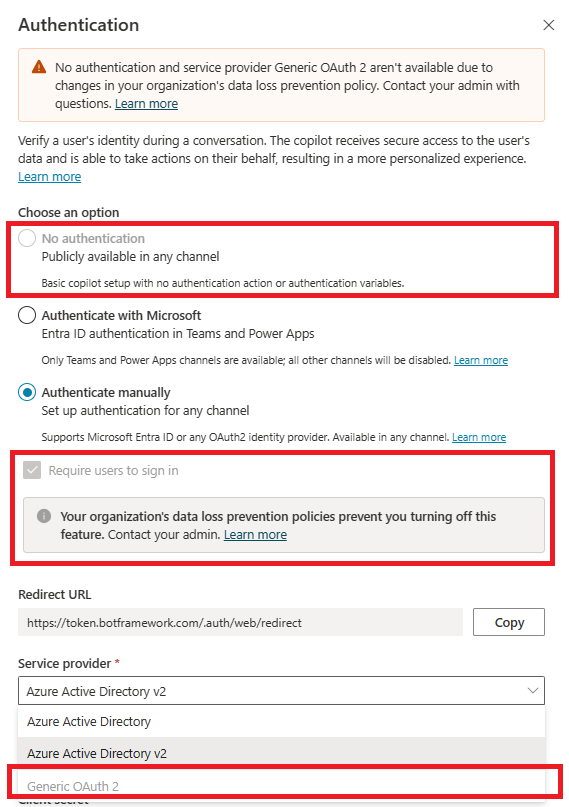
Data loss prevention example - Require end-user authentication in copilots
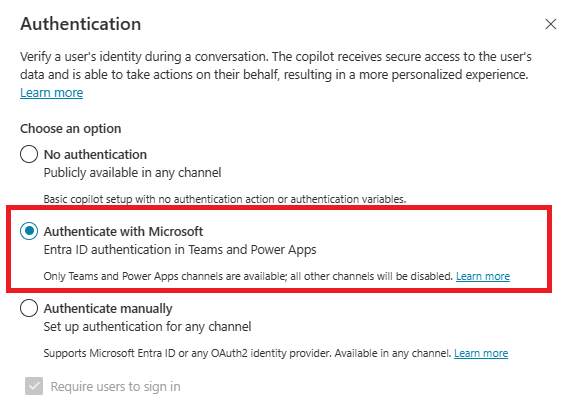
When you create a new copilot, the Authenticate with Microsoft authentication option is turned on by default. The copilot automatically uses Microsoft Entra ID authentication for Authenticate with Microsoft without requiring any manual setup and only lets you chat with your copilot on Teams. However, copilot makers in your organization can select the No authentication authentication option to allow anyone with the link to chat with your copilot.
You can use data loss prevention (DLP) policies to block your copilot makers from configuring and publishing copilots that aren't configured for authentication to help prevent data exfiltration.
If an enforced DLP policy applies to this connector, copilot makers must configure user authentication with Authenticate with Microsoft or Authenticate manually in Copilot Studio.
For more information about other DLP-related connectors, see Configure data loss prevention policies for copilots.
Configure DLP to require authentication in the Power Platform admin center
Select or create a policy
In the Power Platform admin center, under Policies, select Data policies.
Create a new policy, or choose an existing policy to edit:
If you want to create a new policy, select New policy.
If you want to choose an existing policy to edit, select the policy and select Edit policy.
Enter a name for the policy then select Next. You can change the name later.
Choose an environment
Choose one or more environments to add to your policy.
Select + Add to policy.
Select Next.
Add the connector
Use the search box to find the Chat without Microsoft Entra ID authentication in Microsoft Copilot Studio connector.
Select the connector's More actions icon (⋮), and then select Block.
Select Next.
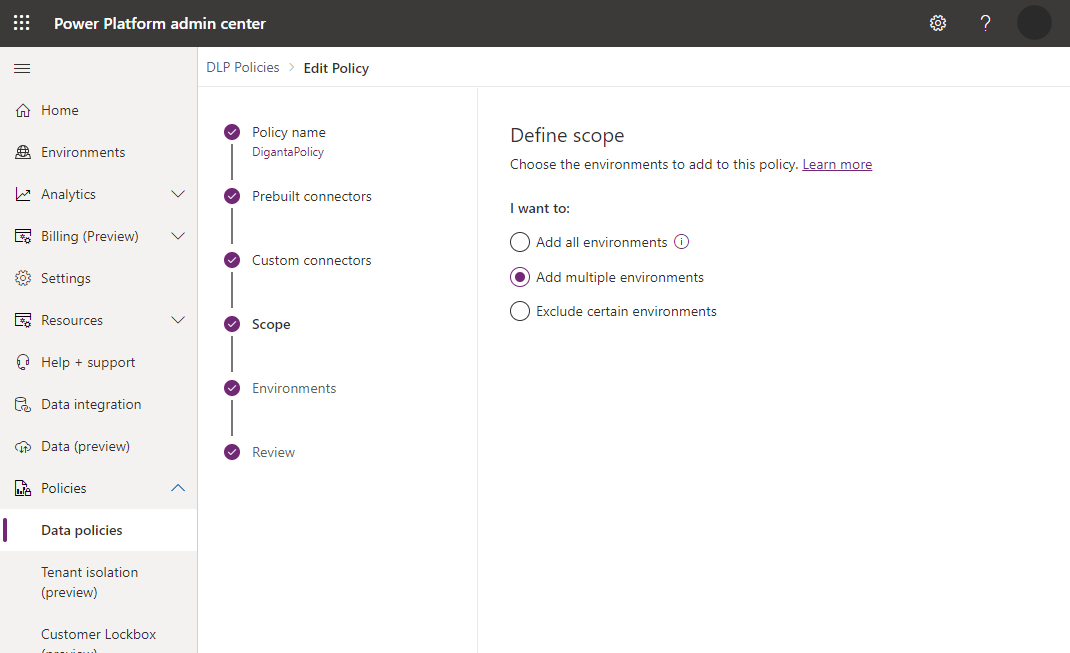
If you're a tenant admin, or an environment admin for multiple environments, you see the Scope step. Choose one or more environments that your DLP policy applies to.
Note
If the policy has a tenant scope, DLP policy will apply to all copilots.
Review your policy, then select Update policy to apply the DLP changes.
Confirm policy enforcement in Microsoft Copilot Studio
You can confirm that this connector is being used in the DLP policy from the Microsoft Copilot Studio web app.
First, open your copilot from the environment where the DLP policy is applied.
If the policy is enforced, you see an error banner with a Details button. To see details, on the Channels page, expand the error link and select the Download button.
In the details file, a row appears to describe each violation.

A copilot maker can contact their admins with the DLP download spreadsheet details to make appropriate updates to the DLP policy. Alternatively, the copilot maker can update the copilot authentication to Authenticate with Microsoft or Authenticate manually (Azure Active Directory or Azure Active Directory v2) in the Authentication configuration page. See Configure user authentication in Copilot Studio.
Authentication options aren't selectable if they don't use Microsoft Entra ID authentication.