Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article describes the steps you need to perform in SAP Cloud Identity Services and Microsoft Entra ID to configure automatic user provisioning. When configured, Microsoft Entra ID automatically provisions and deprovisions users to SAP BTP using the Microsoft Entra provisioning service and SAP Cloud Identity Services. For important details on what Microsoft Entra provisioning does, how it works, and frequently asked questions, see Automate user provisioning and deprovisioning to SaaS applications with Microsoft Entra ID.
Capabilities supported
- Create users in SAP BTP to enable single sign-on to SAP BTP
- Remove users in SAP BTP when they don't require access anymore
- Keep user attributes synchronized between Microsoft Entra ID and SAP BTP
You can also manage access to SAP BTP applications, using Microsoft Entra ID Governance to populate groups associated to roles in the application's BTP role collection. For more information, see Managing access to SAP BTP.
Prerequisites
The scenario outlined in this article assumes that you already have the following prerequisites:
- A Microsoft Entra user account with an active subscription. If you don't already have one, you can Create an account for free.
- One of the following roles:
- An SAP BTP app (SAP BTP ABAP environment or SAP BTP XS Advanced UAA Cloud Foundry)
- SAP Cloud Identity Services tenant
- A user account on SAP Identity Provisioning admin console with Admin permissions. Make sure you have access to the proxy systems in the Identity Provisioning admin console. If you don't see the Proxy Systems tile, create an incident for component BC-IAM-IPS to request access to this tile.
Step 1: Plan your provisioning deployment
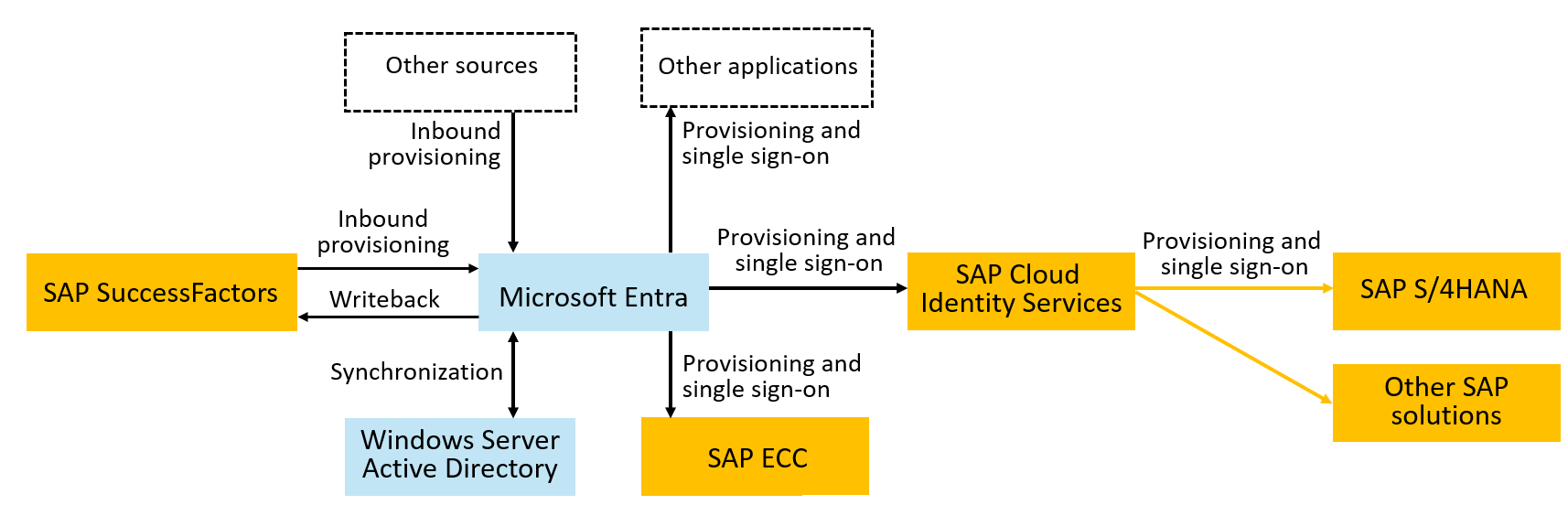
Microsoft Entra has connectors to SAP ECC, SAP Cloud Identity Services, and SAP SuccessFactors. Provisioning into SAP BTP or other applications requires the users to first be present in Microsoft Entra ID. Once you have users in Microsoft Entra ID, you can provision those users from Microsoft Entra ID to SAP Cloud Identity Services. SAP Cloud Identity Services then provisions the users originating from Microsoft Entra ID that are in the SAP Cloud Identity Directory into the downstream SAP applications, including SAP BTP ABAP environment, 'SAP BTP XS Advanced UAA (Cloud Foundry)', and others.
Step 2: Ensure you have the right users in Microsoft Entra ID
You can use HR inbound from sources such as SuccessFactors to keep the list of users in Microsoft Entra ID up to date as employees join, move, and leave. If plan to use groups or application role assignments to scope who can access SAP BTP or what roles they will have, and your tenant has a license for Microsoft Entra ID Governance, you can also automate changes to the application role assignments in Microsoft Entra ID for applications representing SAP Cloud Identity Services or SAP BTP. For more information on performing separation of duties and other compliance checks prior to provisioning, see migrate access lifecycle management scenarios.
For step-by-step guidance on the identity lifecycle with SAP applications as the target, see Plan deploying Microsoft Entra for user provisioning with SAP source and target applications.
Step 3: Configure provisioning from Microsoft Entra ID to SAP Cloud Identity Services
To prepare for provisioning users into SAP BTP or other SAP applications integrated with SAP Cloud Identity Services, confirm the SAP Cloud Identity Services have the necessary schema mappings for those applications. Then, configure provisioning of users from Microsoft Entra ID to SAP Cloud Identity Services. SAP Cloud Identity Services will subsequently provision users into the downstream SAP applications as necessary.
There are two ways to provision users from Microsoft Entra into SAP Cloud Identity Services.
If you be using groups from Microsoft Entra ID, such as to assign users to roles in SAP BTP cloud, then use SAP Cloud Identity Services provisioning. First, create Microsoft Entra groups for your SAP business roles used in SAP Analytics Cloud. Then, in SAP Cloud Identity Services provisioning, configure Microsoft Entra ID as a source to bring users and groups from Microsoft Entra ID to SAP Cloud Identity Services and map the created groups to your SAP business roles. For more information, see SAP documentation on how to provision users from Microsoft Azure AD to SAP Cloud Identity Services - Identity Authentication.
Alternatively, if you don't need to use groups in Microsoft Entra ID, then you can use the Microsoft Entra provisioning service. In this scenario, create an application representing SAP BTP, and assign users who need access to SAP BTP to that application. Then, configure automatic user provisioning with Microsoft Entra ID to SAP Cloud Identity Services for. Wait for those users to be provisioned into SAP Cloud Identity Services, and verify they have the attributes necessary for your SAP BTP target.
Note
Start small. Test with a small set of users and groups before rolling out to everyone. Check the users have the right access in SAP downstream targets and when they sign in, they have the right roles.
Step 4: Configure provisioning from SAP Cloud Identity Services to SAP BTP
At this step, use SAP Cloud Identity Services Identity Provisioning to configure SAP BTP as a target system, where you can provision users and group members. For SAP BTP ABAP environment, see the SAP documentation on provisioning to SAP BTP ABAP environment`. For SAP BTP XS Advanced UAA (Cloud Foundry), see the SAP documentation on provisioning to SAP BTP XS Advanced UAA (Cloud Foundry)'.
Step 5: Configure single sign-on
After you configure provisioning for users into your SAP applications, you should enable Single sign-on for them. Microsoft Entra ID can serve as the identity provider and authentication authority for your SAP applications, and can provide group memberships in claims. If you have not already done so, then configure Microsoft Entra single sign-on (SSO) integration with SAP Cloud Identity Services.
Step 6: Manage access via assigning groups to the SAP BTP role collection
You can manage access to SAP BTP applications using Microsoft Entra ID Governance to populate groups associated to roles in the application's BTP role collection. For more information, see Managing access to SAP BTP.