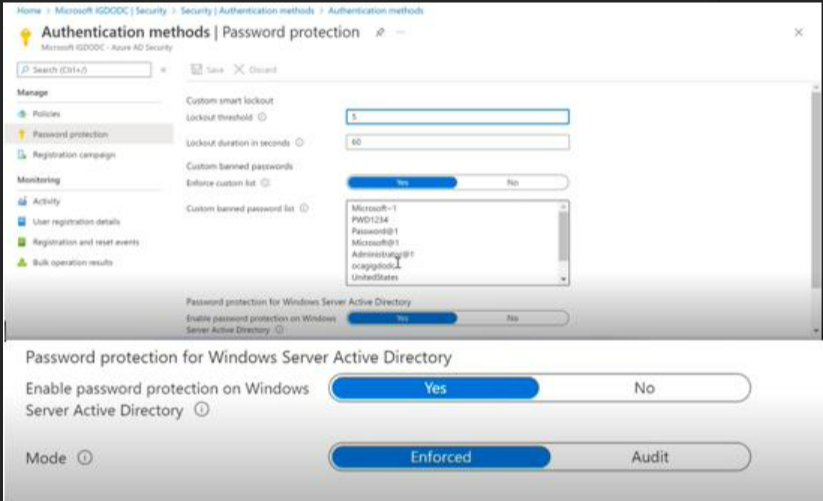
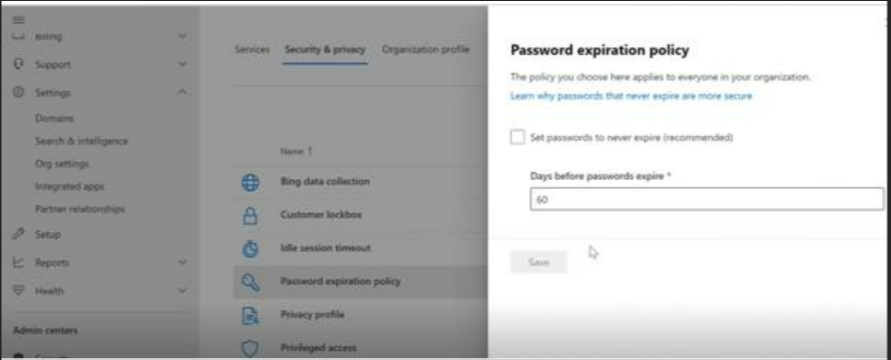
Hello @K Roja and thanks for reaching out. Azure AD password protection cannot be managed trough MS Graph. Azure AD password expiration policy can be managed through MSOL Get-MsolPasswordPolicy and Set-MsolPasswordPolicy cmdlets.
Alternately and for Password protection you might use the Azure AD Portal backed. Please keep in mind this API is not publicly supported and can change in the future w/o notice. You can use az cli to get an access token:
az account get-access-token --resource 74658136-14ec-4630-ad9b-26e160ff0fc6
POST https://main.iam.ad.ext.azure.com/api/AuthenticationMethods/PasswordPolicy
{
"lockoutThreshold": 10,
"lockoutDurationInSeconds": 60,
"enforceCustomBannedPasswords": false,
"customBannedPasswords": [],
"enableBannedPasswordCheckOnPremises": true,
"bannedPasswordCheckOnPremisesMode": 1
}
Let us know if you need additional assistance. If the answer was helpful, please accept it and complete the quality survey so that others can find a solution.