Hi @Jacek B ,
Thanks for reaching out.
I understand you are trying to access web applications for personal Microsoft accounts only and getting error while access the application as mentioned in stack overflow.
You don't need to create another instance if you need to sign in with Microsoft users already added in your Azure AD tenant.
All the users are stored in same Azure AD tenant, but if you want your application to access by personal Microsoft accounts only. You need to set the audience of your application as PersonalMicrosoftAccount while registering the application in Azure AD tenant. This won't allow any other users apart from Microsoft Accounts users to sign into your application.
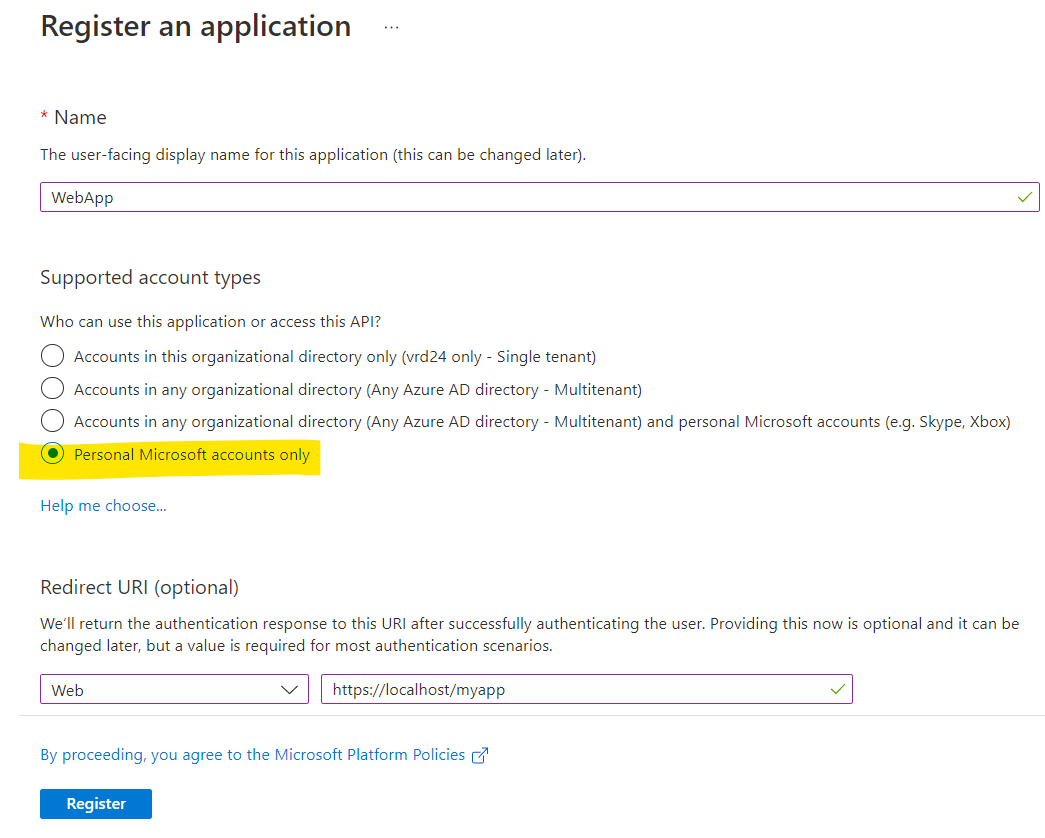
Now, to authenticate the Personal Microsoft accounts users and to get the token, you need to use the endpoints in your application's code depend on the application's type and account types it should support. In this case, https://login.microsoftonline.com/{tenant}/oauth2/v2.0/token endpoint where {tenant} need to replace with consumers for Microsoft accounts only.
Server will send the user to redirect URL once the app has been successfully authorized and granted an authorization code or access token.
Hope this will help. If you have any further questions on that, please let us know.
Thanks,
Shweta
------------------------------
Please remember to "Accept Answer" if answer helped you.
