Hello @ADM-Griffin2, Jay ,
Welcome to the MS Q&A forum.
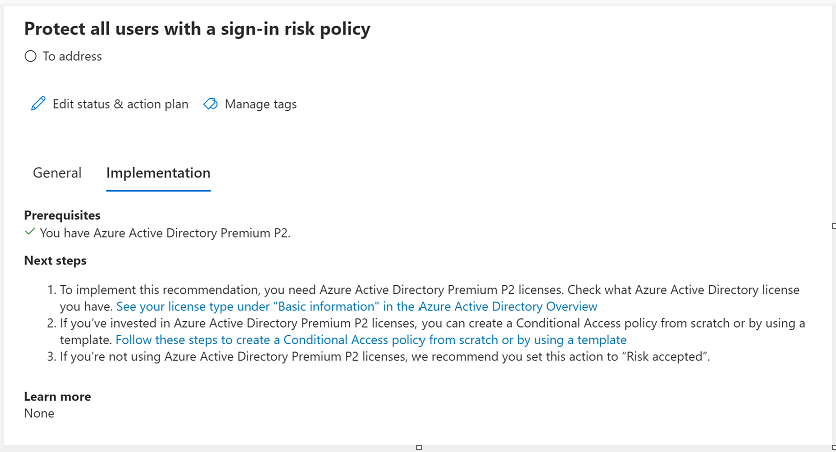
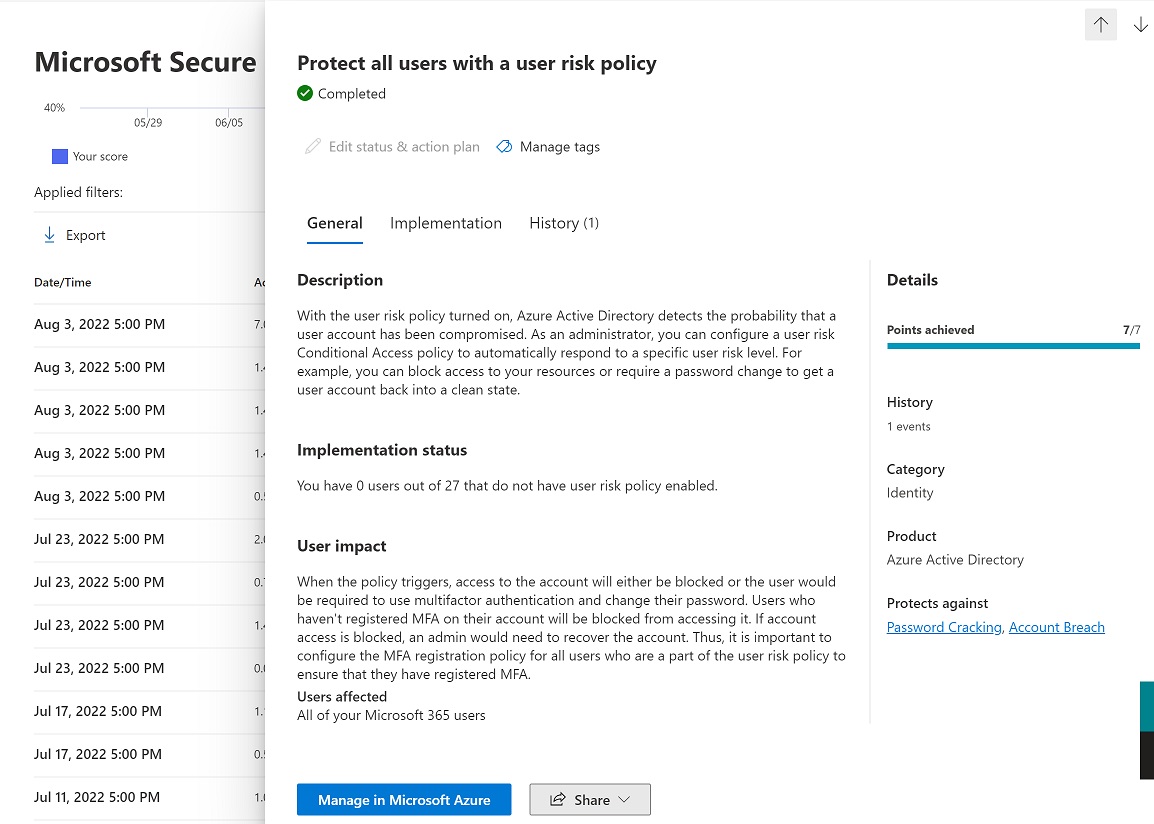
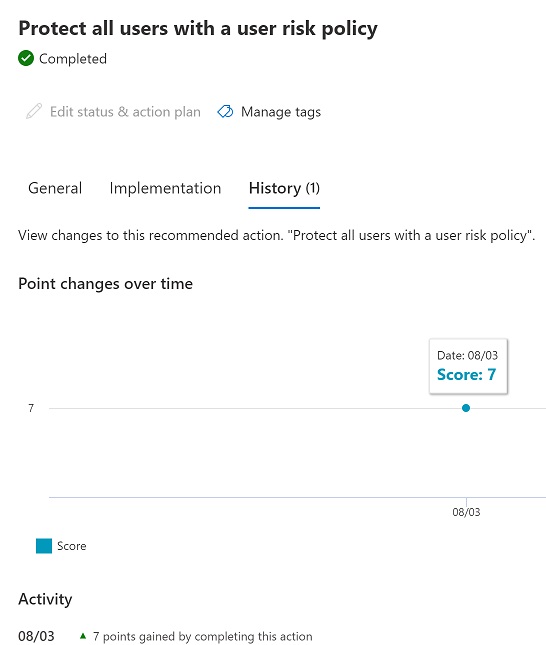
Could you kindly share the exact message referring to this event from the overview page and history page? To find more detailed information, navigate over to the Microsoft 365 Defender portal. You can easily see all the changes to your secure score by reviewing the in-depth changes on the history tab.
Example below:
In addition, check if you have any related change events in the Audit logs from the Overview Page by using filter "Service => Identity Protection" and in the "Conditional Access | Audit logs".
Hope above steps should help you resolve your concern.
--------------------------------------------------------
Let us know if you need additional assistance. If the answer was helpful, please accept it and complete the quality survey so that others can find a solution.