This is not possible with Azure AD. You can pass optional claims but the provisioning for transforming claims on the basis of group membership is not available as of now.
As an alternative, you can configure app roles in the application manifest and pass it in the token. Below is an example of how to add Writer role in app, similarly you can create Admin role. Refer to How to: Add app roles in your application and receive them in the token for more details.
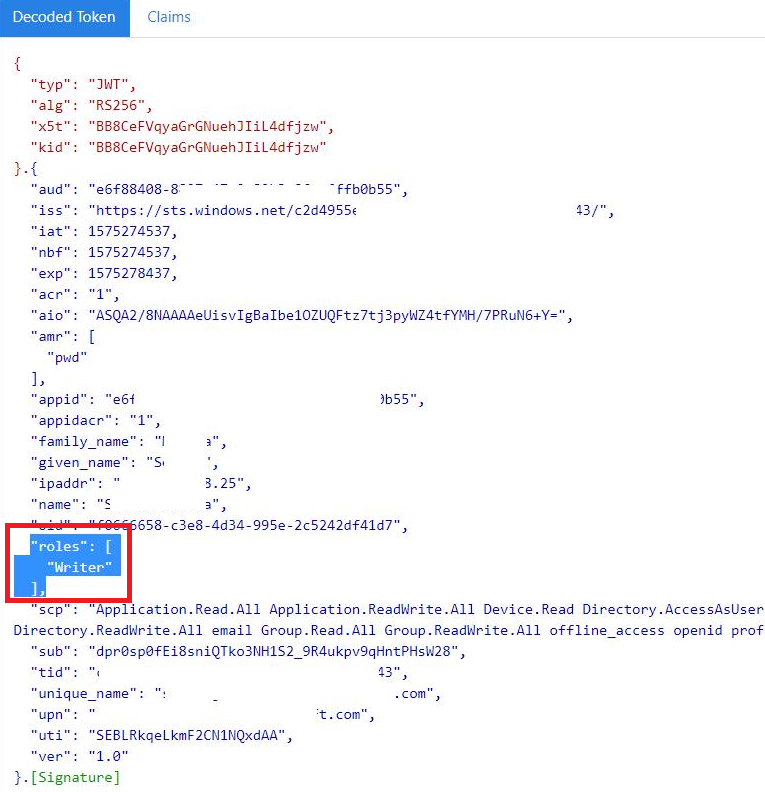
Below is how the app roles appear in the token:
Another alternative solution would be to pass all the groups in the token and configure the application to make authorization decisions based on the group claims.
Hope this information would help.
