Thank you for the described steps and screen shots above. But at first this still did not work for a DC in Windows Server 2019.
I downloaded the admx for both Win10 and Win11 to Windows Server 2019
I ran the MSI.
It extracted/placed the files into C:\Program Files (x86)\Microsoft Group Policy\ under a folder with the policy name
I copied those files and folders to a new folder in central store under \PolicyDefinitions-Win1021h1
(and also to a new folder \PolicyDefinitions-Win11-21h1 for that set)
I run gpupdate /force
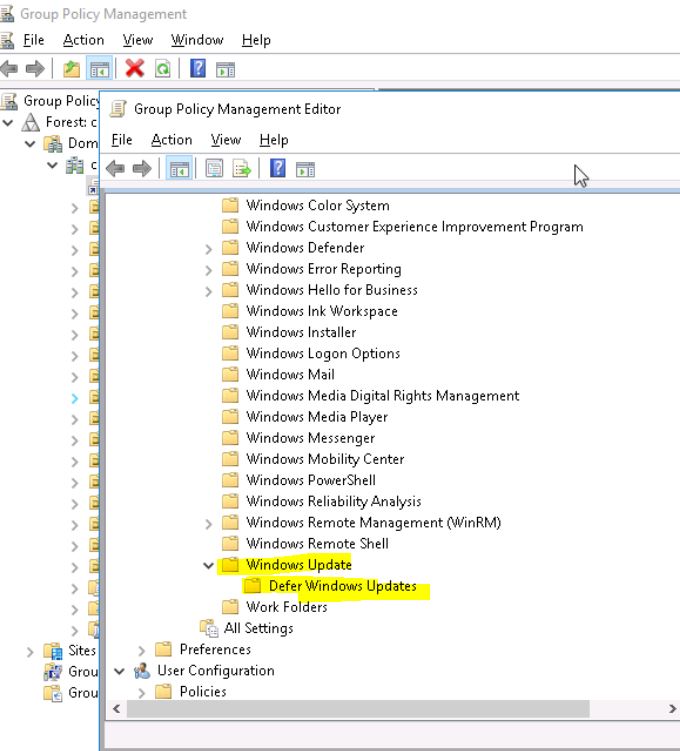
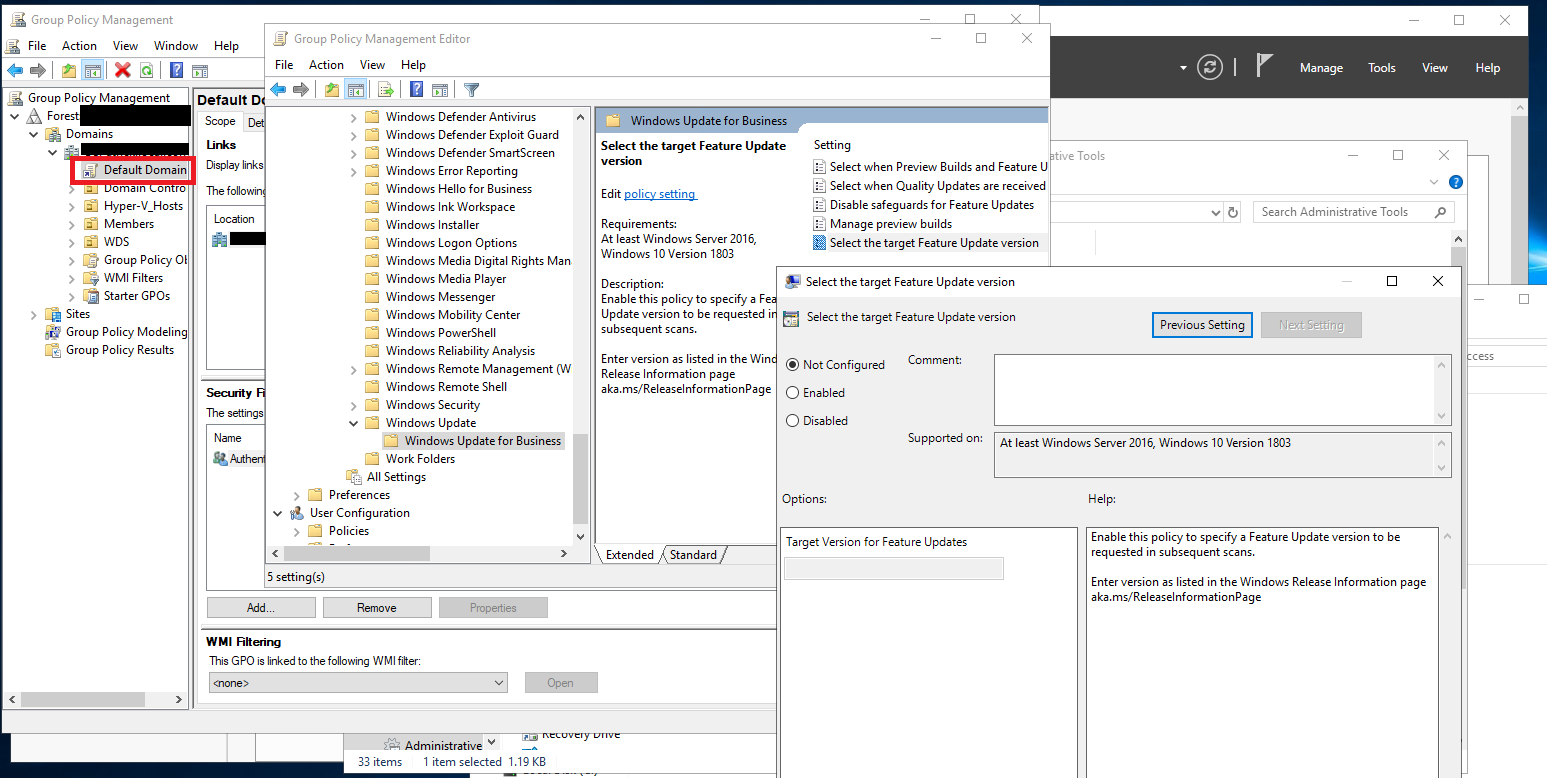
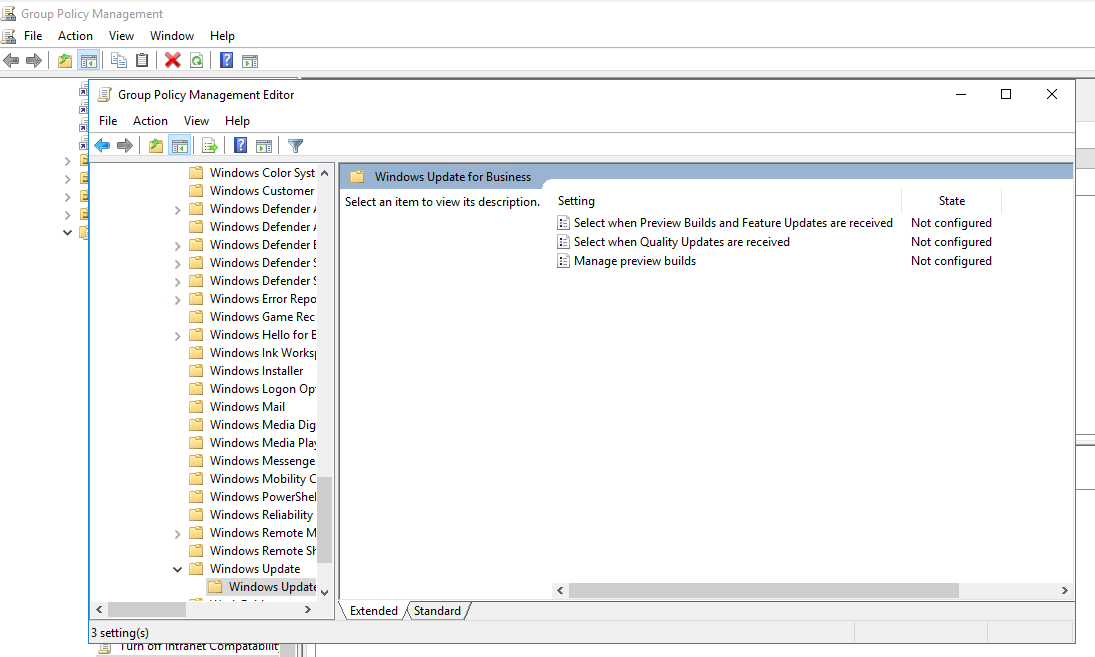
I open Group Policy Manager
I edit the Default Domain Policy object.
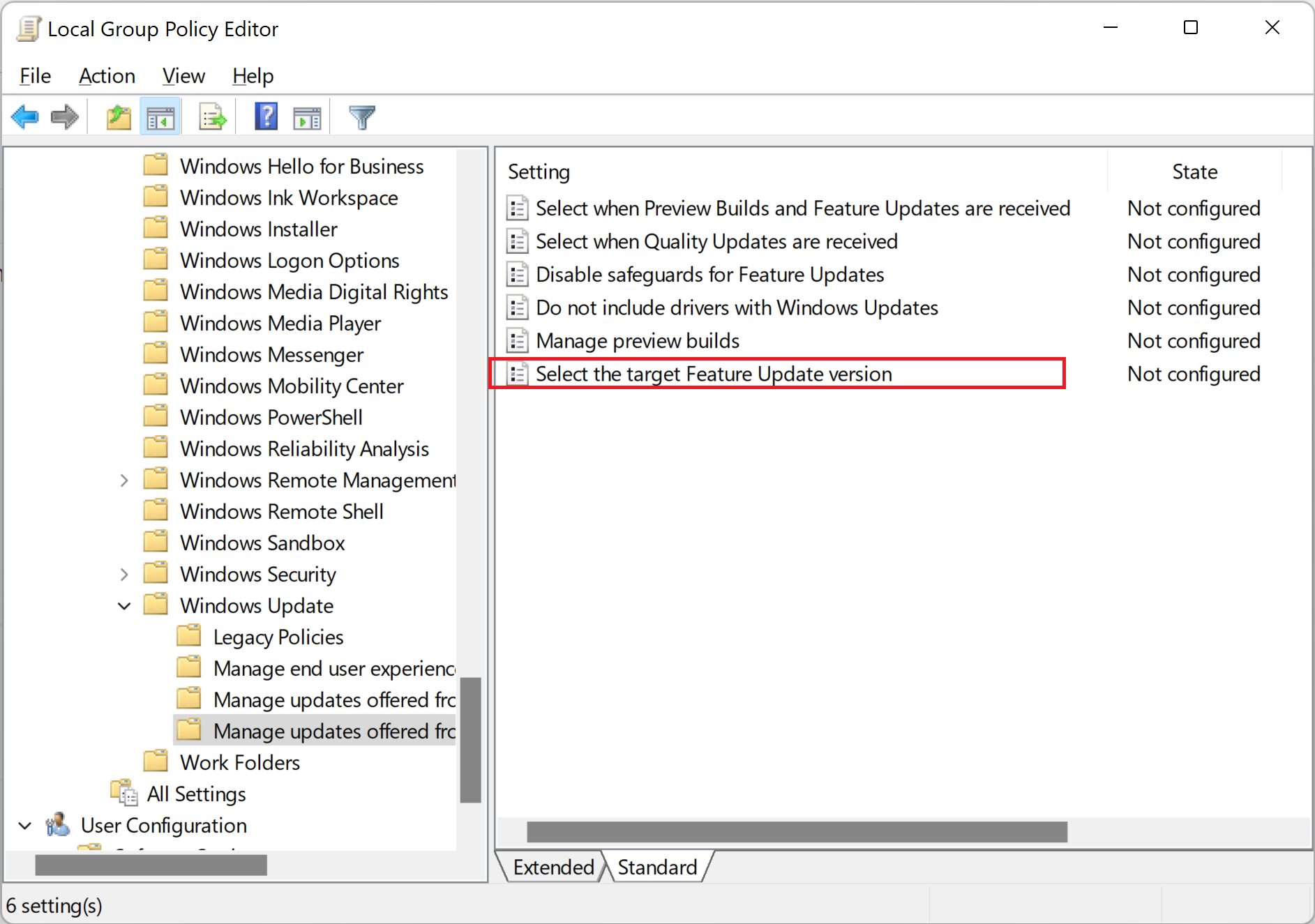
I browse down to Computer Configuration > Policies > Admin Templates > Windows Components > Windows Update >Windows Update for Business
There was NO entry "Select the target feature update version" under that key.
The admx files have to be copied into the existing "PolicyDefinitions" folder, over-writing whatever previous ones you have in there (back them up first!). And do it by selecting the files, and copy/paste. Do not over-write the entire folder (such as en-us) because you could be wiping out files you need - not every admx update contains all the same files. It may have 212, but your en-us folder might have 221. Those other 10 extra files you have may still be very important to you, so don't destroy them by just overwriting the folder itself. Same thing for the base folder of PolicyDefinitions - copy/paste the files. You likely have other ones in there you do not want to lose.. so don't rename/delete the PolicyDefinitions folder itself.
Then run gpupdate and then open the GP editor and the setting should appear.
But this approach by Microsoft is still stupid. It should not be so broken, and should not require such extra manual processes. This should be delivered to servers as an automatic update that provides a one-click setting to push into GPO's to disable access for end users to run major version upgrades. Sys Admins need time to test, test, and test again before such major things can roll out. To just give it to all end users in corporate networks by default is outrageously dangerous.