Get answers to common questions about the Trusted Signing service.
Get started
What versions of Windows does Trusted Signing support?
The Trusted Signing service supports all versions of Windows that support the general user-mode code integrity (UMCI) security policy.
Support for signed binaries was added in the July 2021 Certificate Trust List (CTL) update for Windows. In a typical scenario, when an end-entity certificate from a chain is encountered on a computer, the system retrieves the root certificate authority (CA) certificate and adds it to the trust root store.
For more information about Windows support for Trusted Signing, see Trusted Signing Program Windows Support.
How do I grant API access to Trusted Signing in Microsoft Entra?
Ask your Microsoft Entra admin to approve your request for access. For more information about permissions, see these articles:
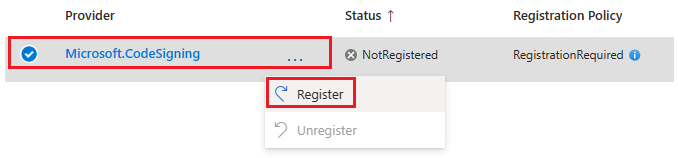
What if I don't see Microsoft.CodeSigning as a resource provider?
To register the Microsoft.CodeSigning app, go to the subscription Resource providers pane as shown in this example:
What if Organization identity validation fails?
- Currently, an organization that has a year-founded date of less than three years can't be onboarded, and identity validation fails.
- If your organization has a year-founded date of more than three years, ensure that you didn't miss an email verification link that was sent to the primary email address you entered when you created your identity validation request. The link expires after seven days. If you overlooked the email or if you didn't select the link in the email within seven days, create a new identity validation request.
- If identity validation fails, but not because of a missed email verification, the Microsoft validation team wasn't able to make a determination about your request based on the information that you provided. Even if you provide more documentation when we request it, if we can't validate the information, we can't onboard you to Trusted Signing. In this scenario, we recommend that you delete your Trusted Signing account so that you aren't billed for unused resources.
For Individual identity validation, I see an error - "You do not have permission to access this page".
For Individual identity validation, what if I don’t have an address on a bank statement or utility bill?
- Be sure to use a government issued ID with address on it, in order to successfully go through the process.
What if I already have a VID?
- Follow the steps to present your existing VID for Trusted Signing. For this process, VIDs must include your address in addition to your name. Ensure that your VIDs have your address on them before using them for Trusted Signing.
What if I need assistance with identity validation?
- For questions about identity validation in Trusted Signing, contact us via Azure Support or by using Microsoft Q&A (use the tag Azure Trusted Signing).
What is the cost of using Trusted Signing?
- For pricing information, see Trusted Signing pricing.
What are my support options when I set up Trusted Signing?
- You can create a support ticket in the Azure portal to get Azure support. Also, you can post a question or search for related questions on Microsoft Q&A (use the tag Azure Trusted Signing) or Stack Overflow (use the tag trusted-signing).
Certificate profiles and identity validation
What if my Trusted Signing subject name is different from the name in my certificate and my MSIX package name is different now?
- For Windows app MSIX packages, follow the guidance in MSIX persistent identity.
Does deleting a certificate profile revoke the certificates?
- No. If you delete a certificate profile, any certificates that were previously issued or used under that profile remain valid. The certificates aren't revoked.
Can I use a custom CN or a custom O with Trusted Signing?
- No, you can't use a custom Common Name (CN) or a custom Organization (O) with Trusted Signing. Currently, the Trusted Signing service doesn't support customization. Also, keep in mind that per the Certification Authority Browser Forum (CA/Browser Forum) in the Code Signing Baseline Requirements (CSBRs) for publicly trusted code signing certificates, CN values must always be the legal entity's validated name (for example,
Microsoft Corporation).
What if the "New identity validation" button in the Azure portal is inactive?
- If the New identity validation button in the Azure portal is inactive and you can't select it, you don't have the Trusted Signing Identity Verifier role assigned to your account. To assign yourself the role, complete the steps in Assign roles in Trusted Signing.
What if my identity validation expires?
- If you don't renew identity validation before the expiration date, certificate renewal stops. All signing processes that are associated with those specific certificate profiles stops. To continue signing by using the Trusted Signing service, create another identity validation and associate it with the relevant certificate profiles. We send multiple reminders starting at 60 days before an identity validation's expiration date to help you begin the process of renewing your identity validation.
Signing
What types of files can we sign by using Trusted Signing?
You can sign all file types that SignTool supports.
What is the Trusted Signing compliance level?
FIPS 140-2 Level 3 (mHSMs).
How do I include the appropriate EKU for our certificates in the ELAM driver resources?
For information about the Early Launch Antimalware (ELAM) driver configuration for protecting antimalware user-mode services, see the following guidance:
"Beginning in 2022, all user mode anti-malware service binaries must be signed by Microsoft's Trusted Signing signing service. The Trusted Signing issued Authenticode certificate for signing anti-malware binaries is updated every 30 days for security. To prevent the need to update the ELAM driver every time the certificate is updated, we recommend that anti-malware vendors include the Trusted Signing PCA certificate TBS hash in the CertHash portion of the ELAM driver resource file info. Additionally, the anti-malware vendor must include their unique Trusted Signing EKU identity in the EKU field of the resource file info. The EKU identity will begin with the prefix 1.3.6.1.4.1.311.97.*."
For the Microsoft ID Verified Code Signing PCA 2021 certificate, see the Microsoft PKI Services repository.
What happens if we run binaries that are signed by using Trusted Signing on a computer that doesn't have the Trusted Signing update (especially binaries that are flagged for /INTEGRITYCHECK)?
- If an /INTEGRITYCHECK flag is set, the user's signature isn't validated at runtime and it isn't run with /INTEGRITYCHECK.
- To check whether the Trusted Signing update is installed, we recommend that you check against one of your packaged /INTEGRITYCHECK-linked DLLs. You can use a test version. This way, you can complete your check and determine the availability of our /INTEGRITYCHECK-linked binaries outside the platform.
My Sectigo certificate is expiring. Can I get a new one, or do I have to use Trusted Signing?
Currently, we don't extend cross-signed certificates. You must sign by using the Trusted Signing service.
How is Trusted Signing different from the signing that partners do with Partner Center?
Signing with the Partner Center is kernel-mode signing (no change with the introduction of Trusted Signing). Sign your user-mode binaries by using Trusted Signing. For your apps that interact with the Windows Security Center (WSC) service, you must include the Code Integrity bit (/INTEGRITYCHECK). Without the Trusted Signing signature, you can't register with the WSC, and Windows Defender runs in parallel.
How do we get the Authenticode certificate?
The Authenticode certificate that's used for signing with the profile is never given to you. All certificates are securely stored within the service and are accessible only at the time of signing. The public certificate is always included in any binary that the service signs.
How do I check whether the time stamp service is healthy?
Run the following command: curl http://timestamp.acs.microsoft.com. If status code 200 is returned, the time stamp service is healthy and running.
I get errors when I do Private Trust signing. What should I do?
If you get an internal error, check that the CN name that you used matches the certificate name. Verify the package name, and copy the complete value for the subject from the Azure portal to the manifest file during signing.
I see the status "Command succeeded" for SignTool, but the file doesn't appear to be signed when I check the digital signature. What should I do?
If the signature doesn't appear in the digital signature property, run this command: .\signtool.exe verify /v /debug /pa fileName. Not all file types include the Signature tab in Properties.
How do I fix pop-up credentials in an Azure virtual machine when I run the SignTool + dlib command?
- Create a user-assigned managed identity.
- Add the user-assigned managed identity to the VM:
- Select the VM.
- On the left menu, select Identity, and then select User assigned.
- Select Add to add the managed identity.
- In the resource group (or subscription) that has the Trusted Signing Certificate Profile Signer role, add the user-assigned managed identity to the role. To assign the correct role, go to Access control (IAM) > Role assignments.
How do I fix pop-up credentials when I use Google Cloud Platform?
Because Google Cloud Platform (GCP) doesn't have an Azure managed identity resource by default, set up an environment credential. Use the EnvironmentCredential class to set up the credential. We recommend that you use these variables:
- AZURE_TENANT_ID for the Microsoft Entra tenant (directory) ID.
- AZURE_CLIENT_ID for the client (application) ID of an app registration in the tenant.
- AZURE_CLIENT_SECRET for a client secret that was generated for the app registration.
To create a client ID and secret, follow the guidance in Create a service principal.
After you create the client ID and secret, go to the resource group (or subscription) that has the Trusted Signing Certificate Profile Signer role, and add this app to the role.
What if my Trusted Signing account is suspended?
If a certificate is misused or abused per the service Terms of Use, Trusted Signing suspends the account or revokes a signing certificate or both. In this scenario, we engage with you directly and follow the guidelines in the CA/Browser Forum CSBRs.
What if I change my subscription ID or tenant ID?
Currently, Trusted Signing resources can't be migrated across subscriptions or tenants or resource groups or resources. If you want to make any change to your tenant ID or subscription ID, you must create all your Trusted Signing resources again.
Does Trusted Signing issue EV certificates?
No, Trusted Signing doesn't issue Extended Validation (EV) certificates. We don't plan to issue EV certificates in the future.
Why does SignTool keep looping when it signs MSIX packages?
Looping multiple times is expected in MSIX signing because each application file and manifest file inside the package is signed.
Common error codes and mitigations
| Error | Details |
|---|---|
| 400 | An Azure authentication error. This error is due to caching of certificates. Add "ExcludeCredentials": ["<include list of credentials to be excluded>"] to your JSON file. For more information, see DefaultAzureCredential Class (Azure.Identity). |
| 401 | You aren't authenticated. Sign out, and then sign in again. |
| 404 | Ensure that no changes were made to your configuration or firewalls rules. |
"MsalUiRequiredException" |
This error typically occurs due to the local cache. The error resolves after the cache is refreshed from Azure. |
| No certificates were found that met all the given criteria. | Check the dlib path, dlib version, dlib name, filename, and SignTool version. This error indicates that SignTool is attempting to pull certificates from your local computer instead of using Trusted Signing certificates. |
| Error: "SignerSign() failed." (-2147024846/0x80070032) | Ensure that you're using the latest version of SignTool. |
| Error code (-2147024885/0x8007000b) | For MSIX signing, this error indicates that the publisher in the manifest file doesn't match the certificate subject. Check the publisher that's listed in the manifest file. |
| Error code (-2147467259/0x80004005) | If you use Service Principal + certificate based authentication, check your Environment Variables listed under the table for "Service principal with certificate". |
| No error codes, SignTool silently fails | Ensure that the relevant .NET runtime version is installed. |
Azure.Identity.CredentialUnavailableException |
You might see this error in environments outside Azure. If you are working outside of Azure, we recommend that you add "exclude ManagedIdentity" to your manifest file. |
| 403 | - Check your Trusted Signing role. - Check the Trusted Signing account name and the Trusted Signing certificate profile name in your metadata.json file. - Check the dlib and dlib path. - Install C++ Redistributables from https://docs.microsoft.com/en-us/cpp/windows/latest-supported-vc-redist?view=msvc-170. - Check your .NET version, dlib version, and Windows SDK version. - Check if the Trusted Signing role is assigned to the identity that's trying to sign the file. - Check if the corresponding identity validation has a status of Completed. - Verify whether you access the Trusted Signing endpoint from this virtual machine or computer. Try executing the action on a different virtual machine or computer. The error might indicate a network issue. - For Private Trust scenarios 403: The user object ID that does the signing is different from the user object ID that calls Get-azCodeSigningRootCert. The appropriate object ID must have the role Trusted Signing Certificate Profile Signer. |
Cost management and billing
How do I view usage costs and billing information for Trusted Signing resources?
To review cost information, in the Azure portal, go to your subscription overview. On the left menu, select Cost Management. For more information, see Cost Management.
To review billing information, go to your subscription overview. On the left menu, select Billing. For more information, see Billing.
Is the pricing pro-rated or it is full amount regardless of when you begin to use the service?
The pricing is not calculated on a pro rata basis. The invoice is generated with the full amount for the SKU that you selected when you created the account, regardless of when you begin to use the service after you create your account.
Unenroll from the Trusted Signing service
How do I unenroll from Trusted Signing?
To unenroll from Trusted Signing, delete your Trusted Signing account. Deleting the account also deletes the associated identity validation and certificate profiles. This stops certificate renewal, effectively halting the signing process that's associated with those specific certificate profiles. However, deleting the account doesn't affect the certificates that were already used to sign your files.