Hello @P ,
Thanks for the question and using MS Q&A platform.
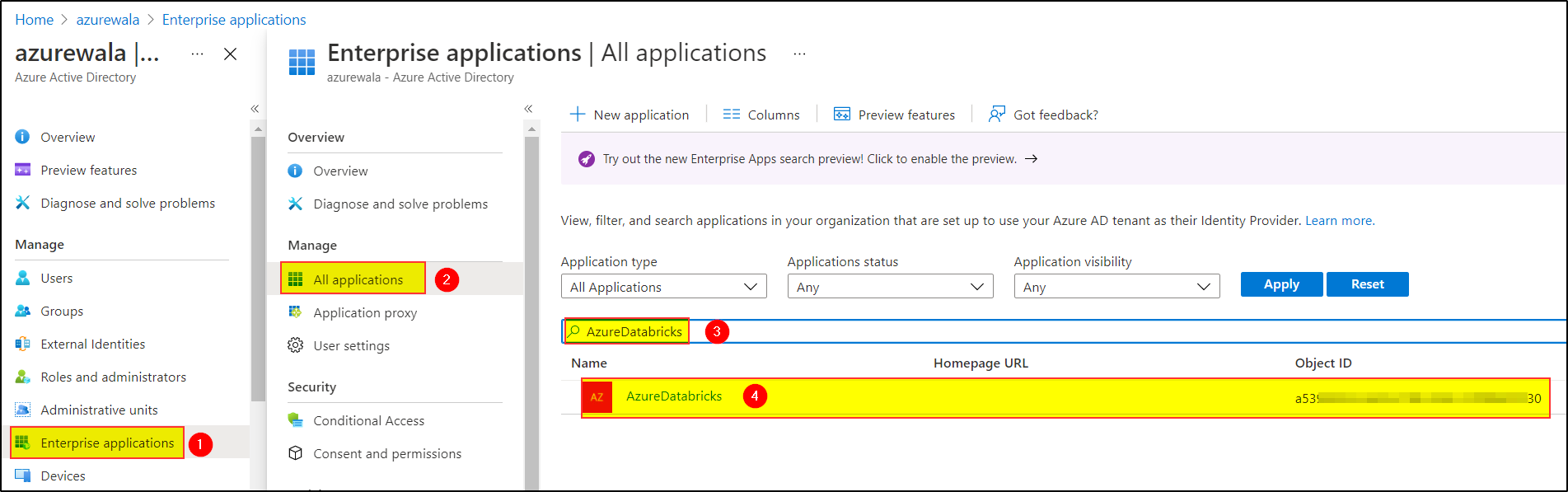
By default, Azure Databricks have an associated Enterprise application called "AzureDatabricks".
For more details, refer to Enable customer-managed keys for managed services.
How to get the Azure Databricks application from Azure portal?
- In Azure Active Directory, select Enterprise Applications from the sidebar menu.
- Search for AzureDatabricks and click the Enterprise application in the results.
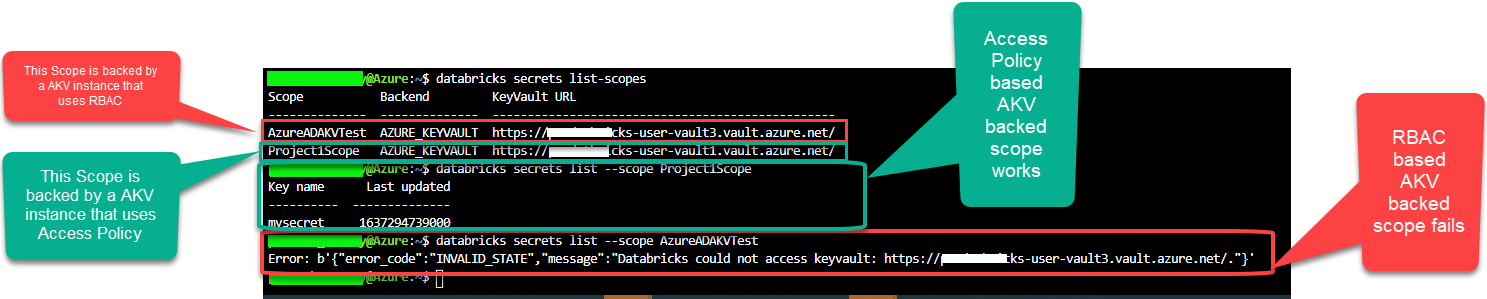
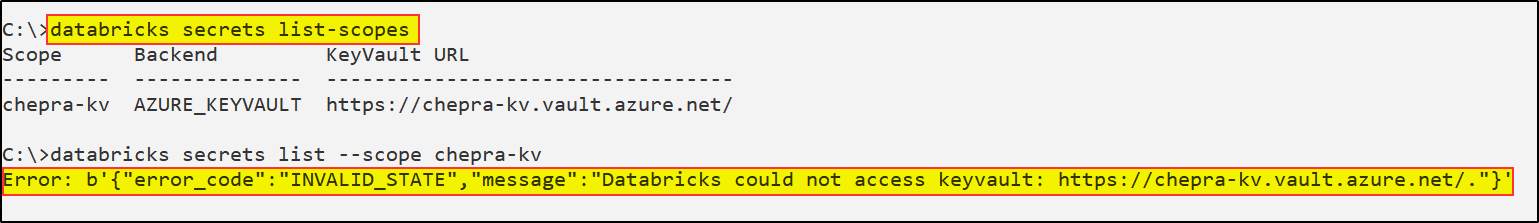
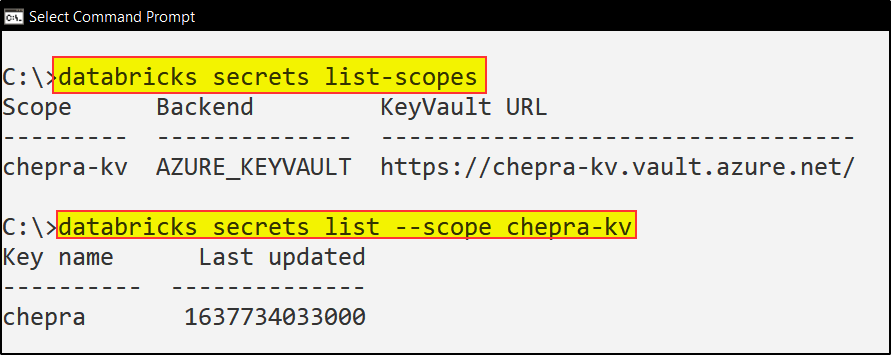
As per the repro, when I used Azure role-based access control in Azure Key Vault noticed the same error as shown above:
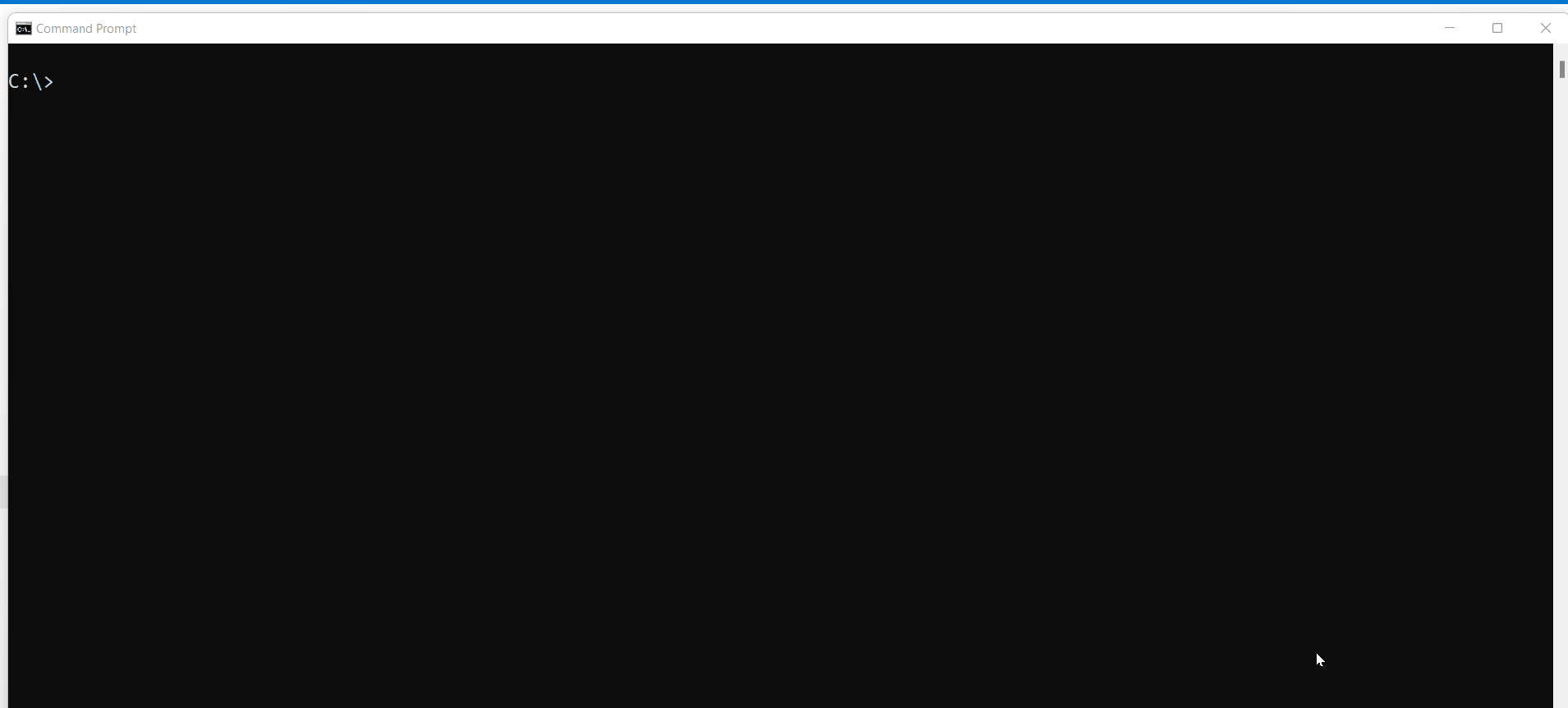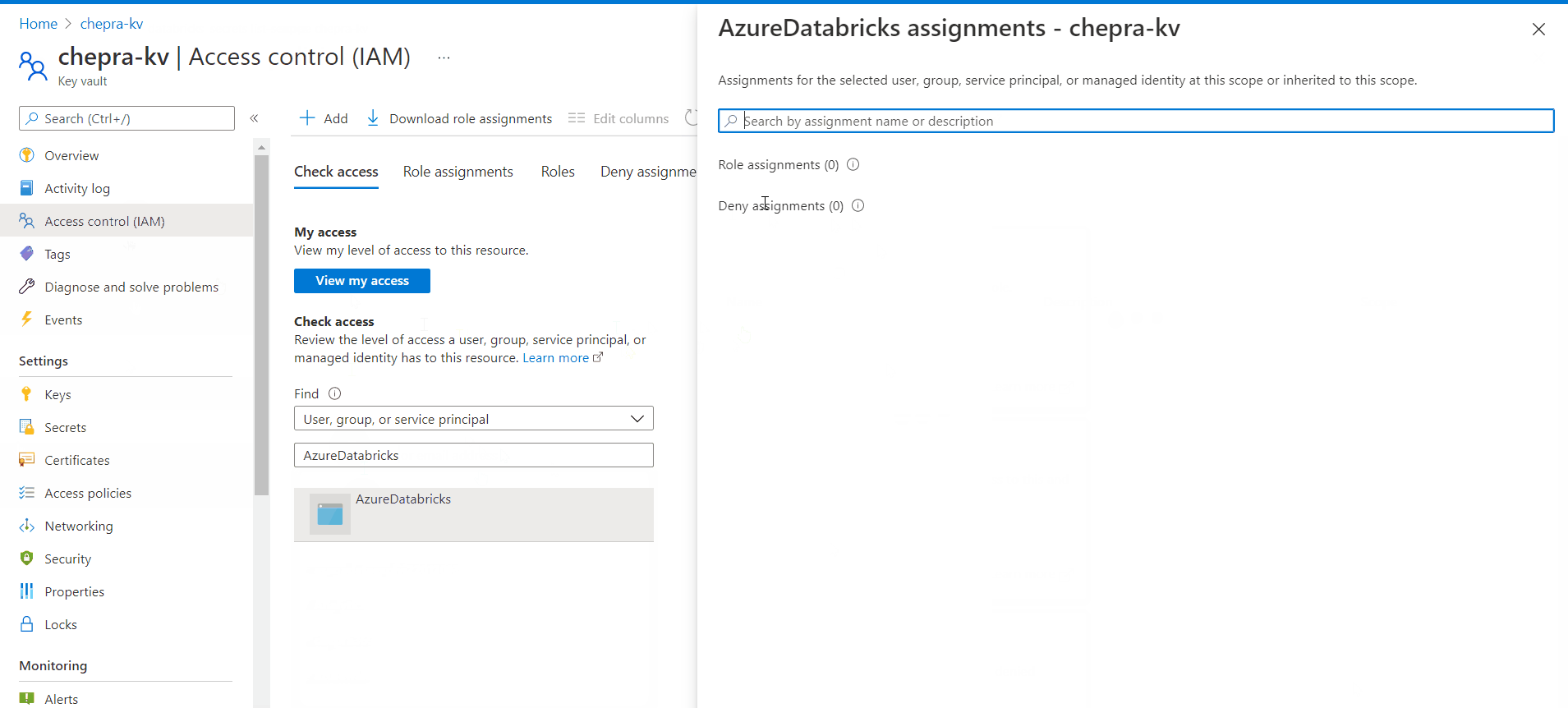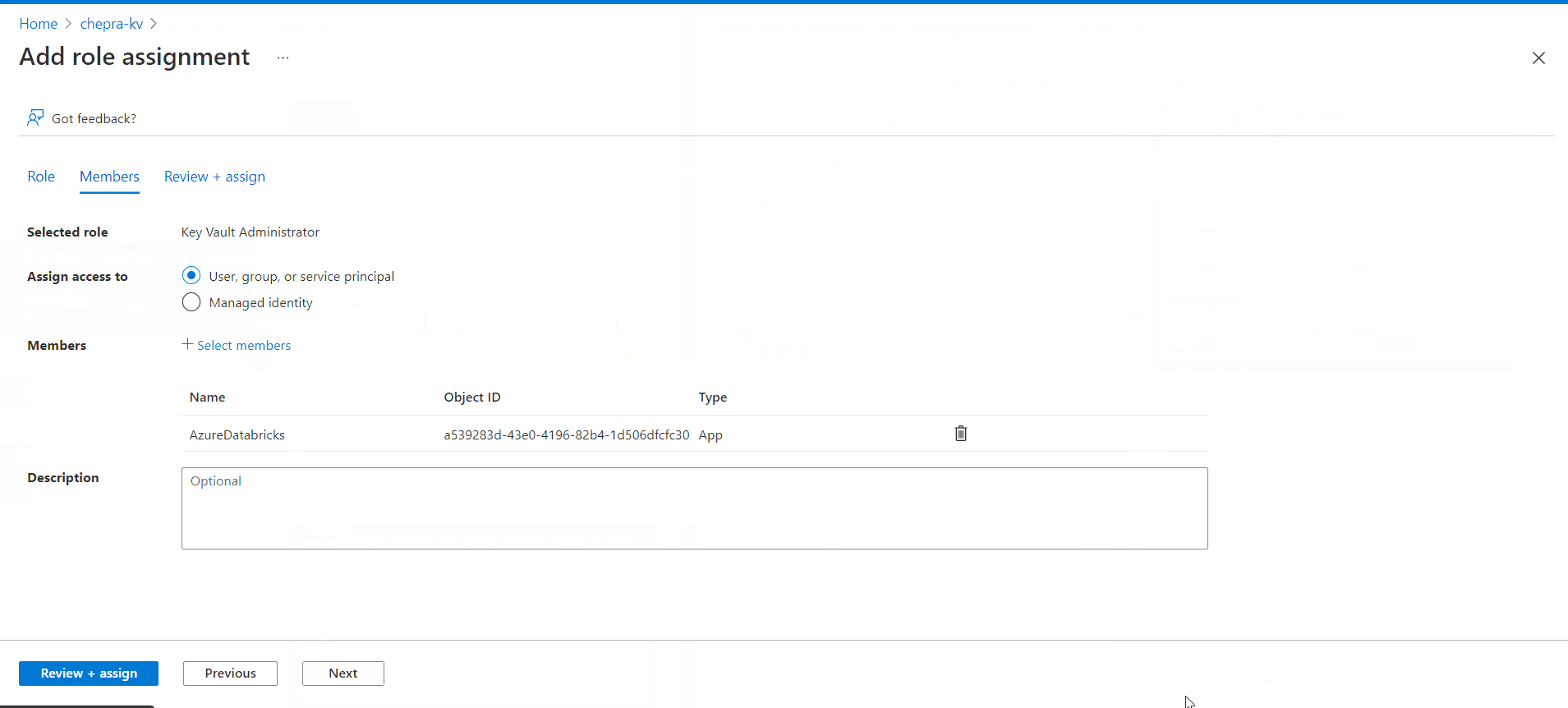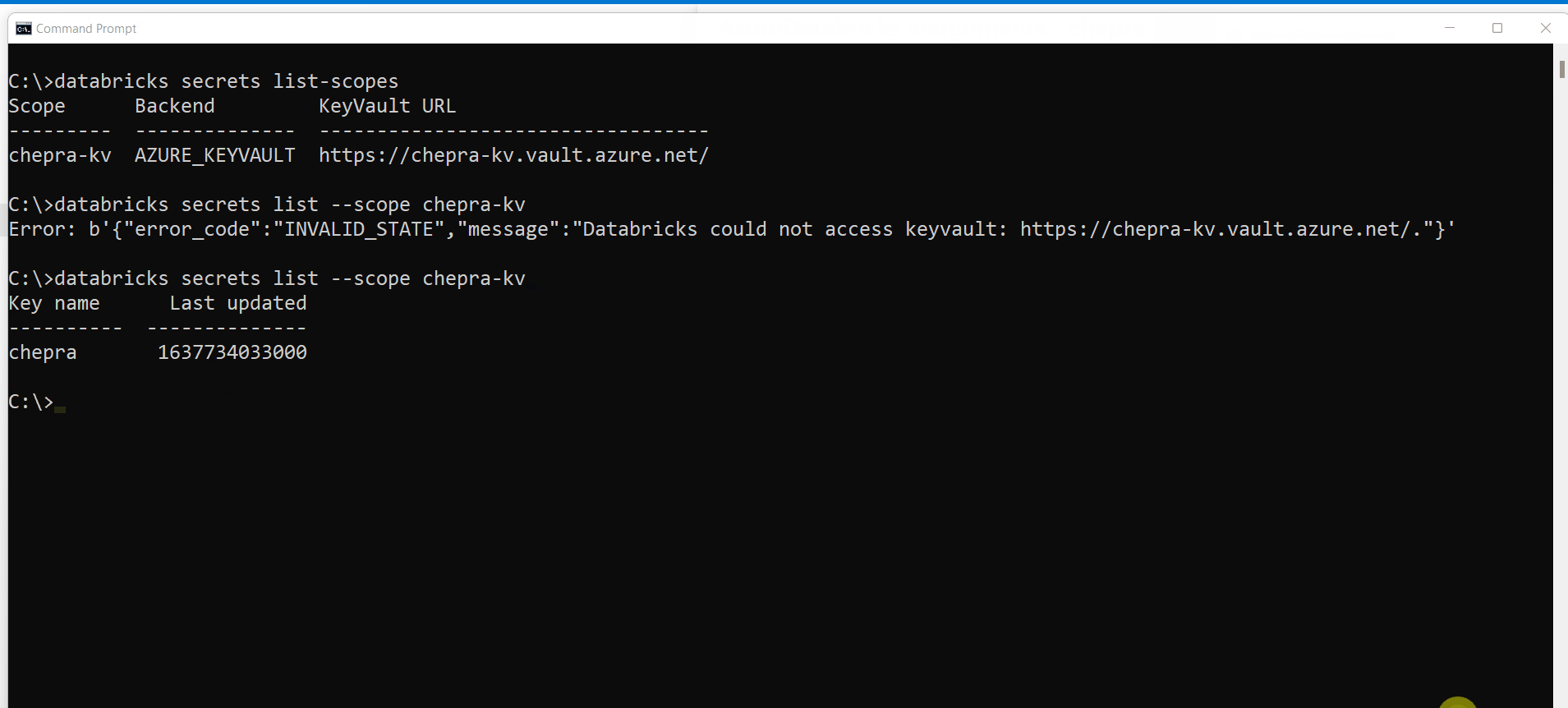
To resolve this issue, you need to Add role assignment to the
AzureDatabricksapplication with roleKey Vault Administrator.
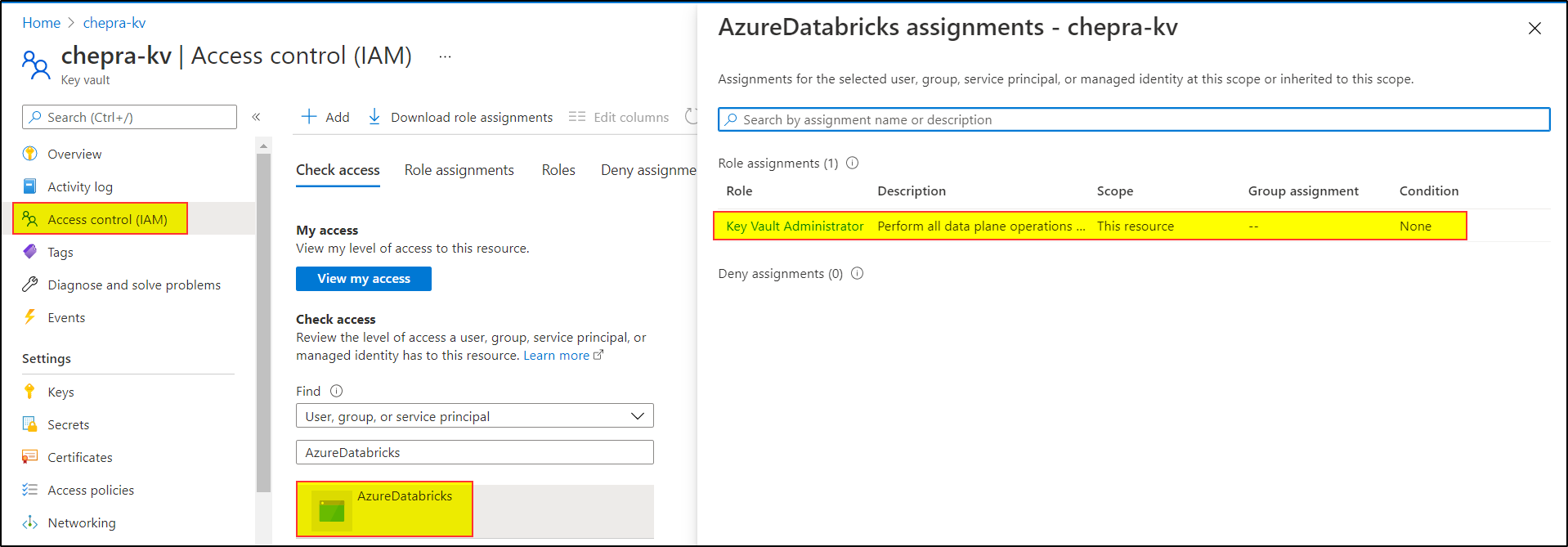
After adding the
Key Vault Administratorrole to theAzureDatabricksapplication able to list the scopes inside the key vault.
Hope this will help. Please let us know if any further queries.
------------------------------
- Please don't forget to click on
 or upvote
or upvote  button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how
button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how - Want a reminder to come back and check responses? Here is how to subscribe to a notification
- If you are interested in joining the VM program and help shape the future of Q&A: Here is how you can be part of Q&A Volunteer Moderators