Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article describes how to implement the modern interactive authentication flow to allow clients running Windows 10 20H1, Windows Server 2022, or a higher version of Windows to authenticate to Azure SQL Managed Instance using Windows Authentication. Clients must be joined to Microsoft Entra ID (formerly Azure Active Directory) or Microsoft Entra hybrid joined.
Enabling the modern interactive authentication flow is one step in setting up Windows Authentication for Azure SQL Managed Instance using Microsoft Entra ID and Kerberos. The incoming trust-based flow is available for AD joined clients running Windows 10 / Windows Server 2012 and higher.
With this feature, Microsoft Entra ID is now its own independent Kerberos realm. Windows 10 21H1 clients are already enlightened and will redirect clients to access Microsoft Entra Kerberos to request a Kerberos ticket. The capability for clients to access Microsoft Entra Kerberos is switched off by default and can be enabled by modifying group policy. Group policy can be used to deploy this feature in a staged manner by choosing specific clients you want to pilot on and then expanding it to all the clients across your environment.
Note
Microsoft Entra ID was previously known as Azure Active Directory (Azure AD).
Prerequisites
There is no Active Directory to Microsoft Entra ID set up required to enable running software on Microsoft Entra-joined VMs to access Azure SQL Managed Instance using Windows Authentication. The following prerequisites are required to implement the modern interactive authentication flow:
| Prerequisite | Description |
|---|---|
| Clients must run Windows 10 20H1, Windows Server 2022, or a higher version of Windows. | |
| Clients must be Microsoft Entra joined or Microsoft Entra hybrid joined. | You can determine if this prerequisite is met by running the dsregcmd command: dsregcmd.exe /status |
| Application must connect to the managed instance via an interactive session. | This supports applications such as SQL Server Management Studio (SSMS) and web applications, but won't work for applications that run as a service. |
| Microsoft Entra tenant. | |
| Azure subscription under the same Microsoft Entra tenant you plan to use for authentication. | |
| Microsoft Entra Connect installed. | Hybrid environments where identities exist both in Microsoft Entra ID and AD. |
Configure group policy
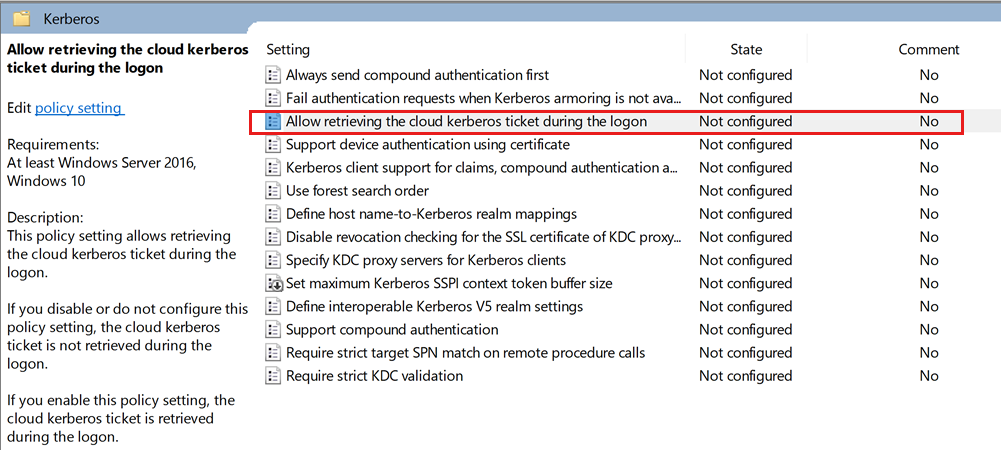
Enable the following group policy setting Administrative Templates\System\Kerberos\Allow retrieving the cloud Kerberos ticket during the logon:
Open the group policy editor.
Navigate to
Administrative Templates\System\Kerberos\.Select the Allow retrieving the cloud kerberos ticket during the logon setting.
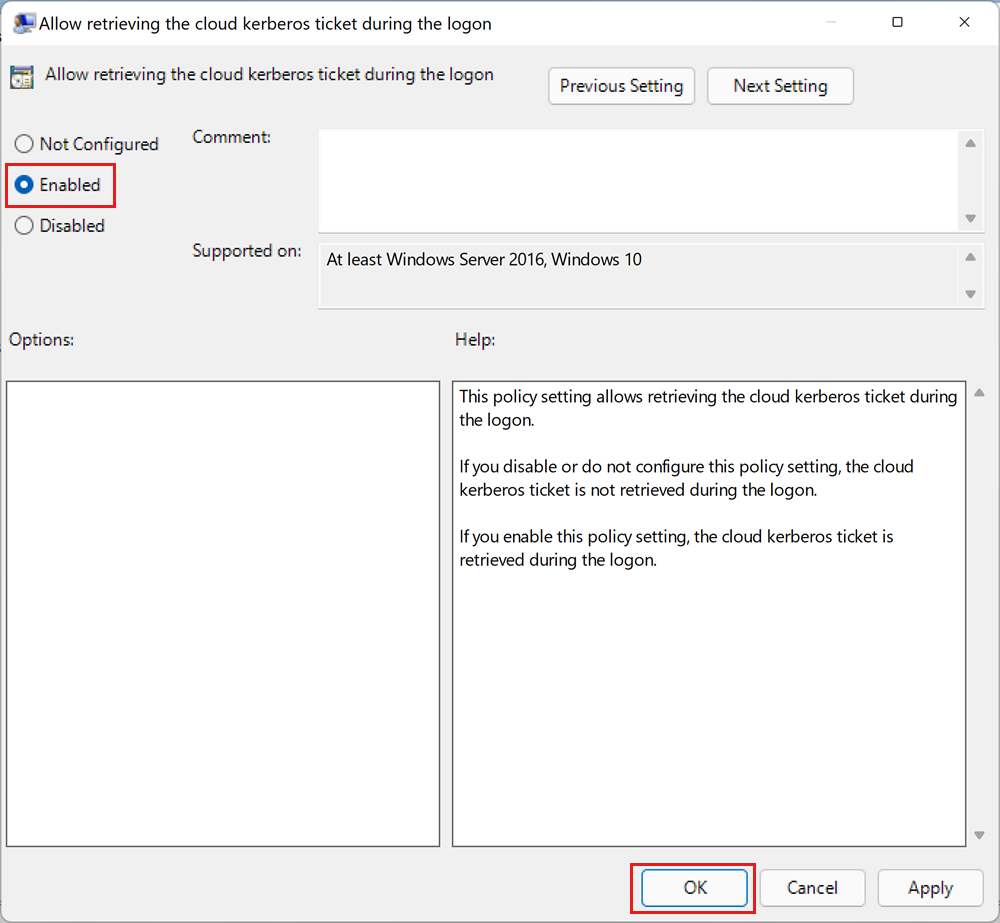
In the setting dialog, select Enabled.
Select OK.
Refresh PRT (optional)
Users with existing logon sessions may need to refresh their Microsoft Entra Primary Refresh Token (PRT) if they attempt to use this feature immediately after it has been enabled. It can take up to a few hours for the PRT to refresh on its own.
To refresh PRT manually, run this command from a command prompt:
dsregcmd.exe /RefreshPrt
Next steps
Learn more about implementing Windows Authentication for Microsoft Entra principals on Azure SQL Managed Instance:
- What is Windows Authentication for Microsoft Entra principals on Azure SQL Managed Instance?
- How Windows Authentication for Azure SQL Managed Instance is implemented with Microsoft Entra ID and Kerberos
- How to set up Windows Authentication for Microsoft Entra ID with the incoming trust-based flow
- Configure Azure SQL Managed Instance for Windows Authentication for Microsoft Entra ID
- Troubleshoot Windows Authentication for Microsoft Entra principals on Azure SQL Managed Instance