Lưu ý
Cần có ủy quyền mới truy nhập được vào trang này. Bạn có thể thử đăng nhập hoặc thay đổi thư mục.
Cần có ủy quyền mới truy nhập được vào trang này. Bạn có thể thử thay đổi thư mục.
Agent makers in your organization can make HTTP requests with the Send HTTP request node.
You can use data loss prevention policies to prevent agent makers from configuring HTTP requests to help prevent data exfiltration.
For more information about other DLP-related connectors, see Configure data loss prevention policies for agents.
Configure DLP to block HTTP requests in the Power Platform admin center
Select or create a policy
In the Power Platform admin center, under Policies, select Data policies.
Create a new policy, or choose an existing policy to edit:
If you want to create a new policy, select New policy.
If you want to choose an existing policy to edit, select the policy and select Edit policy.
Enter a name for the policy then select Next. You can change the name later.
Choose an environment
Choose one or more environments to add to your policy.
Select Add to policy.
Select Next.
Add the connector
Use the search box to find the HTTP connector.
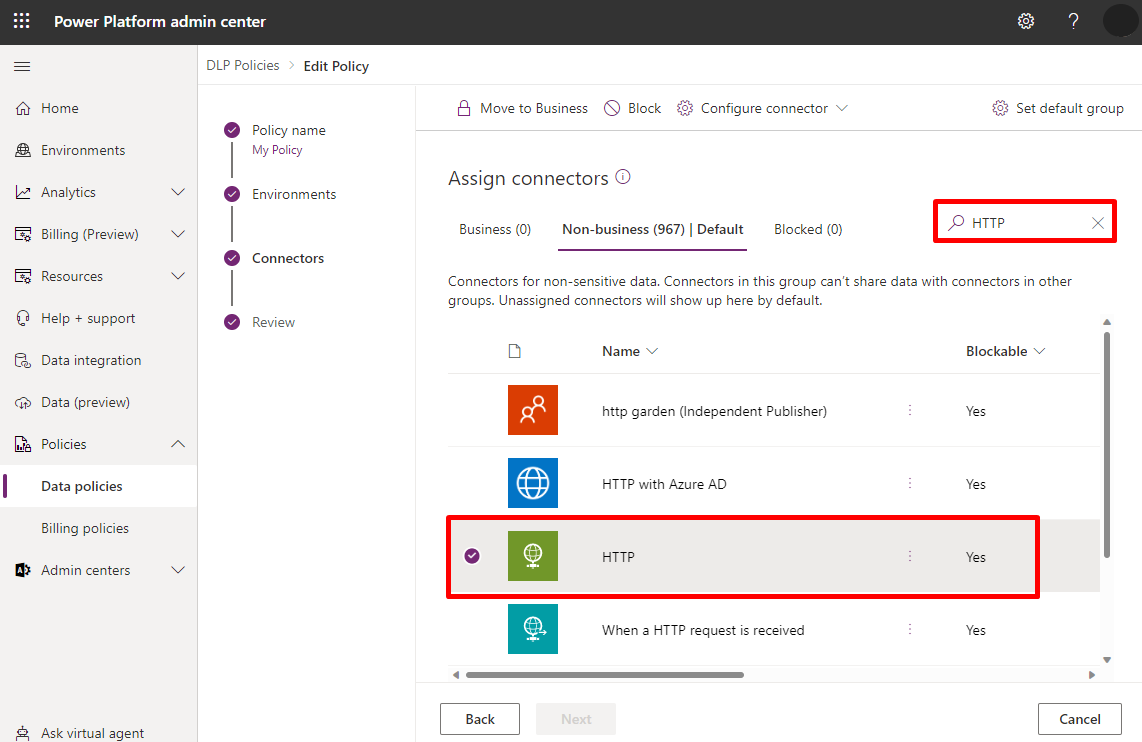
Select the connector's More actions icon (⋮), and then select Block.
If admins want to allow or deny specific HTTP endpoints, they can use DLP connector endpoint filtering instead of blocking all HTTP calls.
Select Next.
Review your policy, then select Update policy to apply the DLP changes.
Confirm policy enforcement
You can confirm that this connector is being used in the DLP policy from the Copilot Studio.
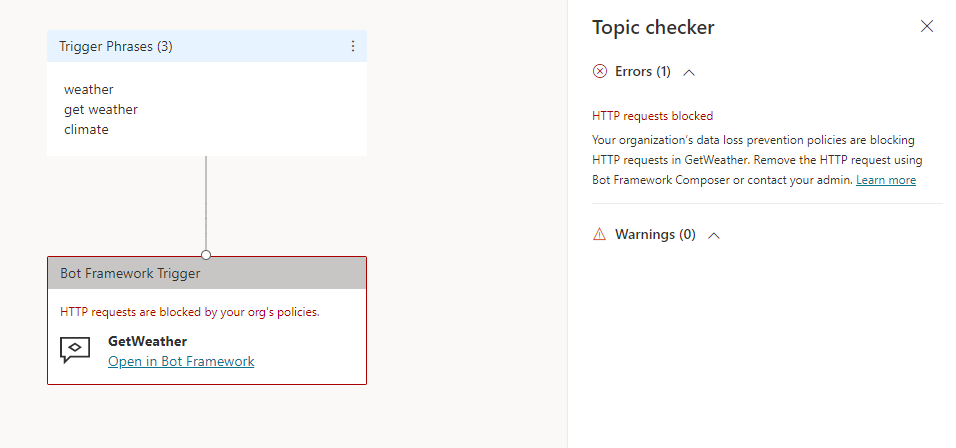
First, open your agent from the environment where the DLP policy is applied. Go to the authoring canvas, create a new topic, add a Send HTTP request node (minimally populating the URL property), and save your topic.
If the policy is enforced, you'll see an error banner with a Details button. On the Channels page, expand the error link and select the Download button to see details.
In the details file, a row appears describing each violation. A violation occurs if the HTTP connector is blocked, if the HTTP connector is in a different data group than other connectors in your DLP policy, or if the HTTP policy isn't blocked but an endpoint is denied.