Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Get started with Azure App Service by deploying an app to the cloud using an Azure Resource Manager template (ARM template) and Azure CLI in Cloud Shell. A Resource Manager template is a JavaScript Object Notation (JSON) file that defines the infrastructure and configuration for your project. You incur no costs to complete this quickstart because you use a free App Service tier.
To complete this quickstart, you need an Azure account with an active subscription. If you don't have an Azure account, you can create one for free.
Skip to the end
If you're familiar with using ARM templates, you can skip to the end by selecting this

In the Azure portal, select Create new to create a new Resource Group and then select the Review + create button to deploy the app.
Get started with Azure App Service by deploying an app to the cloud using an Azure Resource Manager template (ARM template) and Azure CLI in Cloud Shell. A Resource Manager template is a JavaScript Object Notation (JSON) file that defines the infrastructure and configuration for your project. You incur no costs to complete this quickstart because you use a free App Service tier.
To complete this quickstart, you need an Azure account with an active subscription. If you don't have an Azure account, you can create one for free.
Skip to the end
If you're familiar with using ARM templates, you can skip to the end by selecting this

In the Azure portal, select Create new to create a new Resource Group and then select the Review + create button to deploy the app.
Get started with Azure App Service by deploying an app to the cloud using an Azure Resource Manager template (ARM template) and Azure CLI in Cloud Shell. A Resource Manager template is a JavaScript Object Notation (JSON) file that defines the infrastructure and configuration for your project. A premium plan is needed to deploy a Windows container app. See the App Service pricing page for pricing details.
Skip to the end
If you're familiar with using ARM templates, you can skip to the end by selecting this

In the Azure portal, select Create new to create a new Resource Group and then select the Review + create button to deploy the app.
Review the template
The template used in this quickstart is from Azure Quickstart Templates. It deploys an App Service plan and an App Service app on Windows. It's compatible with .NET Core, .NET Framework, PHP, Node.js, and Static HTML apps. For Java, see Create Java app.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"metadata": {
"_generator": {
"name": "bicep",
"version": "0.25.53.49325",
"templateHash": "16144177164140676603"
}
},
"parameters": {
"webAppName": {
"type": "string",
"defaultValue": "[format('webApp-{0}', uniqueString(resourceGroup().id))]",
"minLength": 2,
"metadata": {
"description": "Web app name."
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "Location for all resources."
}
},
"sku": {
"type": "string",
"defaultValue": "F1",
"metadata": {
"description": "The SKU of App Service Plan."
}
},
"language": {
"type": "string",
"defaultValue": ".net",
"allowedValues": [
".net",
"php",
"node",
"html"
],
"metadata": {
"description": "The language stack of the app."
}
},
"helloWorld": {
"type": "bool",
"defaultValue": false,
"metadata": {
"description": "true = deploy a sample Hello World app."
}
},
"repoUrl": {
"type": "string",
"defaultValue": "",
"metadata": {
"description": "Optional Git Repo URL"
}
}
},
"variables": {
"appServicePlanPortalName": "[format('AppServicePlan-{0}', parameters('webAppName'))]",
"gitRepoReference": {
".net": "https://github.com/Azure-Samples/app-service-web-dotnet-get-started",
"node": "https://github.com/Azure-Samples/nodejs-docs-hello-world",
"php": "https://github.com/Azure-Samples/php-docs-hello-world",
"html": "https://github.com/Azure-Samples/html-docs-hello-world"
},
"gitRepoUrl": "[if(bool(parameters('helloWorld')), variables('gitRepoReference')[toLower(parameters('language'))], parameters('repoUrl'))]",
"configReference": {
".net": {
"comments": ".Net app. No additional configuration needed."
},
"html": {
"comments": "HTML app. No additional configuration needed."
},
"php": {
"phpVersion": "7.4"
},
"node": {
"appSettings": [
{
"name": "WEBSITE_NODE_DEFAULT_VERSION",
"value": "12.15.0"
}
]
}
}
},
"resources": [
{
"type": "Microsoft.Web/serverfarms",
"apiVersion": "2023-01-01",
"name": "[variables('appServicePlanPortalName')]",
"location": "[parameters('location')]",
"sku": {
"name": "[parameters('sku')]"
}
},
{
"type": "Microsoft.Web/sites",
"apiVersion": "2023-01-01",
"name": "[parameters('webAppName')]",
"location": "[parameters('location')]",
"identity": {
"type": "SystemAssigned"
},
"properties": {
"siteConfig": "[variables('configReference')[parameters('language')]]",
"serverFarmId": "[resourceId('Microsoft.Web/serverfarms', variables('appServicePlanPortalName'))]",
"httpsOnly": true
},
"dependsOn": [
"[resourceId('Microsoft.Web/serverfarms', variables('appServicePlanPortalName'))]"
]
},
{
"condition": "[contains(variables('gitRepoUrl'), 'http')]",
"type": "Microsoft.Web/sites/sourcecontrols",
"apiVersion": "2023-01-01",
"name": "[format('{0}/{1}', parameters('webAppName'), 'web')]",
"properties": {
"repoUrl": "[variables('gitRepoUrl')]",
"branch": "master",
"isManualIntegration": true
},
"dependsOn": [
"[resourceId('Microsoft.Web/sites', parameters('webAppName'))]"
]
}
]
}
Two Azure resources are defined in the template:
- Microsoft.Web/serverfarms: create an App Service plan.
- Microsoft.Web/sites: create an App Service app.
This template contains several parameters that are predefined for your convenience. See the table for parameter defaults and their descriptions:
| Parameters | Type | Default value | Description |
|---|---|---|---|
| webAppName | string | webApp-<uniqueString> |
App name based on a unique string value |
| appServicePlanName | string | webAppPlan-<uniqueString> |
App Service Plan name based on a unique string value |
| location | string | [resourceGroup().location] |
App region |
| sku | string | F1 |
Instance size (F1 = Free Tier) |
| language | string | .NET |
Programming language stack (.NET, php, node, html) |
| helloWorld | boolean | False |
True = Deploy "Hello World" app |
| repoUrl | string | |
External Git repo (optional) |
The template used in this quickstart is from Azure Quickstart Templates. It deploys an App Service plan and an App Service app on Linux. It's compatible with all supported programming languages on App Service.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"metadata": {
"_generator": {
"name": "bicep",
"version": "0.5.6.12127",
"templateHash": "10602523904429381366"
}
},
"parameters": {
"webAppName": {
"type": "string",
"defaultValue": "[format('webApp-{0}', uniqueString(resourceGroup().id))]",
"minLength": 2,
"metadata": {
"description": "Web app name."
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "Location for all resources."
}
},
"sku": {
"type": "string",
"defaultValue": "F1",
"metadata": {
"description": "The SKU of App Service Plan."
}
},
"linuxFxVersion": {
"type": "string",
"defaultValue": "DOTNETCORE|3.0",
"metadata": {
"description": "The Runtime stack of current web app"
}
},
"repoUrl": {
"type": "string",
"defaultValue": " ",
"metadata": {
"description": "Optional Git Repo URL"
}
}
},
"variables": {
"appServicePlanPortalName": "[format('AppServicePlan-{0}', parameters('webAppName'))]"
},
"resources": [
{
"type": "Microsoft.Web/serverfarms",
"apiVersion": "2021-02-01",
"name": "[variables('appServicePlanPortalName')]",
"location": "[parameters('location')]",
"sku": {
"name": "[parameters('sku')]"
},
"kind": "linux",
"properties": {
"reserved": true
}
},
{
"type": "Microsoft.Web/sites",
"apiVersion": "2021-02-01",
"name": "[parameters('webAppName')]",
"location": "[parameters('location')]",
"properties": {
"httpsOnly": true,
"serverFarmId": "[resourceId('Microsoft.Web/serverfarms', variables('appServicePlanPortalName'))]",
"siteConfig": {
"linuxFxVersion": "[parameters('linuxFxVersion')]",
"minTlsVersion": "1.2",
"ftpsState": "FtpsOnly"
}
},
"identity": {
"type": "SystemAssigned"
},
"dependsOn": [
"[resourceId('Microsoft.Web/serverfarms', variables('appServicePlanPortalName'))]"
]
},
{
"condition": "[contains(parameters('repoUrl'), 'http')]",
"type": "Microsoft.Web/sites/sourcecontrols",
"apiVersion": "2021-02-01",
"name": "[format('{0}/{1}', parameters('webAppName'), 'web')]",
"properties": {
"repoUrl": "[parameters('repoUrl')]",
"branch": "master",
"isManualIntegration": true
},
"dependsOn": [
"[resourceId('Microsoft.Web/sites', parameters('webAppName'))]"
]
}
]
}
Two Azure resources are defined in the template:
- Microsoft.Web/serverfarms: create an App Service plan.
- Microsoft.Web/sites: create an App Service app.
This template contains several parameters that are predefined for your convenience. See the table for parameter defaults and their descriptions:
| Parameters | Type | Default value | Description |
|---|---|---|---|
| webAppName | string | webApp-<uniqueString> |
App name based on a unique string value |
| appServicePlanName | string | webAppPlan-<uniqueString> |
App Service Plan name based on a unique string value |
| location | string | [resourceGroup().location] |
App region |
| sku | string | F1 |
Instance size (F1 = Free Tier) |
| linuxFxVersion | string | DOTNETCORE|9.0 |
"Programming language stack | Version" |
| repoUrl | string | |
External Git repo (optional) |
The template used in this quickstart is from Azure Quickstart Templates. It deploys an App Service plan and an App Service app on a Windows container.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"metadata": {
"_generator": {
"name": "bicep",
"version": "0.25.53.49325",
"templateHash": "10193476814580854111"
}
},
"parameters": {
"appServiceWebAppName": {
"type": "string",
"defaultValue": "[format('webApp-{0}', uniqueString(resourceGroup().id))]",
"minLength": 2,
"metadata": {
"description": "Web App name."
}
},
"appServicePlanName": {
"type": "string",
"defaultValue": "[format('webApp-{0}', uniqueString(resourceGroup().id))]",
"minLength": 2,
"metadata": {
"description": "App Service Plan name."
}
},
"skuTier": {
"type": "string",
"defaultValue": "P1v3"
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]"
}
},
"resources": [
{
"type": "Microsoft.Web/sites",
"apiVersion": "2023-01-01",
"name": "[parameters('appServiceWebAppName')]",
"location": "[parameters('location')]",
"tags": {
"[format('hidden-related:{0}', resourceId('Microsoft.Web/serverfarms', parameters('appServicePlanName')))]": "empty"
},
"properties": {
"siteConfig": {
"appSettings": [
{
"name": "PORT",
"value": "8080"
}
],
"appCommandLine": "",
"windowsFxVersion": "DOCKER|mcr.microsoft.com/dotnet/samples:aspnetapp"
},
"serverFarmId": "[resourceId('Microsoft.Web/serverfarms', parameters('appServicePlanName'))]"
},
"dependsOn": [
"[resourceId('Microsoft.Web/serverfarms', parameters('appServicePlanName'))]"
]
},
{
"type": "Microsoft.Web/serverfarms",
"apiVersion": "2023-01-01",
"name": "[parameters('appServicePlanName')]",
"location": "[parameters('location')]",
"sku": {
"name": "[parameters('skuTier')]"
},
"kind": "windows",
"properties": {
"hyperV": true
}
}
]
}
Two Azure resources are defined in the template:
- Microsoft.Web/serverfarms: create an App Service plan.
- Microsoft.Web/sites: create an App Service app.
This template contains several parameters that are predefined for your convenience. See the table for parameter defaults and their descriptions:
| Parameters | Type | Default value | Description |
|---|---|---|---|
| webAppName | string | webApp-<uniqueString> |
App name based on a unique string value |
| appServicePlanName | string | webAppPlan-<uniqueString> |
App Service Plan name based on a unique string value |
| location | string | [resourceGroup().location] |
App region |
| skuTier | string | P1v3 |
Instance size (View available SKUs) |
| appSettings | string | [{"name": "PORT","value": "8080"}] |
App Service listening port. Needs to be 8080. |
| kind | string | windows |
Operating System |
| hyperv | string | true |
Isolation mode |
| windowsFxVersion | string | DOCKER|mcr.microsoft.com/dotnet/samples:aspnetapp |
Container image |
Deploy the template
Azure CLI is used here to deploy the template. You can also use the Azure portal, Azure PowerShell, and REST API. To learn other deployment methods, see Deploy templates.
The following code creates a resource group, an App Service plan, and a web app. A default resource group, App Service plan, and location are set for you. Replace <app-name> with a globally unique app name (valid characters are a-z, 0-9, and -).
Run the following commands to deploy a .NET framework app on Windows.
az group create --name myResourceGroup --location "southcentralus"
az deployment group create --resource-group myResourceGroup \
--parameters language=".NET" helloWorld="true" webAppName="<app-name>" \
--template-uri "https://raw.githubusercontent.com/Azure/azure-quickstart-templates/master/quickstarts/microsoft.web/app-service-docs-windows/azuredeploy.json"
Run the following commands to create a Python app on Linux:
az group create --name myResourceGroup --location "southcentralus"
az deployment group create --resource-group myResourceGroup --parameters webAppName="<app-name>" linuxFxVersion="PYTHON|3.9" \
--template-uri "https://raw.githubusercontent.com/Azure/azure-quickstart-templates/master/quickstarts/microsoft.web/app-service-docs-linux/azuredeploy.json"
To deploy a different language stack, update linuxFxVersion with appropriate values. Samples are shown in the table. To show current versions, run the following command in the Cloud Shell:
az webapp config show --resource-group myResourceGroup --name <app-name> --query linuxFxVersion
| Language | Example |
|---|---|
| .NET | linuxFxVersion="DOTNETCORE|9.0" |
| Java | linuxFxVersion="JAVA|21-java21 TOMCAT|11.0-java21 JBOSSEAP|8-java17" |
| Node.js | linuxFxVersion="NODE|22-lts |
| Python | linuxFxVersion="PYTHON|3.13" |
| PHP | linuxFxVersion="PHP|8.4" |
Run the following commands to deploy a .NET app on a Windows container.
az group create --name myResourceGroup --location "southcentralus"
az deployment group create --resource-group myResourceGroup \
--parameters webAppName="<app-name>" \
--template-uri "https://raw.githubusercontent.com/Azure/azure-quickstart-templates/master/quickstarts/microsoft.web/app-service-docs-windows-container/azuredeploy.json"
Note
You can find more Azure App Service template samples here.
Validate the deployment
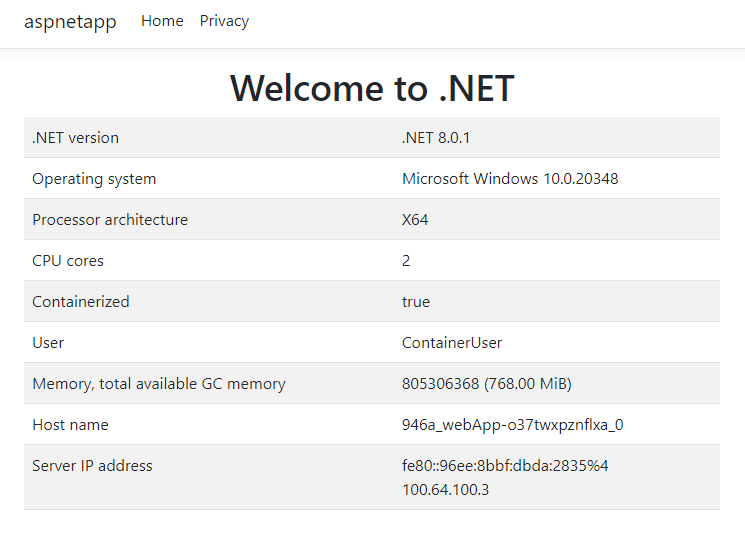
Browse to http://<app_name>.azurewebsites.net/ and verify it's been created.
Clean up resources
When no longer needed, delete the resource group.