Review and remediate endpoint detection and response recommendations (agentless)
Microsoft Defender for Cloud provides recommendations to secure and configure your endpoint detection and response solutions. By remediating these recommendations, you can ensure that your endpoint detection and response solution are compliant and secure across all environments.
The endpoint detection and response recommendations allow you to:
Identify if an endpoint detection and response solution is installed on your multicloud machines
Identify gaps in the security configurations on any of the discovered endpoint detection and response solutions
Remediate detected gaps in your security configurations
Prerequisites
The recommendations mentioned in this article are only available if you have the following prerequisites in place:
Defender for Cloud enabled on your Azure account.
You must have either of the following plans enabled on Defender for Cloud enabled on your subscription:
You must enable agentless scanning for virtual machines.
Note
The feature described on this page is the replacement feature for the MMA based feature, which is set to be retired along with the MMA retirement in August 2024.
Learn more about the migration and the deprecation process of the endpoint protection related recommendations.
Review and remediate endpoint detection and response discovery recommendations
When Defender for Cloud discovers a supported endpoint detection and response solution on your VM, the agentless machine scanner performs the following checks to see:
- If a supported endpoint detection and response solution is enabled
- If Defender for Servers plan 2 is enabled on your subscription and the associated VMs
- If the supported solution is installed successfully
If these checks present issues, the recommendation offers different remediation steps to ensure that your VMs are protected by a supported endpoint detection and response solution and address any security gaps.
Supported solutions and platforms
The following endpoint detection and response solutions are supported in Defender for Cloud:
| Endpoint detection and response solution | Supported platforms |
|---|---|
| Microsoft Defender for Endpoint for Windows | Windows |
| Microsoft Defender for Endpoint for Linux | Linux |
| Microsoft Defender for Endpoint Unified Solution | Windows Server 2012 R2 and Windows 2016 |
| CrowdStrike (Falcon) | Windows and Linux |
| Trellix | Windows and Linux |
| Symantec | Windows and Linux |
| Sophos | Windows and Linux |
| Singularity Platform by SentinelOne | Windows and Linux |
| Cortex XDR | Windows and Linux |
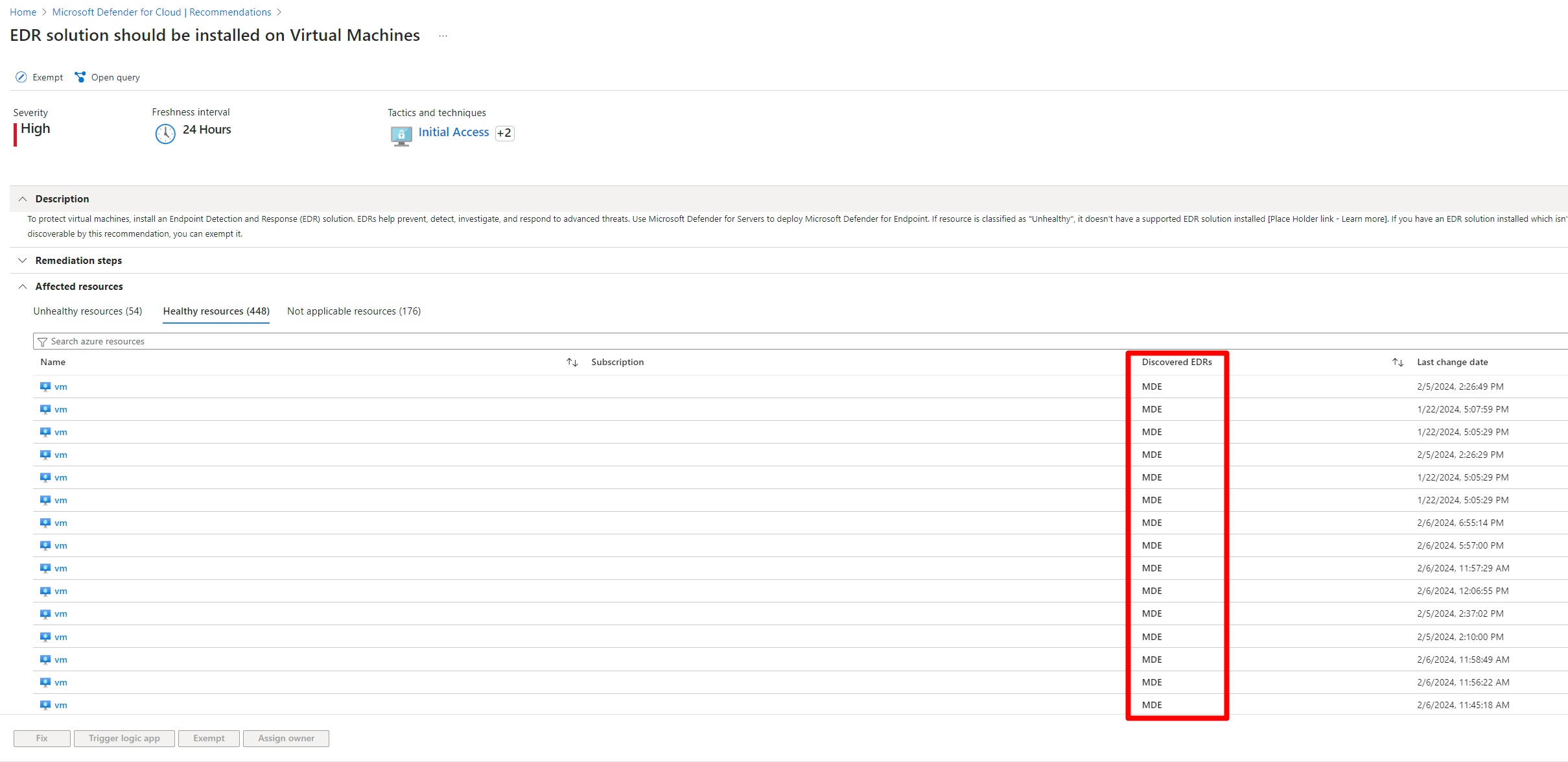
Identify which endpoint detection and response solution is enabled on a VM
Defender for Cloud has the ability to tell you if you have a supported endpoint detection and response solution enabled on your virtual machines (VM) and which one it is.
To identify which solution is enabled on a VM:
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Recommendations.
Search for and select one of the following recommendations:
EDR solution should be installed on Virtual MachinesEDR solution should be installed on EC2sEDR solution should be installed on Virtual Machines (GCP)
Select the Healthy resources tab.
The discovered endpoint detection and response column displays the solution that is detected.
Review and remediate the discovery recommendations
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Recommendations.
Search for and select one of the following recommendations:
EDR solution should be installed on Virtual MachinesEDR solution should be installed on EC2sEDR solution should be installed on Virtual Machines (GCP)
Select the relevant recommendation.
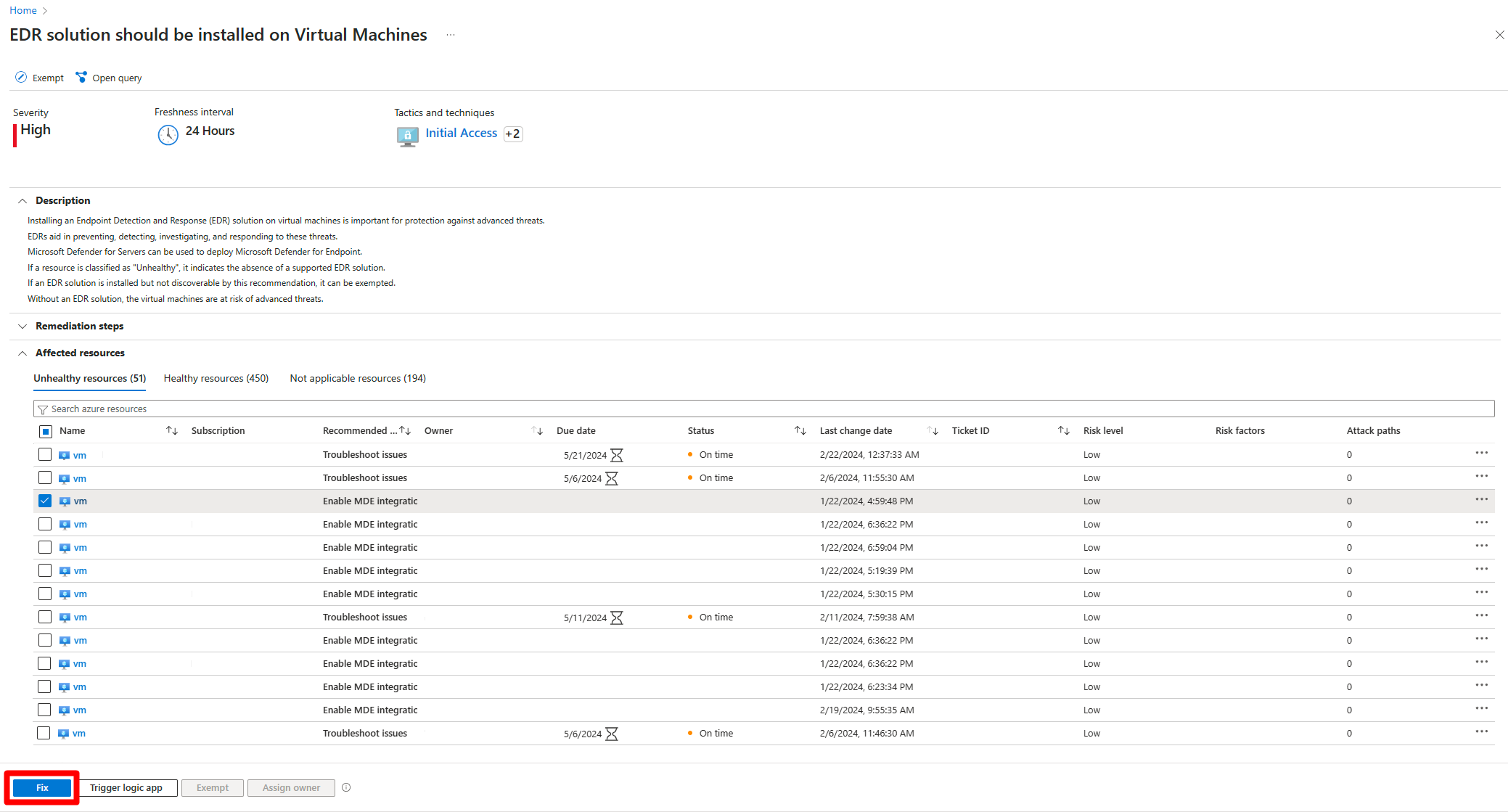
The recommendation offers multiple recommended actions to resolve on each attached machine, select the relevant action to see the remediation steps:
- Enable Microsoft Defender for Endpoint integration. Alternatively, you can remediate this recommendation by installing any of the supported endpoint detection and response solution on your virtual machine
- Upgrade Defender plan
- Troubleshoot issues
Enable the Microsoft Defender for Endpoint integration
This recommended action is available when:
One of the supported endpoint detection and response solution wasn't detected on the VM.
The VM can have Microsoft Defender for Endpoint installed on it as part of the offerings included with Defender for Servers.
To enable the Defender for Endpoint integration on the affected VM:
Select the affected machine.
(Optional) Select multiple affected machines that have the
Enable Microsoft Defender for Endpoint integrationrecommended action.Select Fix.
Select Enable.
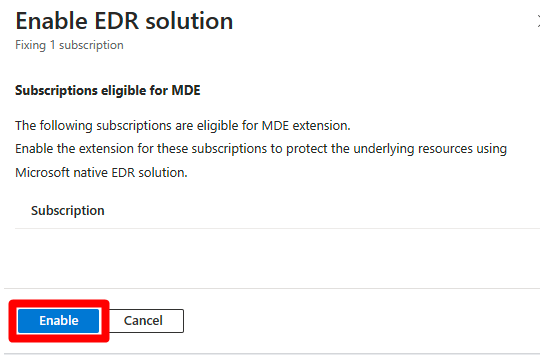
Defender for endpoint is applied to all Windows and Linux servers within your subscription. After the process is completed, it can take up to 24 hours until your machine appears in the Healthy resources tab.
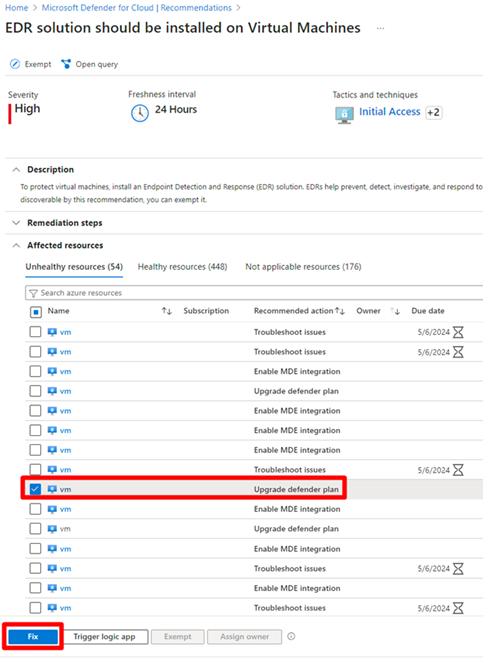
Upgrade Defender plan
This recommended action is available when:
One of the supported endpoint detection and response solution wasn't detected on the VM.
Defender for Servers plan 2 isn't enabled on the VM.
To enable the Defender for Endpoint integration on your Defender for Servers plan on the affected VM:
Select the affected machine.
(Optional) Select multiple affected machines that have the
Upgrade Defender planrecommended action.Select Fix.
Select a plan in the dropdown menu. Each plan comes with a cost, learn more about the cost on the Defender for Cloud pricing page.
Select Enable.
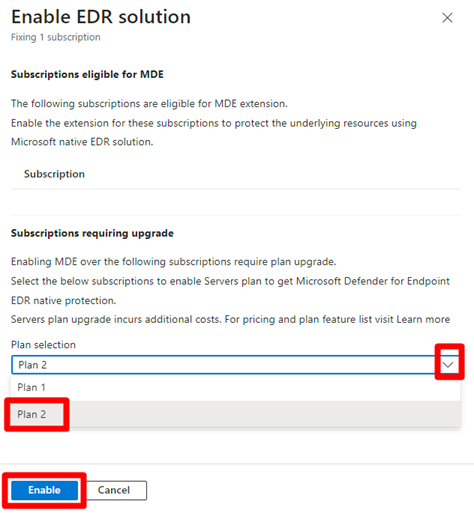
After the process is completed, it can take up to 24 hours until your machine appears in the Healthy resources tab.
Troubleshoot unsuccessful installation
This recommended action is available when:
- Defender for Endpoint is detected on your machine, but the installation was unsuccessful.
To troubleshoot issues on your VM:
Select the affected resource.
Select Remediation steps.
Follow the instructions to troubleshoot Microsoft Defender for Endpoint onboarding issues for Windows or Linux.
After the process is completed, it can take up to 24 hours until your machine appears in the Healthy resources tab.
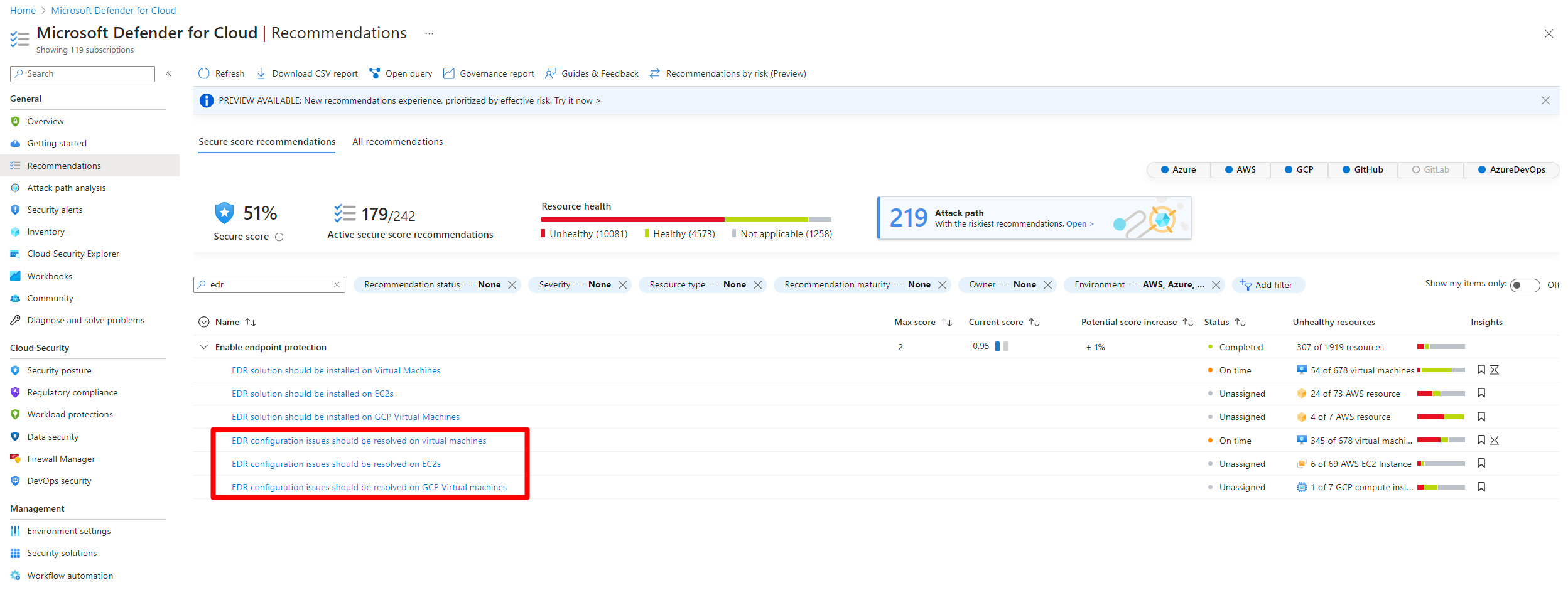
Review and remediate endpoint detection and response misconfiguration recommendations
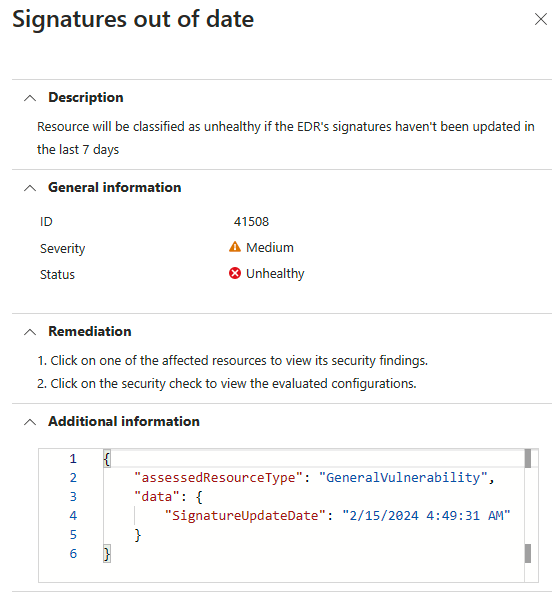
When Defender for Cloud finds misconfigurations in your endpoint detection and response solution, recommendations appear on the recommendations page. This recommendation is only applicable to VMs that have Defender for Endpoint enabled on them. These recommendations check for the following security checks:
Both full and quick scans are out of 7 daysSignature out of dateAnti-virus is off or partially configured
To detect misconfigurations in endpoint detection and response solution:
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Recommendations.
Search for and select one of the following recommendations:
EDR configuration issues should be resolved on virtual machinesEDR configuration issues should be resolved on EC2sEDR configuration issues should be resolved on GCP virtual machines
Select the relevant recommendation.
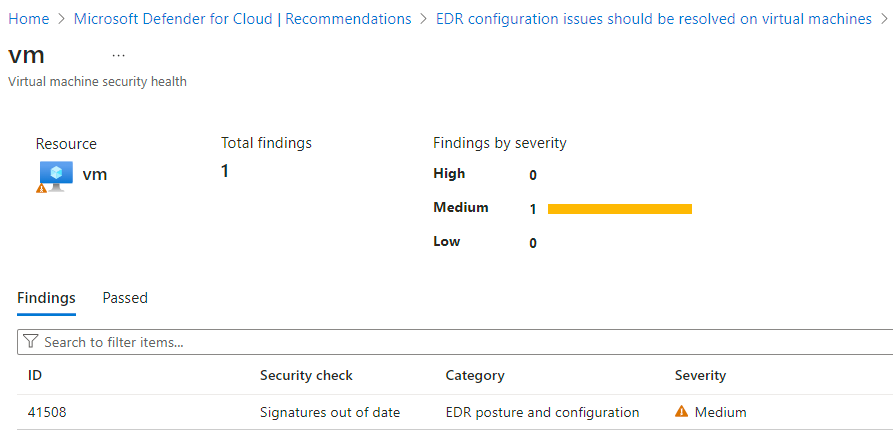
Select a security check to review the affected resources.
Select each security check to review all affected resources.
Expand the affected resources section.
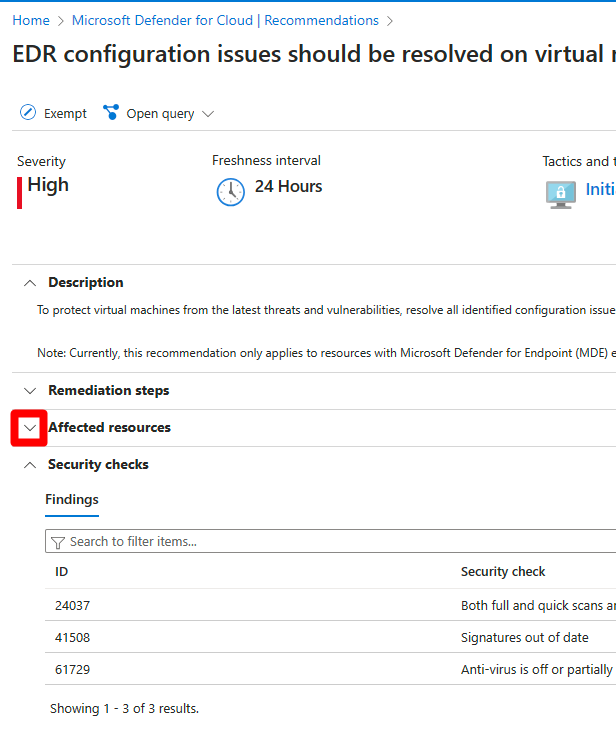
Select an unhealthy resource to review its findings.
Select the security check to see additional information and follow the remediation steps.
After the process is completed, it can take up to 24 hours until your machine appears in the Healthy resources tab.