Sự kiện
15 giờ 9 thg 4 - 12 giờ 10 thg 4
Lập trình tương lai với AI và kết nối với các đồng nghiệp và chuyên gia Java tại JDConf 2025.
Đăng ký ngayTrình duyệt này không còn được hỗ trợ nữa.
Hãy nâng cấp lên Microsoft Edge để tận dụng các tính năng mới nhất, bản cập nhật bảo mật và hỗ trợ kỹ thuật.
The objective of this article is to show the steps required to perform in Salesforce and Microsoft Entra ID to automatically provision and de-provision user accounts from Microsoft Entra ID to Salesforce.
The scenario outlined in this article assumes that you already have the following items:
A Microsoft Entra tenant.
A Salesforce.com tenant.
A Salesforce account username and password and the token. In future, if you reset the account password, Salesforce provides you with a new token and you'll need to edit the Salesforce provisioning settings.
A custom user profile in Salesforce. Once you have created a custom profile in the Salesforce portal, edit the profile's Administrative Permissions to enable the following:
API Enabled.
Manage Users: Enabling this option automatically enables the following: Assign Permission Sets, Manage Internal UsersManage IP Addresses, Manage Login Access Policies, Manage Password Policies, Manage Profiles and Permission Sets, Manage Roles, Manage Sharing, Reset User Passwords and Unlock Users, View All Users, View Roles and Hierarchy, View Setup and Configuration.
See also Salesforce Create or Clone Profiles documentation.
Lưu ý
Assign the permissions directly to the profile. Don't add the permissions through permission sets.
Lưu ý
Roles should not be manually edited in Microsoft Entra ID when doing role imports.
Quan trọng
If you are using a Salesforce.com trial account, then you will be unable to configure automated user provisioning. Trial accounts do not have the necessary API access enabled until they are purchased. You can get around this limitation by using a free developer account to complete this article.
If you are using a Salesforce Sandbox environment, see the Salesforce Sandbox integration article.
Microsoft Entra ID uses a concept called "assignments" to determine which users should receive access to selected apps. In the context of automatic user account provisioning, only the users and groups that are "assigned" to an application in Microsoft Entra ID are synchronized.
Before configuring and enabling the provisioning service, you need to decide which users or groups in Microsoft Entra ID need access to your Salesforce app. You can assign these users to your Salesforce app by following the instructions in Assign a user or group to an enterprise app
It is recommended that a single Microsoft Entra user is assigned to Salesforce to test the provisioning configuration. More users and/or groups may be assigned later.
When assigning a user to Salesforce, you must select a valid user role. The "Default Access" role does not work for provisioning
Lưu ý
This app imports profiles from Salesforce as part of the provisioning process, which the customer may want to select when assigning users in Microsoft Entra ID. Please note that the profiles that get imported from Salesforce appear as Roles in Microsoft Entra ID.
This section guides you through connecting your Microsoft Entra ID to Salesforce's user account provisioning API - v40
Mẹo
You may also choose to enabled SAML-based Single Sign-On for Salesforce, following the instructions provided in the Azure portal. Single sign-on can be configured independently of automatic provisioning, though these two features complement each other.
The objective of this section is to outline how to enable user provisioning of Active Directory user accounts to Salesforce.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications.
If you have configured Salesforce for single sign-on, search for your instance of Salesforce using the search field. Otherwise, select Add and search for Salesforce in the application gallery. Select Salesforce from the search results, and add it to your list of applications.
Select your instance of Salesforce, then select the Provisioning tab.
Set the Provisioning Mode to Automatic.

Under the Admin Credentials section, provide the following configuration settings:
In the Admin Username textbox, type a Salesforce account name that has the System Administrator profile in Salesforce.com assigned.
In the Admin Password textbox, type the password for this account.
To get your Salesforce security token, open a new tab and sign into the same Salesforce admin account. On the top right corner of the page, click your name, and then click Settings.
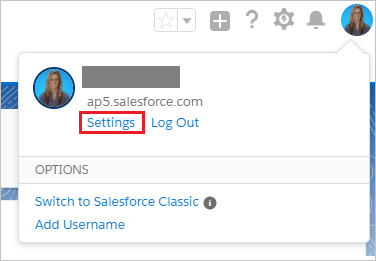
On the left navigation pane, click My Personal Information to expand the related section, and then click Reset My Security Token.
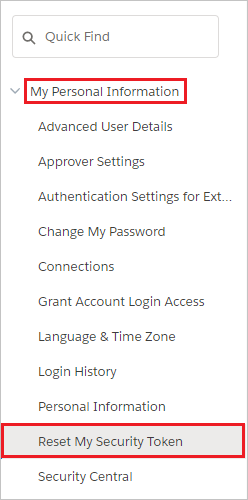
On the Reset Security Token page, click Reset Security Token button.
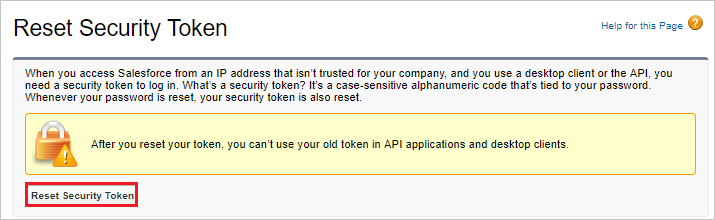
Check the email inbox associated with this admin account. Look for an email from Salesforce.com that contains the new security token.
Copy the token, go to your Microsoft Entra window, and paste it into the Secret Token field.
The Tenant URL should be entered if the instance of Salesforce is on the Salesforce Government Cloud. Otherwise, it is optional. Enter the tenant URL using the format of https://<your-instance>.my.salesforce.com, replacing <your-instance> with the name of your Salesforce instance.
Select Test Connection to ensure Microsoft Entra ID can connect to your Salesforce app.
In the Notification Email field, enter the email address of a person or group who should receive provisioning error notifications, and check the checkbox below.
Click Save.
Under the Mappings section, select Synchronize Microsoft Entra users to Salesforce.
In the Attribute Mappings section, review the user attributes that are synchronized from Microsoft Entra ID to Salesforce. Note that the attributes selected as Matching properties are used to match the user accounts in Salesforce for update operations. Select the Save button to commit any changes.
To enable the Microsoft Entra provisioning service for Salesforce, change the Provisioning Status to On in the Settings section
Click Save.
Lưu ý
Once the users are provisioned in the Salesforce application, administrator need to configure the language specific settings for them. Please see this article for more details on language configuration.
This starts the initial synchronization of any users and/or groups assigned to Salesforce in the Users and Groups section. The initial sync takes longer to perform than subsequent syncs, which occur approximately every 40 minutes as long as the service is running. You can use the Synchronization Details section to monitor progress and follow links to provisioning activity logs, which describe all actions performed by the provisioning service on your Salesforce app.
For more information on how to read the Microsoft Entra provisioning logs, see Reporting on automatic user account provisioning.
Sự kiện
15 giờ 9 thg 4 - 12 giờ 10 thg 4
Lập trình tương lai với AI và kết nối với các đồng nghiệp và chuyên gia Java tại JDConf 2025.
Đăng ký ngayĐào tạo
Mô-đun
Durch die Bereitstellung und Überwachung von Unternehmensanwendungen in Azure-Lösungen kann Sicherheit gewährleistet werden. Erfahren Sie, wie Sie lokale und cloudbasierte Apps für Benutzer bereitstellen.
Chứng chỉ
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Veranschaulichen der Features von Microsoft Entra ID, um Identitätslösungen zu modernisieren sowie Hybridlösungen und Identitätsgovernance zu implementieren
Tài liệu
Erfahren Sie, welche Schritte in Salesforce Sandbox und Microsoft Entra ID ausgeführt werden müssen, um Benutzerkonten von Microsoft Entra ID automatisch in Salesforce Sandbox bereitzustellen bzw. deren Bereitstellung automatisch aufzuheben.
Microsoft Entra Single Sign-On (SSO)-Integration mit Salesforce - Microsoft Entra ID
Erfahren Sie, wie Sie einmaliges Anmelden zwischen Microsoft Entra ID und Salesforce konfigurieren.
Tutorial: Microsoft Entra Integration mit Salesforce Sandbox - Microsoft Entra ID
Erfahren Sie, wie Sie einmaliges Anmelden (SSO) zwischen Microsoft Entra ID und askSpoke konfigurieren.
Eine Einführung in die Verwendung von Microsoft Entra ID für die automatisierte Bereitstellung, die Aufhebung der Bereitstellung und die fortlaufende Aktualisierung von Benutzerkonten über verschiedene Drittanbieteranwendungen hinweg.