Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
With Microsoft Entra Domain Services, you can lift-and-shift legacy applications running on-premises into Azure. Microsoft Entra application proxy then helps you support remote workers by securely publishing those internal applications part of a Domain Services managed domain so they can be accessed over the internet.
If you're new to the Microsoft Entra application proxy and want to learn more, see How to provide secure remote access to internal applications.
This article shows you how to create and configure a Microsoft Entra private network connector to provide secure access to applications in a managed domain.
Before you begin
To complete this article, you need the following resources and privileges:
- An active Azure subscription.
- If you don't have an Azure subscription, create an account.
- A Microsoft Entra tenant associated with your subscription, either synchronized with an on-premises directory or a cloud-only directory.
- If needed, create a Microsoft Entra tenant or associate an Azure subscription with your account.
- A Microsoft Entra ID P1 or P2 license is required to use the Microsoft Entra application proxy.
- A Microsoft Entra Domain Services managed domain enabled and configured in your Microsoft Entra tenant.
Create a domain-joined Windows VM
To route traffic to applications running in your environment, you install the Microsoft Entra private network connector component. This Microsoft Entra private network connector must be installed on a Windows Server virtual machine (VM) that's joined to the managed domain. For some applications, you can deploy multiple servers that each have the connector installed. This deployment option gives you greater availability and helps handle heavier authentication loads.
The VM that runs the Microsoft Entra private network connector must be on the same, or a peered, virtual network as your managed domain. The VMs that then host the applications you publish using the Application Proxy must also be deployed on the same Azure virtual network.
To create a VM for the Microsoft Entra private network connector, complete the following steps:
- Create a custom OU. You can delegate permissions to manage this custom OU to users within the managed domain. The VMs for Microsoft Entra application proxy and that run your applications must be a part of the custom OU, not the default Microsoft Entra DC Computers OU.
- Domain-join the virtual machines, both the one that runs the Microsoft Entra private network connector, and the ones that run your applications, to the managed domain. Create these computer accounts in the custom OU from the previous step.
Download the Microsoft Entra private network connector
Perform the following steps to download the Microsoft Entra private network connector. The setup file you download is copied to your application proxy VM in the next section.
Sign in to the Microsoft Entra admin center as at least an Application Administrator.
Search for and select Enterprise applications.
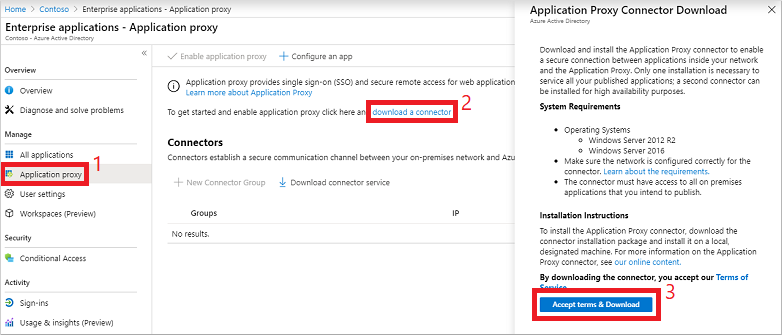
Select Application proxy from the menu on the left-hand side. To create your first connector and enable application proxy, select the link to download a connector.
On the download page, accept the license terms and privacy agreement, then select Accept terms & Download.
Install and register the Microsoft Entra private network connector
With a VM ready to be used as the Microsoft Entra private network connector, now copy and run the setup file downloaded from the Microsoft Entra admin center.
Copy the Microsoft Entra private network connector setup file to your VM.
Run the setup file, such as MicrosoftEntraPrivateNetworkConnectorInstaller.exe. Accept the software license terms.
During the install, you're prompted to register the connector with the Application Proxy in your Microsoft Entra directory.
Note
The account used to register the connector must belong to the same directory where you enable the Application Proxy service.
For example, if the Microsoft Entra domain is contoso.com, the account should be
admin@contoso.comor another valid alias on that domain.- If Internet Explorer Enhanced Security Configuration is turned on for the VM where you install the connector, the registration screen might be blocked. To allow access, follow the instructions in the error message, or turn off Internet Explorer Enhanced Security during the install process.
- If connector registration fails, see Troubleshoot Application Proxy.
At the end of the setup, a note is shown for environments with an outbound proxy. To configure the Microsoft Entra private network connector to work through the outbound proxy, run the provided script, such as
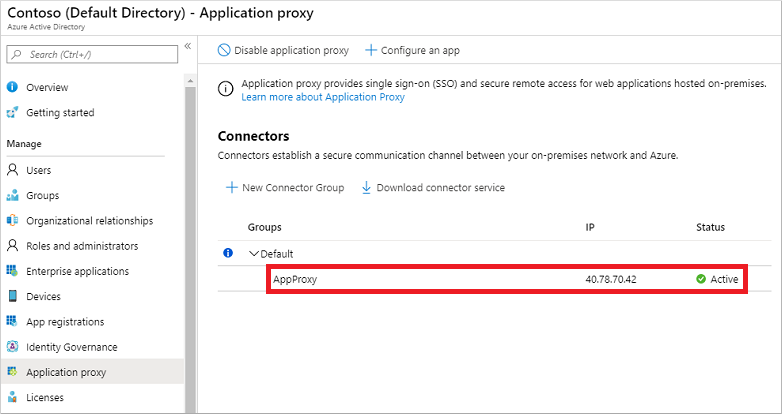
C:\Program Files\Microsoft Entra private network connector\ConfigureOutBoundProxy.ps1.On the Application proxy page in the Microsoft Entra admin center, the new connector is listed with a status of Active, as shown in the following example:
Note
To provide high availability for applications authenticating through the Microsoft Entra application proxy, you can install connectors on multiple VMs. Repeat the same steps listed in the previous section to install the connector on other servers joined to the managed domain.
Enable resource-based Kerberos constrained delegation
If you want to use single sign-on to your applications using integrated Windows authentication (IWA), grant the Microsoft Entra private network connectors permission to impersonate users and send and receive tokens on their behalf. To grant these permissions, you configure Kerberos constrained delegation (KCD) for the connector to access resources on the managed domain. As you don't have domain administrator privileges in a managed domain, traditional account-level KCD cannot be configured on a managed domain. Instead, use resource-based KCD.
For more information, see Configure Kerberos constrained delegation (KCD) in Microsoft Entra Domain Services.
Note
You must be signed in to a user account that's a member of the Microsoft Entra DC administrators group in your Microsoft Entra tenant to run the following PowerShell cmdlets.
The computer accounts for your private network connector VM and application VMs must be in a custom OU where you have permissions to configure resource-based KCD. You can't configure resource-based KCD for a computer account in the built-in Microsoft Entra DC Computers container.
Use the Get-ADComputer to retrieve the settings for the computer on which the Microsoft Entra private network connector is installed. From your domain-joined management VM and logged in as user account that's a member of the Microsoft Entra DC administrators group, run the following cmdlets.
The following example gets information about the computer account named appproxy.aaddscontoso.com. Provide your own computer name for the Microsoft Entra application proxy VM configured in the previous steps.
$ImpersonatingAccount = Get-ADComputer -Identity appproxy.aaddscontoso.com
For each application server that runs the apps behind Microsoft Entra application proxy use the Set-ADComputer PowerShell cmdlet to configure resource-based KCD. In the following example, the Microsoft Entra private network connector is granted permissions to use the appserver.aaddscontoso.com computer:
Set-ADComputer appserver.aaddscontoso.com -PrincipalsAllowedToDelegateToAccount $ImpersonatingAccount
If you deploy multiple Microsoft Entra private network connectors, you must configure resource-based KCD for each connector instance.
Next steps
With the Microsoft Entra application proxy integrated with Domain Services, publish applications for users to access. For more information, see publish applications using Microsoft Entra application proxy.