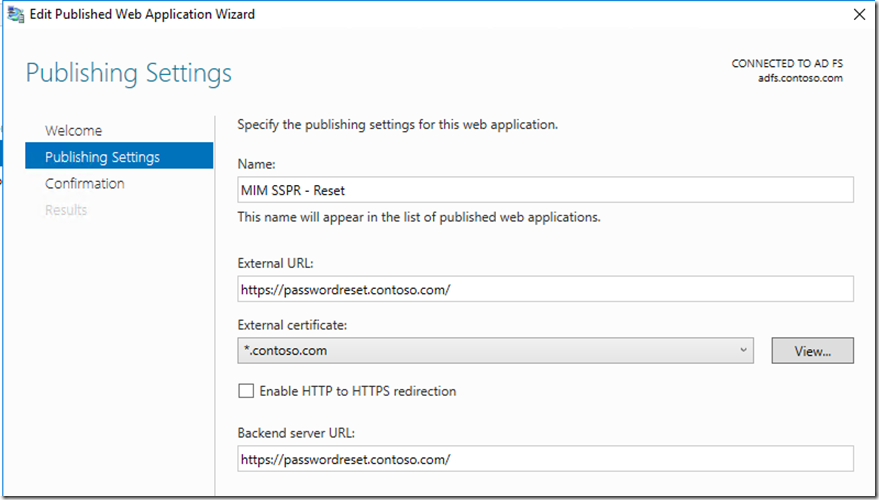
We will do the same for Self Service Registration (SSPR)
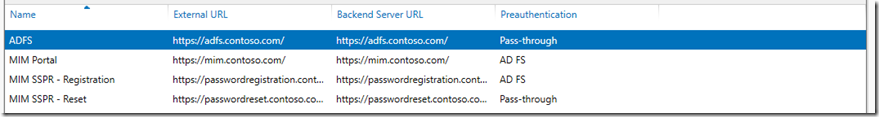
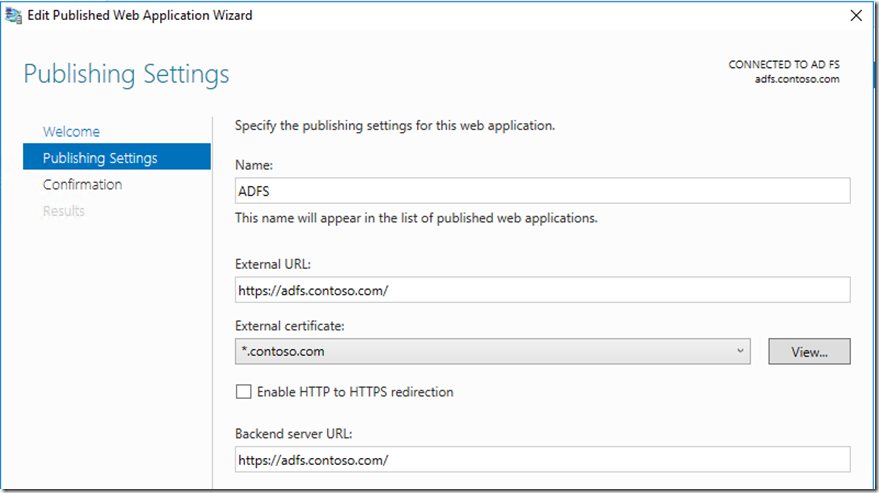
Next lets jump back over to the WAP server and publish the MIM Portal and Registration site to also include ADFS/SSPR(Reset)
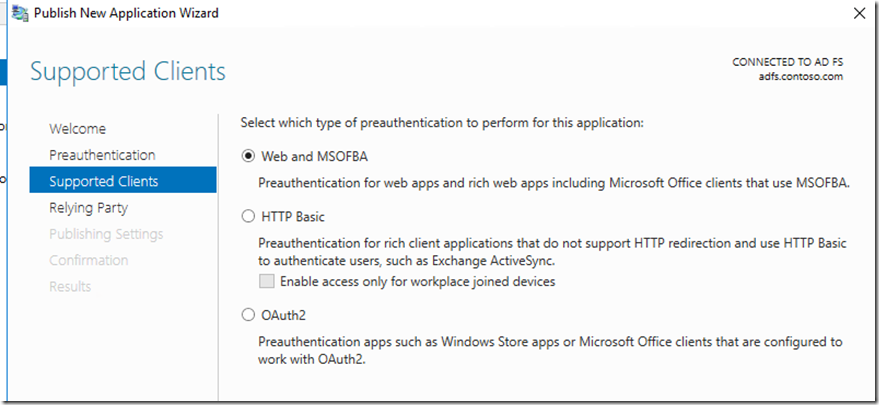
For the MIM Portal and Registration we want to select Pre-auth (AD FS) and Supported Clients will be Web and MSOFBA(From Windows 2016)
The next screen Relying Party will be pulled from the ADFS server and we will select the appropriate one if we are publishing MIM Portal we will select the MIM Portal
Publish setting for MIM Portal and Registration , take special note of the SPN as you need to make sure this matches up with the SPN you selected in the WAP KCD setup earlier we did
For the ADFS and SSPR reset site, we will use pass through as they do not need pre-auth so when publishing we will select pass-through
Then this is the setting we have on the Publishing settings
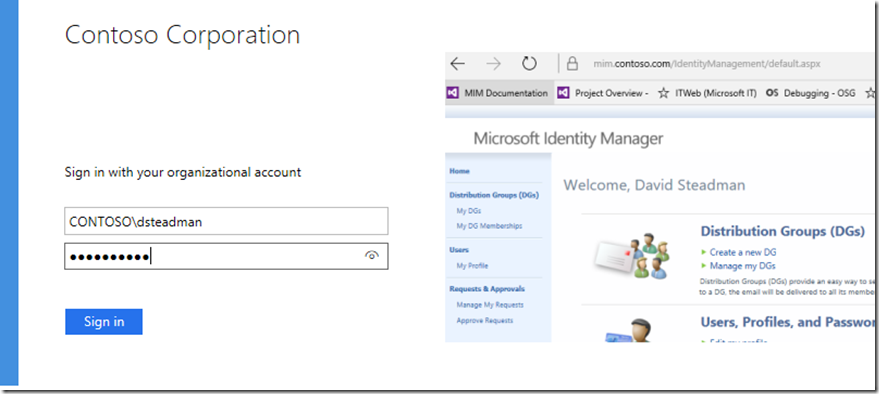
Now when a contractor logs in using VPN and/or Guest network on corporate going to https://mim.contoso.com/IdentityManagement/ or registration they would be prompted to enter credentials using ADFS forms based auth
At this point we have covered publishing securely MIM and it Web interfaces for contractor and internal resources while enforcing Kerberos.
References Articles related links
- SharePoint and WAP: https://blogs.msdn.microsoft.com/sambetts/2014/12/10/publishing-sharepoint-with-windows-server-2012-r2-web-application-proxy/
- Understanding Kerberos: http://setspn.blogspot.com/2011/06/fim-2010-understanding-kerberos.html
- Multifactor Authentication (MFA): /en-us/azure/multi-factor-authentication/multi-factor-authentication-get-started-adfs
- Understanding of Web Application Proxy : https://technet.microsoft.com/en-us/library/dn584113(v=ws.11).aspx
- Understanding of ADFS : https://technet.microsoft.com/en-us/library/cc771542(v=ws.11).aspx
- Understanding of Kerberos https://msdn.microsoft.com/en-us/library/bb742516.aspx &
- Constrained delegation https://technet.microsoft.com/en-us/library/jj553400(v=ws.11).aspx
Comments
- Anonymous
September 28, 2017
Regarding "non domain-joined" scenarios: Do I understand this right, that only IE and Edge are able to connect to the MIM Portal (Kerberos enforced) when they are on the internal network and no WAP is in between? At least this is what I read from you post and also what we experience in practice. FireFox, Chrome, ecc. does not seem to be able to request Kerberos tickets from a not domain-joined machine, whereas IE and Edge are able indeed!So does that mean that to use Firefox/Chrome we are forced to deploy a WAP solution even in the internal network? If this is correct, than you should have pointed this out in a much clearer form! BTW: the Firefox plugin you are mentioning is not working anymore...- Anonymous
October 25, 2017
Hello...I will need to check into this one for us. Tim
- Anonymous