Hello @Sohaib Asghar ,
Apologies for the delay in my response.
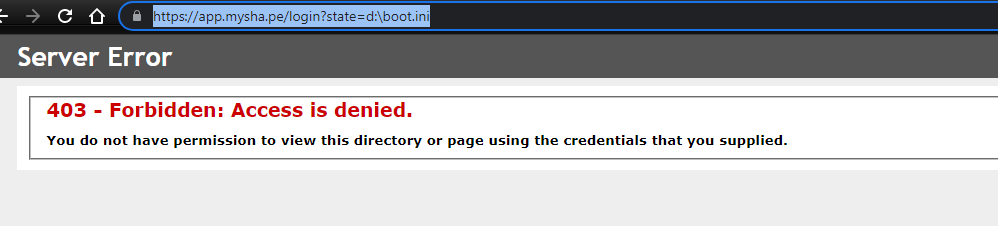
I understand that you have a Web application hosted in Azure App service protected by Application Gateway and it is throwing 403 error when you enter the following URL - https://app.mysha.pe/login?state=d:boot.ini in the browser.
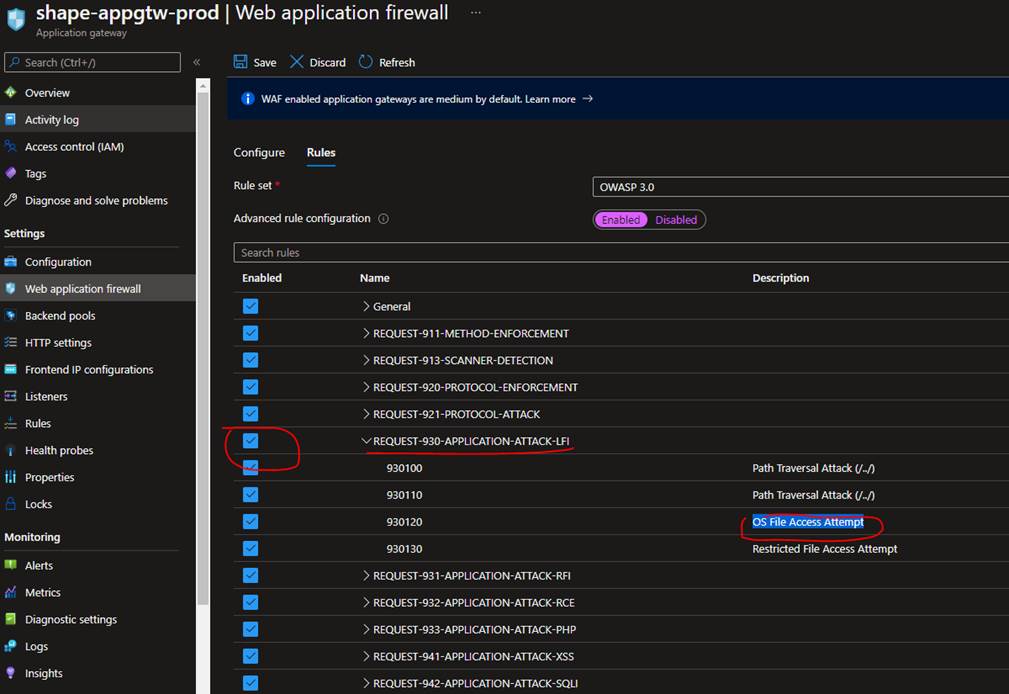
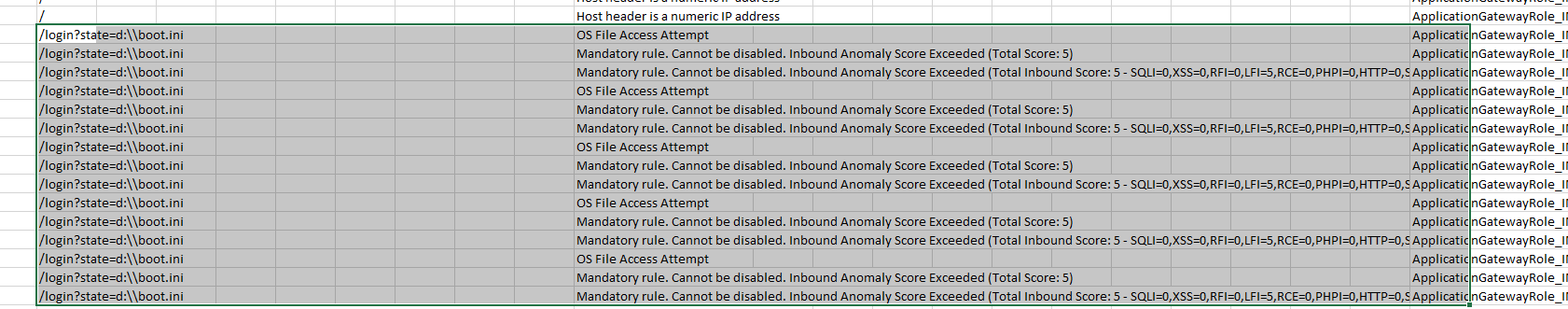
Post discussion on this issue, we found that the configuration of Application gateway v1 is correct and the WAF is preventing the application page access and throwing 403 error as you have WAF enabled in "Prevention" mode. You found that the URL is hitting a mandatory rule in WAF, which cannot be disabled and would need the way forward to fix this issue.
If you believe that the blocked URL is safe and would like to let it pass through the WAF, you could use an Exclusion list.
Refer : https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/web-application-firewall-troubleshoot#using-an-exclusion-list
https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/application-gateway-waf-configuration
Example 2 from the below doc matches your scenario:
https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/application-gateway-waf-configuration#example-2
So, you could setup an exclusion list as shown in the above example replacing your own values and it won't evaluate the string d:boot.ini, but it will still evaluate the parameter name state.
To add an exclusion, you need to create a WAF policy and associate it with your Application gateway.
Refer : https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/policy-overview
You can also set the exclusion via Azure portal in your WAF policy as below:

Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.