Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to:
Azure SQL Managed Instance
This article describes how to configure a managed instance to support Windows Authentication for principals in Microsoft Entra ID (formerly Azure Active Directory). The steps to set up Azure SQL Managed Instance are the same for both the incoming trust-based authentication flow and the modern interactive authentication flow.
Prerequisites
The following prerequisites are required to configure a managed instance for Windows Authentication for Microsoft Entra principals:
| Prerequisite | Description |
|---|---|
| Az.Sql PowerShell module | This PowerShell module provides management cmdlets for Azure SQL resources. Install this module by running the following PowerShell command: Install-Module -Name Az.Sql |
| Microsoft Graph PowerShell Module | This module provides management cmdlets for Microsoft Entra administrative tasks such as user and service principal management. Install this module by running the following PowerShell command: Install-Module –Name Microsoft.Graph |
| A managed instance | You may create a new managed instance or use an existing managed instance. You must enable Microsoft Entra authentication on the managed instance. |
Configure Microsoft Entra authentication for Azure SQL Managed Instance
To enable Windows Authentication for Microsoft Entra principals, you need to enable a system-assigned service principal on each managed instance. The system-assigned service principal allows managed instance users to authenticate using the Kerberos protocol. You also need to grant admin consent to each service principal.
Enable a system assigned service principal
To enable a system assigned service principal for a managed instance:
- Sign in to the Azure portal.
- Navigate to your managed instance.
- Select Identity.
- Set System assigned service principal to On.
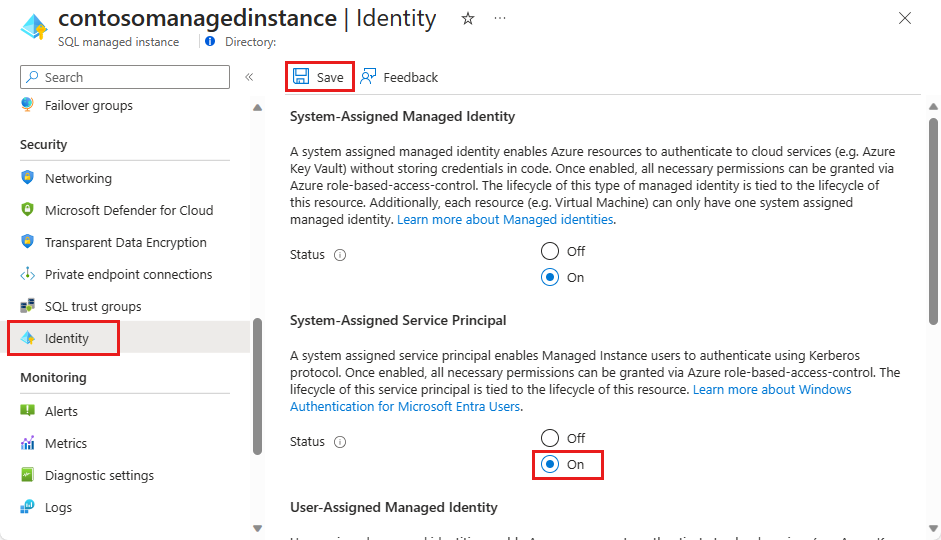
- Select Save.
Grant admin consent to a system assigned service principal
Sign in to the Azure portal.
Open Microsoft Entra ID.
Select App registrations.
Select the application with the display name matching your managed instance. The name will be in the format:
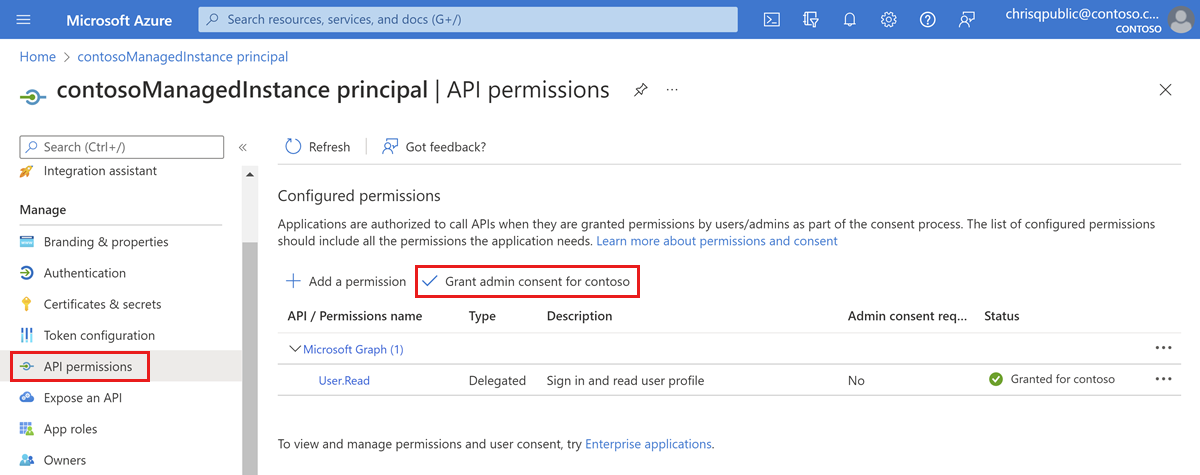
<managedinstancename> principal.Select API permissions.
Select Grant admin consent.
Select Yes on the prompt to Grant admin consent confirmation.
Connect to the managed instance with Windows Authentication
If you have already implemented either the incoming trust-based authentication flow or the modern interactive authentication flow, depending on the version of your client, you can now test connecting to your managed instance with Windows Authentication.
To test the connection with SQL Server Management Studio (SSMS), follow the steps in Quickstart: Use SSMS to connect to and query Azure SQL Database or Azure SQL Managed Instance. Select Windows Authentication as your authentication type.
Next steps
Learn more about implementing Windows Authentication for Microsoft Entra principals on Azure SQL Managed Instance: