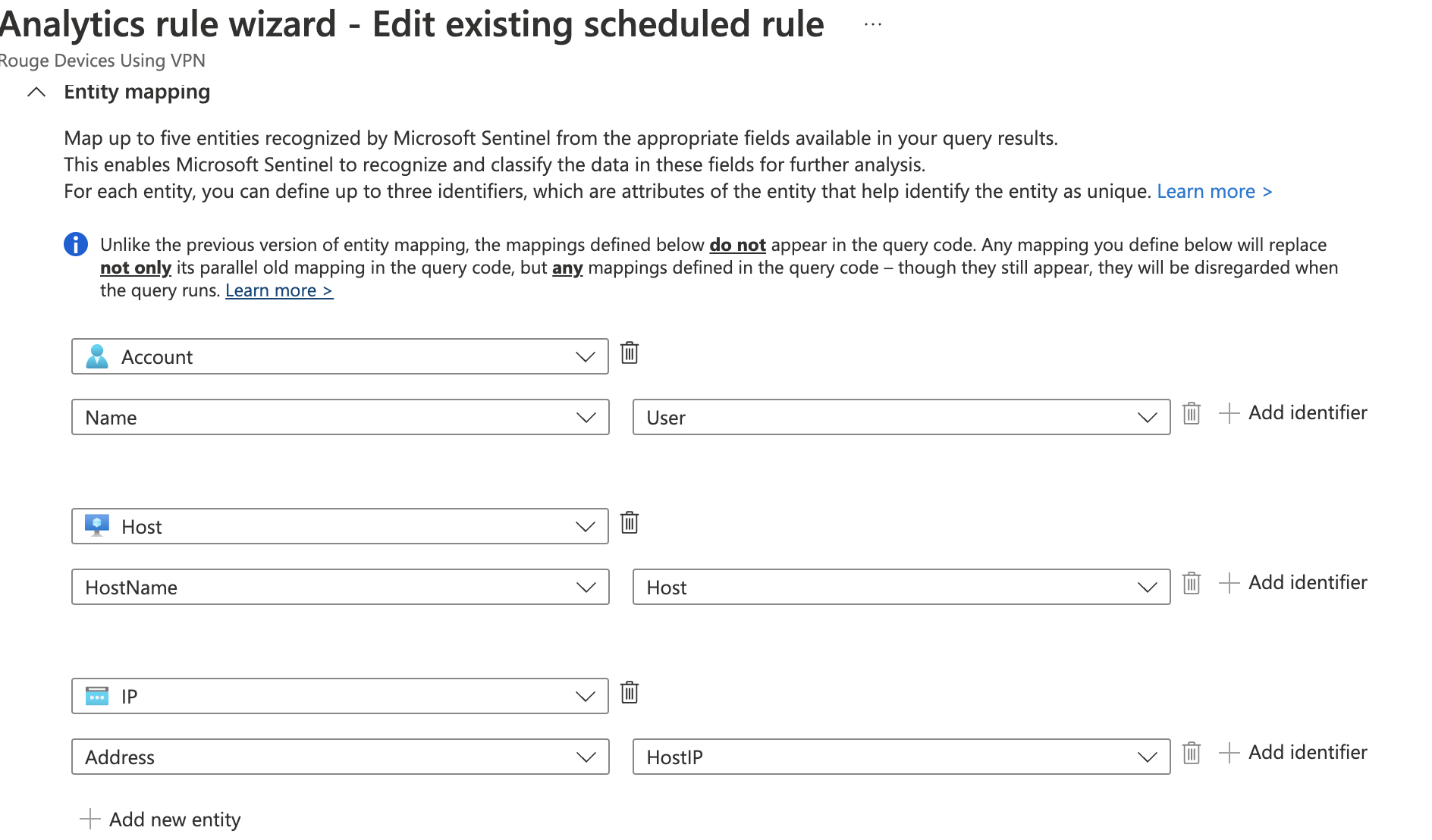
Hi Karthick,
Those entities likely won't map the way you'd like given your analytic rule.
However if you play with your kql you could create a concatenated value and map that to an identifier. (I use strcat frequently)
The other option is to add a log analytics query to your logic app and pull out the 2 fields that way, but I'd do it as in the first suggestion.
Hope that helps.
reference:
strcatfunction


 or upvote
or upvote  button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is
button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is