Use service tags for Azure Web PubSub Service
You can use Service Tags to identify Azure Web PubSub Service traffic. A service tag represents a group of IP address prefixes. Azure Web PubSub Service manages a service tag called AzureWebPubSub for both inbound and outbound traffic.
A service tag can be used when for configuring Network Security Group. Alternatively, you can query the IP address prefixes using Service Tag Discovery API.
Outbound traffic
Endpoints of Azure Web PubSub Service resources are guaranteed to be within IP ranges of Service Tag AzureWebPubSub.
Access Azure Web PubSub Service from virtual network
You can allow outbound traffic from your network to Azure Web PubSub Service by adding a new outbound network security rule.
On portal, go to the network security group.
Select on the settings menu called Outbound security rules.
Select the Add button.
Select Destination and choose Service Tag.
Select Destination service tag and choose AzureWebPubSub.
Enter 443 in Destination port ranges.
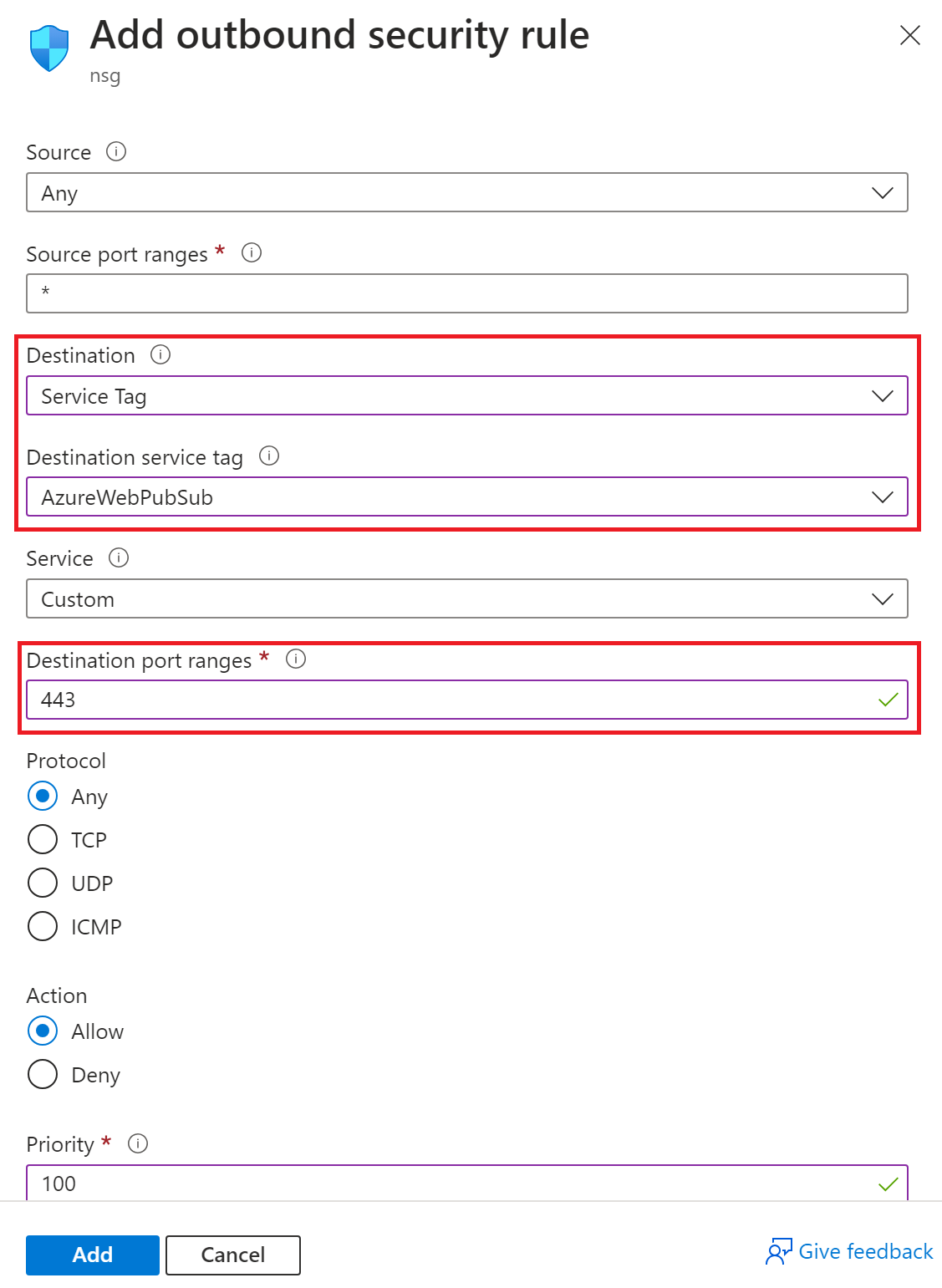
Adjust other fields as needed.
Select Add.
Inbound traffic
In following scenarios, Azure Web PubSub Service can generate network traffic to your resource. The source of traffic is guaranteed to be within IP ranges of Service Tag AzureWebPubSub.
- Use event handlers.
- Use event listeners
- Use Key Vault secret reference in URL template settings.
- Use custom certificate.
Event handler endpoints in virtual network
You can configure Network Security Group to allow inbound traffic to virtual network.
On portal, go to the network security group.
Select Inbound security rules.
Select the Add button.
Select Source and choose Service Tag from the list.
Select Source service tag and choose AzureWebPubSub from the list.
Enter * in Source port ranges.
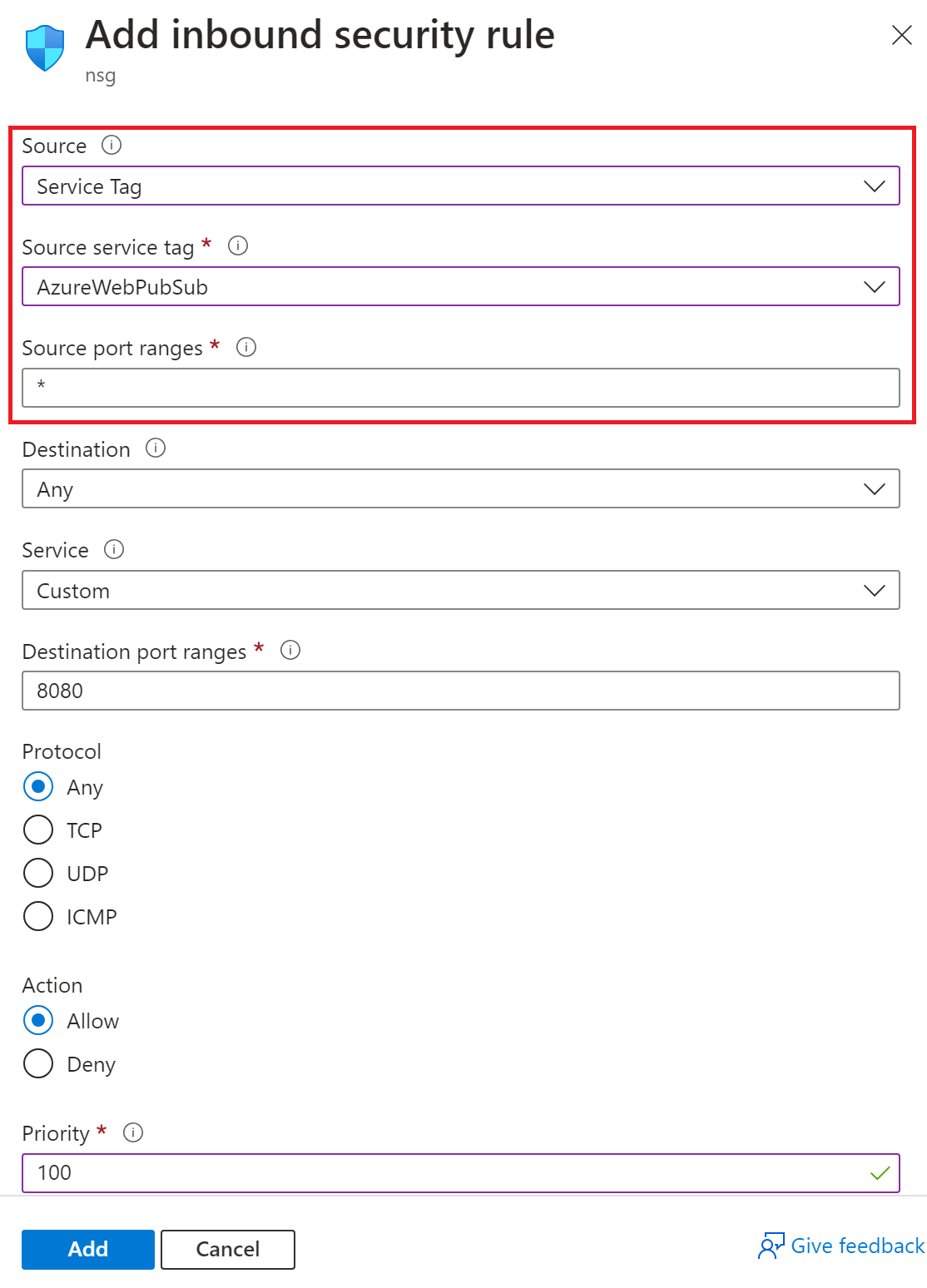
Change other settings as needed.
Select Add.
Note
Azure Web PubSub Service is a shared service. By allowing Service Tag AzureWebPubSub or its associated IP address prefixes, you also allow traffic from other resources, even if they belong to other customers. Make sure you implement appropriate authentication on your endpoints.
Event handler endpoints of Azure Function
You can configure a service tag-based rule.
Alternatively, you can use Shared Private Endpoints for better security. Shared Private Endpoints are dedicated to your resources. No traffic from other resources can access your endpoints.
Event Hubs and Key Vault access
We recommend Shared Private Endpoints for best security.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for