Thank you for posting a detailed question here.
Based on my understanding from your question above. I think you are facing the issue described in this article here.
A host name mismatch can lead to problems when the application server issues cookies and uses the incoming host name to construct the Domain attribute of the cookie. The Domain attribute ensures that the cookie will be used only for that specific domain. These cookies can be generated by the application code or by platform features like the App Service ARR affinity setting. This diagram illustrates the problem:
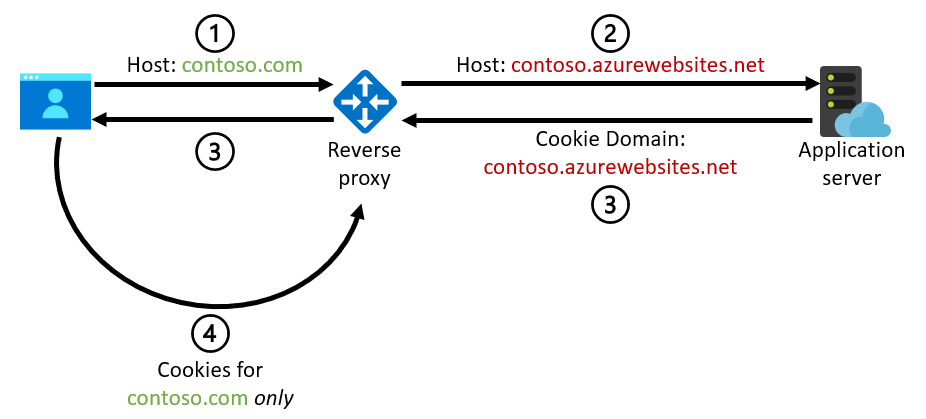 In order to prevent the issue above we recommend that you preserve the original host name in the call between the reverse proxy and the back-end application server:
In order to prevent the issue above we recommend that you preserve the original host name in the call between the reverse proxy and the back-end application server:
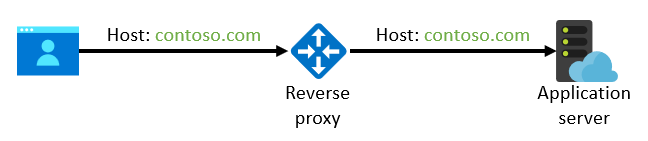 For App Service, you can attach a custom domain name to the web app and avoid using the default
For App Service, you can attach a custom domain name to the web app and avoid using the default azurewebsites.net host name towards the back end. You don't need to change your DNS resolution when you attach a custom domain to the web app: you can verify the domain by using a TXT record without affecting your regular CNAME or A records. (These records will still resolve to the IP address of the reverse proxy.) If you require end-to-end TLS/SSL, you can import an existing certificate from Key Vault or use an App Service Certificate for your custom domain.
Please let us know if the proposed solution above does not work for you and we will gladly continue with our discussion.
I hope this has been helpful! Your feedback is important so please take a moment to accept answers. If you still have questions, please let us know what is needed in the comments so the question can be answered. Thank you for helping to improve Microsoft Q&A!