Implementing an OCSP responder: Part II - Preparing Certificate Authorities
Chris here again. In Part I we covered some of the basics and background information on the reason for the OCSP Responder and a basic understanding of how the OCSP Responder functions. So now we look towards implementing the OCSP Responder. However, before we move forward with the Install of the OCSP Responder we must first configure the CA to support OCSP for revocation status checking.
As discussed in the first part of this series, the OCSP Responder provides revocation information to clients or application requesting revocation status for a specific certificate. In order for this to be accomplished there are certain prerequisites that need to be in place.
Some of the prerequisites are different depending on which version of the CA you are using, and whether you are using a Standalone or Enterprise CA.
Configuring AIA Extension to support OCSP
To advertise that revocation status information for a particular CA can be obtained via OCSP, the CA must include a pointer to the OCSP Responder in the certificate. This is done by adding an OCSP URI to the AIA extension of the certificate.
Although this is mentioned as a prerequisite, you may want to do this after the OCSP Responder is configured. The reason being is that if you issue certificates before the Responder is available you will create unnecessary traffic to the soon to be OCSP location.
1. Open the Certification Authority Snap-in on the CA, as an Enterprise Administrator.
2. Right click on the CA name, and select Properties
3. Click on the Extension Tab. From the Select Extension drop down Box, select Authority Information Access (AIA) .
4. Then click on the Add… button to add the OCSP location
5. Type the location for the OCSP responder. This will typically be:
https://<fqdn of the ocsp responder>/ocsp
6. Then click OK.
7. Check the Checkbox for Include in the online certificate status protocol (OCSP) extension.
8. And click OK, to close the CA Properties.
Preparing Windows Server 2003 Standalone CA for use with OCSP Responder
OCSP Signing Certificates
In order to be able to deploy the OCSP Signing Certificate used by the OCSP Responder, there are some configuration changes that need to be made on a Windows Server 2003 CA.
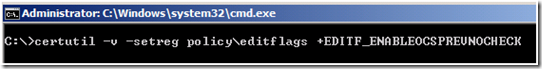
A signing certificate includes the id-pkix-ocsp-nocheck extension. This extension informs the OCSP client that the OCSP signing certificate should not be checked for revocation during the lifetime of the certificate. The OCSP Signing certificate should therefore have a short lifetime. By default, a Windows Server 2003 CA will ignore the id-pkix-ocsp-nocheck extension in a certificate request and will not include that extension in the issued certificate. To change this behavior, you must allow custom extensions to be used in certificate requests.
To enable support for custom extensions, run the following command on the CA:
The extension object ID (OID) for the id-pkix-ocsp-nocheck extension is1.3.6.1.5.5.7.48.1.5. The above command instructs the CA to include that extension in the issued certificate if it is found in the request.
Preparing Windows Server 2003 Enterprise CA for use with OCSP Responder
If you plan on using a Windows Server 2003 Enterprise CA to issue the OCSP Signing Certificate you will need to follow the instructions outlined in the previous section for enabling the use of custom extensions.
If you plan on using a certificate template on the Windows Server 2003 Enterprise CA, you must have at least 1 Windows Server 2008 Enterprise CA in the environment. The reason is you will be duplicating the Version 3 OCSP Signing Template on the Windows Server 2008 CA for use with the Windows Server 2003 CA. Both the Windows Server 2003 and Windows Server 2008 CA, must be running Enterprise Edition. This is due to the fact that only Version 1 templates are supported in the Standard Editions of the Server OS.
Duplicating the OCSP Signing Template
1. Logon to a Windows Server 2008 Enterprise CA, with an account that is a member of the Enterprise Admins group.
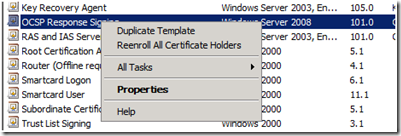
2. Open up the Certificate Template management console (certtmpl.msc).
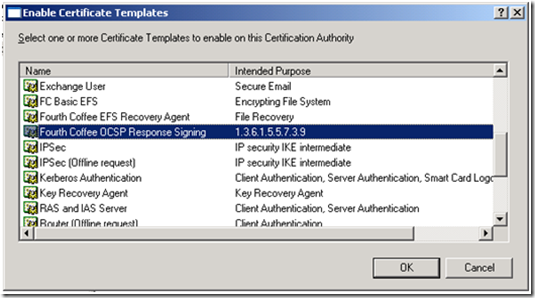
3. Right click on OCSP Response Signing Template, and select Duplicate Template from the context menu, as illustrated below:
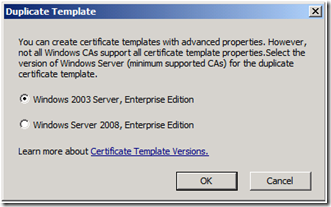
4. From the Duplicate Template dialog box, select Windows Server 2003 Server, Enterprise Edition, and click OK. Selecting Windows Server 2003 Server, Enterprise Edition, creates a Version 2 Template instead of a Version 3 Template.
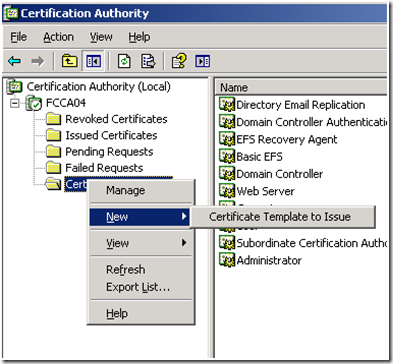
6. Log on to the Windows Server 2003 CA, and open the Certificate Authority Snapin (Certsrv.msc), and right click on Certificate Templates, and select New, then Certificate Template to Issue from the context menu.
7. Select the Duplicated Template, and click on OK.
Preparing Windows Server 2008 Standalone CA for use with OCSP Responder
In the previous section on preparing the Windows Server 2003 Standalone CA, we had to enable the CA to accept custom extensions sent in the request. This was to allow us to request a certificate with the id-pkix-ocsp-nocheck extension. Windows Server 2008 natively supports the id-pkix-ocsp-nocheck extension, so there is no need to allow custom extensions. On the Windows Server 2008 Enterprise CA there is no action necessary to support the id-pkix-ocsp-nocheck extension. However, on the Windows Server 2008 Standalone CA, we need to run the following command to add support for the id-pkix-ocsp-nocheck extension:
Preparing Windows Server 2008 Enterprise CA for use with OCSP Responder
The only preparation required for the Windows Server 2008 Enterprise CA, is to give permissions to the templates to the OCSP Servers, and to make the template available for issuance.
1. Open the Certificate Template Management console (certtmpl.msc)
2. Locate the OCSP Certificate Template, Right-click, and select Properties
3. On the Security Tab, add the hostname of the soon to be OCSP Server, and give the server Read and Enroll permissions to the template. Note: A more scalable solution, as seen in the illustration below, is to create a security group, assign permissions to the security group, and add any OCSP servers to the Security Group.
4. Go back to the Certification Authority management console, Right-click on the Certificates Templates node, and from the context menu, select New and then "Certificate Template to issue.
5. Select the OCSP Response Signing Template, and select OK.
Conclusion
You should now have your Certificate Authorities configured to support the OCSP Responder as a source of revocation status. In the next part of this series I will cover installing and the configuring the OCSP Responder to support Enterprise CAs.
Implementing an OCSP responder: Part I Introducing OCSP
Implementing an OCSP responder: Part II Preparing Certificate Authorities
Implementing an OCSP responder: Part III Configuring OCSP for use with Enterprise CAs
Implementing an OCSP responder: Part IV Configuring OCSP for use with Standalone CAs
Implementing an OCSP Responder: Part V High Availability
Implementing an OCSP Responder: Part VI Configuring Custom OCSP URIs via Group Policy
- Chris Delay
![clip_image002[4] clip_image002[4]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/ImplementinganOCSPresponderPartIIPrepari_93ED/clip_image002%5B4%5D_thumb.jpg)
![clip_image002[6] clip_image002[6]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/ImplementinganOCSPresponderPartIIPrepari_93ED/clip_image002%5B6%5D_thumb.jpg)
![clip_image002[8] clip_image002[8]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/ImplementinganOCSPresponderPartIIPrepari_93ED/clip_image002%5B8%5D_thumb.jpg)

![clip_image002[11] clip_image002[11]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/ImplementinganOCSPresponderPartIIPrepari_93ED/clip_image002%5B11%5D_thumb.jpg)
![clip_image002[13] clip_image002[13]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/ImplementinganOCSPresponderPartIIPrepari_93ED/clip_image002%5B13%5D_thumb.jpg)