Get a complete list of apps using ADAL in your tenant
This article provides guidance on how to use Azure Monitor workbooks to obtain a list of all apps that use ADAL in your tenant.
Azure Active Directory Authentication Library (ADAL) has been deprecated. We strongly recommend migrating to the Microsoft Authentication Library (MSAL), which replaces ADAL. Microsoft no longer releases new features and security fixes on ADAL. Applications using ADAL will not be able to utilize the latest security features, leaving them vulnerable to future security threats. If you have existing applications that use ADAL, be sure to migrate them to MSAL.
Sign-ins workbook
Workbooks are a set of queries that collect and visualize information that is available in Microsoft Entra logs. Learn more about the sign-in logs schema here.
The Sign-ins Workbook in the Azure portal consolidates logs from various types of sign-in events, including interactive, non-interactive, and service principal sign-ins. This aggregation offers detailed insights into the usage of ADAL applications across your tenant to help you fully understand and manage migration of your ADAL applications.
Below, we provide comprehensive instructions on accessing the workbook and subsequently demonstrate effective ways for visualizing the list of applications.
Step 1: Send Microsoft Entra sign-in events to Azure Monitor
Microsoft Entra ID doesn't send sign-in events to Azure Monitor by default, which the Sign-ins Workbook in Azure Monitor requires.
Configure AD to send sign-in events to Azure Monitor by following the steps in Integrate your Microsoft Entra sign-in and audit logs with Azure Monitor. In the Diagnostic settings configuration step, select the SignInLogs check box.
No sign-in event that occurred before you configure Microsoft Entra ID to send the events to Azure Monitor will appear in the Sign-ins workbook.
Step 2: Access Sign-ins workbook in Azure portal
Tip
Steps in this article might vary slightly based on the portal you start from.
Once you've integrated your Microsoft Entra sign-in and audit logs with Azure Monitor as specified in the Azure Monitor integration, access the sign-ins workbook:
- Sign in to the Microsoft Entra admin center as at least a Reports Reader.
- Browse to Identity > Monitoring & health > Workbooks.
- In the Usage section, open the Sign-ins workbook.
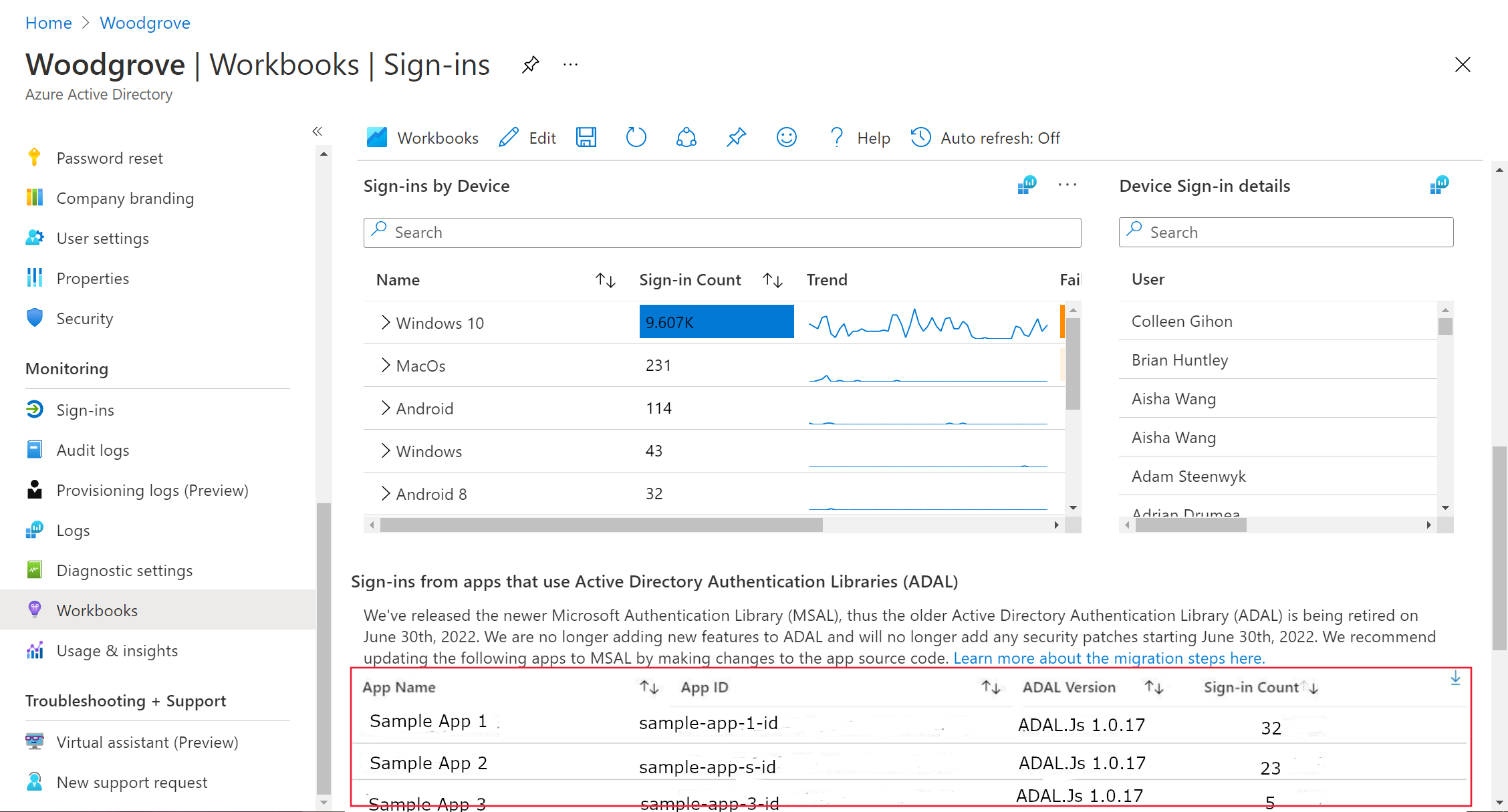
Step 3: Identify apps that use ADAL
The table at the bottom of the Sign-ins workbook page lists apps that recently used ADAL. You can also export a list of the apps. Update these apps to use MSAL.
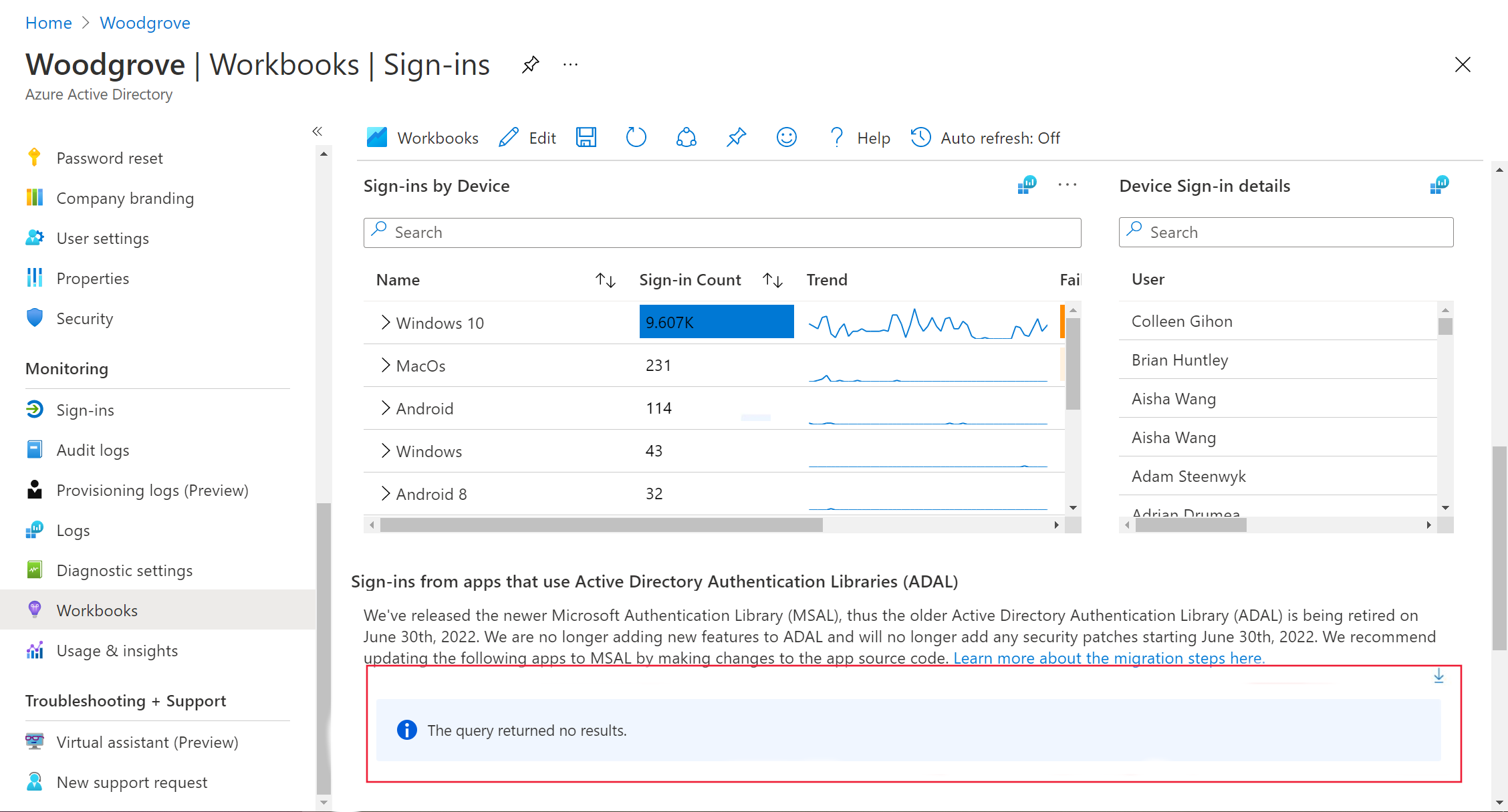
If there are no apps using ADAL, the workbook will display a view as shown below.
Step 4: Dive deep to analyze application usage and authentication data
To thoroughly assess the impact of ADAL applications within your tenant, it's crucial to analyze more detailed data beyond mere identification.
- Application Id: Unique identifier for each application.
- App Display Name: The name of the application, which helps in easily identifying the app across the organization.
- SigninCount: Number of sign-ins per application.
- ADAL Version: Specific version of ADAL used by the application.
- IP Address: Displays the client's IP address from which the sign-in attempt originated.
- Location: Provides the city, state, country/region and from where the sign-in request was made.
- Sign-in by Device: Shares the details of the OS of the device including the specific version.
To access this enhanced data view, apply custom filters and queries within the workbook. This information not only aids in identifying critical applications but also helps in planning the migration strategy by prioritizing applications based on their usage and exposure level.
Step 5: Update your ADAL application
Once you've identified the applications using ADAL, proceed with updating them to MSAL. The migration process varies based on the type of application you are working with. Follow the guidelines provided below for each application type.
Single-page app (SPA)
Mobile app
Service / daemon app
Step 6: Monitor to validate successful migration
With the detailed data from Step 4, you can effectively prioritize and manage the migration process of your applications to MSAL. Here’s how you can use this data to investigate sign-in scenarios and ensure a smooth transition:
- Prioritization: Applications with a high
SigninCountand olderADAL Versionshould be prioritized as they represent higher usage and potentially higher risk. Migrate these applications first to minimize the most significant risks to your organization. - Security Analysis: Use the
IP Addressto detect sign-in patterns. For example, if sign-ins request is made from a user or an organization owned service to identify the source of the call. - Compatibility Checks: Before migrating, assess the
ADAL Versionused by the application. Some versions might have known issues with specific MSAL features. Understanding these nuances will help in planning a migration that minimizes functionality disruptions. - Testing Scenarios: After updating to MSAL, monitor to compare pre-and post-migration behavior. This comparison helps verify that the migration was successful and that the application behaves as expected in the new environment.
By leveraging the detailed data from the Sign-ins workbook, your organization can strategically plan and execute the migration from ADAL to MSAL, ensuring minimal disruption and maintaining robust security protocols.
Next steps
For more information about MSAL, including usage information and which libraries are available for different programming languages and application types, see:
Phản hồi
Sắp ra mắt: Trong năm 2024, chúng tôi sẽ dần gỡ bỏ Sự cố với GitHub dưới dạng cơ chế phản hồi cho nội dung và thay thế bằng hệ thống phản hồi mới. Để biết thêm thông tin, hãy xem: https://aka.ms/ContentUserFeedback.
Gửi và xem ý kiến phản hồi dành cho