你当前正在访问 Microsoft Azure Global Edition 技术文档网站。 如果需要访问由世纪互联运营的 Microsoft Azure 中国技术文档网站,请访问 https://docs.azure.cn。
快速入门:使用 Bicep 创建具有专用对等互连的 ExpressRoute 线路
本快速入门介绍如何使用 Bicep 来创建具有专用对等互连的 ExpressRoute 线路。
Bicep 是一种特定于域的语言 (DSL),使用声明性语法来部署 Azure 资源。 它提供简明的语法、可靠的类型安全性以及对代码重用的支持。 Bicep 会针对你的 Azure 基础结构即代码解决方案提供最佳创作体验。
如果没有 Azure 订阅,请在开始之前创建一个免费帐户。
本快速入门中使用的 Bicep 文件来自 Azure 快速入门模板。
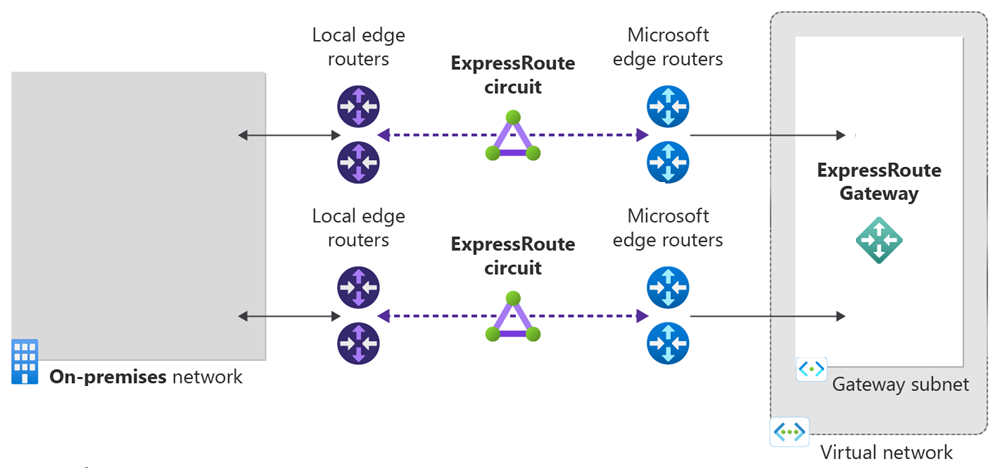
在本快速入门中,你将创建一个以 Equinix 为服务提供商的 ExpressRoute 线路。 该线路将使用高级 SKU,其带宽为 50 Mbps,对等互连位置为华盛顿特区。 使用主要子网 192.168.10.16/30 和辅助子网 192.168.10.20/30 来启用专用对等互连。 创建虚拟网络以及 HighPerformance ExpressRoute 网关。
@description('Location for all resources deployed in the Bicep file')
param location string = resourceGroup().location
@description('ExpressRoute peering location')
param erpeeringLocation string = 'Washington DC'
@description('Name of the ExpressRoute circuit')
param erCircuitName string = 'er-ckt01'
@description('Name of the ExpressRoute provider')
param serviceProviderName string = 'Equinix'
@description('Tier ExpressRoute circuit')
@allowed([
'Premium'
'Standard'
])
param erSKU_Tier string = 'Premium'
@description('Billing model ExpressRoute circuit')
@allowed([
'MeteredData'
'UnlimitedData'
])
param erSKU_Family string = 'MeteredData'
@description('Bandwidth ExpressRoute circuit')
@allowed([
50
100
200
500
1000
2000
5000
10000
])
param bandwidthInMbps int = 50
@description('autonomous system number used to create private peering between the customer edge router and MSEE routers')
param peerASN int = 65001
@description('point-to-point network prefix of primary link between the customer edge router and MSEE router')
param primaryPeerAddressPrefix string = '192.168.10.16/30'
@description('point-to-point network prefix of secondary link between the customer edge router and MSEE router')
param secondaryPeerAddressPrefix string = '192.168.10.20/30'
@description('VLAN Id used between the customer edge routers and MSEE routers. primary and secondary link have the same VLAN Id')
param vlanId int = 100
@description('name of the Virtual Network')
param vnetName string = 'vnet1'
@description('name of the subnet')
param subnet1Name string = 'subnet1'
@description('address space assigned to the Virtual Network')
param vnetAddressSpace string = '10.10.10.0/24'
@description('network prefix assigned to the subnet')
param subnet1Prefix string = '10.10.10.0/25'
@description('network prefixes assigned to the gateway subnet. It has to be a network prefix with mask /27 or larger')
param gatewaySubnetPrefix string = '10.10.10.224/27'
@description('name of the ExpressRoute Gateway')
param gatewayName string = 'er-gw'
@description('ExpressRoute Gateway SKU')
@allowed([
'Standard'
'HighPerformance'
'UltraPerformance'
'ErGw1AZ'
'ErGw2AZ'
'ErGw3AZ'
])
param gatewaySku string = 'HighPerformance'
var erSKU_Name = '${erSKU_Tier}_${erSKU_Family}'
var gatewayPublicIPName = '${gatewayName}-pubIP'
var nsgName = 'nsg'
resource erCircuit 'Microsoft.Network/expressRouteCircuits@2023-09-01' = {
name: erCircuitName
location: location
sku: {
name: erSKU_Name
tier: erSKU_Tier
family: erSKU_Family
}
properties: {
serviceProviderProperties: {
serviceProviderName: serviceProviderName
peeringLocation: erpeeringLocation
bandwidthInMbps: bandwidthInMbps
}
allowClassicOperations: false
}
}
resource peering 'Microsoft.Network/expressRouteCircuits/peerings@2023-09-01' = {
parent: erCircuit
name: 'AzurePrivatePeering'
properties: {
peeringType: 'AzurePrivatePeering'
peerASN: peerASN
primaryPeerAddressPrefix: primaryPeerAddressPrefix
secondaryPeerAddressPrefix: secondaryPeerAddressPrefix
vlanId: vlanId
}
}
resource nsg 'Microsoft.Network/networkSecurityGroups@2023-09-01' = {
name: nsgName
location: location
properties: {
securityRules: [
{
name: 'SSH-rule'
properties: {
description: 'allow SSH'
protocol: 'Tcp'
sourcePortRange: '*'
destinationPortRange: '22'
sourceAddressPrefix: '*'
destinationAddressPrefix: 'VirtualNetwork'
access: 'Allow'
priority: 500
direction: 'Inbound'
}
}
{
name: 'RDP-rule'
properties: {
description: 'allow RDP'
protocol: 'Tcp'
sourcePortRange: '*'
destinationPortRange: '3389'
sourceAddressPrefix: '*'
destinationAddressPrefix: 'VirtualNetwork'
access: 'Allow'
priority: 600
direction: 'Inbound'
}
}
]
}
}
resource vnet 'Microsoft.Network/virtualNetworks@2023-09-01' = {
name: vnetName
location: location
properties: {
addressSpace: {
addressPrefixes: [
vnetAddressSpace
]
}
subnets: [
{
name: subnet1Name
properties: {
addressPrefix: subnet1Prefix
networkSecurityGroup: {
id: nsg.id
}
}
}
{
name: 'GatewaySubnet'
properties: {
addressPrefix: gatewaySubnetPrefix
}
}
]
}
}
resource gatewayPublicIP 'Microsoft.Network/publicIPAddresses@2023-09-01' = {
name: gatewayPublicIPName
location: location
sku: {
name: 'Standard'
tier: 'Regional'
}
properties: {
publicIPAllocationMethod: 'Static'
}
}
resource gateway 'Microsoft.Network/virtualNetworkGateways@2023-09-01' = {
name: gatewayName
location: location
properties: {
ipConfigurations: [
{
properties: {
privateIPAllocationMethod: 'Dynamic'
subnet: {
id: resourceId('Microsoft.Network/virtualNetworks/subnets', vnetName, 'GatewaySubnet')
}
publicIPAddress: {
id: gatewayPublicIP.id
}
}
name: 'gwIPconf'
}
]
gatewayType: 'ExpressRoute'
sku: {
name: gatewaySku
tier: gatewaySku
}
vpnType: 'RouteBased'
}
dependsOn: [
vnet
]
}
output erCircuitName string = erCircuitName
output gatewayName string = gatewayName
output gatewaySku string = gatewaySku
Bicep 文件中已定义了多项 Azure 资源:
- Microsoft.Network/expressRouteCircuits
- Microsoft.Network/expressRouteCircuits/peerings(用于线路上已启用的专用对等互连)
- Microsoft.Network/networkSecurityGroups(网络安全组应用于虚拟网络中的子网)
- Microsoft.Network/virtualNetworks
- Microsoft.Network/publicIPAddresses(公共 IP 由 ExpressRoute 网关使用)
- Microsoft.Network/virtualNetworkGateways(ExpressRoute 网关用于将 VNet 链接到线路)
将该 Bicep 文件另存为本地计算机上的 main.bicep。
使用 Azure CLI 或 Azure PowerShell 来部署该 Bicep 文件。
az group create --name exampleRG --location eastus az deployment group create --resource-group exampleRG --template-file main.bicep部署完成后,应会看到一条指出部署成功的消息。
使用 Azure 门户、Azure CLI 或 Azure PowerShell 列出资源组中已部署的资源。
az resource list --resource-group exampleRG
备注
你将需要调用提供程序来完成预配过程,然后才能将虚拟网络链接到线路。
如果不再需要,请使用 Azure 门户、Azure CLI 或 Azure PowerShell 删除 VM 和资源组中的所有资源。
az group delete --name exampleRG
在本快速入门中,我们创建了:
- ExpressRoute 线路
- 虚拟网络
- VPN 网关
- 公共 IP
- 网络安全组
若要了解如何将虚拟网络链接到线路,请继续学习 ExpressRoute 教程。