Same here (on B2C), followed the exact same procedure but "roles" does not appear in our tokens
app roles in client credentials scope in azure b2c for s2s
Why in azure b2c I can't seem to create custom scopes for service-to-service communication?
For example I want to have api1 request token via client creds for api2 with scope orders:read. However it seems I'm unable to do that thru azure b2c. (Delegated permissions are avail, but not application ones)
Why?
Microsoft Security | Microsoft Entra | Microsoft Entra External ID
3 answers
Sort by: Most helpful
-
-
Shweta Mathur 30,296 Reputation points Microsoft Employee Moderator
2022-03-03T12:37:53.727+00:00 Hi @Zachar Kapustin ,
Thanks for reaching out.
I understand that you are looking to implement service-to-service communication in Azure AD B2C but unable to create custom scopes for Web API.
For daemon/service based applications you can authenticate and get tokens by using the application's identity (rather than a user's delegated identity) and by using the client credentials flow.
Although Client credentials grant flow is not currently directly supported by the Azure AD B2C as mentioned here, You can set up client credentials flow using Azure AD and the Microsoft identity platform endpoint for an application in your Azure AD B2C tenant.
As mentioned , Custom scopes create only delegated permissions which cannot be added as application permissions.
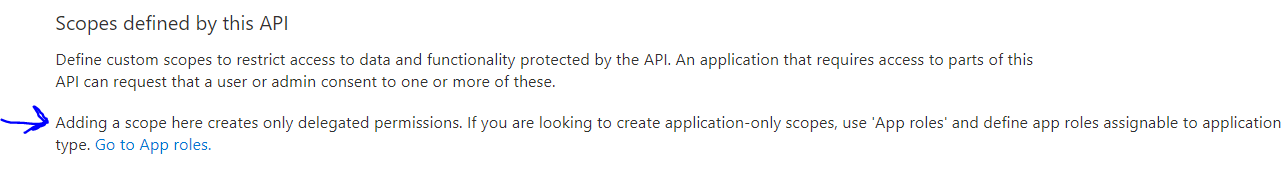
To add scopes as application permissions, you need to create the appRole of the server application(api2), and then grant that role as an application permission to the client application(api1) to access the application permissions.
To set the application permission, you need to assign app role to the application.
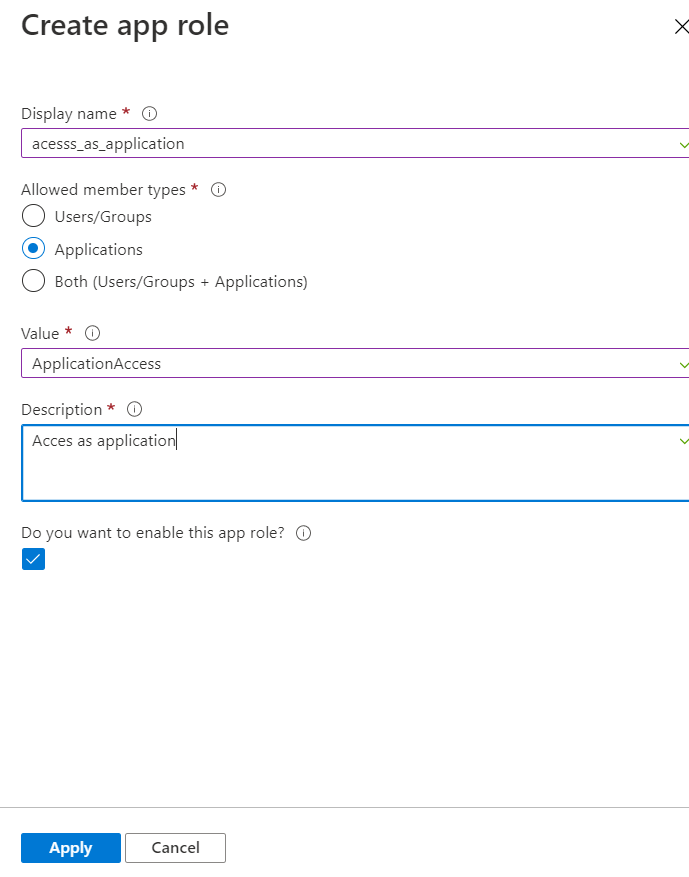
There might be chance you are not able to see App roles in the B2C blade and client credential is not supported in B2C.
To add App roles in your Web API (api2), you can update the value of app roles in manifest as:
"appRoles": [ { "allowedMemberTypes": [ "Application" ], "description": "Access as application", "displayName": "access_as_application", "id": "c0999c9d-bf5f-4202-8b1c-f660baf4f78b", "isEnabled": true, "lang": null, "origin": "Application", "value": "access_as_application" } ],Also, you need to expose the api of the server application protected by Azure as:
Azure portal>App registrations>Expose an API> set the application id URI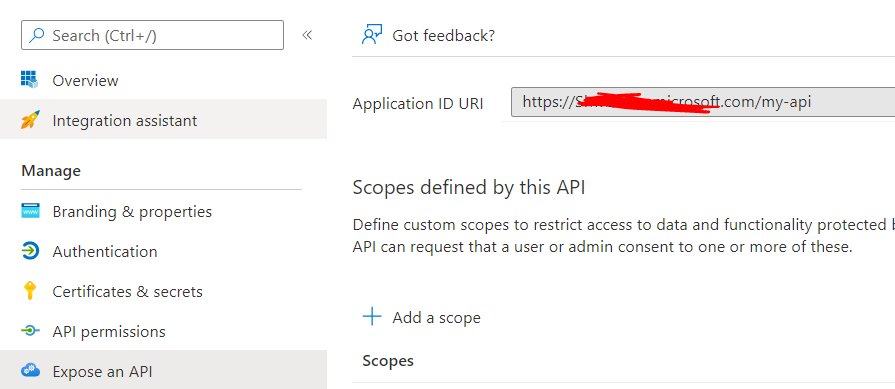
Next, go to client application(api1)>API permissions>Add a permission>My APIs>your api application(api2) and grant admin consent to that permission.
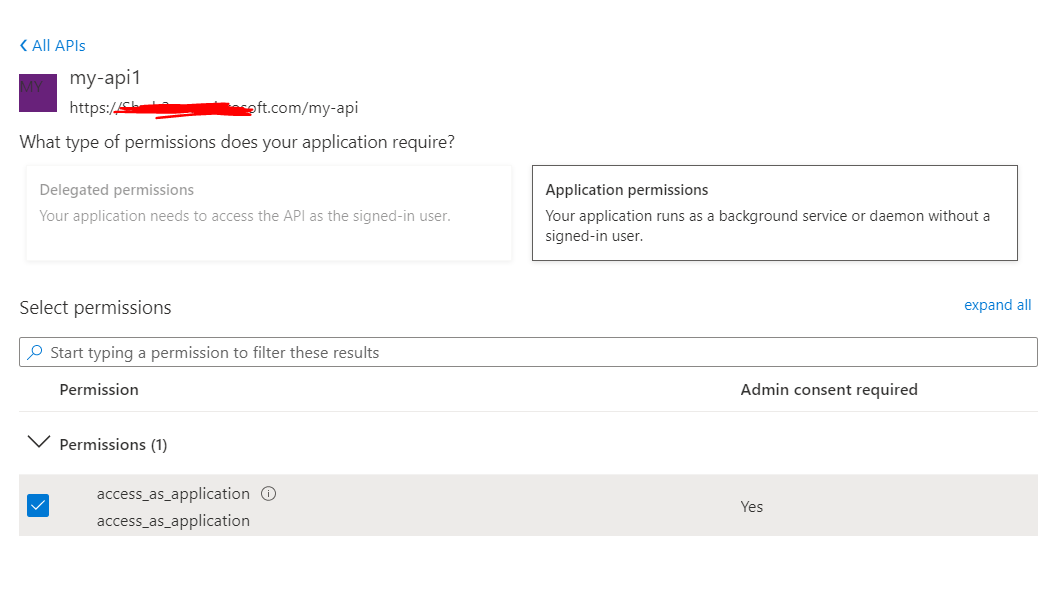
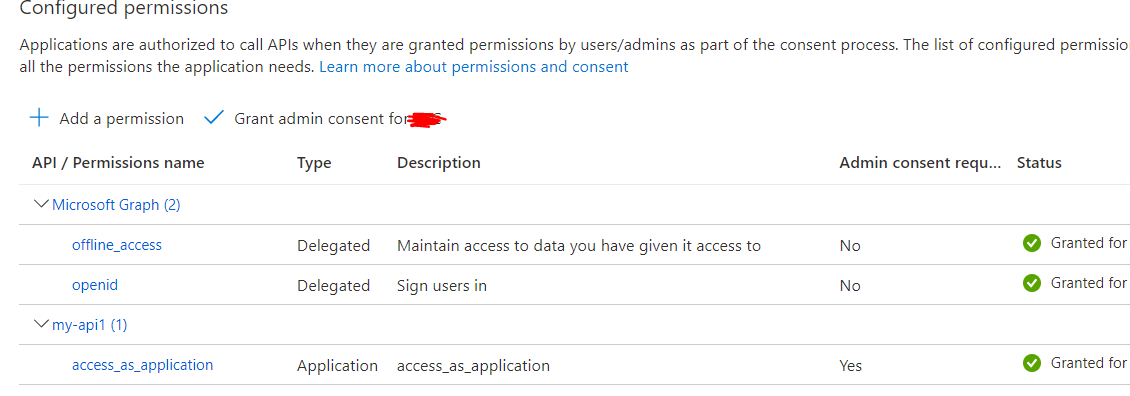
Now get the access token with client credential flow using token endpoint to call protected webAPI(api2)
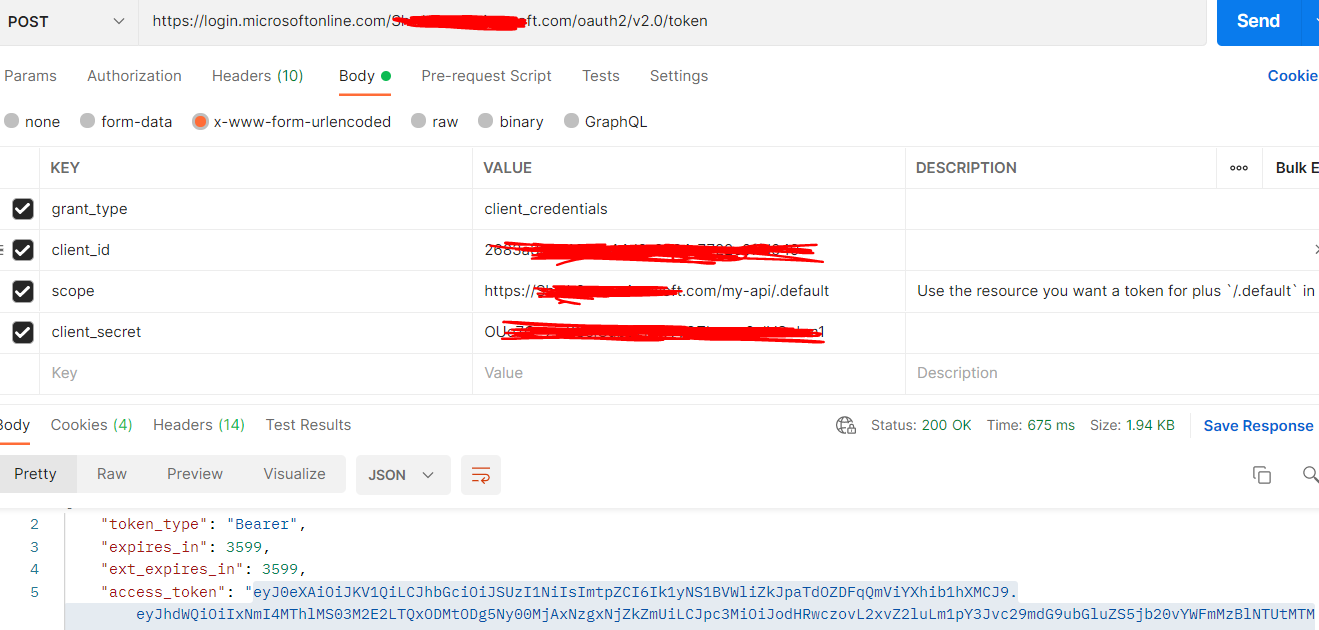
Hope this will help.
Thanks,
Shweta--------------------------------------
Please remember to "Accept Answer" if answer helped you.
-
Kenneth Egholm 1 Reputation point
2022-10-05T12:22:35.713+00:00 Hi.
I have this exact same setup, however I am struggling getting the "appRoles" out in the token.
As an experiment I created a role in the client application and that is the only one that is carried over to the token.
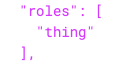
The roles that comes from the protected application isn't there.
(They are Granted admin consent)