Hello @Darius Basznianin ,
Thanks for reaching out.
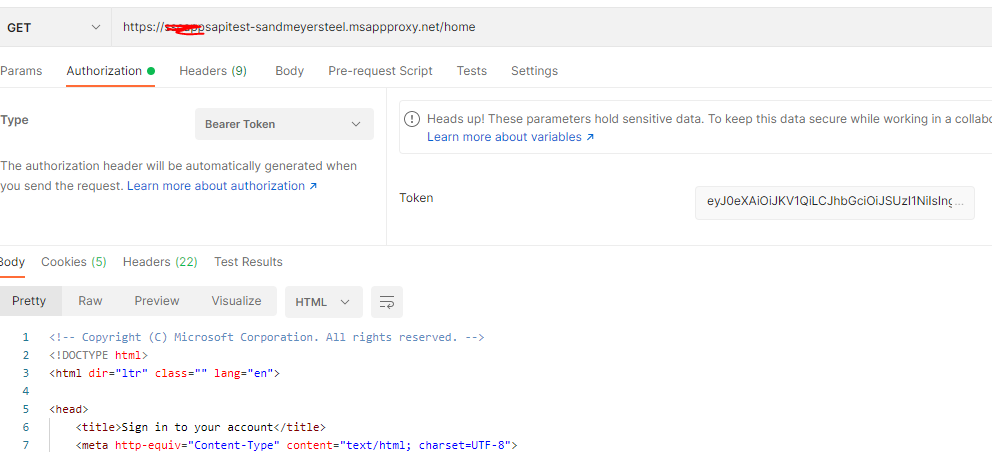
Here are detailed guidance on accessing published proxy application through Native application programmatically.
To give your native app access to interact with published backend web API: https://learn.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-secure-api-access
To give your native app access to interact with published backend web applications: https://learn.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-configure-native-client-application
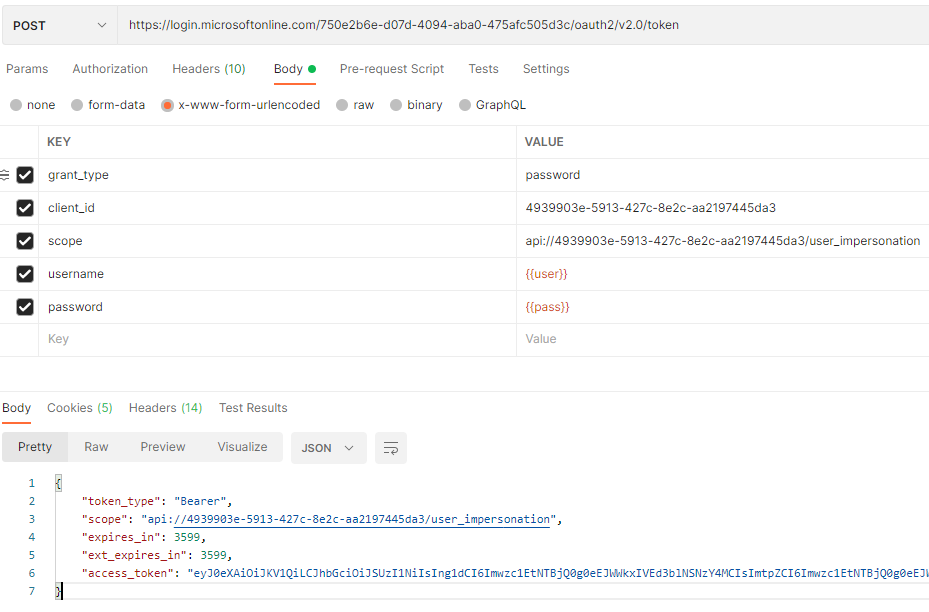
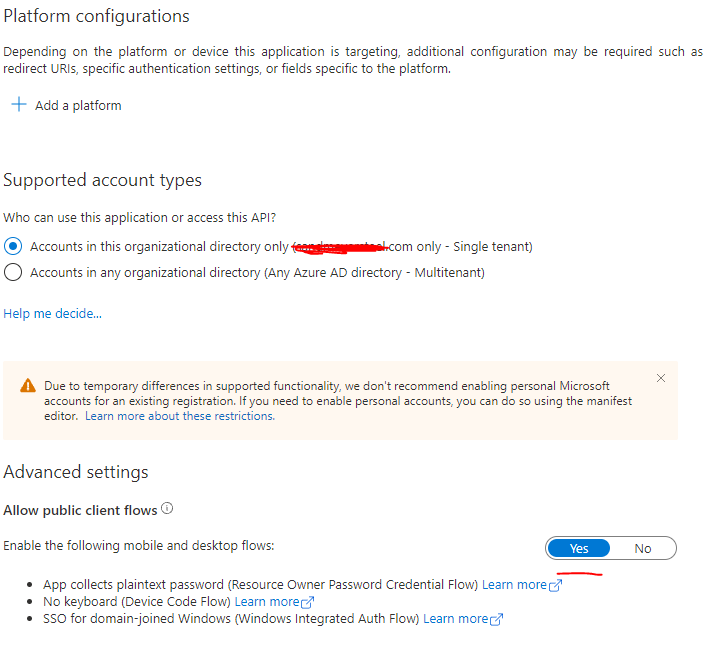
In addition to that, I could see you are using "Resource Owner Password Credentials (ROPC)" flow (grant_type=password) which is not recommends because in this flow user password sent in HTTP header which carries risks so try using more secure alternatives flows.
This ROPC flow requires a very high degree of trust in the application, and carries risks which are not present in other flows. You should only use this flow when other more secure flows can't be used.
Hope this helps.
------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.