Validate your Microsoft Defender for APIs alerts
Microsoft Defender for APIs offers full lifecycle protection, detection, and response coverage for APIs that are published in Azure API Management. One of the main capabilities is the ability to detect exploits of the Open Web Application Security Project (OWASP) API Top 10 vulnerabilities through runtime observations of anomalies using machine learning-based and rule-based detections.
This page will walk you through the steps to trigger an alert for one of your API endpoints through Defender for APIs. In this scenario, the alert will be for the detection of a suspicious user agent.
Prerequisites
Create a new Azure API Management service instance in the Azure portal
Check the support and prerequisites for Defender for APIs deployment
An account with Postman
Simulate an alert
Sign in to the Azure portal.
Search for and select API Management services.
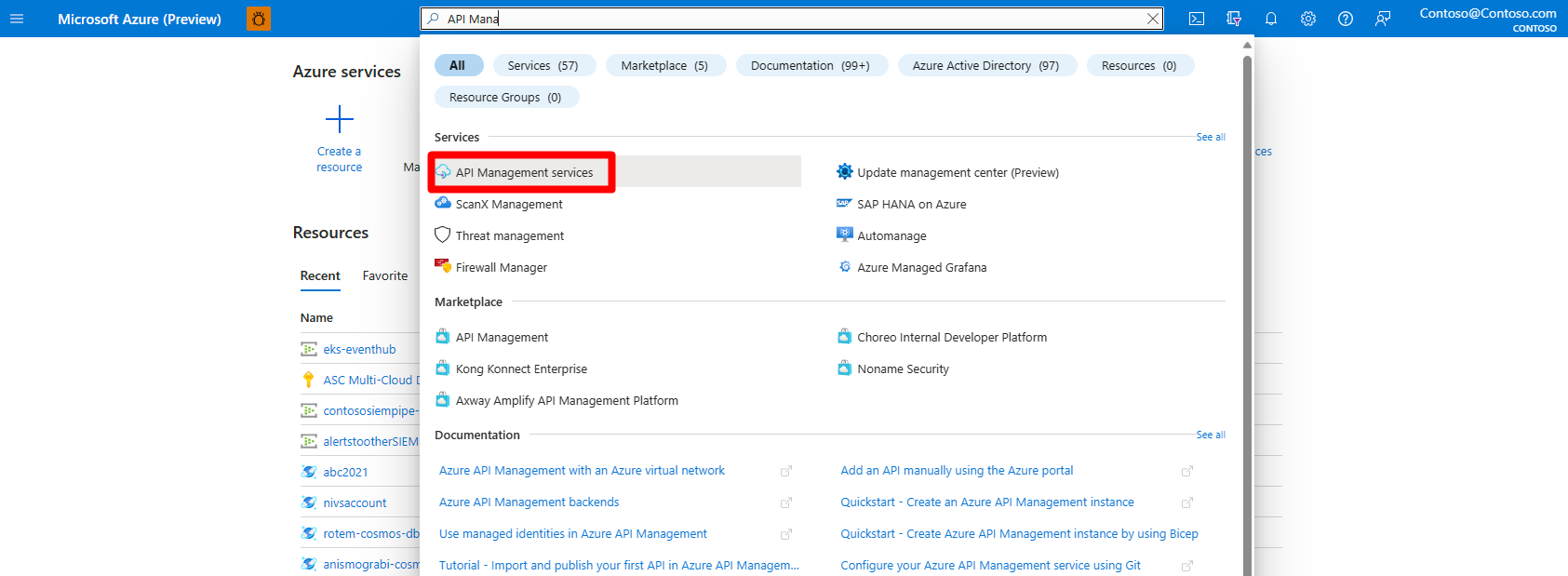
Select APIs.
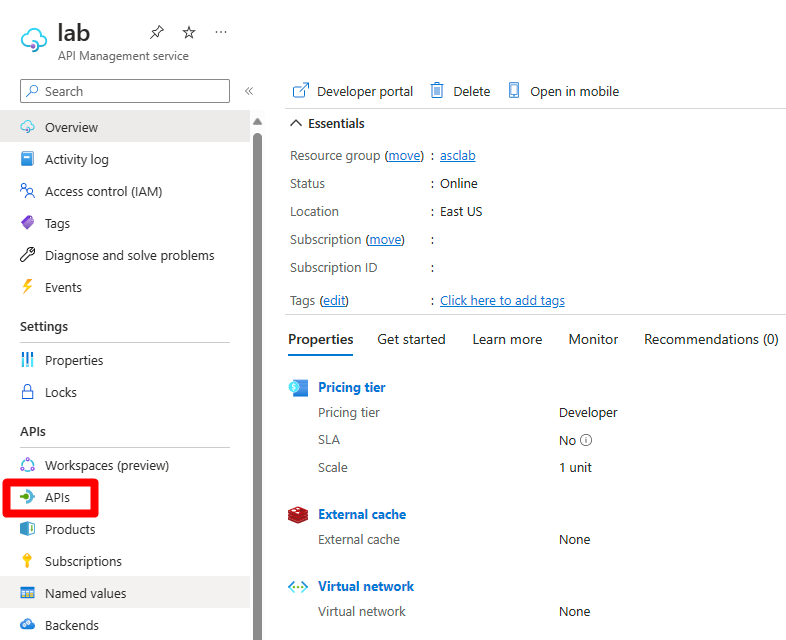
Select an API endpoint.
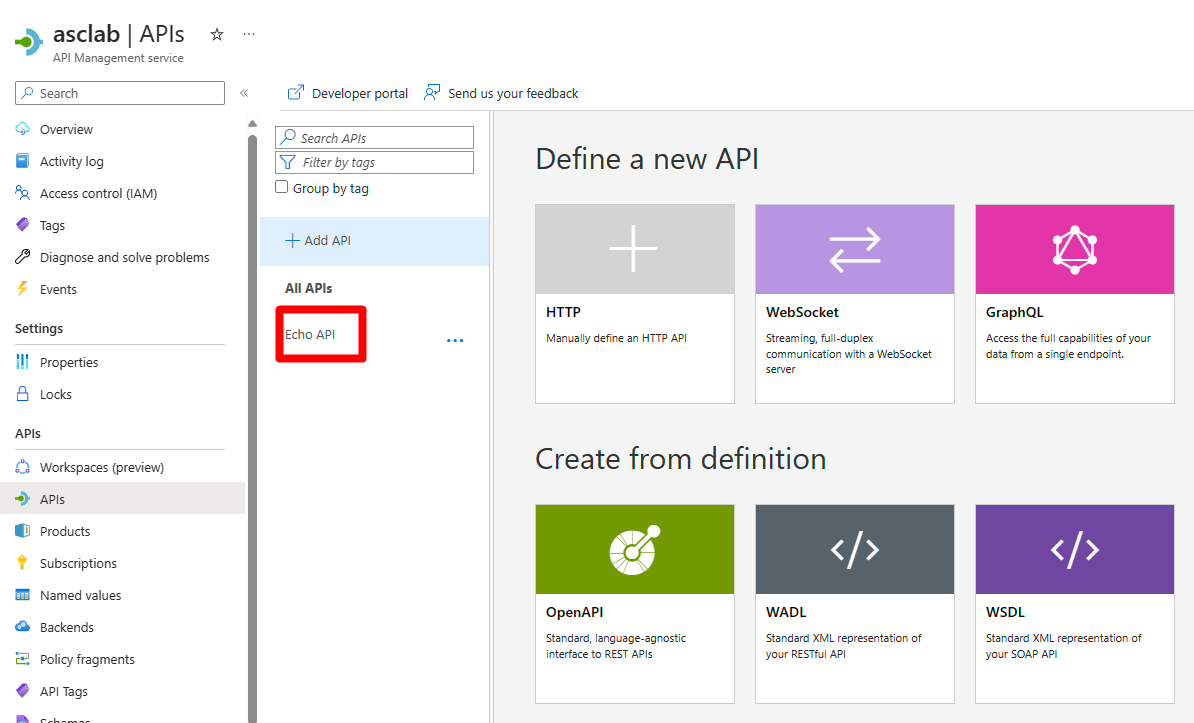
Navigate to the Test tab.
Select Get Retrieve resource (cashed).
In the HTTP request section select the see more button.
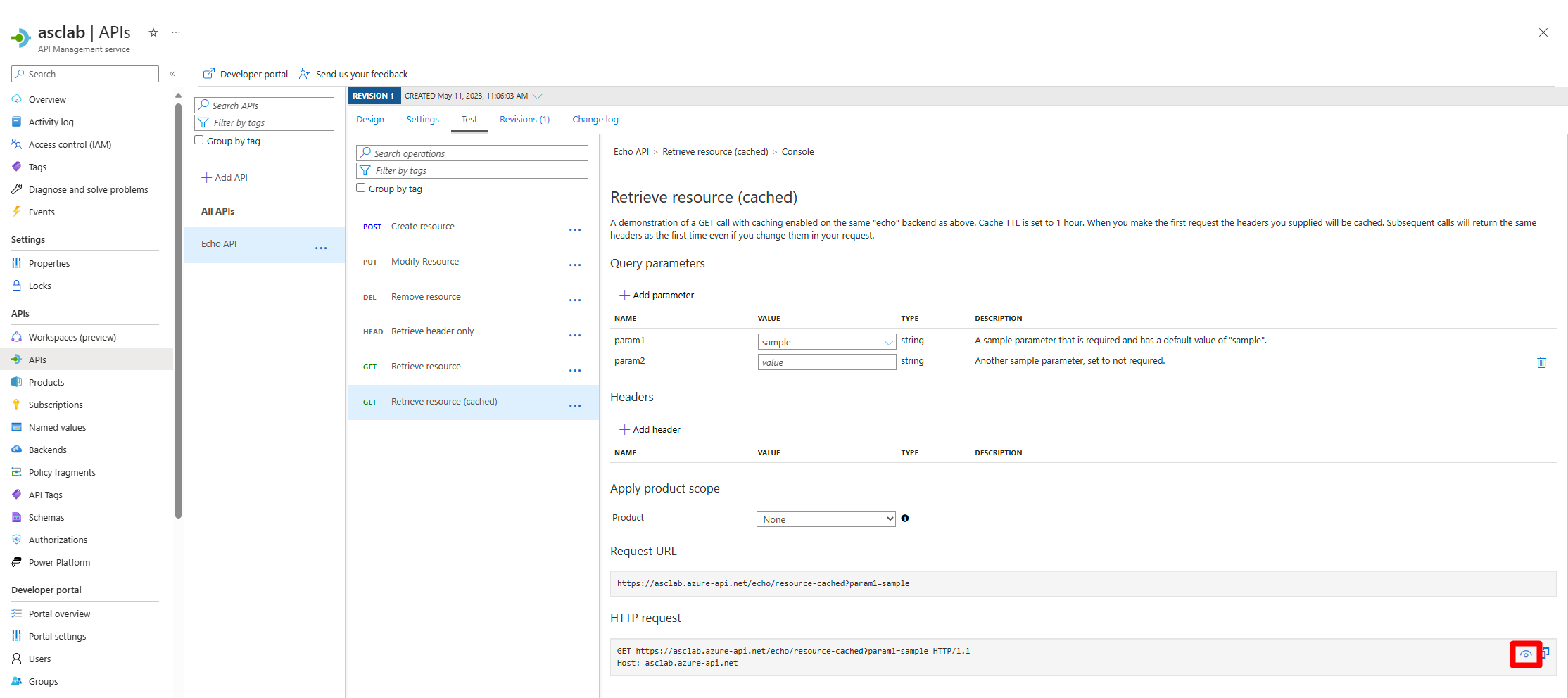
Select the Copy button.
Navigate and sign in to your Postman account.
Select My Workspace.
Select +.
Enter the HTTPS request information you copied.
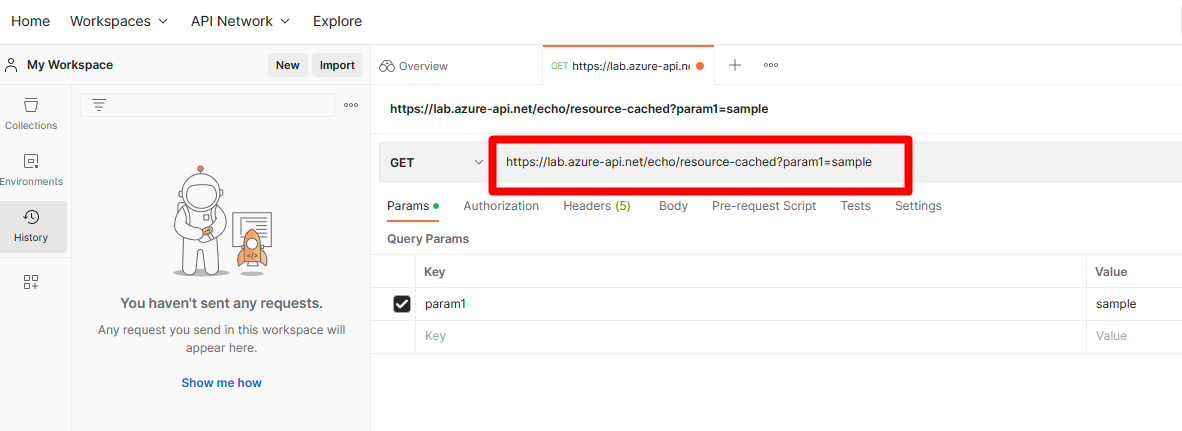
Select the Headers tab
In the key field, enter Ocp-Apim-Subscription-Key.
In the value field enter the key you copied.
In the key field enter User-Agent.
In the value field enter javascript:.
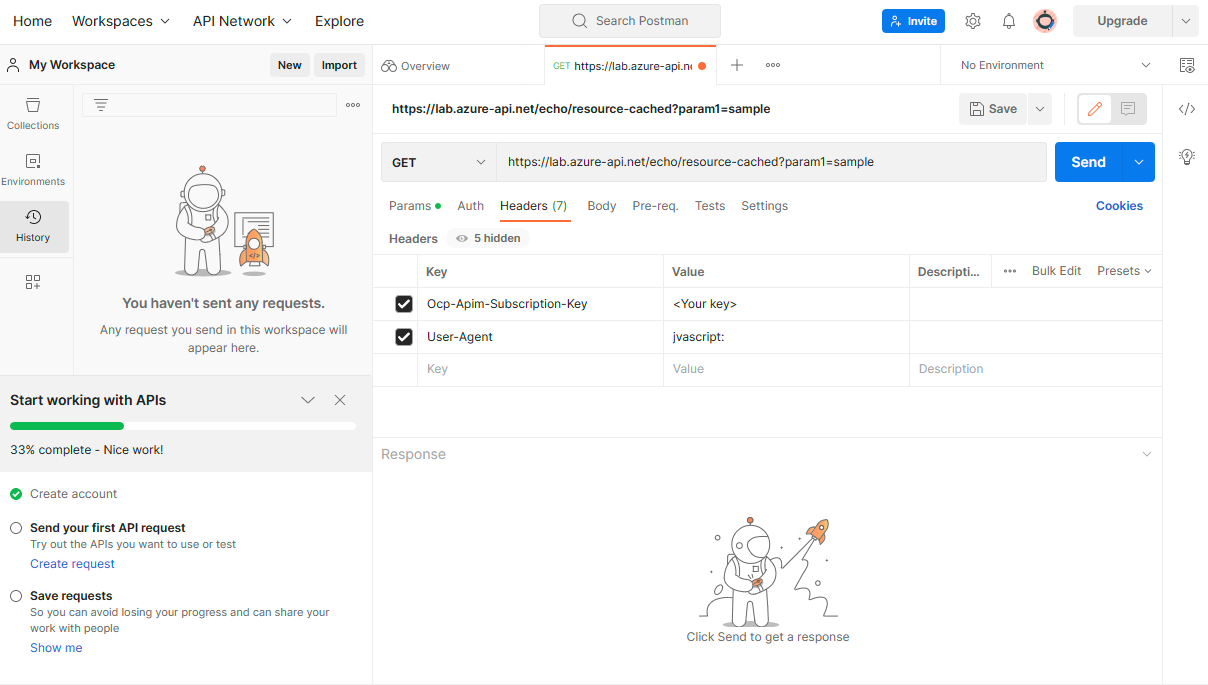
Select Send
You will see a 200 OK which will let you know that it succeeded.
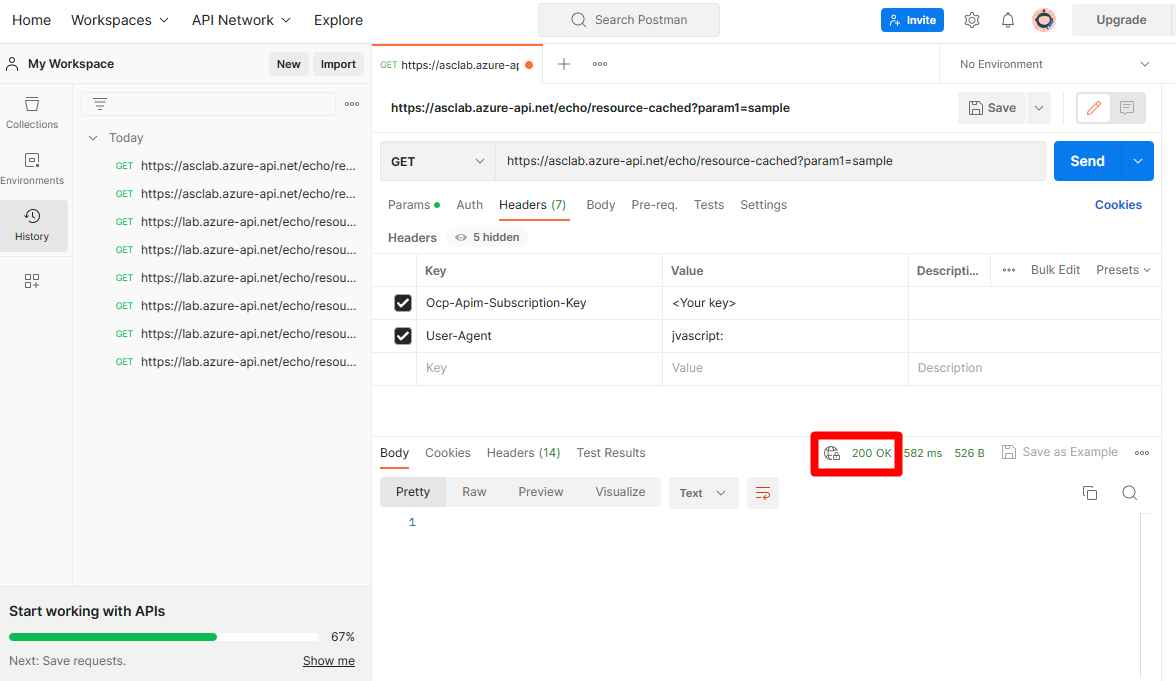
After some time, Defenders APIs will trigger an alert with detailed information about the simulated suspicious user agent activity.
Next steps
Learn how to Investigate API findings, recommendations, and alerts.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for