Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
To do most things on your HoloLens, you have to be connected to a network. HoloLens contains a 802.11ac-capable, 2x2 Wi-Fi radio and connecting it to a network is similar to connecting a Windows 10 Desktop or Mobile device to a Wi-Fi network. This guide helps you to:
- Connect to a network using Wi-Fi, or for HoloLens 2 only, Wi-Fi Direct or Ethernet over USB-C
- Disable and re-enable Wi-Fi
Read more about using HoloLens offline.
Connecting for the first time
The first time you use your HoloLens, you'll be guided through connecting to a Wi-Fi network. If you have trouble connecting to Wi-Fi during setup, make sure that your network is either an open, password-protected network or a captive portal network. Also, confirm that the network doesn't require you to use a certificate to connect. After setup, you can connect to other types of Wi-Fi networks.
On HoloLens 2 devices, users may also use a USB-C to Ethernet adapter to connect directly to Wi-Fi to help setting up the device. Once the device is set up, users may continue to use the adapter, or they may disconnect the device from the adapter and connect to wi-fi after setup.
Connecting to Wi-Fi after setup
- Perform the Start gesture and select Settings. The Settings app will be auto-placed in front of you.
- Select Network & Internet > Wi-Fi. Make sure Wi-Fi is turned on. If you don't see your network, scroll down the list.
- Select a network, then select Connect.
- If you're prompted for a network password, type it and select Next.
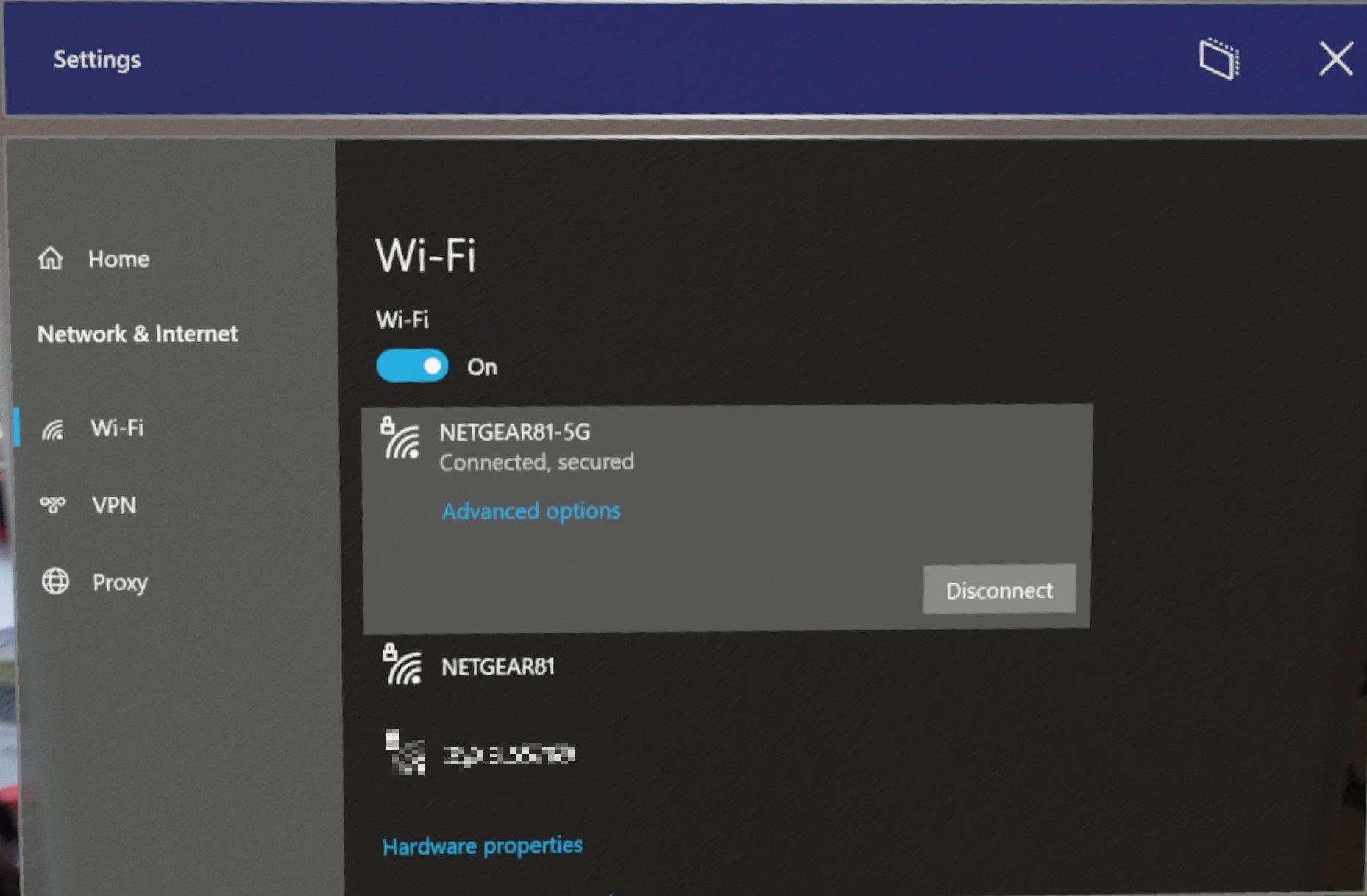
To confirm you're connected to a Wi-Fi network, check the Wi-Fi status in the Start menu:
- Open the Start menu.
- Look at the top left of the Start menu for Wi-Fi status. The state of Wi-Fi and the SSID of the connected network will be shown.
Tip
If Wi-Fi is not available, you can also connect to Cellular and 5G networks.
Important
By design, users cannot fine-tune the Wi-Fi roaming behavior of the HoloLens 2. The only way to refresh the Wi-Fi list is to toggle the Wi-Fi Off and On. This prevents many issues, like where a device can remain "stuck" to an AP once it is out of range.
HoloLens 2 Wi-Fi module
When connecting HoloLens 2 devices to a Wi-Fi network, use the following technical specifications to ensure good roaming between Wi-Fi terminals.
- Chipset: SDM850 with WCN3990 Wi-Fi modules. 802.11 AC wave 1
- Channel bandwidths: 2.4 GHz supports 20 MHz, 5 GHz supports 20 MHz, 40 MHz, and 80 MHz
- Spatial Streams: 2x2 MIMO
- Supports 802.11r (fast roaming), RSSI to trigger roaming is ~70dBm
The Wi-Fi signal level directly affects roaming because throughput requirements vary by use case. Consider the following specifications when setting up Wi-Fi terminals.
Connect HoloLens to Enterprise Wi-Fi Network
Enterprise Wi-Fi profiles use Extensible Authentication Protocol (EAP) to authenticate Wi-Fi connections. The HoloLens Enterprise Wi-Fi profile can be configured through MDM or a provisioning package created by Windows Configuration Designer.
For a Microsoft Intune managed device, refer to Intune for configuration instructions.
To create a Wi-Fi provisioning package in WCD, a preconfigured Wi-Fi profile .xml file is required. Here's a sample Wi-Fi profile for WPA2-Enterprise with EAP-TLS authentication:
<?xml version="1.0"?>
<WLANProfile xmlns="http://www.microsoft.com/networking/WLAN/profile/v1">
<name>SampleEapTlsProfile</name>
<SSIDConfig>
<SSID>
<hex>53616d706c65</hex>
<name>Sample</name>
</SSID>
<nonBroadcast>true</nonBroadcast>
</SSIDConfig>
<connectionType>ESS</connectionType>
<connectionMode>auto</connectionMode>
<autoSwitch>false</autoSwitch>
<MSM>
<security>
<authEncryption>
<authentication>WPA2</authentication>
<encryption>AES</encryption>
<useOneX>true</useOneX>
<FIPSMode xmlns="http://www.microsoft.com/networking/WLAN/profile/v2">false</FIPSMode>
</authEncryption>
<PMKCacheMode>disabled</PMKCacheMode>
<OneX xmlns="http://www.microsoft.com/networking/OneX/v1">
<authMode>machine</authMode>
<EAPConfig>
<EapHostConfig xmlns="http://www.microsoft.com/provisioning/EapHostConfig">
<EapMethod>
<Type xmlns="http://www.microsoft.com/provisioning/EapCommon">13</Type>
<VendorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorId>
<VendorType xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorType>
<AuthorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</AuthorId>
</EapMethod>
<Config xmlns="http://www.microsoft.com/provisioning/EapHostConfig">
<Eap xmlns="http://www.microsoft.com/provisioning/BaseEapConnectionPropertiesV1">
<Type>13</Type>
<EapType xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV1">
<CredentialsSource><CertificateStore><SimpleCertSelection>true</SimpleCertSelection>
</CertificateStore>
</CredentialsSource>
<ServerValidation>
<DisableUserPromptForServerValidation>false</DisableUserPromptForServerValidation>
<ServerNames></ServerNames>
<TrustedRootCA>00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f 10 11 12 13</TrustedRootCA>
</ServerValidation>
<DifferentUsername>false</DifferentUsername>
<PerformServerValidation xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">true</PerformServerValidation>
<AcceptServerName xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">false</AcceptServerName>
</EapType>
</Eap>
</Config>
</EapHostConfig>
</EAPConfig>
</OneX>
</security>
</MSM>
</WLANProfile>
Depending on the EAP type, a server root CA certificate and client certificate may have to be provisioned on the device.
Other resources:
- WLANv1Profile Schema: [MS-GPWL]: Wireless LAN Profile v1 Schema | Microsoft Docs
- EAP-TLS Schema: [MS-GPWL]: Microsoft EAP TLS Schema | Microsoft Docs
Check our Troubleshooting page if you're having trouble connecting to your Wi-Fi.
HoloLens 2 protocols and ports
This table lists IP protocols and TCP/UDP ports used by HoloLens 2 system services.
| Port | Protocol | Application protocol | System service name |
|---|---|---|---|
| N/A | ICMP | ICMP (IP protocol 1) | TCP/IP |
| N/A | IGMP | IGMP (IP protocol 2) | TCP/IP |
| N/A | IPv6 | IPv6 Encapsulation | TCP/IP |
| N/A | ESP | IPsec ESP (IP protocol 50) | Routing and Remote Access |
| N/A | AH | IPsec AH (IP protocol 51) | Routing and Remote Access |
| N/A | IPv6-ICMP | ICMP for IPv6 (IP protocol 58) | TCP/IP |
| 53 | UDP | DNS | DNS Client |
| 67 | UDP | DHCP | TCP/IP |
| 80 | TCP | HTTP | Apps & Services |
| 123 | UDP | SNTP | Windows Time |
| 443 | TCP | HTTPS | Apps & Services |
| 500 | UDP | IPSec IKE | Routing and Remote Access |
| 546 | UDP | DHCPv6 | TCP/IP |
| 1701 | UDP | L2TP | Routing and Remote Access |
| 1900 | UDP | SSDP | SSDP Discovery Service |
| 2869 | TCP | SSDP event notification | SSDP Discovery Service |
| 4500 | UDP | NAT-T | Routing and Remote Access |
| 5353 | UDP | mDNS | DNS Client |
| 5355 | UDP | LLMNR | DNS Client |
| 7236 | TCP | Mixed Reality Capture | MRC Service |
| 7236 | UDP | Mixed Reality Capture | MRC Service |
Configure Network Proxy
This section covers network proxy for HoloLens OS and Universal Windows Platform (UWP) Apps using Windows HTTP stack. Applications using non-Windows HTTP stack may have their own proxy configuration and handling.
Proxy Configurations
- Proxy Auto-Config (PAC) script: a PAC file (opens a non-Microsoft site) contains a JavaScript function FindProxyForURL(url, host).
- Static Proxy: in the form of Server:Port.
- Web Proxy Auto-Discovery Protocol (WPAD): provide URL of proxy configuration file through DHCP or DNS.
Proxy Provisioning Methods
There are three ways to provision proxies:
Settings UI:
- Per-user proxy (20H2 or earlier):
- Open the Start menu and select Settings.
- Select Network & Internet and then Proxy on the left menu.
- Scroll down to Manual proxy set up and toggle Use a proxy server to On.
- Enter the IP address of the proxy server.
- Enter the port number.
- Click Save.
- WiFi proxy (21H1 or higher):
- Open the Start menu and go to your Wi-Fi Network’s Properties page.
- Scroll down to Proxy
- Change to Manual Setup
- Enter the IP address of the proxy server.
- Enter the port number.
- Click Apply.
- Per-user proxy (20H2 or earlier):
MDM
PPKG
- Open Windows Configuration Designer
- Click on Advanced Provisioning, enter the name for your new Project and click Next.
- Select Windows Holographic (HoloLens 2) and click Next.
- Import your PPKG (optional) and click Finish.
- Expand Runtime Settings -> Connectivity Profiles -> WLAN -> WLAN Proxy.
- Enter the SSID of your Wi-Fi network and click Add.
- Select your Wi-Fi network in the left window and enter your desired customizations. The enabled customizations will show in bold on the left menu.
- Click Save and Exit.
- Apply the provisioning package to the HoloLens.
CSPs are behind many of the management tasks and policies for Windows 10, both in Microsoft Intune and in non-Microsoft MDM service providers. You can also use Windows Configuration Designer to create a provisioning package and apply it to the HoloLens 2. The most likely CSPs that will be applied to your HoloLens 2 are:
- WiFi CSP: per-profile Wi-Fi proxy
Other CSPs supported in HoloLens devices
VPN
A VPN connection can help provide a more secure connection and access to your company's network and the Internet. HoloLens 2 supports built-in VPN client and Universal Windows Platform (UWP) VPN plug-in.
Supported Built-in VPN protocols:
- IKEv2
- L2TP
- PPTP
If certificate is used for authentication for built-in VPN client, the required client certificate needs to be added to user certificate store. To find if a 3rd party VPN plug-in supports HoloLens 2, go to Store to locate VPN app and check if HoloLens is listed as a supported device and in the System Requirement page the app supports ARM or ARM64 architecture. HoloLens only supports Universal Windows Platform applications for 3rd party VPN.
VPN can be managed by MDM via Settings/AllowVPN, and set via Vpnv2-csp policy.
Learn more about how to configure VPN with these guides.
VPN via UI
VPN isn't enabled by default but can be enabled manually by opening Settings app and navigating to Network & Internet -> VPN.
- Select a VPN provider.
- Create a connection name.
- Enter your server name or address.
- Select the VPN type.
- Select type of sign-in info.
- Optionally add user name and password.
- Apply the VPN settings.
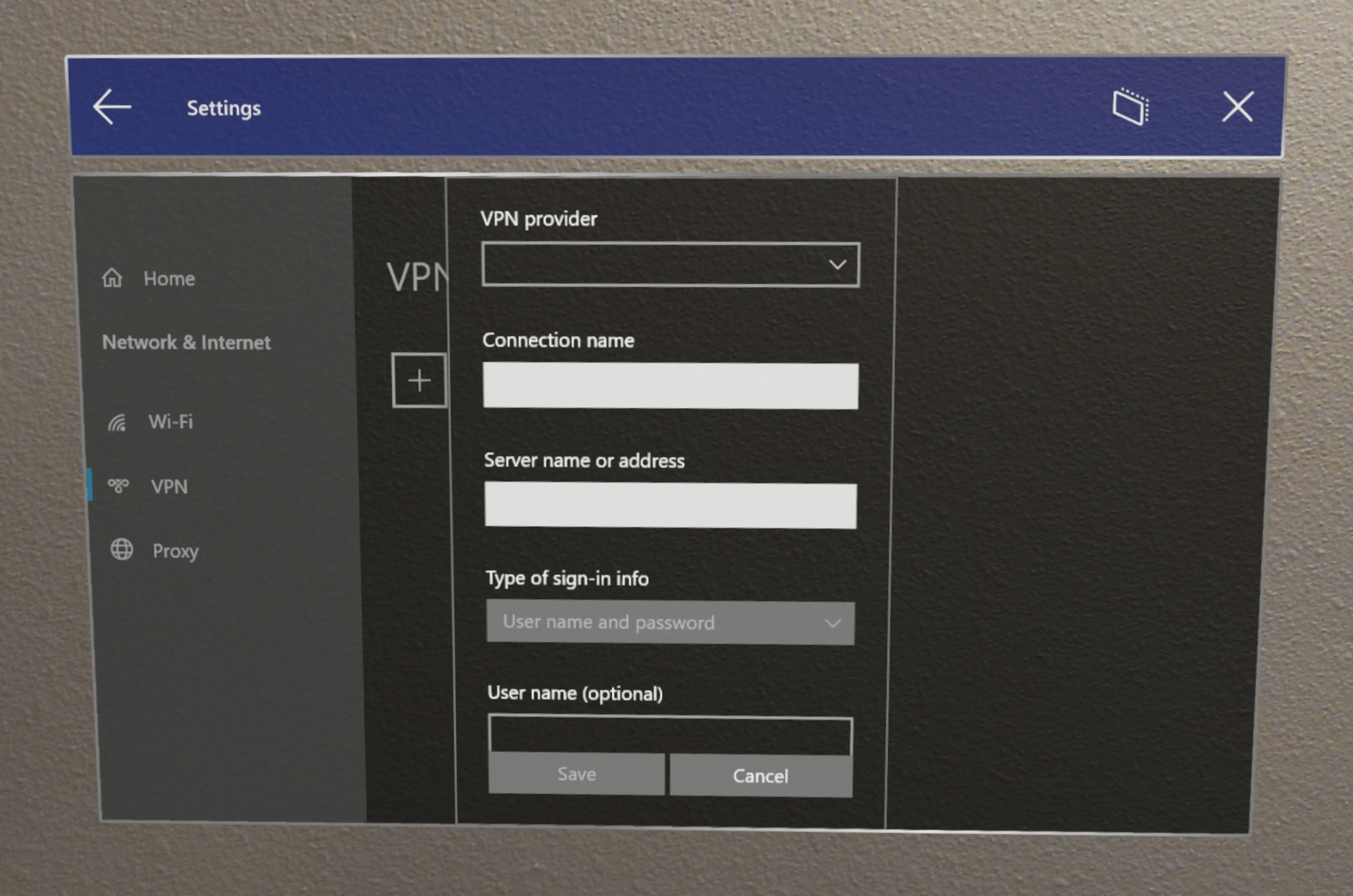
VPN set via Provisioning Package
Tip
In our Windows Holographic, version 20H2 we fixed a proxy configuration issue for VPN connection. Please consider upgrading devices to this build if you intend to use this flow.
- Launch Windows Configuration Designer.
- Click Provision HoloLens devices, then select target device and Next.
- Enter package name and path.
- Click Switch to advanced editor.
- Open Runtime settings -> ConnectivityProfiles -> VPN -> VPNSettings.
- Configure VPNProfileName
- Select ProfileType: Native or Third Party.
- For Native profile, select NativeProtocolType, then configure server, routing policy, authentication type and other settings.
- For "Third Party" profile, configure server URL, VPN plug-in App package family name (only 3 predefined) and custom configurations.
- Export your package.
- Connect your HoloLens and copy the .ppkg file to the device.
- On HoloLens, apply the VPN .ppkg by opening the Start menu and selecting Settings -> Account -> Access work or school -> Add or remove provisioning package -> Select your VPN package.
Setting up VPN via Intune
Just follow the Intune documents to get started. When following these steps, keep in mind the built-in VPN protocols that HoloLens devices support.
Create VPN profiles to connect to VPN servers in Intune.
Windows 10 and Windows Holographic device settings to add VPN connections using Intune.
When done, remember to assign the profile.
VPN via 3rd party MDM solutions
3rd party VPN connection example:
<!-- Configure VPN Server Name or Address (PhoneNumber=) [Comma Separated]-->
<Add>
<CmdID>10001</CmdID>
<Item>
<Target>
<LocURI>./Vendor/MSFT/VPNv2/VPNProfileName/PluginProfile/ServerUrlList</LocURI>
</Target>
<Data>selfhost.corp.contoso.com</Data>
</Item>
</Add>
<!-- Configure VPN Plugin AppX Package ID (ThirdPartyProfileInfo=) -->
<Add>
<CmdID>10002</CmdID>
<Item>
<Target>
<LocURI>./Vendor/MSFT/VPNv2/VPNProfileName/PluginProfile/PluginPackageFamilyName</LocURI>
</Target>
<Data>TestVpnPluginApp-SL_8wekyb3d8bbwe</Data>
</Item>
</Add>
<!-- Configure Microsoft's Custom XML (ThirdPartyProfileInfo=) -->
<Add>
<CmdID>10003</CmdID>
<Item>
<Target>
<LocURI>./Vendor/MSFT/VPNv2/VPNProfileName/PluginProfile/CustomConfiguration</LocURI>
</Target> <Data><pluginschema><ipAddress>auto</ipAddress><port>443</port><networksettings><routes><includev4><route><address>172.10.10.0</address><prefix>24</prefix></route></includev4></routes><namespaces><namespace><space>.vpnbackend.com</space><dnsservers><server>172.10.10.11</server></dnsservers></namespace></namespaces></networksettings></pluginschema></Data>
</Item>
</Add>
Native IKEv2 VPN example:
<Add>
<CmdID>10001</CmdID>
<Item>
<Target>
<LocURI>./Vendor/MSFT/VPNv2/VPNProfileName/NativeProfile/Servers</LocURI>
</Target>
<Data>Selfhost.corp.contoso.com</Data>
</Item>
</Add>
<Add>
<CmdID>10002</CmdID>
<Item>
<Target>
<LocURI>./Vendor/MSFT/VPNv2/VPNProfileName/NativeProfile/RoutingPolicyType</LocURI>
</Target>
<Data>ForceTunnel</Data>
</Item>
</Add>
<!-- Configure VPN Protocol Type (L2tp, Pptp, Ikev2) -->
<Add>
<CmdID>10003</CmdID>
<Item>
<Target>
<LocURI>./Vendor/MSFT/VPNv2/VPNProfileName/NativeProfile/NativeProtocolType</LocURI>
</Target>
<Data>Ikev2</Data>
</Item>
</Add>
<!-- Configure VPN User Method (Mschapv2, Eap) -->
<Add>
<CmdID>10004</CmdID>
<Item>
<Target>
<LocURI>./Vendor/MSFT/VPNv2/VPNProfileName/NativeProfile/Authentication/UserMethod</LocURI>
</Target>
<Data>Eap</Data>
</Item>
</Add>
<Add>
<CmdID>10004</CmdID>
<Item>
<Target>
<LocURI>./Vendor/MSFT/VPNv2/VPNProfileName/NativeProfile/Authentication/Eap/Configuration</LocURI>
</Target>
<Data>EAP_configuration_xml_content</Data>
</Item>
</Add>
Disabling Wi-Fi on HoloLens (1st gen)
Using the Settings app on HoloLens
Open the Start menu.
Select the Settings app from Start or from the All Apps list on the right of the Start menu. The Settings app will be auto-placed in front of you.
Select Network & Internet.
Select the Wi-Fi slider switch to move it to the Off position. This will turn off the RF components of the Wi-Fi radio and disable all Wi-Fi functionality on HoloLens.
Warning
When the Wi-Fi radio is disabled, HoloLens will not be able to automatically load your spaces.
Move the slider switch to the On position to turn on the Wi-Fi radio and restore Wi-Fi functionality on Microsoft HoloLens. The selected Wi-Fi radio state (On or Off) will persist across reboots.
Identifying the IP Address of your HoloLens on the Wi-Fi network
By using the Settings app
Open the Start menu.
Select the Settings app from Start or from the All Apps list on the right of the Start menu. The Settings app will be auto-placed in front of you.
Select Network & Internet.
Scroll down to beneath the list of available Wi-Fi networks and select Hardware properties.
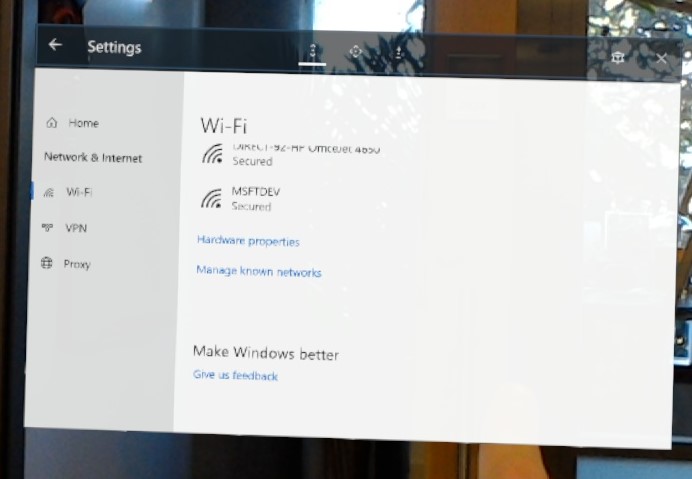
The IP address appears next to IPv4 address.
By using voice commands
Depending on your devices build you can either use built in voice commands or Cortana to display your IP address. On builds after 19041.1103 speak "What's my IP address?" and it will be displayed. For earlier builds or HoloLens (1st gen) say "Hey Cortana, What's my IP address?" and Cortana will display and read out your IP address.
By using Windows Device Portal
- In a web browser on your PC, open the device portal.
- Navigate to the Networking section.
This section displays your IP address and other network information. By using this method, you can copy and paste of the IP address on your development PC.
Change IP Address to static address
By using Settings
- Open the Start menu.
- Select the Settings app from Start or from the All Apps list on the right of the Start menu. The Settings app will be auto-placed in front of you.
- Select Network & Internet.
- Scroll down to beneath the list of available Wi-Fi networks and select Hardware properties.
- In the Edit IP settings window, change the first field to Manual.
- Input the desired IP configuration in the remaining fields and then click Save.
By using Windows Device Portal
- In a web browser on your PC, open the device portal.
- Navigate to the Networking section.
- Select the IPv4 Configuration button.
- Select Use the following IP address and input the desired TCP/IP configuration.
- Select Use the following DNS server addresses and enter the Preferred and Alternate DNS server addresses, if needed.
- Click Save.