I would like to add a user to a group using a custom policy.
I have this claim:
<ClaimType Id="graphUserUri">
<DisplayName>graphUserUri</DisplayName>
<DataType>string</DataType>
</ClaimType>
Which I use it with this transformation:
<ClaimsTransformation Id="REST-AddToFreelancersGroup-UserUri" TransformationMethod="FormatStringClaim">
<InputClaims>
<InputClaim ClaimTypeReferenceId="objectId" TransformationClaimType="inputClaim" />
</InputClaims>
<InputParameters>
<InputParameter Id="stringFormat" DataType="string" Value='{{ "@odata.id " : "https://graph.microsoft.com/v1.0/users/{0}" }}' />
</InputParameters>
<OutputClaims>
<OutputClaim ClaimTypeReferenceId="graphUserUri" TransformationClaimType="outputClaim" />
</OutputClaims>
</ClaimsTransformation>
I get a token for the graph api using:
<TechnicalProfile Id="REST-AcquireAccessTokenForGraph">
<DisplayName>Acquire Token</DisplayName>
<Protocol Name="Proprietary" Handler="Web.TPEngine.Providers.RestfulProvider, Web.TPEngine, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null" />
<Metadata>
<Item Key="ServiceUrl">https://login.microsoftonline.com/TestAuth312.onmicrosoft.com/oauth2/v2.0/token</Item>
<Item Key="AuthenticationType">Basic</Item>
<Item Key="SendClaimsIn">Form</Item>
</Metadata>
<CryptographicKeys>
<Key Id="BasicAuthenticationUsername" StorageReferenceId="B2C_1A_MSGraphClientId" />
<Key Id="BasicAuthenticationPassword" StorageReferenceId="B2C_1A_MSGraphClientSecret" />
</CryptographicKeys>
<InputClaims>
<InputClaim ClaimTypeReferenceId="grant_type" DefaultValue="client_credentials" />
<InputClaim ClaimTypeReferenceId="scope" DefaultValue="https://graph.microsoft.com/.default" />
</InputClaims>
<OutputClaims>
<OutputClaim ClaimTypeReferenceId="bearerToken" PartnerClaimType="access_token" />
</OutputClaims>
<UseTechnicalProfileForSessionManagement ReferenceId="SM-Noop" />
</TechnicalProfile>
And I make a call to the graph api to add the user to a group:
<TechnicalProfile Id="REST-AddToFreelancersGroup">
<DisplayName>Add user to group</DisplayName>
<Protocol Name="Proprietary" Handler="Web.TPEngine.Providers.RestfulProvider, Web.TPEngine, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null" />
<Metadata>
<Item Key="ServiceUrl">https://graph.microsoft.com/v1.0/groups/4e780e3e-1d75-4b5b-b1da-7c71edbac077/members/$ref</Item>
<Item Key="SendClaimsIn">Body</Item>
<Item Key="ClaimUsedForRequestPayload">graphUserUri</Item>
<Item Key="AuthenticationType">Bearer</Item>
<Item Key="UseClaimAsBearerToken">bearerToken</Item>
<Item Key="DebugMode">true</Item>
</Metadata>
<InputClaimsTransformations>
<InputClaimsTransformation ReferenceId="REST-AddToFreelancersGroup-UserUri"/>
</InputClaimsTransformations>
<InputClaims>
<InputClaim ClaimTypeReferenceId="objectId" />
<InputClaim ClaimTypeReferenceId="graphUserUri" />
<InputClaim ClaimTypeReferenceId="bearerToken" />
</InputClaims>
<OutputClaims>
<OutputClaim ClaimTypeReferenceId="err" />
</OutputClaims>
<UseTechnicalProfileForSessionManagement ReferenceId="SM-Noop" />
</TechnicalProfile>
All these steps work perfectly in PostMan but as a custom policy they end up in a Bad Request.
My issue is with Custom Policies and Application Insights.
The logs are limited at 30k characters and they terminate right at the important part
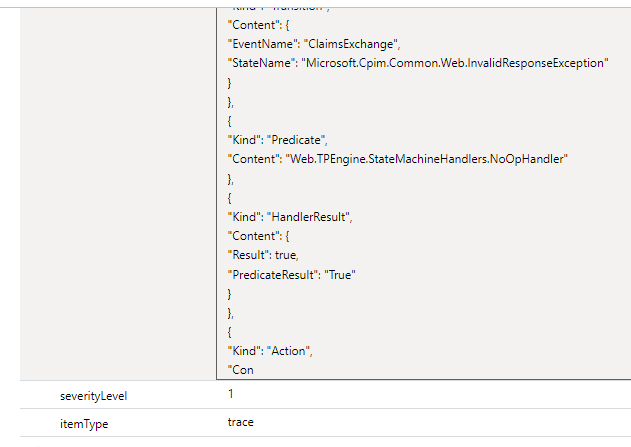
The next log available is just stating that the error happened without further details.
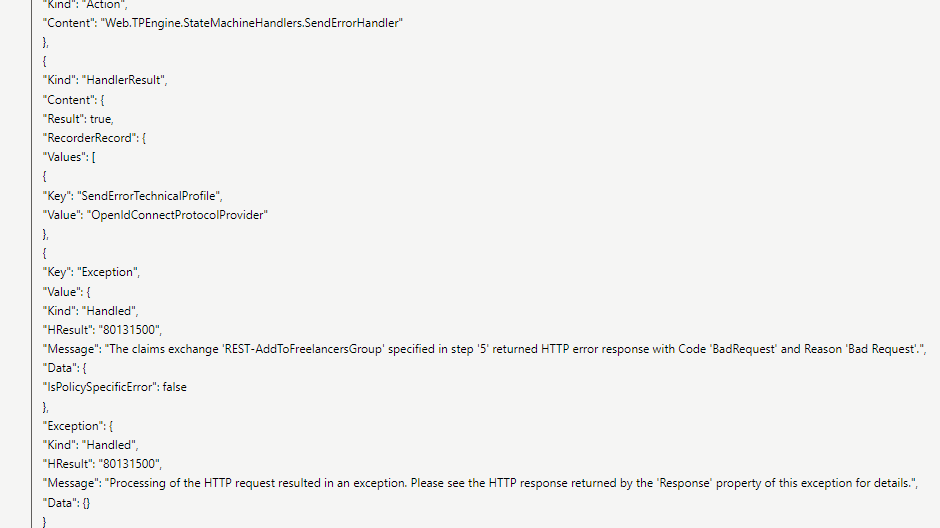
The generated claim inside the logs looks fine:
"graphUserUri": "{ \"@odata.id \" : \"https://graph.microsoft.com/v1.0/users/f0d3a13e-c2f3-4607-be90-ba0e41ffd0b1\" }"
and I tested the generated bearer token in postman and it works.
The issue seems to be with the call to the API but due to the lack of logs I can't figure it out.
I've tried to enable all the debugging features of the custom policies including
<Item Key="DebugMode">true</Item> for the techincal profile and
DeploymentMode="Development"
UserJourneyRecorderEndpoint="urn:journeyrecorder:applicationinsights"
for the TrustFrameworkPolicy
I'm happy to offer additional details if asked.


