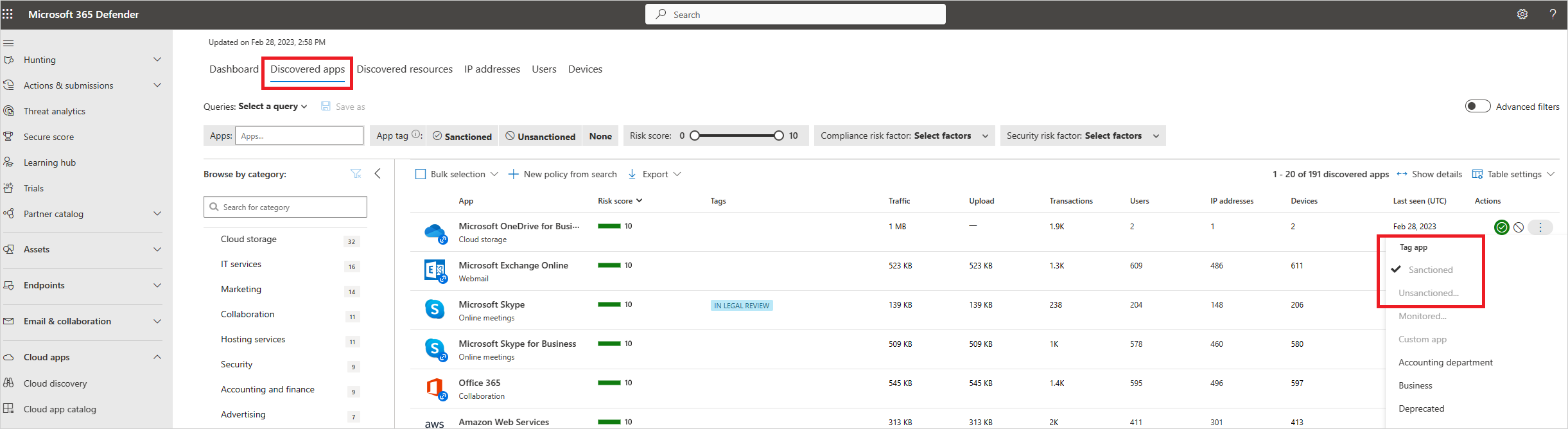
Govern discovered apps
After you review the list of discovered apps in your environment, you can secure your environment by approving safe apps (Sanctioned) or prohibiting unwanted apps (Unsanctioned) in the following ways.
Sanctioning/unsanctioning an app
You can mark a specific risky app as unsanctioned by clicking the three dots at the end of the row. Then select Unsanctioned. Unsanctioning an app doesn't block use, but enables you to more easily monitor its use with the cloud discovery filters. You can then notify users of the unsanctioned app and suggest an alternative safe app for their use, or generate a block script using the Defender for Cloud Apps APIs to block all unsanctioned apps.
Note
An app that is onboarded to inline proxy or connected via app connector, all such applications would be auto sanctioned state in Cloud Discovery.
Blocking apps with built-in streams
If your tenant uses Microsoft Defender for Endpoint, once you mark an app as unsanctioned, it's automatically blocked. Moreover, you can scope blocking to specific Defender for Endpoint device groups, monitor applications, and use the warn and educate features. For more information, see Govern discovered apps using Microsoft Defender for Endpoint.
Otherwise, if your tenant uses Zscaler NSS, iboss, Corrata, Menlo, or Open Systems, you can still enjoy seamless blocking capabilities when an app is unsanctioned, but you can't use the scope by device groups or warn and educate features. For more information, see Integrate with Zscaler, Integrate with iboss, Integrate with Corrata, Integrate with Menlo, and Integrate with Open Systems.
Block apps by exporting a block script
Defender for Cloud Apps enables you to block access to unsanctioned apps by using your existing on-premises security appliances. You can generate a dedicated block script and import it to your appliance. This solution doesn't require redirection of all of the organization's web traffic to a proxy.
In the cloud discovery dashboard, tag any apps you want to block as Unsanctioned.
In the title bar, select Actions and then select Generate block script....
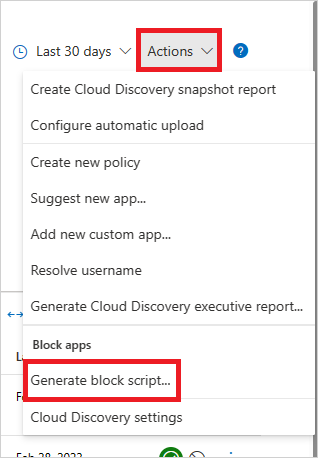
In Generate block script, select the appliance you want to generate the block script for.
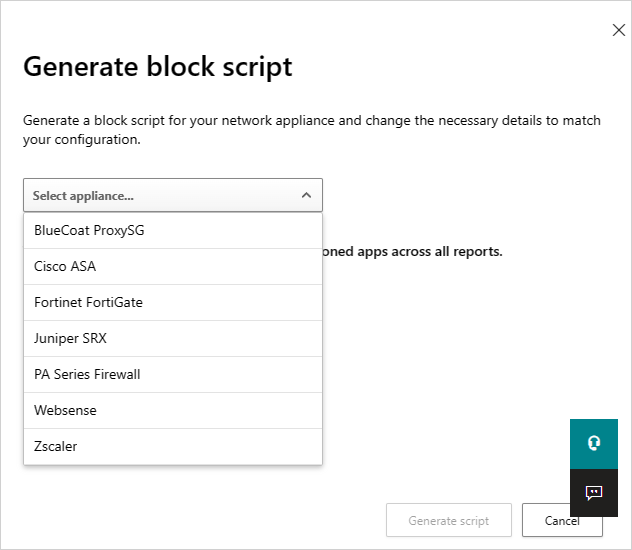
Then select the Generate script button to create a block script for all your unsanctioned apps. By default, the file is named with the date on which it was exported and the appliance type you selected. 2017-02-19_CAS_Fortigate_block_script.txt would be an example file name.
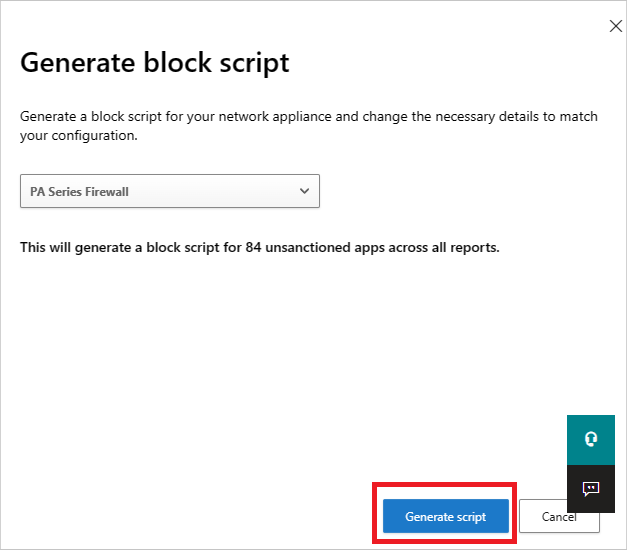
Import the file created to your appliance.
Blocking unsupported streams
If your tenant doesn't use any of the streams above, you can still export a list of all the domains of all unsanctioned apps and configure your third-party nonsupported appliance to block those domains.
In the Discovered apps page, filter all Unsanctioned apps and then use the export capability to export all the domains.
Nonblockable applications
To prevent users from accidentally blocking business-critical services and causing downtime, the following services can't be blocked using Defender for Cloud Apps, via the UI or policies:
- Microsoft Defender for Cloud Apps
- Microsoft Defender Security Center
- Microsoft 365 Security Center
- Microsoft Defender for Identity
- Microsoft Purview
- Microsoft Entra Permissions Management
- Microsoft Conditional Access Application Control
- Microsoft Secure Score
- Microsoft Purview
- Microsoft Intune
- Microsoft Support
- Microsoft AD FS Help
- Microsoft Support
- Microsoft Online Services
Governance conflicts
If there's a conflict between manual governance actions and governance set by policy, the last operation applied takes precedence.
Next steps
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.