@Jarret McGraw
Thank you for your post and I apologize for the delayed response!
I understand that you're trying to create a new KQL query for Security Alerts or Incidents based off a set of users within Microsoft Sentinel. To hopefully help point you in the right direction or resolve your issue, I'll share my findings below.
Findings:
When it comes to creating a query for Security Alerts or Incidents based off a set of users within MS Sentinel, you can definitely leverage a Watchlist and query for the users' name or ID.
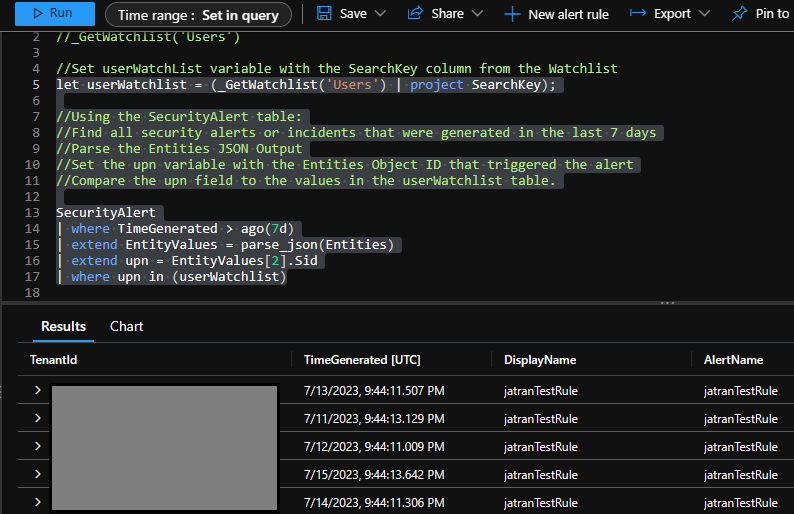
I created a sample query for your reference which compares the upn field to the values in the userWatchlist table using the in operator. This should return your security alerts or incidents that were generated in the last 7 days and where the user that triggered the alert is in the Watchlist.
-
Note: This query assumes that the Sid field is always the third entity in the Entities array. If the order of the array changes, this may not work as expected. Additionally, the "in" operator is case-sensitive, so you'll want to ensure your values in the Watchlist match
Watchlist Data:
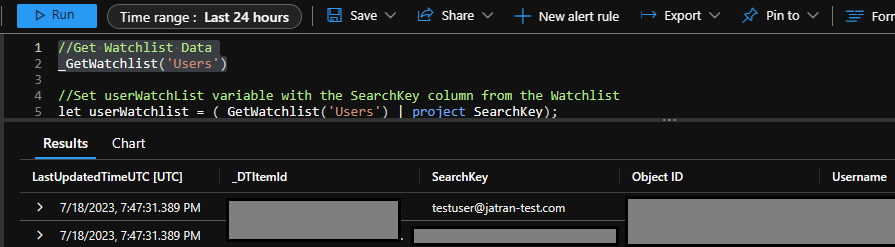
//Set userWatchList variable with the SearchKey column from the Watchlist
let userWatchlist = (_GetWatchlist('Users') | project SearchKey);
//Using the SecurityAlert table:
//Find all security alerts or incidents that were generated in the last 7 days
//Parse the Entities JSON Output
//Set the upn variable with the Entities Object ID that triggered the alert
//Compare the upn field to the values in the userWatchlist table.
SecurityAlert
| where TimeGenerated > ago(7d)
| extend EntityValues = parse_json(Entities)
| extend upn = EntityValues[2].Sid
| where upn in (userWatchlist)
Additional Links:
I hope this helps!
If you have any other questions, please let me know. Thank you for your time and patience throughout this issue.
If the information helped address your question, please Accept the answer. This will help us and also improve searchability for others in the community who might be researching similar information.


