Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Zero Trust is a security strategy for designing and implementing the following sets of security principles:
| Verify explicitly | Use least privilege access | Assume breach |
|---|---|---|
| Always authenticate and authorize based on all available data points. | Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection. | Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses. |
This article describes how to use the Microsoft Sentinel Zero Trust (TIC 3.0) solution, which helps governance and compliance teams monitor and respond to Zero Trust requirements according to the TRUSTED INTERNET CONNECTIONS (TIC) 3.0 initiative.
Microsoft Sentinel solutions are sets of bundled content, pre-configured for a specific set of data. The Zero Trust (TIC 3.0) solution includes a workbook, analytics rules, and a playbook, which provide an automated visualization of Zero Trust principles, cross-walked to the Trust Internet Connections framework, helping organizations to monitor configurations over time.
Note
Get a comprehensive view of your organization's Zero Trust status with the Zero Trust initiative in Microsoft Exposure Management. For more information, see Rapidly modernize your security posture for Zero Trust | Microsoft Learn.
The Zero Trust solution and the TIC 3.0 framework
Zero Trust and TIC 3.0 aren't the same, but they share many common themes and together provide a common story. The Microsoft Sentinel solution for Zero Trust (TIC 3.0) offers detailed crosswalks between Microsoft Sentinel and the Zero Trust model with the TIC 3.0 framework. These crosswalks help users to better understand the overlaps between the two.
While the Microsoft Sentinel solution for Zero Trust (TIC 3.0) provides best practice guidance, Microsoft doesn't guarantee nor imply compliance. All Trusted Internet Connection (TIC) requirements, validations, and controls are governed by the Cybersecurity & Infrastructure Security Agency.
The Zero Trust (TIC 3.0) solution provides visibility and situational awareness for control requirements delivered with Microsoft technologies in predominantly cloud-based environments. Customer experience will vary by user, and some panes may require additional configurations and query modification for operation.
Recommendations don't imply coverage of respective controls, as they're often one of several courses of action for approaching requirements, which is unique to each customer. Recommendations should be considered a starting point for planning full or partial coverage of respective control requirements.
The Microsoft Sentinel solution for Zero Trust (TIC 3.0) is useful for any of the following users and use cases:
- Security governance, risk, and compliance professionals, for compliance posture assessment and reporting
- Engineers and architects, who need to design Zero Trust and TIC 3.0-aligned workloads
- Security analysts, for alert and automation building
- Managed security service providers (MSSPs) for consulting services
- Security managers, who need to review requirements, analyze reporting, evaluating capabilities
Prerequisites
Before installing the Zero Trust (TIC 3.0) solution, make sure you have the following prerequisites:
Onboard Microsoft services: Make sure that you have both Microsoft Sentinel and Microsoft Defender for Cloud enabled in your Azure subscription.
Microsoft Defender for Cloud requirements: In Microsoft Defender for Cloud:
Add required regulatory standards to your dashboard. Make sure to add both the Microsoft Cloud security benchmark and NIST SP 800-53 R5 Assessments to your Microsoft Defender for Cloud dashboard. For more information, see add a regulatory standard to your dashboard in the Microsoft Defender for Cloud documentation.
Continuously export Microsoft Defender for Cloud data to your Log Analytics workspace. For more information, see Continuously export Microsoft Defender for Cloud data.
Required user permissions. To install the Zero Trust (TIC 3.0) solution, you must have access to your Microsoft Sentinel workspace with Security Reader permissions.
The Zero Trust (TIC 3.0) solution is also enhanced by integrations with other Microsoft Services, such as:
- Microsoft Defender XDR
- Microsoft Information Protection
- Microsoft Entra ID
- Microsoft Defender for Cloud
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Office 365
Install the Zero Trust (TIC 3.0) solution
To deploy the Zero Trust (TIC 3.0) solution from the Azure portal:
In Microsoft Sentinel, select Content hub and locate the Zero Trust (TIC 3.0) solution.
At the bottom-right, select View details, and then Create. Select the subscription, resource group, and workspace where you want to install the solution, and then review the related security content that will be deployed.
When you're done, select Review + Create to install the solution.
For more information, see Deploy out-of-the-box content and solutions.
Sample usage scenario
The following sections show how a security operations analyst could use the resources deployed with the Zero Trust (TIC 3.0) solution to review requirements, explore queries, configure alerts, and implement automation.
After installing the Zero Trust (TIC 3.0) solution, use the workbook, analytics rules, and playbook deployed to your Microsoft Sentinel workspace to manage Zero Trust in your network.
Visualize Zero Trust data
Navigate to the Microsoft Sentinel Workbooks > Zero Trust (TIC 3.0) workbook, and select View saved workbook.
In the Zero Trust (TIC 3.0) workbook page, select the TIC 3.0 capabilities you want to view. For this procedure, select Intrusion Detection.
Tip
Use the Guide toggle at the top of the page to display or hide recommendations and guide panes. Make sure that the correct details are selected in the Subscription, Workspace, and TimeRange options so that you can view the specific data you want to find.
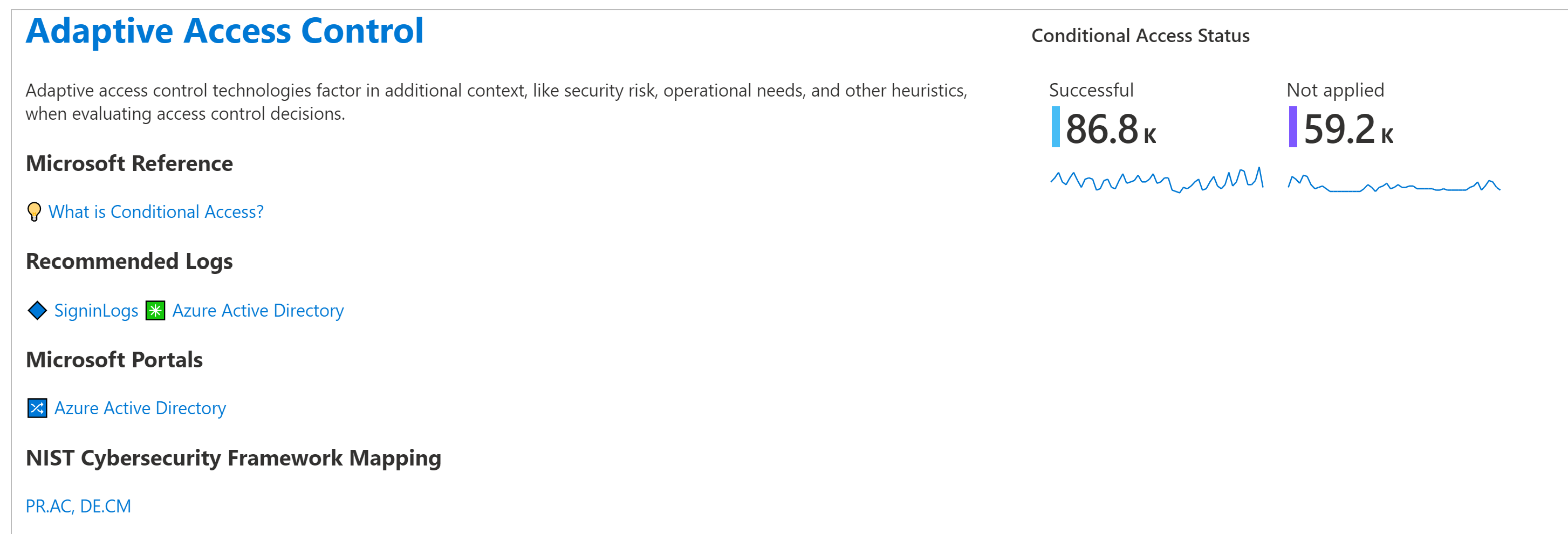
Select the control cards you want to display. For this procedure, select Adaptive Access Control, and then continue scrolling to view the displayed card.
Tip
Use the Guides toggle at the top left to view or hide recommendations and guide panes. For example, these may be helpful when you first access the workbook, but unnecessary once you've understood the relevant concepts.
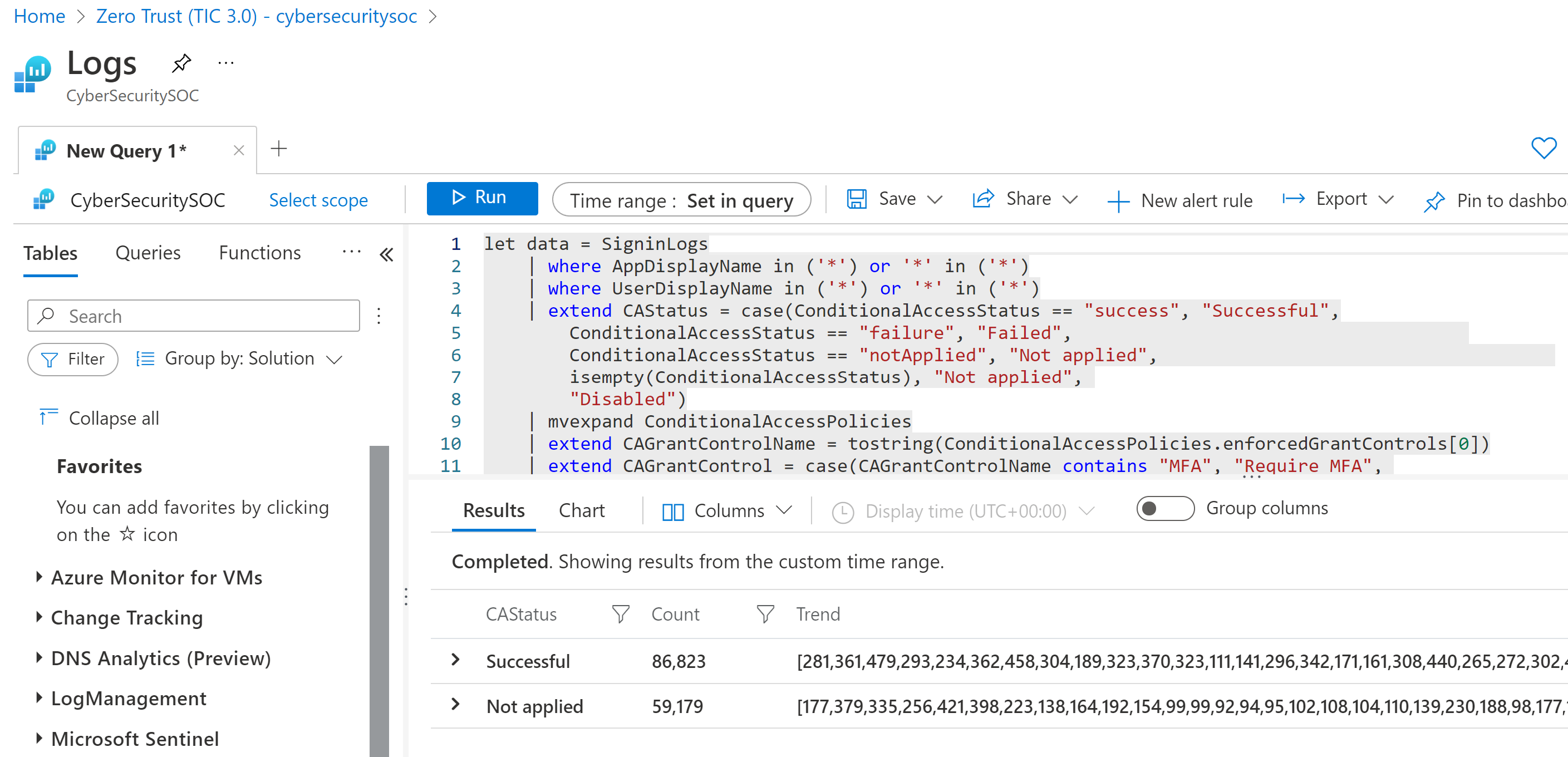
Explore queries. For example, at the top right of the Adaptive Access Control card, select the three dot Options menu, and then select Open the last run query in the Logs view.
The query is opened in the Microsoft Sentinel Logs page:
Configure Zero Trust-related alerts
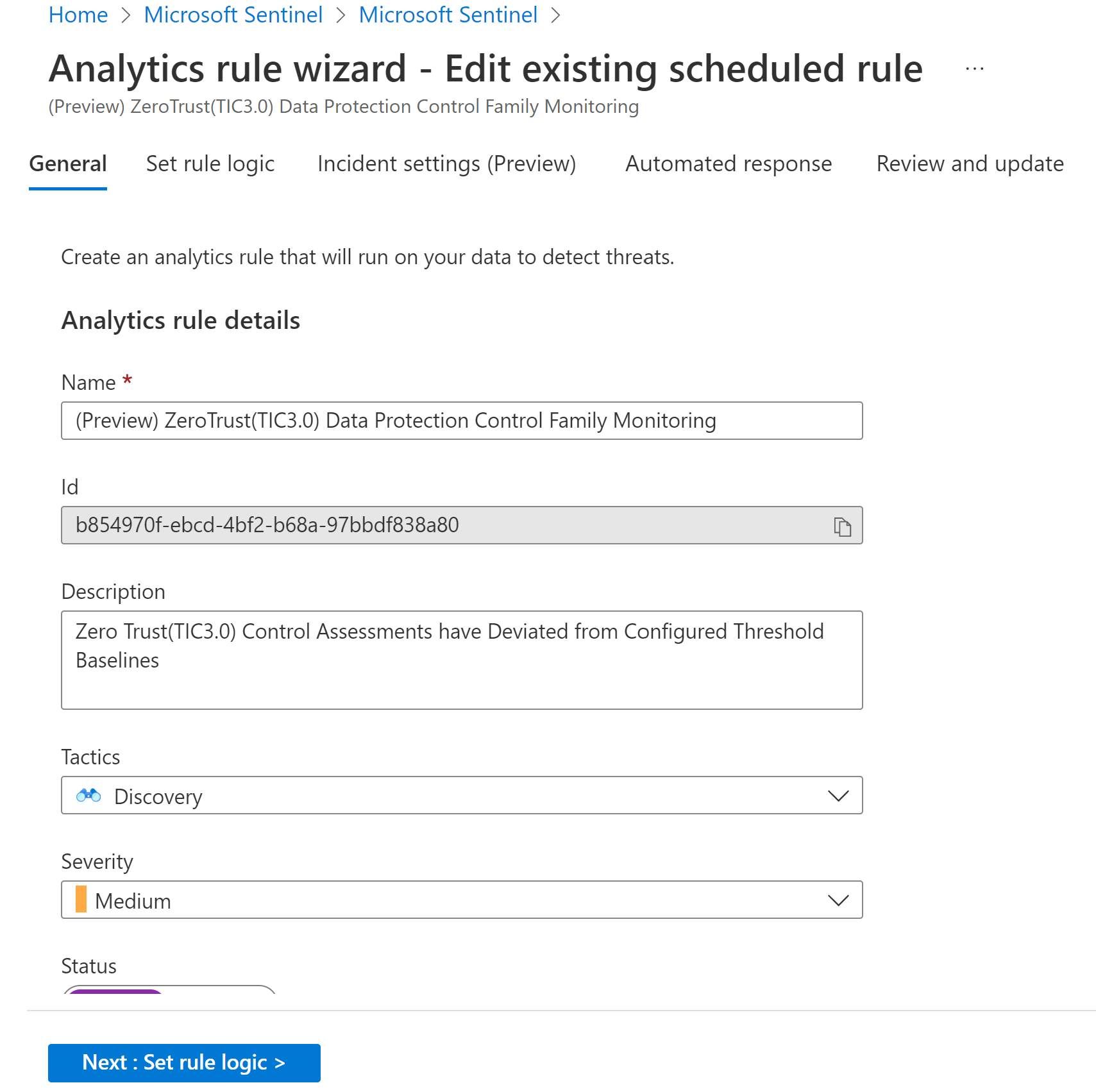
In Microsoft Sentinel, navigate to the Analytics area. View out-of-the-box analytics rules deployed with the Zero Trust (TIC 3.0) solution by searching for TIC3.0.
By default, the Zero Trust (TIC 3.0) solution installs a set of analytics rules that are configured to monitor Zero Trust (TIC3.0) posture by control family, and you can customize thresholds for alerting compliance teams to changes in posture.
For example, if your workload's resiliency posture falls below a specified percentage in a week, Microsoft Sentinel will generate an alert to detail the respective policy status (pass/fail), the assets identified, the last assessment time, and provide deep links to Microsoft Defender for Cloud for remediation actions.
Update the rules as needed or configure a new one:
For more information, see Create custom analytics rules to detect threats.
Respond with SOAR
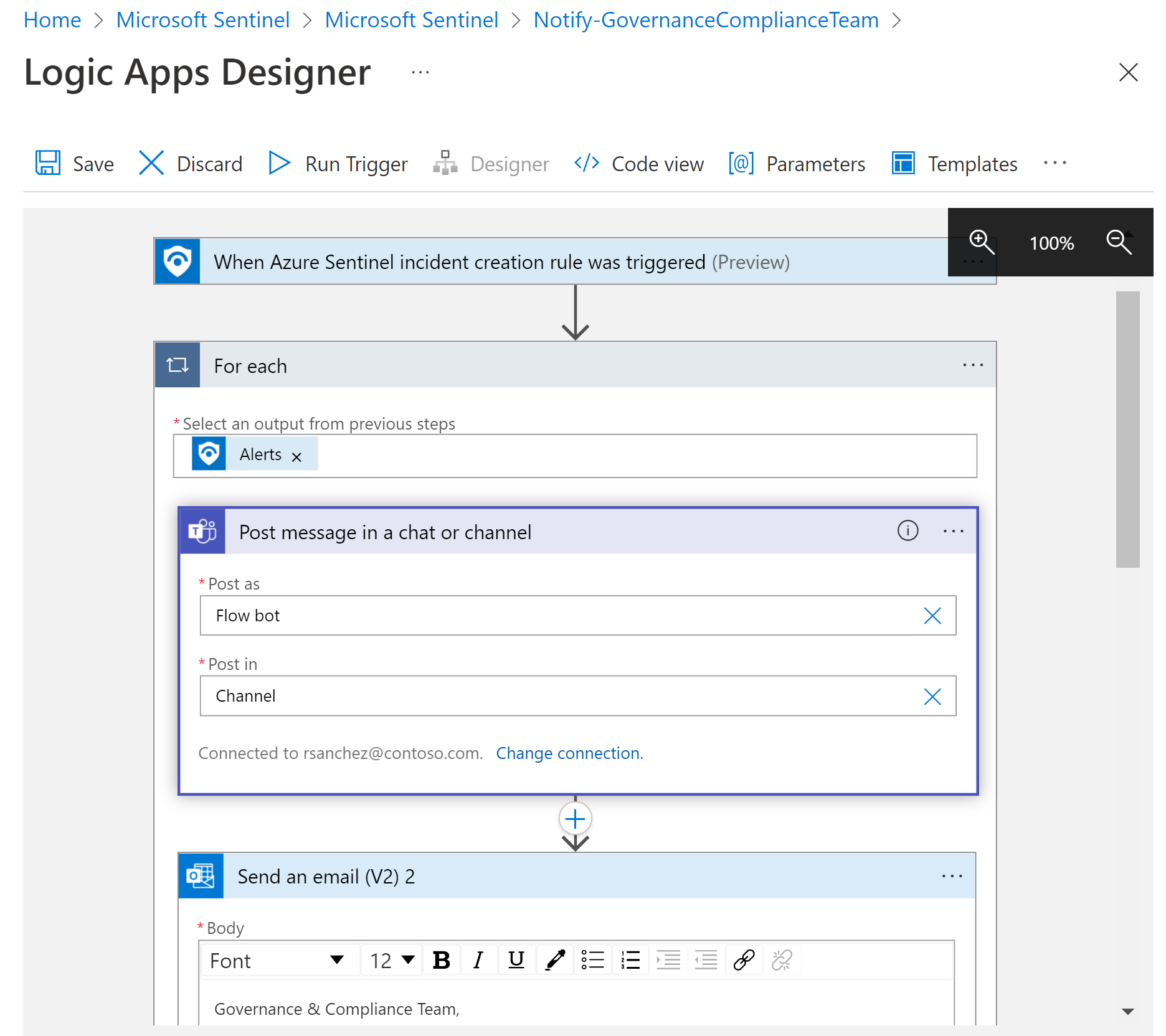
In Microsoft Sentinel, navigate to the Automation > Active playbooks tab, and locate the Notify-GovernanceComplianceTeam playbook.
Use this playbook to automatically monitor CMMC alerts, and notify the governance compliance team with relevant details via both email and Microsoft Teams messages. Modify the playbook as needed:
For more information, see Use triggers and actions in Microsoft Sentinel playbooks.
Frequently asked questions
Are custom views and reports supported?
Yes. You can customize your Zero Trust (TIC 3.0) workbook to view data by subscription, workspace, time, control family, or maturity level parameters, and you can export and print your workbook.
For more information, see Use Azure Monitor workbooks to visualize and monitor your data.
Are additional products required?
Both Microsoft Sentinel and Microsoft Defender for Cloud are required.
Aside from these services, each control card is based on data from multiple services, depending on the types of data and visualizations being shown in the card. Over 25 Microsoft services provide enrichment for the Zero Trust (TIC 3.0) solution.
What should I do with panels with no data?
Panels with no data provide a starting point for addressing Zero Trust and TIC 3.0 control requirements, including recommendations for addressing respective controls.
Are multiple subscriptions, clouds, and tenants supported?
Yes. You can use workbook parameters, Azure Lighthouse, and Azure Arc to leverage the Zero Trust (TIC 3.0) solution across all of your subscriptions, clouds, and tenants.
For more information, see Use Azure Monitor workbooks to visualize and monitor your data and Manage multiple tenants in Microsoft Sentinel as an MSSP.
Is partner integration supported?
Yes. Both workbooks and analytics rules are customizable for integrations with partner services.
For more information, see Use Azure Monitor workbooks to visualize and monitor your data and Surface custom event details in alerts.
Is this available in government regions?
Yes. The Zero Trust (TIC 3.0) solution is in Public Preview and deployable to Commercial/Government regions. For more information, see Cloud feature availability for commercial and US Government customers.
Which permissions are required to use this content?
Microsoft Sentinel Contributor users can create and edit workbooks, analytics rules, and other Microsoft Sentinel resources.
Microsoft Sentinel Reader users can view data, incidents, workbooks, and other Microsoft Sentinel resources.
For more information, see Permissions in Microsoft Sentinel.
Next steps
For more information, see:
- Get Started with Microsoft Sentinel
- Visualize and monitor your data with workbooks
- Microsoft Zero Trust Model
- Zero Trust Deployment Center
Watch our videos:
- Demo: Microsoft Sentinel Zero Trust (TIC 3.0) Solution
- Microsoft Sentinel: Zero Trust (TIC 3.0) Workbook Demo
Read our blogs!
- Announcing the Microsoft Sentinel: Zero Trust (TIC3.0) Solution
- Building and monitoring Zero Trust (TIC 3.0) workloads for federal information systems with Microsoft Sentinel
- Zero Trust: 7 adoption strategies from security leaders
- Implementing Zero Trust with Microsoft Azure: Identity and Access Management (6 Part Series)