Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Overview
This tutorial describes the steps you need to perform in both LinkedIn Learning and Azure Active Directory (Azure AD) to configure automatic user provisioning. When configured, Azure AD automatically provisions and de-provisions users and groups to LinkedIn Learning using SCIM.
For important details on what this service does, how it works, and frequently asked questions, see What is app provisioning in Azure Active Directory?.
Capabilities Supported
- Create user profiles and assign licenses in LinkedIn Learning
- Remove user licenses in LinkedIn Learning when they do not require access anymore
- Keep user attributes synchronized between Azure AD and LinkedIn Learning
- Provision groups and group memberships in LinkedIn Learning
- Single sign-on to LinkedIn Learning (preferred)
Prerequisites
The scenario outlined in this tutorial assumes that you already have the following prerequisites:
- An Azure AD tenant
- A user account in Azure AD with permission to configure provisioning (e.g. Application Administrator, Cloud Application administrator, Application Owner, or Global Administrator)
- LinkedIn Learning admin access
- Accurate user data in LinkedIn Learning. See this guide for instructions on cleaning up your user data if necessary for existing Learning accounts.
Configure LinkedIn Learning to Support SCIM Provisioning with Azure AD
Log into LinkedIn Learning as an admin and navigate to Admin> Authentication.

Click on Automate user management and expand the Configure SCIM section.
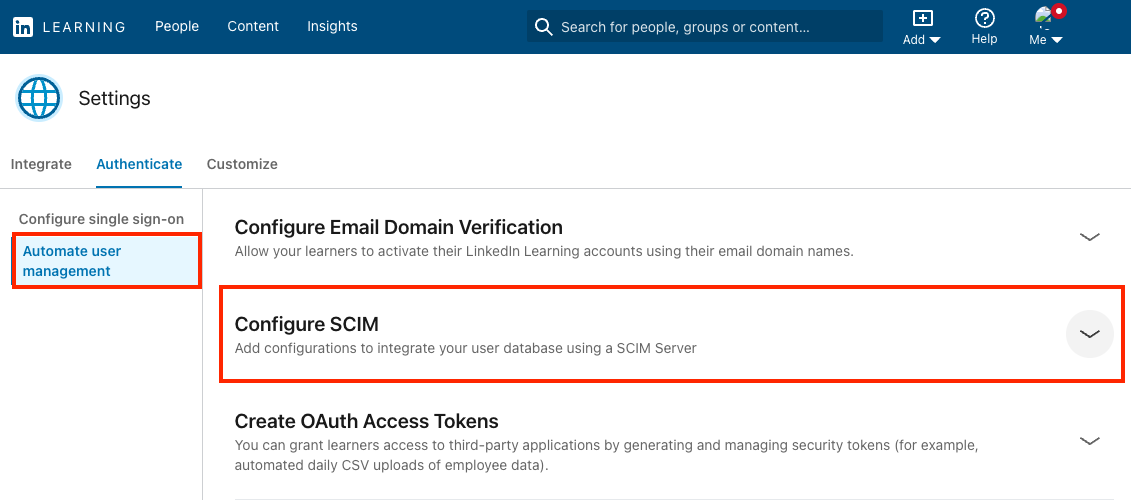
In the Configure SCIM section, elect Add SCIM.
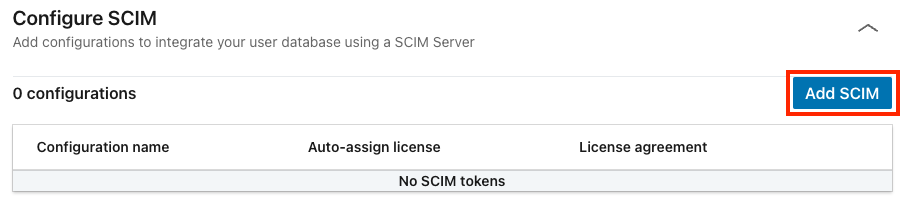
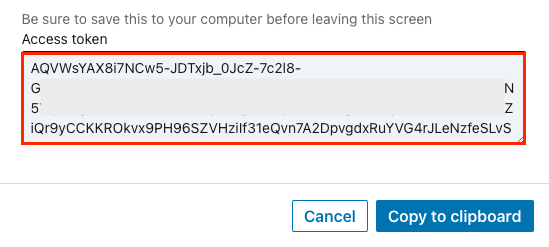
Enter a name for the configuration and set Auto-assign licenses to On. Then, click Generate token.

Copy the Access token for use in the next section.
Enable SCIM Provisioning in Azure AD
If you have previously set up Single Sign-On for LinkedIn Learning, you can use the same application you’ve already configured.
If you have not yet configured SSO for LinkedIn Learning and plan to utilize SSO, follow the instructions here before moving on.
Determine who will be in scope for provisioning
Azure AD allows you to assign the application to specific users or groups or to all users and groups. When SCIM provisioning is enabled, all users and groups assigned to the application will be automatically provisioned in LinkedIn Learning.
Start small. Test with a small set of users and/or groups before assigning the application to your full user group. When the scope for provisioning is set to only assigned users and groups, you can control this by assigning one or two users or groups to the app.
Tip
When new users are provisioned in LinkedIn Learning, an invitation email is sent out automatically. If you want to assign users to the application without notifying them, you should disable emails to new learners as well as recommendation emails in the LinkedIn Learning admin settings. Make sure to re-enable these settings when you are ready to notify your learners. You can also re-send the invitation email at any time in the admin settings.
Configure automatic user provisioning to LinkedIn Learning
This section guides you through the steps to configure the Azure AD provisioning service to create, update, and disable users and/or groups in LinkedIn Learning based on user and/or group assignments in Azure AD.
To configure automatic user provisioning for LinkedIn Learning in Azure AD:
Sign in to the Azure portal and navigate to Azure Active Directory. Select Enterprise Applications, then select All applications.

In the applications list, select LinkedIn Learning.

Select the Provisioning tab from the Manage menu on the left.

Set the Provisioning Mode to Automatic.

Under the Admin Credentials section, input
https://api.linkedin.com/scimin the Tenant URL field and input the access token value retrieved earlier in the Secret Token field. Click Test Connection to ensure Azure AD can connect to LinkedIn Learning.
Click Save.
Under the Mappings section, select Provision Azure Active Directory Users.
Review the user attributes that are synchronized from Azure AD to LinkedIn Learning in the Attribute-Mapping section.
At this time, the list of attributes eligible to be synched automatically is limited to the below table. Leave as-is or remove attributes as needed.
Note
The user attribute mapped to both externalId and userName must match the Unique User Identifier attribute configured for Single Sign-On. By default, these attributes are mapped to userPrincipalName. If userPrincipalName is not a unique, immutable value in your organization, you may want to change the source attribute to employeeId for both Provisioning and Single Sign-On. If you are at all unsure which attribute should be used for the unique identifier, reach out to your LinkedIn Learning account team for guidance.
Default Azure AD Attribute SCIM Attribute Mapping Required userPrincipalName externalId Yes userPrincipalName userName Yes manager urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:manager No givenName name.givenName No surname name.familyName No displayName displayName No city addresses[type eq "work"].locality No jobTitle title No department urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:department No mail emails[type eq "work"].value No (Preferred) Click Save if you made any changes to the attribute mapping.
Expand the Settings section.
In the Notification Email field, enter the email address of a person or group who should receive the provisioning error notifications, and select the Send an email notification when a failure occurs check box.

Define the users and/or groups that you would like to provision to LinkedIn Learning by choosing the desired values in the Scope section.
Note
When enabling automatic provisioning for the first time, choose Sync only assigned users and groups. When provisioning is enabled, an activation email from LinkedIn Learning will be sent to all users who are provisioned to the application in Azure AD. You may want to start by only provisioning a handful of administrators and/or test users.

If your scope is only assigned user and groups, make sure to assign users and groups in the Azure AD LinkedIn Learning application under Users and Groups.
To enable the Azure AD provisioning service for LinkedIn Learning, change the Provisioning Status to On.

When you are ready to provision, click Save.

This operation starts the initial synchronization cycle of all users and groups defined in the Scope section. The initial cycle takes longer to perform than subsequent cycles, which occur approximately every 40 minutes, as long as the Azure AD provisioning service is running.
Monitor Your Deployment
Once you've configured the provisioning service , use the following resources to monitor your deployment:
Use the provisioning logs to determine which users have been provisioned successfully or unsuccessfully.
Check the progress bar to see the status of the provisioning cycle and how close it is to completion.
If the provisioning configuration seems to be in an unhealthy state, the application will go into quarantine. Learn more about quarantine states here.
Note
After successfully completing the initial sync, it is highly recommended you stop the provisioning service before making any changes to assigned users/groups to avoid revoking licenses in error. Stop provisioning, complete all changes, then restart the provisioning process.
If you have any questions, please reach out to your LinkedIn Learning Account team.
Appendix
Additional resources
- Azure AD SSO Tutorial
- Managing user account provisioning for Enterprise Apps
- What is application access and single sign-on with Azure Active Directory?
LinkedIn’s Privacy and Data Security Policy
https://www.linkedin.com/legal/privacy-policy
LinkedIn Security Contacts
If you have any security questions or you would like to report a security issue, write to us at security@linkedin.com.