你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
作为操作组定义的一部分,可以配置 webhook 终结点以接收活动日志警报通知。 通过 webhook 可以将这些通知路由到其他系统,以便进行后续处理或自定义操作。 本文展示用于 webhook 的 HTTP POST 数据负载的实际示例。
有关活动日志警报的详细信息,请参阅如何创建 Azure 活动日志警报。
有关操作组的信息,请参阅如何创建操作组。
对 webhook 进行身份验证
Webhook 可以选择使用基于令牌的授权进行身份验证。 Webhook URI 与令牌 ID 一同保存,例如,https://mysamplealert/webcallback?tokenid=sometokenid&someparameter=somevalue。
负载架构
POST 操作中包含的 JSON 有效负载因有效负载的 data.context.activityLog.eventSource 字段而异。
注意
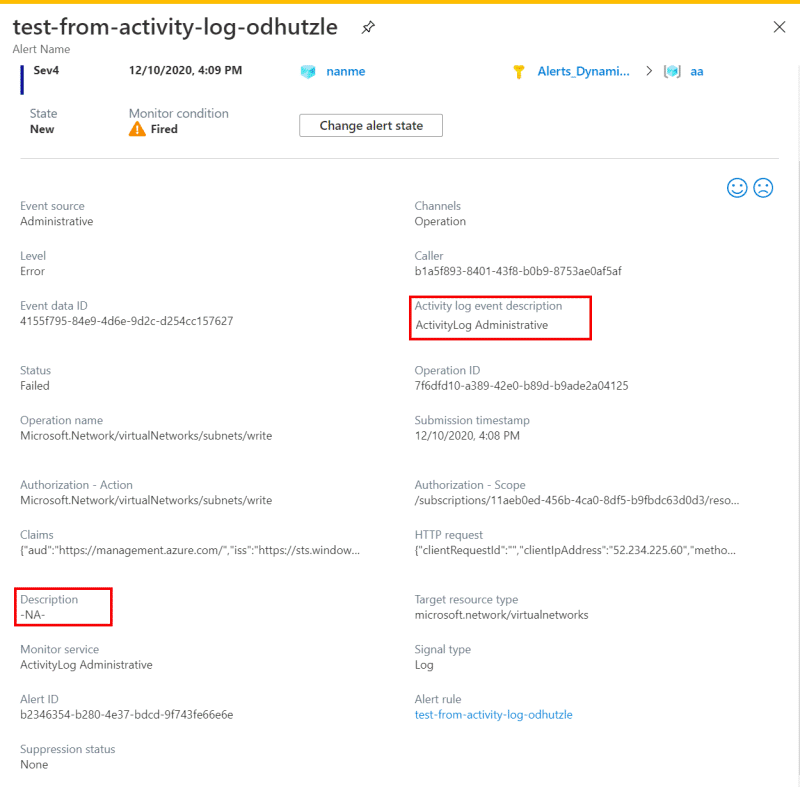
目前,作为活动日志事件的一部分的描述将复制到触发的 Alert Description 属性。
为使活动日志有效负载与其他警报类型保持一致,自 2021 年 4 月 1 日起,触发的警报属性 Description 改为包含警报规则描述。
为了准备适应该更改,我们为活动日志触发的警报创建了新属性 Activity Log Event Description。 此新属性由已经可供使用的 Description 属性填充。 因此,新字段 Activity Log Event Description 包含作为活动日志事件一部分的描述。
请检查你的警报规则、操作规则、Webhook、逻辑应用或任何其他可能使用触发警报中Description属性的配置。 将 Description 属性替换为 Activity Log Event Description 属性。
如果你的操作规则、Webhook、逻辑应用或任何其他配置中的条件目前基于活动日志警报的 Description 属性,则可能需要将其修改为基于 Activity Log Event Description 属性。
若要填充新的 Description 属性,可以在警报规则定义中添加描述。
通用
{
"schemaId": "Microsoft.Insights/activityLogs",
"data": {
"status": "Activated",
"context": {
"activityLog": {
"channels": "Operation",
"correlationId": "aaaa0000-bb11-2222-33cc-444444dddddd",
"eventSource": "Administrative",
"eventTimestamp": "2017-03-29T15:43:08.0019532+00:00",
"eventDataId": "8195a56a-85de-4663-943e-1a2bf401ad94",
"level": "Informational",
"operationName": "Microsoft.Insights/actionGroups/write",
"operationId": "aaaa0000-bb11-2222-33cc-444444dddddd",
"status": "Started",
"subStatus": "",
"subscriptionId": "aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e",
"submissionTimestamp": "2017-03-29T15:43:20.3863637+00:00",
...
}
},
"properties": {}
}
}
行政
{
"schemaId": "Microsoft.Insights/activityLogs",
"data": {
"status": "Activated",
"context": {
"activityLog": {
"authorization": {
"action": "Microsoft.Insights/actionGroups/write",
"scope": "/subscriptions/bbbb1b1b-cc2c-dd3d-ee4e-ffffff5f5f5f/resourceGroups/CONTOSO-TEST/providers/Microsoft.Insights/actionGroups/IncidentActions"
},
"claims": "{...}",
"caller": "me@contoso.com",
"description": "",
"httpRequest": "{...}",
"resourceId": "/subscriptions/bbbb1b1b-cc2c-dd3d-ee4e-ffffff5f5f5f/resourceGroups/CONTOSO-TEST/providers/Microsoft.Insights/actionGroups/IncidentActions",
"resourceGroupName": "CONTOSO-TEST",
"resourceProviderName": "Microsoft.Insights",
"resourceType": "Microsoft.Insights/actionGroups"
}
},
"properties": {}
}
}
安全性
{
"schemaId":"Microsoft.Insights/activityLogs",
"data":{"status":"Activated",
"context":{
"activityLog":{
"channels":"Operation",
"correlationId":"2518408115673929999",
"description":"Failed SSH brute force attack. Failed brute force attacks were detected from the following attackers: [\"IP Address: 01.02.03.04\"]. Attackers were trying to access the host with the following user names: [\"root\"].",
"eventSource":"Security",
"eventTimestamp":"2017-06-25T19:00:32.607+00:00",
"eventDataId":"Sec-07f2-4d74-aaf0-03d2f53d5a33",
"level":"Informational",
"operationName":"Microsoft.Security/locations/alerts/activate/action",
"operationId":"Sec-07f2-4d74-aaf0-03d2f53d5a33",
"properties":{
"attackers":"[\"IP Address: 01.02.03.04\"]",
"numberOfFailedAuthenticationAttemptsToHost":"456",
"accountsUsedOnFailedSignInToHostAttempts":"[\"root\"]",
"wasSSHSessionInitiated":"No","endTimeUTC":"06/25/2017 19:59:39",
"actionTaken":"Detected",
"resourceType":"Virtual Machine",
"severity":"Medium",
"compromisedEntity":"LinuxVM1",
"remediationSteps":"[In case this is an Azure virtual machine, add the source IP to NSG block list for 24 hours (see https://azure.microsoft.com/documentation/articles/virtual-networks-nsg/)]",
"attackedResourceType":"Virtual Machine"
},
"resourceId":"/subscriptions/12345-5645-123a-9867-123b45a6789/resourceGroups/contoso/providers/Microsoft.Security/locations/centralus/alerts/Sec-07f2-4d74-aaf0-03d2f53d5a33",
"resourceGroupName":"contoso",
"resourceProviderName":"Microsoft.Security",
"status":"Active",
"subscriptionId":"12345-5645-123a-9867-123b45a6789",
"submissionTimestamp":"2017-06-25T20:23:04.9743772+00:00",
"resourceType":"MICROSOFT.SECURITY/LOCATIONS/ALERTS"
}
},
"properties":{}
}
}
建议
{
"schemaId":"Microsoft.Insights/activityLogs",
"data":{
"status":"Activated",
"context":{
"activityLog":{
"channels":"Operation",
"claims":"{\"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress\":\"Microsoft.Advisor\"}",
"caller":"Microsoft.Advisor",
"correlationId":"bbbb1111-cc22-3333-44dd-555555eeeeee",
"description":"A new recommendation is available.",
"eventSource":"Recommendation",
"eventTimestamp":"2017-06-29T13:52:33.2742943+00:00",
"httpRequest":"{\"clientIpAddress\":\"0.0.0.0\"}",
"eventDataId":"1bf234ef-e45f-4567-8bba-fb9b0ee1dbcb",
"level":"Informational",
"operationName":"Microsoft.Advisor/recommendations/available/action",
"properties":{
"recommendationSchemaVersion":"1.0",
"recommendationCategory":"HighAvailability",
"recommendationImpact":"Medium",
"recommendationName":"Enable Soft Delete to protect your blob data",
"recommendationResourceLink":"https://portal.azure.com/#blade/Microsoft_Azure_Expert/RecommendationListBlade/recommendationTypeId/12dbf883-5e4b-4f56-7da8-123b45c4b6e6",
"recommendationType":"12dbf883-5e4b-4f56-7da8-123b45c4b6e6"
},
"resourceId":"/subscriptions/12345-5645-123a-9867-123b45a6789/resourceGroups/contoso/providers/microsoft.storage/storageaccounts/contosoStore",
"resourceGroupName":"CONTOSO",
"resourceProviderName":"MICROSOFT.STORAGE",
"status":"Active",
"subStatus":"",
"subscriptionId":"12345-5645-123a-9867-123b45a6789",
"submissionTimestamp":"2017-06-29T13:52:33.2742943+00:00",
"resourceType":"MICROSOFT.STORAGE/STORAGEACCOUNTS"
}
},
"properties":{}
}
}
ServiceHealth
{
"schemaId": "Microsoft.Insights/activityLogs",
"data": {
"status": "Activated",
"context": {
"activityLog": {
"channels": "Admin",
"correlationId": "cccc2222-dd33-4444-55ee-666666ffffff",
"description": "Active: Virtual Machines - Australia East",
"eventSource": "ServiceHealth",
"eventTimestamp": "2017-10-18T23:49:25.3736084+00:00",
"eventDataId": "6fa98c0f-334a-b066-1934-1a4b3d929856",
"level": "Informational",
"operationName": "Microsoft.ServiceHealth/incident/action",
"operationId": "cccc2222-dd33-4444-55ee-666666ffffff",
"properties": {
"title": "Virtual Machines - Australia East",
"service": "Virtual Machines",
"region": "Australia East",
"communication": "Starting at 02:48 UTC on 18 Oct 2017 you have been identified as a customer using Virtual Machines in Australia East who may receive errors starting Dv2 Promo and DSv2 Promo Virtual Machines which are in a stopped "deallocated" or suspended state. Customers can still provision Dv1 and Dv2 series Virtual Machines or try deploying Virtual Machines in other regions, as a possible workaround. Engineers have identified a possible fix for the underlying cause, and are exploring implementation options. The next update will be provided as events warrant.",
"incidentType": "Incident",
"trackingId": "0NIH-U2O",
"impactStartTime": "2017-10-18T02:48:00.0000000Z",
"impactedServices": "[{\"ImpactedRegions\":[{\"RegionName\":\"Australia East\"}],\"ServiceName\":\"Virtual Machines\"}]",
"defaultLanguageTitle": "Virtual Machines - Australia East",
"defaultLanguageContent": "Starting at 02:48 UTC on 18 Oct 2017 you have been identified as a customer using Virtual Machines in Australia East who may receive errors starting Dv2 Promo and DSv2 Promo Virtual Machines which are in a stopped "deallocated" or suspended state. Customers can still provision Dv1 and Dv2 series Virtual Machines or try deploying Virtual Machines in other regions, as a possible workaround. Engineers have identified a possible fix for the underlying cause, and are exploring implementation options. The next update will be provided as events warrant.",
"stage": "Active",
"communicationId": "636439673646212912",
"version": "0.1.1"
},
"status": "Active",
"subscriptionId": "cccc2c2c-dd3d-ee4e-ff5f-aaaaaa6a6a6a",
"submissionTimestamp": "2017-10-18T23:49:28.7864349+00:00"
}
},
"properties": {}
}
}
有关服务运行状况通知活动日志警报的特定架构详细信息,请参阅服务运行状况通知。 还可以了解如何使用现有的问题管理解决方案配置服务运行状况 Webhook 通知。
ResourceHealth
{
"schemaId": "Microsoft.Insights/activityLogs",
"data": {
"status": "Activated",
"context": {
"activityLog": {
"channels": "Admin, Operation",
"correlationId": "dddd3333-ee44-5555-66ff-777777aaaaaa",
"eventSource": "ResourceHealth",
"eventTimestamp": "2018-09-04T23:09:03.343+00:00",
"eventDataId": "2b37e2d0-7bda-4de7-ur8c6-1447d02265b2",
"level": "Informational",
"operationName": "Microsoft.Resourcehealth/healthevent/Activated/action",
"operationId": "2b37e2d0-7bda-489f-81c6-1447d02265b2",
"properties": {
"title": "Virtual Machine health status changed to unavailable",
"details": "Virtual machine has experienced an unexpected event",
"currentHealthStatus": "Unavailable",
"previousHealthStatus": "Available",
"type": "Downtime",
"cause": "PlatformInitiated"
},
"resourceId": "/subscriptions/<subscription Id>/resourceGroups/<resource group>/providers/Microsoft.Compute/virtualMachines/<resource name>",
"resourceGroupName": "<resource group>",
"resourceProviderName": "Microsoft.Resourcehealth/healthevent/action",
"status": "Active",
"subscriptionId": "<subscription Id>",
"submissionTimestamp": "2018-09-04T23:11:06.1607287+00:00",
"resourceType": "Microsoft.Compute/virtualMachines"
}
}
}
}
| 元素名称 | 说明 |
|---|---|
| 地位 | 用于度量值警报。 对于活动日志警报,始终设置为 activated。 |
| 上下文 | 事件的上下文。 |
| 资源提供者名称 | 受影响资源的资源提供程序。 |
| 条件类型 | 始终为 Event。 |
| 名称 | 警报规则的名称。 |
| 身份证件 | 警报的资源 ID。 |
| 描述 | 创建警报时设置警报说明。 |
| 订阅ID | Azure 订阅 ID。 |
| timestamp | 处理请求的 Azure 服务生成事件的时间。 |
| 资源ID | 受影响资源的资源 ID。 |
| 资源组名称 | 受影响资源的资源组名称。 |
| 属性 | 一组包含事件详细信息的 <Key, Value> 对(即 Dictionary<String, String>)。 |
| 事件 | 包含有关事件的元数据的元素。 |
| 授权 | 事件的 Azure 基于角色的访问控制属性。 这些属性通常包括动作、角色和范围。 |
| category | 事件的类别。 支持的值包括 Administrative、Alert、Security、ServiceHealth 和 Recommendation。 |
| 来电者 | 执行操作的用户的电子邮件地址(基于可用性的 UPN 声明或 SPN 声明)。 对于某些系统调用可以为 null。 |
| correlationId | 通常是字符串格式的 GUID。 具有 correlationId 的事件属于同一个较大操作,通常共享一个 correlationId。 |
| eventDescription | 事件的静态文本说明。 |
| eventDataId | 事件的唯一标识符。 |
| eventSource | 生成事件的 Azure 服务或基础结构的名称。 |
| http请求 | 请求通常包括 clientRequestId、clientIpAddress 和 HTTP 方法(例如 PUT)。 |
| level | 以下值之一:Critical、Error、Warning 和 Informational。 |
| operationId | 通常是在与单个操作对应的事件之间共享的 GUID。 |
| 操作名称 | 操作的名称。 |
| 属性 | 事件的属性。 |
| 地位 | 字符串。 操作状态 常用值包括 Started、In Progress、Succeeded、Failed、Active 和 Resolved。 |
| subStatus | 通常包含对应 REST 调用的 HTTP 状态代码。 它还可能包含描述子状态的其他字符串。 常用 substatus 值包括 OK(HTTP 状态代码:200)、Created(HTTP 状态代码:201)、Accepted(HTTP 状态代码:202)、No Content(HTTP 状态代码:204)、Bad Request(HTTP 状态代码:400)、Not Found(HTTP 状态代码:404)、Conflict(HTTP 状态代码:409)、Internal Server Error(HTTP 状态代码:500)、Service Unavailable(HTTP 状态代码:503)和 Gateway Timeout(HTTP 状态代码:504)。 |
有关所有其他活动日志警报的特定架构的详细信息,请参阅 Azure 活动日志概述。
后续步骤
- 了解有关活动日志的更多信息。
- 对 Azure 警报执行 Azure 自动化脚本 (Runbook)。
- 使用逻辑应用通过 Twilio 从 Azure 警报发送短信。 本示例适用于度量值警报,但经过修改后可用于活动日志警报。
- 使用逻辑应用从 Azure 警报发送 Slack 消息。 本示例适用于度量值警报,但经过修改后可用于活动日志警报。
- 使用逻辑应用从 Azure 警报中将消息发送到 Azure 队列。 本示例适用于度量值警报,但经过修改后可用于活动日志警报。