Hi @Pinkesh Dashrathbhai Patel ,
Thanks for reaching out.
I understand that you are trying to authorize your APIs using client credentials flow, but not able to get scp claims in the Azure AD access token.
Client credentials grant flow is not currently directly supported by the Azure AD B2C, You can set up client credentials flow using Azure AD and the Microsoft identity platform endpoint for an application in your Azure AD B2C tenant because an Azure AD B2C tenant shares some functionality with Azure AD.
Azure AD Authorization code flow allows to authenticate using user's delegated identity (Delegated Permissions) and returned permissions as scp claims in the token. However ,client credential Flow in Azure AD get tokens using application's identity(Application Permissions) as there is no user interaction in this flow and return permissions as roles claim in the access token.
To add scopes as application permissions, you need to create the appRole to the API, and then grant that role as an application permission to the client application to access the application permissions.
To set the application permission, you need to assign app role to the application.
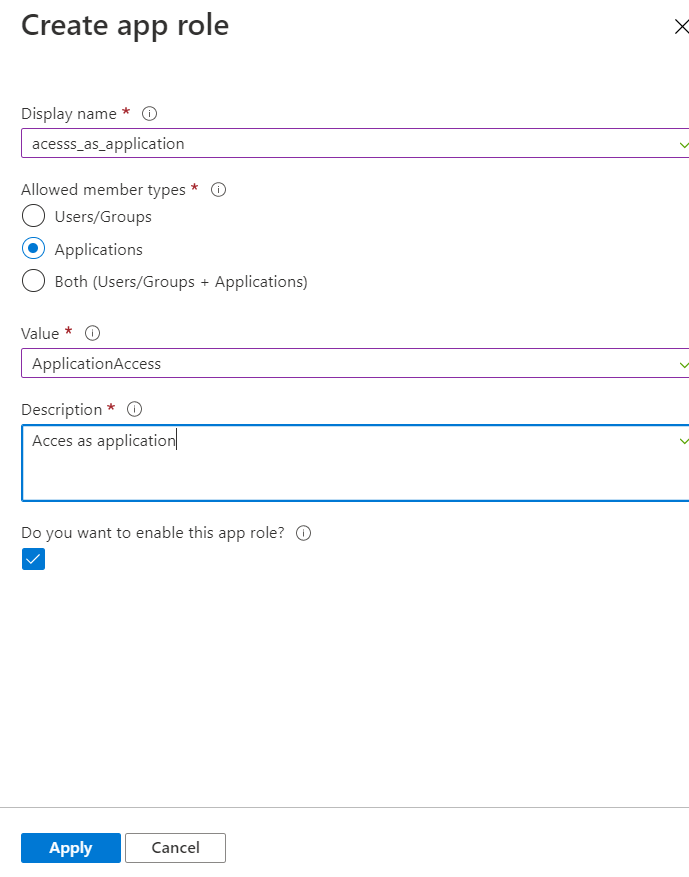
There might be chance you are not able to see App roles in the B2C blade as client credential is not supported in B2C.
To add App roles in your Web API , you can update the value of app roles in manifest as:
"appRoles": [
{
"allowedMemberTypes": [
"Application"
],
"description": "Access as application",
"displayName": "access_as_application",
"id": "c0999c9d-bf5f-4202-8b1c-f660baf4f78b",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "access_as_application"
}
],
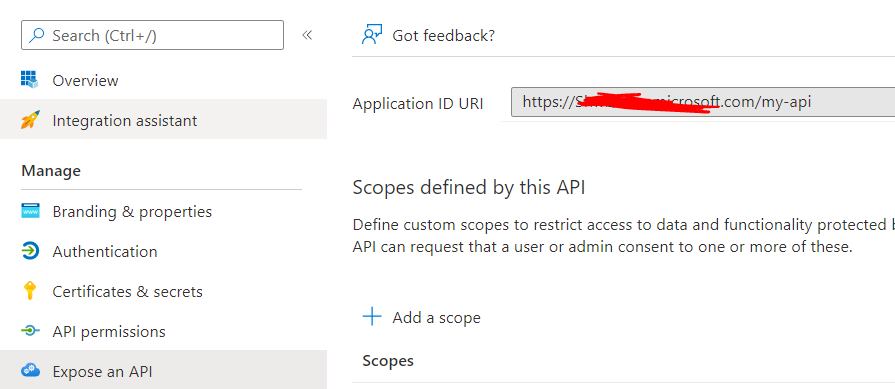
Also, you need to expose the Web API protected by Azure as:
Azure portal>App registrations>Expose an API> set the application id URI
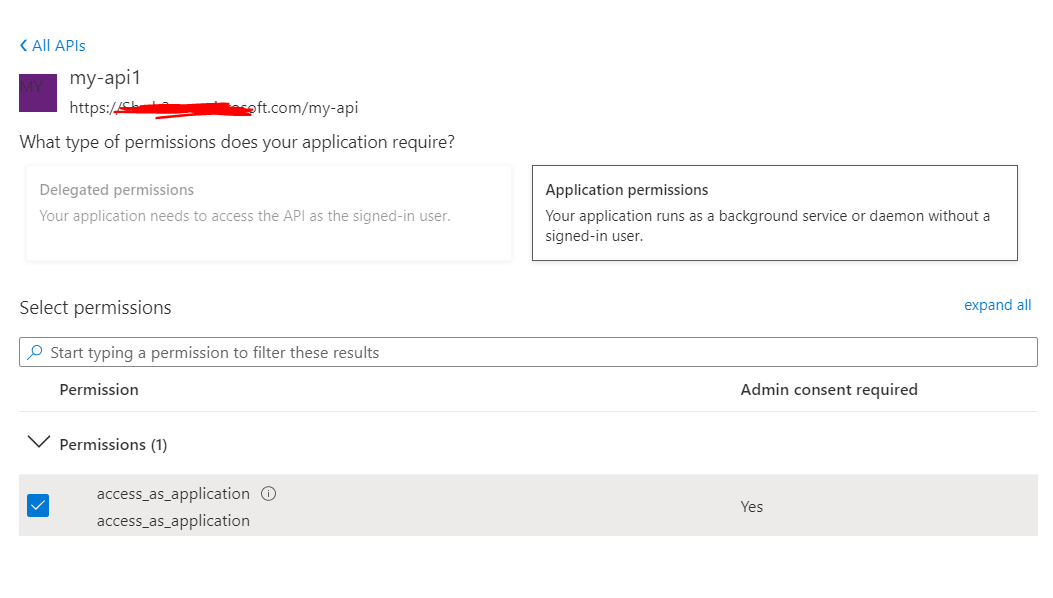
Next, in the client application>API permissions>Add a permission>My APIs>your api application>and grant admin consent to that permission.
Now get the access token with client credential flow using token endpoint to call Web API.
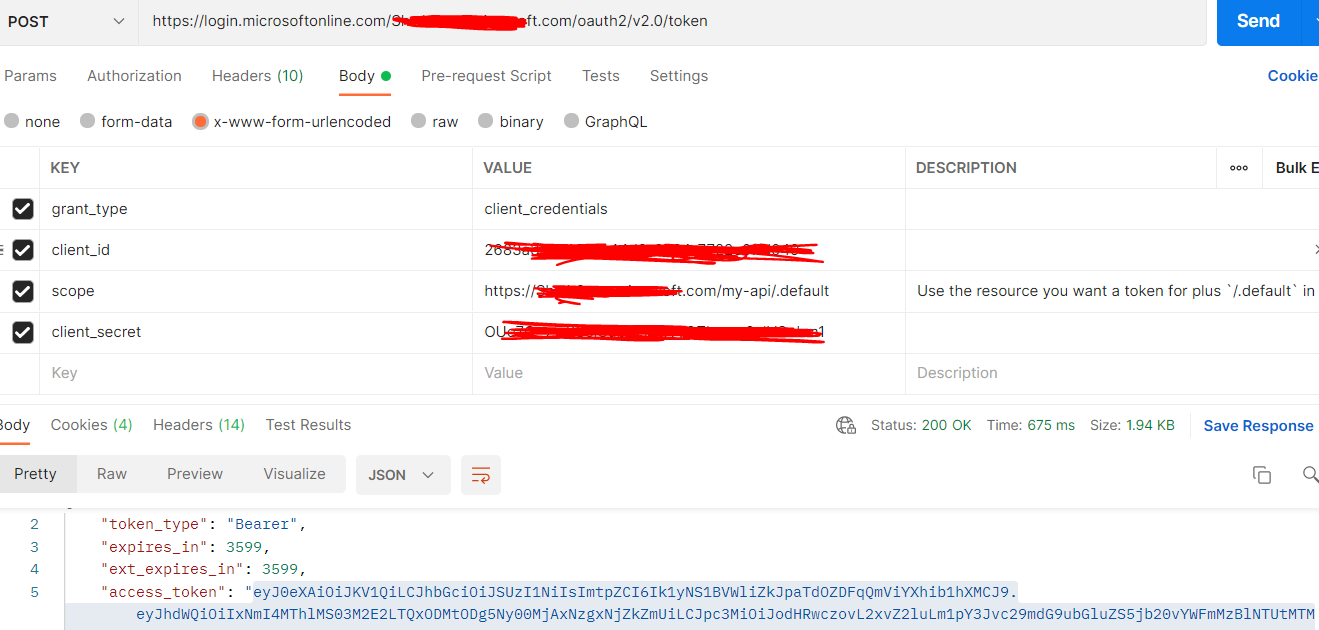
You can decode the access token using jwt.ms to see application permissions in roles claim.
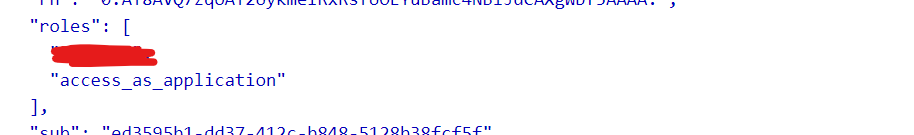
Hope this will help. If you have any doubt on this, please let us know.
Thanks,
Shweta
-------------------------------
Please remember to "Accept Answer" if answer helped you.