Methods for connecting sensors to Azure
This article is one in a series of articles describing the deployment path for OT monitoring with Microsoft Defender for IoT.
Use the content below to learn about the architectures and methods supported for connecting Defender for IoT sensors to the Azure portal in the cloud.
Network sensors connect to Azure to provide data about detected devices, alerts, and sensor health, to access threat intelligence packages, and more. For example, connected Azure services include IoT Hub, Blob Storage, Event Hubs, Aria, the Microsoft Download Center.
All connection methods provide:
Improved security, without additional security configurations. Connect to Azure using specific and secure endpoints, without the need for any wildcards.
Encryption, Transport Layer Security (TLS1.2/AES-256) provides encrypted communication between the sensor and Azure resources.
Scalability for new features supported only in the cloud
Important
To ensure that your network is ready, we recommend that you first run your connections in a lab or testing environment so that you can safely validate your Azure service configurations.
Choose a sensor connection method
Use this section to help determine which connection method is right for your cloud-connected Defender for IoT sensor.
| If ... | ... Then use |
|---|---|
| - You want to connect your sensor to Azure directly | Direct connections |
| - Your sensor needs a proxy to reach from the OT network to the cloud, or - You want multiple sensors to connect to Azure through a single point |
Proxy connections with proxy chaining |
| - You require private connectivity between your sensor and Azure, - Your site is connected to Azure via ExpressRoute, or - Your site is connected to Azure over a VPN |
Proxy connections with an Azure proxy |
| - You have sensors hosted in multiple public clouds | Multicloud connections |
Note
While most connection methods are relevant for OT sensors only, Direct connections are also used for Enterprise IoT sensors.
Direct connections
The following image shows how you can connect your sensors to the Defender for IoT portal in Azure directly over the internet from remote sites, without traversing the enterprise network.
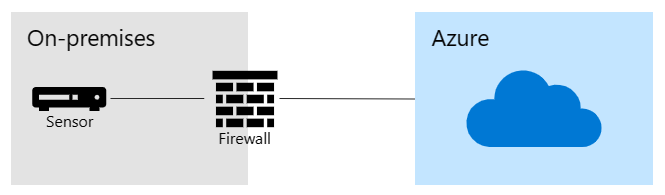
With direct connections:
Any sensors connected to Azure data centers directly over the internet or Azure ExpressRoute have a secure and encrypted connection to the Azure data centers. Transport Layer Security (TLS1.2/AES-256) provides always-on communication between the sensor and Azure resources.
The sensor initiates all connections to the Azure portal. Initiating connections only from the sensor protects internal network devices from unsolicited inbound connections, but also means that you don't need to configure any inbound firewall rules.
For more information, see Provision sensors for cloud management.
Proxy connections with proxy chaining
The following image shows how you can connect your sensors to the Defender for IoT portal in Azure through multiple proxies, using different levels of the Purdue model and the enterprise network hierarchy.
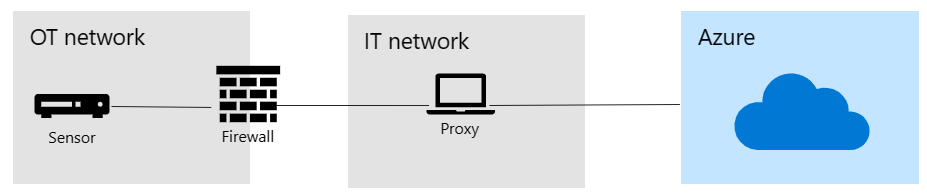
This method supports connecting your sensors with either direct internet access, private VPN or ExpressRoute, the sensor will establish an SSL-encrypted tunnel to transfer data from the sensor to the service endpoint via multiple proxy servers. The proxy server doesn't perform any data inspection, analysis, or caching.
It is the customer's responsibility to set up and maintain third-party proxy services with proxy chaining; Microsoft does not provide support for them.
For more information, see Connect via proxy chaining.
Proxy connections with an Azure proxy
The following image shows how you can connect your sensors to the Defender for IoT portal in Azure through a proxy in the Azure VNET. This configuration ensures confidentiality for all communications between your sensor and Azure.
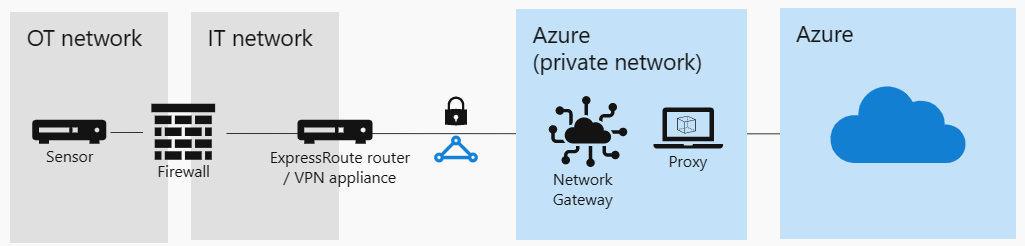
Depending on your network configuration, you can access the VNET via a VPN connection or an ExpressRoute connection.
This method uses a proxy server hosted within Azure. To handle load balancing and failover, the proxy is configured to scale automatically behind a load balancer.
For more information, see Connect via an Azure proxy.
Multicloud connections
You can connect your sensors to the Defender for IoT portal in Azure from other public clouds for OT/IoT management process monitoring.
Depending on your environment configuration, you might connect using one of the following methods:
ExpressRoute with customer-managed routing
ExpressRoute with a cloud exchange provider
A site-to-site VPN over the internet.
For more information, see Connect via multicloud vendors.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for
